![]()
Monthly Archives: August 2014
Robin Williams’ last phone call? Sick Facebook video scam exploits celebrity suicide
Be on your guard against yet another Facebook scam, this time exploiting the tragic death of comic actor Robin Williams.
The scam, which you may see shared by your Facebook friends oblivious to the fact that they are helping fraudsters earn money, claims to be a ghoulish video of Robin Williams making his last phone call before committing suicide earlier this week.
Of course, you might be fooled into believing it is genuine. After all, you have seen one of your Facebook friends share it on their wall.
But the truth is that they have been duped into sharing it by a simple social engineering trick, and you would be wise not to fall into the same trap.
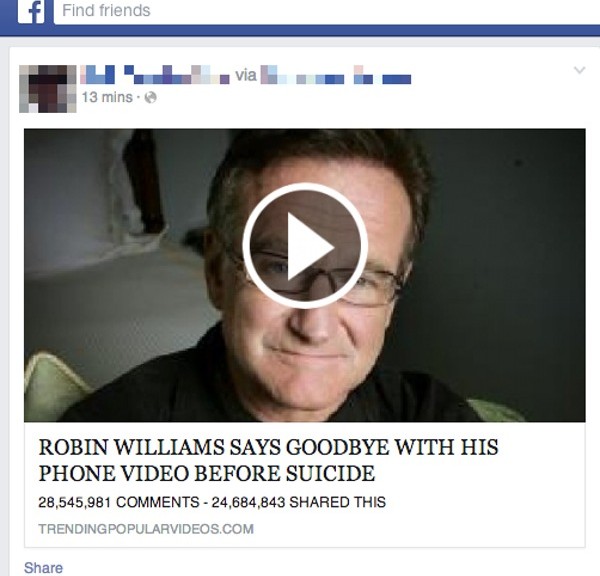
The first thing you see is a post made by one of your Facebook friends:
<blockquote style=”margin: 15px;padding: 15px 15px 5px;border-left: 5px solid #ccc;font-size: 13px;
font-style: normal;font-family: ‘Helvetica Neue’, Helvetica, sans-serif;line-height: 19px;”>
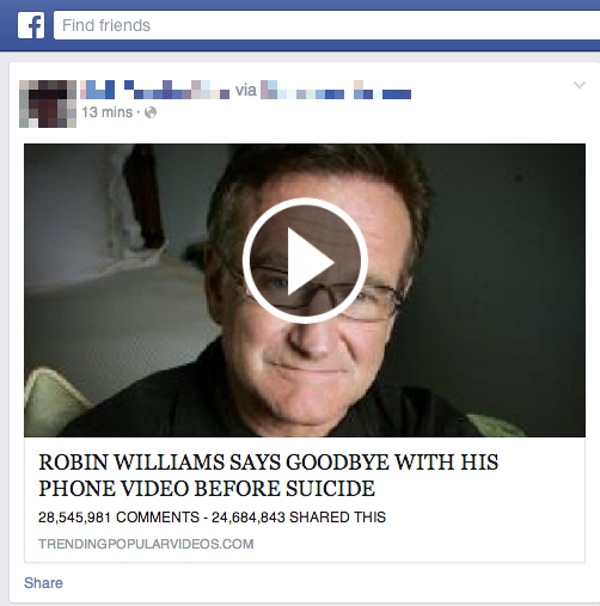
ROBIN WILLIAMS SAYS GOODBYE WITH HIS PHONE VIDEO BEFORE SUICIDE
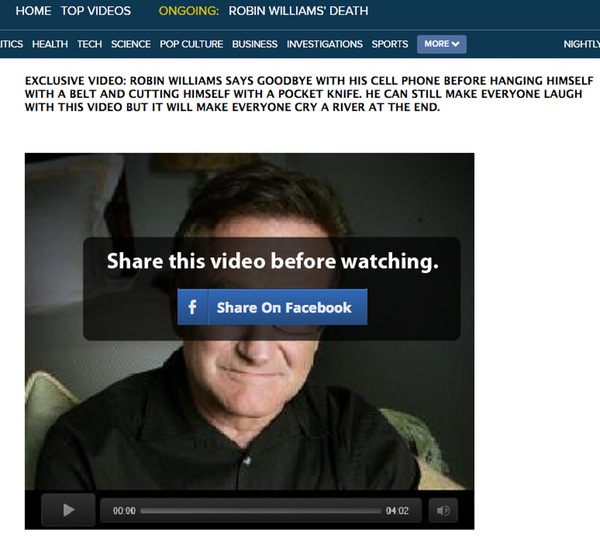
If you click on the link you are taken to a third-party website, which claims to have a phone video made by the award-winning comedian in the minutes before his death:
<blockquote style=”margin: 15px;padding: 15px 15px 5px;border-left: 5px solid #ccc;font-size: 13px;
font-style: normal;font-family: ‘Helvetica Neue’, Helvetica, sans-serif;line-height: 19px;”>
EXCLUSIVE VIDEO: ROBIN WILLIAMS SAYS GOODBYE WITH HIS CELL PHONE BEFORE HANGING HIMSELF WITH A BELT AND CUTTING HIMSELF WITH A POCKET KNIFE. HE CAN STILL MAKE EVERYONE LAUGH WITH THIS VIDEO BUT IT WILL MAKE EVERYONE CRY A RIVER AT THE END.
You would have to be pretty ghoulish to proceed any further, but the truth is that the internet has deadened our sensitivities and made many of us all too willing to watch unpleasant things on our computer screens.
