Apache HTTP Server 2.4.10 Released
The Apache Software Foundation and the Apache HTTP Server Project
are pleased to announce the release of version 2.4.10 of the Apache
HTTP Server ("Apache"). This version of Apache is our latest GA
release of the new generation 2.4.x branch of Apache HTTPD and
represents fifteen years of innovation by the project, and is
recommended over all previous releases. This release of Apache is
principally a security, feature and bug fix release.
CVE-2014-0117 (cve.mitre.org)
mod_proxy: Fix crash in Connection header handling which
allowed a denial of service attack against a reverse proxy
with a threaded MPM.
CVE-2014-3523 (cve.mitre.org)
Fix a memory consumption denial of service in the WinNT MPM (used in all Windows
installations). Workaround: AcceptFilter <protocol> {none|connect}
CVE-2014-0226 (cve.mitre.org)
Fix a race condition in scoreboard handling, which could lead to
a heap buffer overflow.
CVE-2014-0118 (cve.mitre.org)
mod_deflate: The DEFLATE input filter (inflates request bodies) now
limits the length and compression ratio of inflated request bodies to avoid
denial of sevice via highly compressed bodies. See directives
DeflateInflateLimitRequestBody, DeflateInflateRatioLimit,
and DeflateInflateRatioBurst.
CVE-2014-0231 (cve.mitre.org)
mod_cgid: Fix a denial of service against CGI scripts that do
not consume stdin that could lead to lingering HTTPD child processes
filling up the scoreboard and eventually hanging the server. By
default, the client I/O timeout (Timeout directive) now applies to
communication with scripts. The CGIDScriptTimeout directive can be
used to set a different timeout for communication with scripts.
Also in this release are some exciting new features including:
*) Proxy FGI and websockets improvements
*) Proxy capability via handler
*) Finer control over scoping of RewriteRules
*) Unix Domain Socket (UDS) support for mod_proxy backends.
*) Support for larger shared memory sizes for mod_socache_shmcb
*) mod_lua and mod_ssl enhancements
*) Support named groups and backreferences within the LocationMatch,
DirectoryMatch, FilesMatch and ProxyMatch directives.
We consider this release to be the best version of Apache available, and
encourage users of all prior versions to upgrade.
Apache HTTP Server 2.4.10 is available for download from:
http://httpd.apache.org/download.cgi
Apache 2.4 offers numerous enhancements, improvements, and performance
boosts over the 2.2 codebase. For an overview of new features
introduced since 2.4 please see:
http://httpd.apache.org/docs/trunk/new_features_2_4.html
Please see the CHANGES_2.4 file, linked from the download page, for a
full list of changes. A condensed list, CHANGES_2.4.10 includes only
those changes introduced since the prior 2.4 release. A summary of all
of the security vulnerabilities addressed in this and earlier releases
is available:
http://httpd.apache.org/security/vulnerabilities_24.html
This release requires the Apache Portable Runtime (APR) version 1.5.x
and APR-Util version 1.5.x. The APR libraries must be upgraded for all
features of httpd to operate correctly.
This release builds on and extends the Apache 2.2 API. Modules written
for Apache 2.2 will need to be recompiled in order to run with Apache
2.4, and require minimal or no source code changes.
http://svn.apache.org/repos/asf/httpd/httpd/trunk/VERSIONING
When upgrading or installing this version of Apache, please bear in mind
that if you intend to use Apache with one of the threaded MPMs (other
than the Prefork MPM), you must ensure that any modules you will be
using (and the libraries they depend on) are thread-safe.
