| adobe — adobe_air |
Adobe Flash Player before 13.0.0.241 and 14.x before 14.0.0.176 on Windows and OS X and before 11.2.202.400 on Linux, Adobe AIR before 14.0.0.178 on Windows and OS X and before 14.0.0.179 on Android, Adobe AIR SDK before 14.0.0.178, and Adobe AIR SDK & Compiler before 14.0.0.178 do not properly restrict the SWF file format, which allows remote attackers to conduct cross-site request forgery (CSRF) attacks against JSONP endpoints, and obtain sensitive information, via a crafted OBJECT element with SWF content satisfying the character-set requirements of a callback API, in conjunction with a manipulation involving a ‘$’ (dollar sign) or ‘(‘ (open parenthesis) character. NOTE: this issue exists because of an incomplete fix for CVE-2014-4671. |
2014-08-19 |
6.8 |
CVE-2014-5333
MISC |
| alienvault — open_source_security_information_management |
SQL injection vulnerability in AlienVault OSSIM before 4.7.0 allows remote authenticated users to execute arbitrary SQL commands via unspecified vectors. |
2014-08-21 |
6.5 |
CVE-2014-5383 |
| apache — ofbiz |
Multiple cross-site scripting (XSS) vulnerabilities in framework/common/webcommon/includes/messages.ftl in Apache OFBiz 11.04.01 before 11.04.05 and 12.04.01 before 12.04.04 allow remote attackers to inject arbitrary web script or HTML via unspecified vectors, which are not properly handled in a (1) result or (2) error message. |
2014-08-22 |
4.3 |
CVE-2014-0232
XF
SECTRACK
BID
BUGTRAQ
SECUNIA
MLIST
MISC |
| apache — subversion |
The (1) serf_ssl_cert_issuer, (2) serf_ssl_cert_subject, and (3) serf_ssl_cert_certificate functions in Serf 0.2.0 through 1.3.x before 1.3.7 does not properly handle a NUL byte in a domain name in the subject’s Common Name (CN) field of an X.509 certificate, which allows man-in-the-middle attackers to spoof arbitrary SSL servers via a crafted certificate issued by a legitimate Certification Authority. |
2014-08-19 |
4.0 |
CVE-2014-3504
CONFIRM |
| apache — subversion |
The Serf RA layer in Apache Subversion 1.4.0 through 1.7.x before 1.7.18 and 1.8.x before 1.8.10 does not properly handle wildcards in the Common Name (CN) or subjectAltName field of the X.509 certificate, which allows man-in-the-middle attackers to spoof servers via a crafted certificate. |
2014-08-19 |
4.0 |
CVE-2014-3522
XF
BID
SECUNIA |
| apache — subversion |
Apache Subversion 1.0.0 through 1.7.x before 1.7.17 and 1.8.x before 1.8.10 uses an MD5 hash of the URL and authentication realm to store cached credentials, which makes it easier for remote servers to obtain the credentials via a crafted authentication realm. |
2014-08-19 |
4.0 |
CVE-2014-3528 |
| apache — httpasyncclient |
org.apache.http.conn.ssl.AbstractVerifier in Apache HttpComponents HttpClient before 4.3.5 and HttpAsyncClient before 4.0.2 does not properly verify that the server hostname matches a domain name in the subject’s Common Name (CN) or subjectAltName field of the X.509 certificate, which allows man-in-the-middle attackers to spoof SSL servers via a “CN=” string in a field in the distinguished name (DN) of a certificate, as demonstrated by the “foo,CN=www.apache.org” string in the O field. |
2014-08-21 |
5.8 |
CVE-2014-3577
FULLDISC
MISC |
| baidu — spark_browser |
Stack-based buffer overflow in Baidu Spark Browser 26.5.9999.3511 allows remote attackers to cause a denial of service (application crash) via nested calls to the window.print JavaScript function. |