However, the truth is also that no such video is known to exist, and if you click to watch it you will be told that you have to share the link on your Facebook wall – encouraging your friends and family to go through the same process that you have – and ordered to complete an online survey before you may watch the footage.
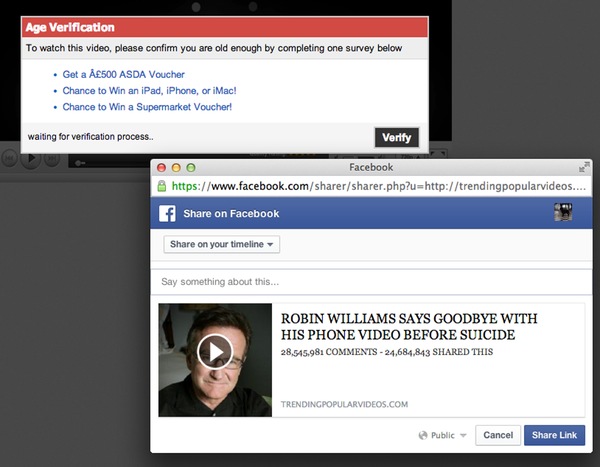
And that’s the point of the scam.
By tricking thousands of people into taking a survey, in the misbelief that they will watch the final moments of a comedy legend whose life ended tragically, the scammers aim to make affiliate cash.
Because every survey that is taken earns them some cents – and the more people they can drive towards the survey (even if they use the bait of a celebrity death video), the more money will end up in their pockets. In other cases, scammers have used such tricks to install malware or sign users up for expensive premium rate mobile phone services.
The scammers have no qualms about exploiting the death of a famous actor and comedian to earn their cash, and give no thought whatsoever to the distressed family he must have left behind.
Always be extremely wary about what links you click on on social networks, and never Share or Like something before you have seen it for yourself, and decided whether it warrants sharing with your online friends.
Because you might not just be putting yourself at risk, you could also be endangering your friends and family.
The post Robin Williams’ last phone call? Sick Facebook video scam exploits celebrity suicide appeared first on We Live Security.
![]()
Russian PM has his Twitter account hacked, announces “I resignâ€
There may be red faces in Red Square, after Russian prime minister Dmitry Medvedev had his Twitter account hacked.
The Russian-language account @MedvedevRussia, which has more than 2.5 million followers, was compromised on Thursday by hackers who posted messages suggesting Medvedev was immediately resigning, and making criticisms of Russia’s president Vladimir Putin.