Monthly Archives: July 2014
CVE-2014-3523
Memory leak in the winnt_accept function in server/mpm/winnt/child.c in the WinNT MPM in the Apache HTTP Server 2.4.x before 2.4.10 on Windows, when the default AcceptFilter is enabled, allows remote attackers to cause a denial of service (memory consumption) via crafted requests. (CVSS:5.0) (Last Update:2014-07-23)
CVE-2014-0226
Race condition in the mod_status module in the Apache HTTP Server before 2.4.10 allows remote attackers to cause a denial of service (heap-based buffer overflow), or possibly obtain sensitive credential information or execute arbitrary code, via a crafted request that triggers improper scoreboard handling within the status_handler function in modules/generators/mod_status.c and the lua_ap_scoreboard_worker function in modules/lua/lua_request.c. (CVSS:6.8) (Last Update:2014-09-04)
CVE-2014-0118
The deflate_in_filter function in mod_deflate.c in the mod_deflate module in the Apache HTTP Server before 2.4.10, when request body decompression is enabled, allows remote attackers to cause a denial of service (resource consumption) via crafted request data that decompresses to a much larger size. (CVSS:4.3) (Last Update:2014-09-04)
CVE-2014-0231
The mod_cgid module in the Apache HTTP Server before 2.4.10 does not have a timeout mechanism, which allows remote attackers to cause a denial of service (process hang) via a request to a CGI script that does not read from its stdin file descriptor. (CVSS:5.0) (Last Update:2014-09-04)
CVE-2014-0117
The mod_proxy module in the Apache HTTP Server 2.4.x before 2.4.10, when a reverse proxy is enabled, allows remote attackers to cause a denial of service (child-process crash) via a crafted HTTP Connection header. (CVSS:4.3) (Last Update:2014-09-04)
CVE-2013-4352
The cache_invalidate function in modules/cache/cache_storage.c in the mod_cache module in the Apache HTTP Server 2.4.6, when a caching forward proxy is enabled, allows remote HTTP servers to cause a denial of service (NULL pointer dereference and daemon crash) via vectors that trigger a missing hostname value. (CVSS:4.3) (Last Update:2014-08-04)
CVE-2014-2623 (storage_data_protector)
Unspecified vulnerability in HP Storage Data Protector 8.x allows remote attackers to execute arbitrary code via unknown vectors.
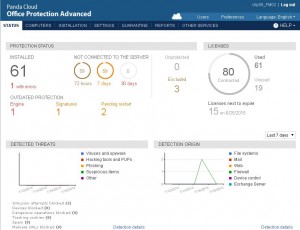
Panda Security launches Version 7.0 of its cross-platform corporate solution
?Panda Security, The Cloud Security Company, has announced major improvements in the new version 7.0 of Panda Cloud Office Protection (PCOP). Since the initial launch of Panda Cloud Office Protection, many companies have been able to enjoy the best possible cloud-based protection in a simple, agile and effective solution. Now, thanks to this latest release, customers will be able to act independently in the event of infections or problems with the protection deployed on their IT infrastructure. Similarly, customers now have easy access to all the information they need about their licenses, detections and the protections status.
?Benefits for organizations with more than 100 endpoints The latest release includes improvements aimed especially at customers with more than 100 endpoints. Panda Cloud Office Protection 7.0 includes major new technologies and features, including:
- New dashboards. Offering key information about licenses, detections and the protection status of customers? computers.
- Improved reports. Providing more detailed information about detections, reports are now easier to access and threat data is organized according to the level of risk, making it simpler to identify the most vulnerable systems.
- Remediation. In the event of an infection, administrators can launch Panda Cloud Cleaner, Panda Security?s disinfection tool, remotely from the PCOP Web console. Administrators can also force reboots of computers from the console and find information on how to act should problems arise on the protection deployed on the company?s IT infrastructure. Similarly, FAQs are available detailing the steps to take to resolve such issues or if signature files are out-of-date.
?This latest version of Panda Cloud Office Protection responds to the needs and demands of our users. Many of the key improvements included will be particularly welcomed by customers with more than 100 endpoints. We have improved the reports process in PCOP 7.0 so our customers will now have more intuitive access to information about threats: where they?re located, where they came from, etc.,? says Manuel Santamar?a, Product Manager Director at Panda Security.
![]()
CVE-2014-4243 (mysql, solaris, suse_linux_enterprise_desktop, suse_linux_enterprise_server, suse_linux_enterprise_software_development_kit)
Unspecified vulnerability in the MySQL Server component in Oracle MySQL 5.5.35 and earlier and 5.6.15 and earlier allows remote authenticated users to affect availability via vectors related to ENFED.