2014-08-19 |
5.0 |
CVE-2014-5349
MISC
EXPLOIT-DB
OSVDB |
| binarymoon — timthumb |
Cross-site scripting (XSS) vulnerability in timthumb.php in TimThumb 1.09 and earlier, as used in Mimbo Pro 2.3.1 and other products, allows remote attackers to inject arbitrary web script or HTML via the src parameter. |
2014-08-21 |
4.3 |
CVE-2009-5142
CONFIRM
OSVDB
MISC |
| binarymoon — timthumb |
Cross-site scripting (XSS) vulnerability in timthumb.php in TimThumb before 1.15 as of 20100908 (r88), as used in multiple products, allows remote attackers to inject arbitrary web script or HTML via the QUERY_STRING. |
2014-08-21 |
4.3 |
CVE-2010-5302
CONFIRM
OSVDB |
| binarymoon — timthumb |
Cross-site scripting (XSS) vulnerability in the displayError function in timthumb.php in TimThumb before 1.15 (r85), as used in multiple products, allows remote attackers to inject arbitrary web script or HTML via unspecified vectors related to $errorString. |
2014-08-21 |
4.3 |
CVE-2010-5303 |
| bitdefender — gravityzone |
Multiple directory traversal vulnerabilities in Bitdefender GravityZone before 5.1.11.432 allow remote attackers to read arbitrary files via a (1) .. (dot dot) in the id parameter to webservice/CORE/downloadFullKitEpc/a/1 in the Web Console or (2) %2E%2E (encoded dot dot) in the default URI to port 7074 on the Update Server. |
2014-08-19 |
5.0 |
CVE-2014-5350
MISC
CONFIRM
FULLDISC |
| blackberry — q10 |
The Storage and Access service in BlackBerry OS 10.x before 10.2.1.1925 on Q5, Q10, Z10, and Z30 devices does not enforce the password requirement for SMB filesystem access, which allows context-dependent attackers to read arbitrary files via (1) a session over a Wi-Fi network or (2) a session over a USB connection in Development Mode. |
2014-08-18 |
6.1 |
CVE-2014-2388
BUGTRAQ
MISC
MISC |
| cisco — asr_5000_series_software |
The Session Manager component in Packet Data Network Gateway (aka PGW) in Cisco ASR 5000 Series Software 11.0, 12.0, 12.1, 12.2, 14.0, 15.0, 16.x through 16.1.2, and 17.0 allows remote attackers to cause a denial of service (process crash) via a crafted TCP packet, aka Bug ID CSCuo21914. |
2014-08-20 |
4.3 |
CVE-2014-3331 |
| cisco — webex_meetmenow |
Directory traversal vulnerability in an unspecified PHP script in the server in Cisco WebEx MeetMeNow allows remote authenticated users to read arbitrary files via a crafted request, aka Bug ID CSCuo16166. |
2014-08-20 |
4.0 |
CVE-2014-3340 |
| cisco — nexus_5000 |
The SNMP module in Cisco NX-OS 7.0(3)N1(1) and earlier on Nexus 5000 and 6000 devices provides different error messages for invalid requests depending on whether the VLAN ID exists, which allows remote attackers to enumerate VLANs via a series of requests, aka Bug ID CSCup85616. |
2014-08-19 |
5.0 |
CVE-2014-3341 |
| debian — kde4libs |
KDE kdelibs before 4.14 and kauth before 5.1 does not properly use D-Bus for communication with a polkit authority, which allows local users to bypass intended access restrictions by leveraging a PolkitUnixProcess PolkitSubject race condition via a (1) setuid process or (2) pkexec process, related to CVE-2013-4288 and “PID reuse race conditions.” |
2014-08-19 |
6.9 |
CVE-2014-5033
UBUNTU
DEBIAN
SECUNIA
SECUNIA
SECUNIA
CONFIRM
SUSE |
| disqus — disqus_comment_system |