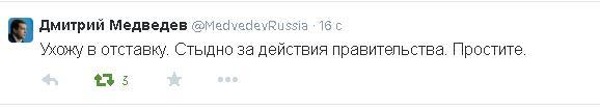
<blockquote style=”margin: 15px;padding: 15px 15px 5px;border-left: 5px solid #ccc;font-size: 13px;
font-style: normal;font-family: ‘Helvetica Neue’, Helvetica, sans-serif;line-height: 19px;”>
I resign. I am ashamed for the actions of the government. I’m sorry
If such an announcement were genuine, of course, it would make headlines and raise eyebrows around the world.
But when the hackers followed up by posting messages on the account proposing the banning of electricity, and that the Russian PM would now pursue a career as a professional freelance photographer, it should have become obvious to everyone that Medvedev was no longer in control of his social media account.
According to media reports, the Twitter account was under the control of hackers for approximately 40 minutes yesterday before control was wrestled back by the PM’s office.
The only silver lining is that whoever hacked the account did not take advantage of the situation to direct some of the Medvedev’s 2.5 million followers to websites which might have contained malware designed to infect their computers.
A hacker calling themselves Shaltay Boltay (“Humpty Dumpty”) has claimed responsibility for the hack. Besides the attack on Medvedev’s Twitter account, Shaltay Boltay has also in the past published internal Kremlin documents and leaked private emails from government officials.
Shaltay Boltay, who describes him or herself as a member of Anonymous on their Twitter profile, posted a message claiming that they they had also managed to compromise the Gmail account and three iPhones belonging to the Russian prime minister. However, whether that is true or not is open to question.
In all likelihood, a busy chap like Dmitry Medvedev isn’t running his Twitter account on his own. Chances are that he has staff in his office who assist him with his social media presence.
And there lies the problem.
Although Twitter has introduced extra levels of protection like two factor authentication to better protect accounts from being hijacked, it doesn’t have good systems in place that work well when more than one person is accessing and posting from a Twitter account.
It would only have taken Medvedev, or one of his staff, to have been careless with their passwords once, or to have used an easy-to-guess password, or to have used the same password elsewhere on the web, for the hackers to have found the weak point necessary to break in and seize control.
Remember – you should always be careful with your passwords. Choose passwords wisely, make sure that they are hard to crack, hard to guess and that you are not using them anywhere else online.
If you find it hard to remember your passwords (which would be understandable if you are following the advice above) use a password management program which can remember them for you, and store them securely behind one master password that you *will* remember.
And once you’re following a strong password policy, ensure that you are always careful where you are entering your passwords, that you never enter them on a third-party site that could be phishing for your credentials, and be sure not to share passwords with friends or colleagues unsafely.
The post Russian PM has his Twitter account hacked, announces “I resign” appeared first on We Live Security.
![]()
‘Biometric’ earbuds invisibly prove it’s you, with no need for passwords
Biometrics such as fingerprints or eye-scans are touted as a replacement for the passwords and PINs we all know and hate – and Intel’s new smartphone earbuds could be the most discreet way of authenticating a user ever.
The earbuds, designed with SMS Audio, harvest heart-rate information using optics inside the ear – monitoring blood pulses and eliminating “noise†according to Business Insider.
The SMS Audio Fitness buds are built for fitness fans, but Intel plans further applications – and is vocal in its opposition to passwords. Other gadgets, such as the Bionym bracelet, already use heart-rate as an identifier: it’s more unique than fingerprints, and the SMS Audio buds could be a step towards a wearable “password†you can almost forget.
“A built-in optical sensor that continuously measures heart rate during intense exercise, states of relaxation and every moment in between – while dynamically removing noise signals caused by body motion and ambient light,†says Intel in a statement.
In the past month, We Live Security reported five major database leaks, usually of passwords.
Passwords: Let there be light?
Gizmodo reports that biometric devices have so far failed to gain widespread acceptance in part because of their bulk – whereas the SMS Audio devices charge themselves using motion, removing the need for extra batteries or chargers.
