Monthly Archives: March 2015
California Bill Requires Warrant For Stingray Use
Romanian Man Extradited To U.S. To Face Hacking Charges
Threat sharing bill introduced to House of Representatives
The House of Representatives Intelligence Committee has introduced a new threat sharing bill designed to let businesses share details of security treats without fear of litigation, reports Gizmodo.
The post Threat sharing bill introduced to House of Representatives appeared first on We Live Security.
Not using IPv6? Are you sure?

Internet Protocol version 6 (IPv6) has been around for many years and was first supported in Red Hat Enterprise Linux 6 in 2010. Designed to provide, among other things, additional address space on the ever-growing Internet, IPv6 has only recently become a priority for ISPs and businesses.
On February 3, 2011, ICANN announced that the available pool of unallocated IPv4 addresses had been completely emptied and urged network operators and server owners to implement IPv6 if they had not already done so. Unfortunately, many networks still do not support IPv6 and many system and network administrators don’t understand the security risks associated with not having some sort of IPv6 control within their networks setup even if IPv6 is not supported. The common thought of not having to worry about IPv6 since it’s not supported on a network is a false one.
The Threat
On many operating systems, Red Hat Enterprise Linux and Fedora included, IPv6 is preferred over IPv4. A DNS lookup will search first for an IPv6 address and then an IPv4 address. A system requesting a DHCP allocation will, by default, attempt to obtain both addresses as well. When a network does not support IPv6 it leaves open the possibility of rogue IPv6 DHCP and DNS servers coming online to redirect traffic either around current network restrictions or through a specific choke point where traffic can be inspected or both. Basically, if you aren’t offering up IPv6 within your network someone else could.
Just like on an IPv4 network, monitoring IPv6 on the internal network is crucial for security, especially if you don’t have IPv6 rolled out. Without proper monitoring, an attacker, or poorly configured server, could start providing a path way out of your network, bypassing all established safety mechanisms to keep your data under control.
Implementing IPv6
There are several methods for protecting systems and networks from attacks revolving around IPv6. The simplest, and most preferred method, is to simply start using IPv6. It becomes much more difficult for rouge DNS and DHCP servers to be implemented on a functioning IPv6 network. Implementing IPv6 isn’t particularly difficult either.
Unfortunately IPv6 isn’t all the simple to implement either. As UNC‘s Dr. Joni Julian spoke about in her SouthEast LinuxFest presentation on IPv6 Security, many of the tools administrators use to manage network connections have been rewritten, and thus renamed, to support IPv6. This adds to the confusion when other tools, such as iptables, require different rules to be written to support IPv6. Carnegie Mellon University’s CERT addresses many different facets of implementing IPv6 including ip6tables rules. There are many resources available to help system and network administrators setup IPv6 on their systems and networks and by doing so networks will automatically be available to IPv6-only networks of the future present.
Blocking and Disabling IPv6
If setting up IPv6 isn’t possible the next best thing is disabling, blocking, and monitoring for IPv6 on the network. This means disabling IPv6 in the network stack and blocking IPv6 in ip6tables.
# Set DROP as default policy to INPUT, OUTPUT, and FORWARD chains. ip6tables -P INPUT DROP ip6tables -P OUTPUT DROP ip6tables -P FORWARD DROP# Set DROP as a rule to INPUT and OUTPUT chains.ip6tables -I INPUT -p all -j DROP ip6tables -I OUTPUT -p all -j DROP
Because it can never known that every system on a network will be properly locked down, monitoring for IPv6 packets on the network is important. Many IDSs can be configured to alert on such activity but configuration is key.
A few final words
IPv6 doesn’t have to be scary but if you want to maintain a secure network a certain amount of respect is required. With proper monitoring IPv6 can be an easily manageable “threat”. Of course the best way to mitigate the risks is to embrace IPv6. Rolling it out and using it prevents many of the risks already discussed and it could already be an availability issue if serving up information over the Internet is important.