Cross-site scripting (XSS) vulnerability in upgrade.php in the Disqus Comment System plugin before 2.76 for WordPress allows remote attackers to inject arbitrary web script or HTML via the step parameter. |
2014-08-19 |
4.3 |
CVE-2014-5345
MISC
BID
FULLDISC
MISC |
| disqus — disqus_comment_system |
Multiple cross-site request forgery (CSRF) vulnerabilities in the Disqus Comment System plugin 2.77 for WordPress allow remote attackers to hijack the authentication of administrators for requests that (1) activate or (2) deactivate the plugin via the active parameter to wp-admin/edit-comments.php, (3) import comments via an import_comments action, or (4) export comments via an export_comments action to wp-admin/index.php. |
2014-08-19 |
6.8 |
CVE-2014-5346
MISC
FULLDISC |
| disqus — disqus_comment_system |
Multiple cross-site request forgery (CSRF) vulnerabilities in the Disqus Comment System plugin before 2.76 for WordPress allow remote attackers to hijack the authentication of administrators for requests that conduct cross-site scripting (XSS) attacks via the (1) disqus_replace, (2) disqus_public_key, or (3) disqus_secret_key parameter to wp-admin/edit-comments.php in manage.php or that (4) reset or (5) delete plugin options via the reset parameter to wp-admin/edit-comments.php. |
2014-08-19 |
6.8 |
CVE-2014-5347
MISC
MISC
XF
XF
BID
EXPLOIT-DB
FULLDISC
MISC
MISC |
| drupal — drupal |
The Incutio XML-RPC (IXR) Library, as used in WordPress before 3.9.2 and Drupal 6.x before 6.33 and 7.x before 7.31, permits entity declarations without considering recursion during entity expansion, which allows remote attackers to cause a denial of service (memory and CPU consumption) via a crafted XML document containing a large number of nested entity references, a similar issue to CVE-2003-1564. |
2014-08-18 |
5.0 |
CVE-2014-5265
CONFIRM
CONFIRM |
| drupal — drupal |
The Incutio XML-RPC (IXR) Library, as used in WordPress before 3.9.2 and Drupal 6.x before 6.33 and 7.x before 7.31, does not limit the number of elements in an XML document, which allows remote attackers to cause a denial of service (CPU consumption) via a large document, a different vulnerability than CVE-2014-5265. |
2014-08-18 |
5.0 |
CVE-2014-5266
CONFIRM
CONFIRM
CONFIRM
CONFIRM
CONFIRM |
| emc — rsa_archer_egrc |
EMC RSA Archer GRC Platform 5.x before 5.5 SP1 allows remote authenticated users to bypass intended restrictions on resource access via unspecified vectors. |
2014-08-20 |
4.0 |
CVE-2014-0640
BUGTRAQ |
| emc — rsa_archer_egrc |
Cross-site request forgery (CSRF) vulnerability in EMC RSA Archer GRC Platform 5.x before 5.5 SP1 allows remote attackers to hijack the authentication of arbitrary users. |
2014-08-20 |
6.8 |
CVE-2014-0641
BUGTRAQ |
| emc — rsa_archer_egrc |
EMC RSA Archer GRC Platform 5.x before 5.5 SP1 allows remote attackers to trigger the download of arbitrary code, and consequently change the product’s functionality, via unspecified vectors. |
2014-08-20 |
5.4 |
CVE-2014-2505
BUGTRAQ |
| emc — digital_assets_manager |
Multiple cross-site scripting (XSS) vulnerabilities in EMC Documentum WebTop before 6.7 SP1 P28 and 6.7 SP2 before P14 allow remote attackers to inject arbitrary web script or HTML via the (1) startat or (2) entryId parameter. |
2014-08-20 |
4.3 |
CVE-2014-2511
BUGTRAQ |
| emc — rsa_archer_egrc |
