The US government’s $6 Billion firewall is nothing but a big blunder.
Dubbed EINSTEIN, the nationwide firewall run by the US Department of Homeland Security (DHS) is not as smart as its name suggests.
An audit conducted by the United States Government Accountability Office (GAO) has claimed that the firewall used by US government agencies is failing to fully meet its objectives and leaving the agencies open to zero-day attacks.
EINSTEIN, which is officially known as the US’ National Cybersecurity Protection System (NCPS) and has cost $5.7 Billion to develop, detects only 6 percent of today’s most common security vulnerabilities and failed to detect the rest 94 percent.
How bad is EINSTEIN Firewall in reality?
In a series of tests conducted last year, Einstein only
detected 29 out of 489 vulnerabilities across Flash, Office, Java, IE and Acrobat disclosed via CVE reports published in 2014, according to a report [
PDF] released by the GAO late last year.
Among the extraordinary pieces of information revealed are the fact that the system is:
- Unable to monitor web traffic for malicious content.
- Unable to uncover malware in a system.
- Unable to monitor cloud services either.
- Only offers signature-based threat and intrusion detection, rather than monitoring for unusual activity.
Yes, Einstein only carries out signature-based threat and intrusion detection, which means the system acts like a dumb terminal that waits for the command what to find, rather than to search itself for unusual activity.
Einstein Uses Outdated Signatures Database
In fact, more than 65 percent of intrusion detection signatures (digital fingerprints of known viruses and exploit code) are outdated, making Einstein wide open to recently discovered zero-day vulnerabilities.
However, in response to this, DHS told the office Einstein was always meant to be a signature-based detection system only. Here’s what the department told the auditors:
“It is the responsibility of each agency to ensure their networks and information systems are secure while it is the responsibility of DHS to provide a baseline set of protections and government-wide situational awareness, as part of a defense-in-depth information security strategy.”
Einstein is Effectively Blind
If this wasn’t enough to figure out the worth of the $6 Billion firewall, Einstein is effectively Blind.
The Department of Homeland Security (DHS), which is behind the development of Einstein, has not included any feature to measure the system’s own performance, so the system doesn’t even know if it is doing a good job or not.
So, “until its intended capabilities are more fully developed, DHS will be hampered in its abilities to provide effective cybersecurity-related support to federal agencies,” reads the report.
Einstein was actually developed in 2003 to automatically monitor agency network traffic, and later in 2009 expanded to offer signature-based detection as well as malware-blocking abilities.
Most of the 23 agencies are actually required to implement the firewall, but the GAO found that only 5 of them were utilising the system to deal with possible intrusions.
Despite having spent $1.2 Billion in 2014 and
$5.7 Billion in total project, Einstein still only monitors certain types of network flaws along with no support for monitoring web traffic or cloud services.
 Avast CEO, Vince Steckler, joined a panel of top security experts for a roundtable discussion about cybersecurity in our everyday lives.
Avast CEO, Vince Steckler, joined a panel of top security experts for a roundtable discussion about cybersecurity in our everyday lives.![]()


 What WhatsApp’s new end-to-end encryption means for you
What WhatsApp’s new end-to-end encryption means for you





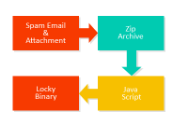 A closer look at the Locky ransomware
A closer look at the Locky ransomware