“In the wearable space, we see a lot of hype. I don’t think the market is ever going to be that big if all we have are just square cellphones taped to your wrist,†says Mike Bell, General Manager of Intel’s New Devices Group.
There are competitors which use the reading – but the Bionym bracelet relies on being charged, unlike Intel’s, which communicates directly with smartphones via the audio jack.
It was actually observed over 40 years ago that ECGs had unique characteristics,†Bionym chief executive Martin said. “The modern research into practical systems goes back about 10 years or so. What we do is ultimately look for the unique features in the shape of the wave that will also be permanent over time. The big breakthrough was a set of signal-processing and machine-learning algorithms that find those features reliably and to turn them into a biometric template.â€
For you, no charge
ESET Senior Research Fellow David Harley discusses the advantages of biometric systems in a We Live Security blog post, “The sad fact is, static passwords are a superficially cheap but conceptually unsatisfactory solution to a very difficult problem, especially if they aren’t protected by supplementary techniques. Biometrics and one-time passwords and tokens are much more secure, especially when implemented in hardware as a two-factor authentication measure.â€
Intel said, “The complexity of keeping digital identities safe grows as mobile applications and devices become a more important part of our daily lives. Intel’s intent is to intensify our efforts dedicated to making the digital world more secure, and staying ahead of threats to private information on mobile and wearable devices.”
TechCrunch reports that, “additional application support†will be added. Intel is reaching out to developers to make apps: “Intel has created an SDK called the Intel IQ Software Kits for any companies that want to use the features that Intel developed while building the circuitry inside the BioSport.â€
The post ‘Biometric’ earbuds invisibly prove it’s you, with no need for passwords appeared first on We Live Security.
![]()
Gamescom 2014: World of Malware?
The gaming industry keeps growing in terms of popularity, and the large population of gamers, and the crowds at Cologne’s Gamescom 2014, represents an opportunity for miscreants to make money. In this blog post, we will explore various attacks specifically tailored to gamers, by starting with trojanized legitimate games, then by exploring some malicious software and targeted attacks against the video games industry. Finally, we will describe some recent exploits found in video games.
Gamescom 2014: Bitcoin Miners
Recent years have seen the introduction of Bitcoin, Dogecoin and other trendy and trending cryptographic currencies. These currencies are created by solving computationally-intensive cryptographic challenges, which require a lot of processing power. As gaming rigs are built with powerful processors and cutting-edge video cards, they can be considered one of the most efficient environments in which to “mine†these digital currencies, with the advantage of being widely spread among the Internet-using population.
In 2013, an employee of the ESEA Counter-Strike league silently introduced a Bitcoin miner into their anti-cheating software, which every member of the league had to install in order to participate. Fortunately the stratagem was uncovered rather quickly, and less than $4,000 worth of bitcoins were ‘earned’ by the malicious employee. More recently, a pirate version of the game ‘WatchDogs’ included a bitcoin mining Trojan which made a profit for the torrent’s author.
Keyloggers and Information Stealers
As the size of the gamer population has increased, some in-game goods have acquired some real monetary value. High-level/high-value characters, in-game currency, legendary items or even hats can be purchased with real money. But when something is worth money, it also means that for some people, it is worth stealing. Consequently, some malicious software focuses on stealing video games credentials. These information stealers are usually distributed under false pretenses, hiding behind so-called “game experience enhancers†or disguised as legitimate tools.
Keyloggers are the most prevalent type of malware in the gaming world, identified as Win32/PSW.OnLineGames by ESET. These programs can be pretty simple but have proven to be very effective at stealing players’ credentials, in order to resell items and characters. So many accounts are compromised that games editors are used to it and have implemented an FAQ and process to handle this situation.
To counter this type of malware, some MMORPG creators, such as Blizzard (who publish World Of Warcraft), have introduced two-factor authentication – and new titles introduced at Gamescom 2014 will do the same. This two-factor authentication takes the form of an electronic device (or a smartphone application) delivering unique six-digit codes that are active and valid only for a limited time before a new code has to be generated.