Unspecified vulnerability in EMC RSA Archer GRC Platform 5.x before 5.5 SP1 allows remote authenticated users to gain privileges via unknown vectors. |
2014-08-20 |
6.5 |
CVE-2014-2517
BUGTRAQ |
| emc — digital_assets_manager |
Multiple cross-site request forgery (CSRF) vulnerabilities in EMC Documentum WDK before 6.7SP1 P28 and 6.7SP2 before P15 allow remote attackers to hijack the authentication of arbitrary users. |
2014-08-20 |
6.8 |
CVE-2014-2518
BUGTRAQ |
| emc — documentum_content_server |
EMC Documentum Content Server before 6.7 SP2 P16 and 7.x before 7.1 P07, when Oracle Database is used, does not properly restrict DQL hints, which allows remote authenticated users to conduct DQL injection attacks and read sensitive database content via a crafted request. |
2014-08-20 |
6.3 |
CVE-2014-2520
BUGTRAQ |
| emc — documentum_content_server |
EMC Documentum Content Server before 6.7 SP2 P16 and 7.x before 7.1 P07 allows remote authenticated users to read sensitive object metadata via an RPC command. |
2014-08-20 |
6.3 |
CVE-2014-2521
BUGTRAQ |
| esri — arcgis_for_server |
Multiple cross-site scripting (XSS) vulnerabilities in ESRI ArcGIS for Server 10.1.1 allow remote attackers to inject arbitrary web script or HTML via unspecified parameters. |
2014-08-22 |
4.3 |
CVE-2014-5121
BUGTRAQ |
| esri — arcgis_for_server |
Open redirect vulnerability in ESRI ArcGIS for Server 10.1.1 allows remote attackers to redirect users to arbitrary web sites and conduct phishing attacks via an unspecified parameter, related to login. |
2014-08-22 |
5.8 |
CVE-2014-5122
BUGTRAQ |
| fedoraproject — 389_directory_server |
Red Hat Directory Server 8 and 389 Directory Server, when debugging is enabled, allows remote attackers to obtain sensitive replicated metadata by searching the directory. |
2014-08-21 |
5.0 |
CVE-2014-3562
CONFIRM |
| fengoffice — feng_office |
Cross-site scripting (XSS) vulnerability in Feng Office allows remote attackers to inject arbitrary web script or HTML via a client Name field. |
2014-08-19 |
4.3 |
CVE-2014-5343
XF
BID
MISC |
| freebsd — freebsd |
The HZ module in the iconv implementation in FreeBSD 10.0 before p6 and NetBSD allows context-dependent attackers to cause a denial of service (NULL pointer dereference) via a crafted argument to the iconv_open function. NOTE: this issue was SPLIT per ADT2 due to different vulnerability types. CVE-2014-5384 is used for the NULL pointer dereference. |
2014-08-21 |
5.0 |
CVE-2014-3951
SECTRACK
MLIST |
| freebsd — freebsd |
The VIQR module in the iconv implementation in FreeBSD 10.0 before p6 and NetBSD allows context-dependent attackers to cause a denial of service (out-of-bounds array access) via a crafted argument to the iconv_open function. NOTE: this issue was SPLIT from CVE-2014-3951 per ADT2 due to different vulnerability types. |
2014-08-21 |
5.0 |
CVE-2014-5384
SECTRACK
MLIST |
| ibm — websphere_datapower_soa_appliance |
IBM WebSphere DataPower SOA appliances through 4.0.2.15, 5.x through 5.0.0.17, 6.0.0.x through 6.0.0.9, and 6.0.1.x through 6.0.1.5 make it easier for remote attackers to obtain a PreMasterSecret value and defeat cryptographic protection mechanisms by sending a large number of requests in an SSL/TLS side-channel timing attack. |
2014-08-16 |
4.3 |
CVE-2014-0852
XF |
| ibm — websphere_application_server |