Product
Red Hat Enterprise Linux
Not using IPv6? Are you sure?
Internet Protocol version 6 (IPv6) has been around for many years and was first supported in Red Hat Enterprise Linux 6 in 2010. Designed to provide, among other things, additional address space on the ever-growing Internet, IPv6 has only recently become a priority for ISPs and businesses.
On February 3, 2011, ICANN announced that the available pool of unallocated IPv4 addresses had been completely emptied and urged network operators and server owners to implement IPv6 if they had not already done so. Unfortunately, many networks still do not support IPv6 and many system and network administrators don’t understand the security risks associated with not having some sort of IPv6 control within their networks setup even if IPv6 is not supported. The common thought of not having to worry about IPv6 since it’s not supported on a network is a false one.
The Threat
On many operating systems, Red Hat Enterprise Linux and Fedora included, IPv6 is preferred over IPv4. A DNS lookup will search first for an IPv6 address and then an IPv4 address. A system requesting a DHCP allocation will, by default, attempt to obtain both addresses as well. When a network does not support IPv6 it leaves open the possibility of rouge IPv6 DHCP and DNS servers coming online to redirect traffic either around current network restrictions or through a specific choke point where traffic can be inspected or both. Basically, if you aren’t offering up IPv6 within your network someone else could.
Just like on an IPv4 network, monitoring IPv6 on the internal network is crucial for security, especially if you don’t have IPv6 rolled out. Without proper monitoring, an attacker, or poorly configured server, could start providing a path way out of your network, bypassing all established safety mechanisms to keep your data under control.
Implementing IPv6
There are several methods for protecting systems and networks from attacks revolving around IPv6. The simplest, and most preferred method, is to simply start using IPv6. It becomes much more difficult for rouge DNS and DHCP servers to be implemented on a functioning IPv6 network. Implementing IPv6 isn’t particularly difficult either.
Unfortunately IPv6 isn’t all the simple to implement either. As UNC‘s Dr. Joni Julian spoke about in her SouthEast LinuxFest presentation on IPv6 Security, many of the tools administrators use to manage network connections have been rewritten, and thus renamed, to support IPv6. This adds to the confusion when other tools, such as iptables, require different rules to be written to support IPv6. Carnegie Mellon University’s CERT addresses many different facets of implementing IPv6 including ip6tables rules. There are many resources available to help system and network administrators setup IPv6 on their systems and networks and by doing so networks will automatically be available to IPv6-only networks of the future present.
Blocking and Disabling IPv6
If setting up IPv6 isn’t possible the next best thing is disabling, blocking, and monitoring for IPv6 on the network. This means disabling IPv6 in the network stack and blocking IPv6 in ip6tables.
# Set DROP as default policy to INPUT, OUTPUT, and FORWARD chains. ip6tables -P INPUT DROP ip6tables -P OUTPUT DROP ip6tables -P FORWARD DROP# Set DROP as a rule to INPUT and OUTPUT chains.ip6tables -I INPUT -p all -j DROP ip6tables -I OUTPUT -p all -j DROP
Because it can never known that every system on a network will be properly locked down, monitoring for IPv6 packets on the network is important. Many IDSs can be configured to alert on such activity but configuration is key.
A few final words
IPv6 doesn’t have to be scary but if you want to maintain a secure network a certain amount of respect is required. With proper monitoring IPv6 can be an easily manageable “threat”. Of course the best way to mitigate the risks is to embrace IPv6. Rolling it out and using it prevents many of the risks already discussed and it could already be an availability issue if serving up information over the Internet is important.