At the beginning of this year, malicious software named Disker was able to bypass this double-authentication mechanism. Disker appears to be as complex as malicious software that focuses on stealing banking information and it has the ability to steal both the victim’s account credentials and his or her authenticating six-digit passcode.
But as the passcode remains valid only for a short period of time, the attacker has to be behind his keyboard when the information is exfiltrated so as to be able to use it. So Disker implements a way to circumvent this problem: as it leaks the 6-digit passcode to the attacker, it will actually send a wrong passcode to the World Of Warcraft server, preventing the user from logging in. At this point, the victim will almost certainly disable the two-factor authentication in order to enjoy his game. Once this is done, the attacker is no longer restricted to operating within a short period of time.
Targeted Attacks
Players are not the only target in the gaming ecosystem, games companies can also be specifically attacked. For example Kaspersky discovered last year a malware targeting no less than 30 MMORPG game companies. In this case the attack was intended to:
- Deploy malware on gamers’ computers by using the MMORPG update server
- Manipulate in-game currencies
- Steal digital-certificate to create signed-malware, making the malware easier to propagate
- Steal the MMORPG source code to deploy it on rogue servers
Exploits
MMORPGs are not the only targeted type of games, other kinds of multiplayer games are also potential targets. Recently, security researchers Luigi Auriemma and Donato Ferrante have been looking for vulnerabilities in games and game engines.
The results are impressive: they found vulnerabilities in the Source Engine, making any game based on this engine vulnerable, such as the famous Counter-Strike Source, Team Fortress 2 and Left 4 Dead. Those vulnerabilities could be used to execute code on a player’s computer without their knowledge and consent, potentially leading to installation of malware without requiring any action from the user other than his usual gaming activity.
Today, no known malware spreads using vulnerabilities in games but the rising value of in-game goods could motivate malicious people enough to use this kind of attack to spread game-targeted malware.
Conclusion
The emergence of such malware shows that the high value of in-game goods is appealing to bad guys – and the titles shown at Gamescom 2014 will be high-value targets.
The complexity of these types of malware, and the implementation by Blizzard of protective measures similar to those used by banks, indicate that we are at the beginning of an arms race between criminals and the gaming world. In this race, everyone has a role to play, editors by securing players’ accounts adequately, and players by educating themselves about the dangers, the existing solutions, and how to behave in order to enjoy safer gaming.
The post Gamescom 2014: World of Malware? appeared first on We Live Security.
![]()
NCSC Spearphishing Security Advisory
Original release date: August 14, 2014
New Zealand’s National Cyber Security Centre (NCSC) has released Security Advisory NCSC-C-2014-17 which highlights a spearphishing campaign targeting government employees. The NCSC provides enhanced cybersecurity services to the New Zealand Government and private sector organizations against cybersecurity threats.
This product is provided subject to this Notification and this Privacy & Use policy.
Apple Releases Security Update for Safari
Original release date: August 14, 2014
Apple has released security updates for Safari to address vulnerabilities which could allow an attacker to execute arbitrary code or cause an unexpected application termination.
Updates include Safari 6.1.6 and Safari 7.0.6 for OS X Lion v10.7.5, OS X Lion Server v10.7.5, OS X Mountain Lion v10.8.5 and OS X Mavericks v10.9.4.
Users and administrators are encouraged to review Apple security update HT6367 and apply the necessary updates.
This product is provided subject to this Notification and this Privacy & Use policy.
Phone scams: card fraud with that steak, Sir?
A new telephone scam has been targeting upscale restaurants in London, with “convincing†scammers calling restaurant staff and tricking them into believing there’s a problem with their payment system – according to a report issued by Financial Fraud Action. The scammers have targeted restaurants in affluent areas such as the West End and Twickenham.
The fraudsters give staff a phone line to call for customers to make payments, the Telegraph reports. Transactions are then funneled through the fraudulent phone line – restaurant owners have been warned to phone banks on a number known to be legitimate to check before changing payment methods. Katy Worobec, Director of Financial Fraud Action UK, said “It’s important that restaurant owners are alert.  Fraudsters can sound very professional – don’t be fooled.”