IBM WebSphere Application Server (WAS) 7.0.x before 7.0.0.33, 8.0.x before 8.0.0.9, and 8.5.x before 8.5.5.3 allows remote attackers to obtain sensitive information via a crafted SOAP response. |
2014-08-21 |
4.3 |
CVE-2014-0965
XF
AIXAPAR |
| ibm — infosphere_master_data_management |
SQL injection vulnerability in the GDS component in IBM InfoSphere Master Data Management – Collaborative Edition 10.x and 11.x before 11.0-FP5 and InfoSphere Master Data Management Server for Product Information Management 9.x through 11.x before 11.3-IF2 allows remote authenticated users to execute arbitrary SQL commands via unspecified vectors. |
2014-08-17 |
6.5 |
CVE-2014-0966
XF |
| ibm — infosphere_master_data_management |
Cross-site request forgery (CSRF) vulnerability in the GDS component in IBM InfoSphere Master Data Management – Collaborative Edition 10.x and 11.x before 11.0-FP5 and InfoSphere Master Data Management Server for Product Information Management 9.x through 11.x before 11.3-IF2 allows remote authenticated users to hijack the authentication of arbitrary users. |
2014-08-17 |
6.8 |
CVE-2014-0969
XF |
| ibm — websphere_application_server |
IBM WebSphere Application Server (WAS) 7.0.x before 7.0.0.33, 8.0.x before 8.0.0.9, and 8.5.x before 8.5.5.3 allows remote attackers to obtain sensitive information via a crafted URL that triggers an error condition. |
2014-08-21 |
4.3 |
CVE-2014-3022
XF
AIXAPAR |
| ibm — websphere_application_server |
The addFileRegistryAccount Virtual Member Manager (VMM) SPI Admin Task in IBM WebSphere Application Server (WAS) 8.0.x before 8.0.0.10 and 8.5.x before 8.5.5.3 does not properly create accounts, which allows remote attackers to bypass intended access restrictions via unspecified vectors. |
2014-08-21 |
5.0 |
CVE-2014-3070
XF
AIXAPAR |
| ibm — global_console_manager_16_firmware |
Multiple cross-site scripting (XSS) vulnerabilities on IBM GCM16 and GCM32 Global Console Manager switches with firmware before 1.20.20.23447 allow remote attackers to inject arbitrary web script or HTML via (1) the query string to kvm.cgi or (2) the key parameter to avctalert.php. |
2014-08-17 |
4.3 |
CVE-2014-3080
XF
EXPLOIT-DB |
| ibm — global_console_manager_16_firmware |
prodtest.php on IBM GCM16 and GCM32 Global Console Manager switches with firmware before 1.20.20.23447 allows remote authenticated users to read arbitrary files via the filename parameter. |
2014-08-17 |
6.3 |
CVE-2014-3081
XF
EXPLOIT-DB |
| ibm — websphere_application_server |
IBM WebSphere Application Server (WAS) 7.0.x before 7.0.0.35, 8.0.x before 8.0.0.10, and 8.5.x before 8.5.5.3 does not properly restrict resource access, which allows remote attackers to obtain sensitive information via unspecified vectors. |
2014-08-21 |
5.0 |
CVE-2014-3083
XF
AIXAPAR |
| ibm — business_process_manager |
callService.do in IBM Business Process Manager (BPM) 7.5 through 8.5.5 and WebSphere Lombardi Edition 7.2 through 7.2.0.5 allows remote authenticated users to read arbitrary files via an XML external entity declaration in conjunction with an entity reference, related to an XML External Entity (XXE) issue. |
2014-08-17 |
4.0 |
CVE-2014-3087
XF |
| ibm — rational_directory_administrator |
The RDS Java Client library in IBM Rational Directory Server (RDS) 5.1.1.x before 5.1.1.2 iFix004 and 5.2.x before 5.2.1 iFix003, and Rational Directory Administrator (RDA) 6.0 before iFix002, includes the cleartext root password, which allows local users to obtain sensitive information by reading a library file. |