Kaspersky Lab Awarded Bronze Stevie Award in 2015 Stevie Awards for Sales & Customer Service
The Future Of Internet Dating – Infographic
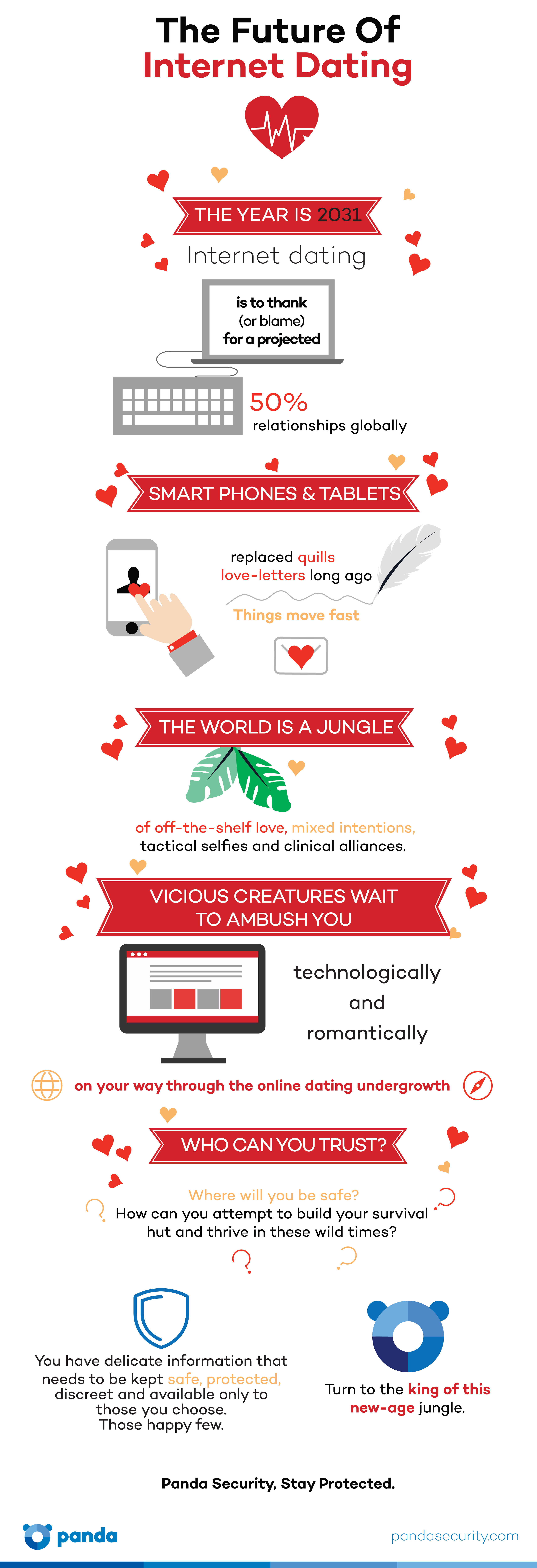
The Future Of Internet Dating
The year is 2031. Internet dating is to thank (or blame) for a projected 50% of relationships globally.
Smart phones and tablets replaced quills and love-letters long ago. Things move fast.
The world is a jungle of off-the-shelf love, mixed intentions, tactical selfies and clinical alliances.
Vicious creatures wait to ambush you – technologically and romantically – on your way through the online dating undergrowth.
Who can you trust? Where will you be safe? How can you attempt to build your survival hut and thrive in these wild times?
You have delicate information that needs to be kept safe, protected, discreet and available only to those you choose. Those happy few.
Turn to the king of this new-age jungle.
Panda Security. Stay Protected
If you want to share this infographic, here it’s the code!
The post The Future Of Internet Dating – Infographic appeared first on MediaCenter Panda Security.
Wearables will evolve beyond screens
A healthy human has multiple biological senses he or she was born with. Sight, hearing, taste, smell and touch are the five traditionally recognized. The ability to detect other stimuli beyond those governed by the traditional senses exists, including temperature, kinesthetic sense, pain and balance.
If I had to explain a human sense, in our digital world, I would describe it as a biological sensor that responds to a specific physical stimuli and transmits the data to brain cells that later interpret them for us and may lead to a response.
Our biological senses respond to physical stimuli, but could we develop a sensor that responds to stimuli created in the digital world?
