Severity Rating: Important
Revision Note: V1.0 (May 13, 2014): Bulletin published.
Summary: This security update resolves a privately reported vulnerability in Microsoft Windows. The vulnerability could allow elevation of privilege if an attacker runs a specially crafted application that uses ShellExecute. An attacker must have valid logon credentials and be able to log on locally to exploit this vulnerability.
Monthly Archives: May 2014
MS14-026 – Important: Vulnerability in .NET Framework Could Allow Elevation of Privilege (2958732) – Version: 1.0
Severity Rating: Important
Revision Note: V1.0 (May 13, 2014): Bulletin published.
Summary: This security update resolves a privately reported vulnerability in Microsoft .NET Framework. The vulnerability could allow elevation of privilege if an authenticated attacker sends specially crafted data to an affected workstation or server that uses .NET Remoting. .NET Remoting is not widely used by applications; only custom applications that have been specifically designed to use .NET Remoting would expose a system to the vulnerability.
MS14-023 – Important: Vulnerabilities in Microsoft Office Could Allow Remote Code Execution (2961037) – Version: 1.1
Severity Rating: Important
Revision Note: V1.1 (May 13, 2014): V1.1 (May 13, 2014): Corrected the update replacement for the Microsoft Office 2010 (proofing tools) (2878284) update.
Summary: This security update resolves two privately reported vulnerabilities in Microsoft Office. The most severe vulnerability could allow remote code execution if a user opens an Office file that is located in the same network directory as a specially crafted library file. An attacker who successfully exploited this vulnerability could gain the same user rights as the current user. Customers whose accounts are configured to have fewer user rights on the system could be less impacted than those who operate with administrative user rights.
MS14-024 – Important: Vulnerability in a Microsoft Common Control Could Allow Security Feature Bypass (2961033) – Version: 1.0
Severity Rating: Important
Revision Note: V1.0 (May 13, 2014): Bulletin published.
Summary: This security update resolves one privately reported vulnerability in an implementation of the MSCOMCTL common controls library. The vulnerability could allow security feature bypass if a user views a specially crafted webpage in a web browser capable of instantiating COM components, such as Internet Explorer. In a web-browsing attack scenario, an attacker who successfully exploited this vulnerability could bypass the Address Space Layout Randomization (ASLR) security feature, which helps protect users from a broad class of vulnerabilities. The security feature bypass by itself does not allow arbitrary code execution. However, an attacker could use this ASLR bypass vulnerability in conjunction with another vulnerability, such as a remote code execution vulnerability that could take advantage of the ASLR bypass to run arbitrary code.
MS14-022 – Critical: Vulnerabilities in Microsoft SharePoint Server Could Allow Remote Code Execution (2952166) – Version: 1.0
Severity Rating: Critical
Revision Note: V1.0 (May 13, 2014): Bulletin published.
Summary: This security update resolves multiple privately reported vulnerabilities in Microsoft Office server and productivity software. The most severe of these vulnerabilities could allow remote code execution if an authenticated attacker sends specially crafted page content to a target SharePoint server.
MS14-025 – Important: Vulnerability in Group Policy Preferences Could Allow Elevation of Privilege (2962486) – Version: 1.0
Severity Rating: Important
Revision Note: V1.0 (May 13, 2014): Bulletin published.
Summary: This security update resolves a publicly disclosed vulnerability in Microsoft Windows. The vulnerability could allow elevation of privilege if an authenticated attacker uses certain Active Directory Group Policy preferences extensions to configure, distribute and ultimately decrypt the passwords that are stored with Group Policy preferences.
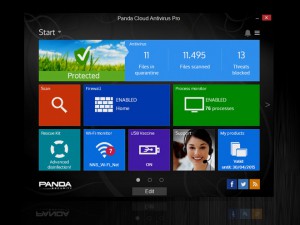
Panda Security launches Panda Cloud Antivirus 3.0, more intuitive, lighter and safer than ever before
Panda Security, The Cloud Security Company, today announced the launch of a new version of its popular cloud-based free antivirus scanner Panda Cloud Antivirus, v3.0. The launch follows the successful release last February of the product’s 2.9 beta, which has already been downloaded more than 30,000 times by users from more than 130 countries.
Panda Cloud Antivirus 3.0 has, in both its free and Pro Edition versions, a completely new look and feel, much more modern and intuitive than ever before. Additionally, the solution provides significantly improved protection against new threats and exploits that take advantage of system vulnerabilities, as well as automatic USB vaccination, a feature which was previously restricted to Pro users only and is now available to all users.
Also, the solution includes a Rescue Kit extremely useful in emergency situations caused by malware infections, and a more powerful process monitor.
New Features
The new Panda Cloud Antivirus provides the ability to run scheduled scans, a feature strongly demanded by the Panda Security community, and a new Panda Account, a personal area where users can download products, manage their services, obtain documentation, access technical support through a new support forum, and manage their Android devices provided they are protected with Panda Mobile Security.
In addition, users of the Pro version will be able to enjoy VIP support via a Web form and the technical support forum. The Pro version comes with a new Wi-Fi monitor module which enables users to display a list of all devices that are currently connected to their network and find out if there is someone stealing their Wi-Fi.
All these improvements make the new Panda Cloud Antivirus 3.0 lighter and more complete than ever. “We are constantly evolving our detection technologies to protect our customers against new and emerging threats while minimizing false positives. And our efforts are paying off, as shown by the excellent results obtained by Panda Cloud Antivirus in the latest AV-Test evaluation, where it ranked as the best free antivirus solutionâ€, said Alberto Añón, Panda Cloud Antivirus Product Manager at Panda Security.
Top Ratings by AV-Test
The latest evaluation and certification report published by the prestigious IT security institute AV-Test rates Panda Cloud Antivirus as the best free antivirus solution. The product obtained top ratings in the protection (6/6) and ease of use (6/6) areas, without a single false positive.
Click here for more information about Panda Cloud Antivirus
![]()
CVE-2014-3214 (bind)
The prefetch implementation in named in ISC BIND 9.10.0, when a recursive nameserver is enabled, allows remote attackers to cause a denial of service (REQUIRE assertion failure and daemon exit) via a DNS query that triggers a response with unspecified attributes.
CVE-2014-0189 (enterprise_linux_desktop, enterprise_linux_server, enterprise_linux_workstation, virt-who)
virt-who uses world-readable permissions for /etc/sysconfig/virt-who, which allows local users to obtain password for hypervisors by reading the file.