2014-08-21 |
4.9 |
CVE-2014-3089
XF |
| ibm — powervc |
IBM PowerVC 1.2.0 before FixPack3 does not properly use the known_hosts file, which allows man-in-the-middle attackers to spoof SSH servers via an arbitrary server key. |
2014-08-20 |
4.3 |
CVE-2014-4749
XF |
| ibm — websphere_application_server |
IBM WebSphere Application Server (WAS) Liberty Profile 8.5.x before 8.5.5.3 does not properly use the Liberty Repository for feature installation, which allows remote authenticated users to execute arbitrary code via unspecified vectors. |
2014-08-21 |
6.5 |
CVE-2014-4767
XF
AIXAPAR |
| ibm — infosphere_master_data_management |
IBM InfoSphere Master Data Management – Collaborative Edition 10.x before 10.1-FP11 and 11.x before 11.0-FP5 and InfoSphere Master Data Management Server for Product Information Management 9.x before 9.1-FP15 and 10.x and 11.x before 11.3-IF2 do not properly protect credentials, which allows remote attackers to obtain sensitive information via unspecified vectors. |
2014-08-17 |
5.0 |
CVE-2014-4775
XF |
| linecorp — line |
LINE 3.2.1.83 and earlier on Windows and 3.2.1 and earlier on OS X does not verify X.509 certificates from SSL servers, which allows man-in-the-middle attackers to spoof servers and obtain sensitive information via a crafted certificate. |
2014-08-16 |
4.3 |
CVE-2013-7144
MISC |
| mobiloud — mobiloud |
Multiple cross-site scripting (XSS) vulnerabilities in the Mobiloud (mobiloud-mobile-app-plugin) plugin before 2.3.8 for WordPress allow remote attackers to inject arbitrary web script or HTML via unspecified vectors. NOTE: some of these details are obtained from third party information. |
2014-08-19 |
4.3 |
CVE-2014-5344
SECUNIA |
| openstack — neutron |
The notifier middleware in OpenStack PyCADF 0.5.0 and earlier, Telemetry (Ceilometer) 2013.2 before 2013.2.4 and 2014.x before 2014.1.2, Neutron 2014.x before 2014.1.2 and Juno before Juno-2, and Oslo allows remote authenticated users to obtain X_AUTH_TOKEN values by reading the message queue (v2/meters/http.request). |
2014-08-19 |
5.0 |
CVE-2014-4615
UBUNTU
BID
MLIST
MLIST
MLIST
SECUNIA
REDHAT |
| owncloud — owncloud |
Directory traversal vulnerability in the routing component in ownCloud Server before 5.0.17 and 6.0.x before 6.0.4 allows remote attackers to include and execute arbitrary local files via a .. (dot dot) in a filename, related to index.php. |
2014-08-20 |
6.8 |
CVE-2014-4929
BID
MANDRIVA
CONFIRM |
| piwigo — piwigo |
Cross-site scripting (XSS) vulnerability in admin/picture_modify.php in the photo-edit subsystem in Piwigo 2.6.3 and earlier allows remote attackers to inject arbitrary web script or HTML via the associate[] field, a different vulnerability than CVE-2014-4649. |
2014-08-17 |
4.3 |
CVE-2014-3900
CONFIRM
JVNDB
JVN |
| redhat — jboss_enterprise_application_platform |
The EJB invocation handler implementation in Red Hat JBossWS, as used in JBoss Enterprise Application Platform (EAP) 6.2.0 and 6.3.0, does not properly enforce the method level restrictions for outbound messages, which allows remote authenticated users to access otherwise restricted JAX-WS handlers by leveraging permissions to the EJB class. NOTE: this vulnerability exists because of an incomplete fix for CVE-2013-2133. |
2014-08-19 |
5.5 |
CVE-2014-3464