I believe the answer is simple; yes. For example, I could get a notification delivered directly to my brain when something important is happening, such as my child has not returned from school on time or when my glucose level is high.
The idea isn’t unprecedented. Many animals have unusual biological sensors that to support their surroundings and lifestyle. This however, took millions of years; we could create something in just a few.
Over the last few years, we’ve developed new technologies to help people with different disabilities to gain back their lost senses. Advances include a tiny eye implant that restores sight to the blind and electronic hearing devices that help people with severe hearing loss.
While these technologies are very important for our society and for the people who need them, their main goal is to restore (or provide an alternative to) the damaged/missing sense that respond to a physical stimuli.
How do we create a digital sense?
Digital senses aren’t as far away as you may think. Smartwatches have started to emerge. Although they are still in their first release version people struggle to understand the benefit of them. Is it yet another screen to look at? Does it just save me from having to take my phone out of my pocket? Will it replace some tasks I do on my smartphone? Or is it just another input peripheral to my smartphone? Where is the value to me?
While most of the available applications of a smartwatch are to bring the smartphone notifications to my eyes via a screen on my wrist, there is another – hidden- value in such devices and that is to develop a new sense. I call it the Digital Sense.
A digital sense can respond to digital events, convert them into physical ones and transmit that information to our brain cells in non-invasive methods – for example, with a combination of one or more micro vibrations. The human brain will then interpret them and respond.
In the digital mobile world, smartphones receive data from many sources: the web, email, embedded sensors and cloud services. However, the main method smartphones use to convey all this data to the human brain is via a screen. As a result, we find ourselves spending many hours in front of multiple screens in order to consume data.
Google Glass introduced new possibilities in the way we interact with and respond to our digital world. Some would say that Google Glass failed as it was too intrusive and harmful to real world social experiences.
A sensor would never do this. A sensor should be part of the body and transmit information for the brain cells to process – not to form another obstacle as we saw with Google Glass.
I believe that by taking advantage of wearable technologies and using them to transform digital data into a physical stimulus that our biological sensors can interpret, in a non-invasive way, will be the most valuable application of wearables. I believe it will dramatically increase the adoption of wearable tech as the value proposition can be immediately understood.
Imagine a smartband on your wrist or a smart device on your shirt that will vibrate or move when your glucose level is high or when your family or colleagues urgently need you.
This is not the notification sound, as we know it from our smartphone today. They are intrusive, not necessarily private and not properly secured. It is more advanced than that. It’s a new sense that we wear and transforms our digital data into something our biological sense can transmit to our brain cells in a non-intrusive, secure and private way. This is where wearable technologies will find their home, not as an additional tiny screen.
Recently I experimented and implementation of such new sense on my wrist, and I do not feel like I will let it go any time soon.
All four major browsers hacked at pwn2own
Last week computer hacking competition pwn2own once again took place at the CanSecWest conference in Vancouver.
During the competition, hackers and security researchers are challenged to exploit popular software and devices using previously unknown vulnerabilities.
Successful hackers win the device that they exploited, a cash prize, and a “Masters” jacket celebrating the year of their win.
Pwn2own 2015 was an incredibly eventful competition with over $500,000 dollars of rewards issued and all four major browsers successfully hacked, some in under a second.
News of ubiquitous software being hacked in such a short time can often leave us feeling despondent about the state of security but I believe that competitions such as pwn2own give us cause for optimism.
Cash prizes for hacking at competitions and bug bounty programs, such as those run by Google and Facebook, motivate hackers and researchers to use their skills to help improve security and not just exploit it.
As long as vulnerabilities are disclosed to the right parties when they are discovered, it helps to reduce the window of opportunity for malicious hackers to turn a profit.
Remember to update
While software manufacturers were likely hoping to come through pwn2own 2015 unscathed, most will now set about fixing and patching their products and services to mitigate these newly discovered threats.
Expect new security updates in the near future and remember to always keep your operating system and programs up to date.