CONFIRM |
| redhat — jboss_enterprise_application_platform |
The isCallerInRole function in SimpleSecurityManager in JBoss Application Server (AS) 7, as used in Red Hat JBoss Enterprise Application Platform (JBEAP) 6.3.0, does not properly check caller roles, which allows remote authenticated users to bypass access restrictions via unspecified vectors. |
2014-08-19 |
4.9 |
CVE-2014-3472
CONFIRM |
| riverbed — steelapp_traffic_manager |
Cross-site scripting (XSS) vulnerability in apps/zxtm/locallog.cgi in Riverbed Stingray (aka SteelApp) Traffic Manager Virtual Appliance 9.6 patchlevel 9620140312 allows remote attackers to inject arbitrary web script or HTML via the logfile parameter. |
2014-08-19 |
4.3 |
CVE-2014-5348
BID
FULLDISC |
| schrack — technik_microcontrol |
Multiple cross-site scripting (XSS) vulnerabilities in the web interface in Schrack Technik microControl with firmware 1.7.0 (937) allow remote attackers to inject arbitrary web script or HTML via the position textbox in the configuration menu or other unspecified vectors. |
2014-08-20 |
4.3 |
CVE-2014-5382
MISC
FULLDISC |
| shopizer — shopizer |
com/salesmanager/central/profile/ProfileAction.java in Shopizer 1.1.5 and earlier does not restrict the number of authentication attempts, which makes it easier for remote attackers to guess passwords via a brute force attack. |
2014-08-21 |
5.0 |
CVE-2014-5385
BUGTRAQ
FULLDISC |
| symantec — encryption_desktop |
Symantec Encryption Desktop 10.3.x before 10.3.2 MP3, and Symantec PGP Desktop 10.0.x through 10.2.x, allows remote attackers to cause a denial of service (CPU and memory consumption) via a crafted encrypted e-mail message that decompresses to a larger size. |
2014-08-21 |
5.0 |
CVE-2014-3436
BID |
| tenfourzero — shutter |
Cross-site scripting (XSS) vulnerability in tenfourzero Shutter 0.1.4 allows remote attackers to inject arbitrary web script or HTML via unspecified vectors. |
2014-08-17 |
4.3 |
CVE-2014-3905 |
| wordpress — wordpress |
wp-includes/pluggable.php in WordPress before 3.9.2 rejects invalid CSRF nonces with a different timing depending on which characters in the nonce are incorrect, which makes it easier for remote attackers to bypass a CSRF protection mechanism via a brute-force attack. |
2014-08-18 |
6.8 |
CVE-2014-5204
CONFIRM
MLIST |
| wordpress — wordpress |
wp-includes/pluggable.php in WordPress before 3.9.2 does not use delimiters during concatenation of action values and uid values in CSRF tokens, which makes it easier for remote attackers to bypass a CSRF protection mechanism via a brute-force attack. |
2014-08-18 |
6.8 |
CVE-2014-5205
CONFIRM
MLIST |
| xml-dt_project — xml-dt |
The (1) mkxmltype and (2) mkdtskel scripts in XML-DT before 0.64 allow local users to overwrite arbitrary files via a symlink attack on a /tmp/_xml_##### temporary file. |
2014-08-16 |
4.9 |
CVE-2014-5260
CONFIRM
CONFIRM
CONFIRM
MLIST |
![]()


 ‘See who has been looking at your Facebook profile’
‘See who has been looking at your Facebook profile’
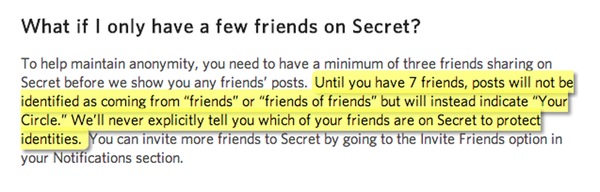
 And the Secret app’s developers have confirmed that since a bug bounty was introduced in February, a total of 42 security holes have been identified and fixed.
And the Secret app’s developers have confirmed that since a bug bounty was introduced in February, a total of 42 security holes have been identified and fixed.