Phone scam: ‘Classic social engineering’
To customers, Financial Fraud Action said, “If you receive any calls from your bank claiming there’s a problem with payments, make sure you phone them on an established number to confirm the request is genuine. In addition, always wait five minutes to ensure the line is clear, as fraudsters will sometimes try to stay on the phone line and pretend to be your bank.” The tactics used are variations of those in many current phone scams. In the common ‘courier scam’ used to obtain cards and PINs, the caller waits on the phone and pretends to be a new connection after the caller dials.
Phone scams: Old tricks
ESET senior researcher David Harley says, “The ‘staying on the phone line’ gambit is worth mentioning: it’s certainly been used a lot in the context of other scams.†The tactic works simply because few users take measures to ensure the caller is not waiting – and when they dial, they are still connected. All that happens is the fraudster hears a series of beeps. Harley suggests ‘interrupting’ the call by hanging up and dialing another number – or calling on a different phone.
Action Fraud said,â€When the restaurant calls the phone number, the fraudster asks to speak with the paying customer and then goes through their security questions. Once sufficient security details have been obtained from the customer, the fraudster will instruct the restaurant to put the transaction through.†The fraudster then subsequently calls the customer’s bank – usually within five minutes – and attempts to transfer funds, the Daily Mail said.
The scam is not new – and several elements are “classic social engineering†says ESET Senior Research Fellow David Harley – but it has spiked in the past six weeks, “Certainly there’s a problem with the concept of answering security questions over the phone unless the bank or other caller has already authenticated themselves to you,†Harley says.
Harley says the key to avoiding such scams is not to place trust in unknown callers. If unsure, hang up, and call back on a known number. “In this case, a restaurant that falls for this has clearly failed to verify the credentials of the ‘bank’ and a customer who goes along with it has put too much trust in the restaurant. The ‘security questions’ must persuade the customer to give quite a lot of information away if they have any hope of persuading the bank to make the fraudulent transaction over the phone. One would hope…â€
The post Phone scams: card fraud with that steak, Sir? appeared first on We Live Security.
![]()
Will web browsers turn cars lethal?
Two researchers have launched a petition to change how car companies and technology companies work together – with a new villain: in-car web browsers.
“We request that you unite with us in a joint commitment to safety between the automotive and cyber security industries,†the researchers say via Change.org.
A paper presented at Black Hat, shows a danger crossing the line from “proof of concept†to reality. The researchers point out that while hacking a car to give total control is extremely hard, it’s easier to, for instance, attack individual systems, such as commuications or navigation, both of which could be lethal.
Car code is complex, and often bespoke – which means attacks tend towards the level of disabling locks, or affecting electric windows, rather than outright destruction. Even Bluetooth – often hyped as the Achilles’ Heel.
Internet of Things: Car crash ahead?
“Bluetooth has become ubiquitous within the automotive spectrum, giving attackers a reliable entry point to test,†they write. But hacks would be of the level of adding an unauthorized device – not outright control.
When CNN Money devotes a section to the year’s “most hackable carsâ€, automotive security is clearly a real issue – a prize won by the Cadillac Escalade and 2014 Toyota Prius incidentally.
Charlie Miller and Chris Valasek in their paper A Survey of Remote Automotive Attack Surfaces conclude that the danger of “hackable†cars is expanding – but is about to grow rapidly, as web browsers are added to cars.
“Once you add a web browser to a car, it’s open. I may not be able to write a Bluetooth exploit, but I know I can exploit web browsers.” The recent reported hack against the Tesla Model S relied on its connected control panel.
A SlashDot user claims to have found a hidden port on the Tesla Model S, and used it to prove the car ran a modified version of Firefox.
Nick Bagot, Motoring Editor of the Mail on Sunday says, “Web browser obviously considerable safety issues – and it’s questionable why they’re needed. The inclusion of browsers in cars may well be to do with the convenience of advertising, and lucrative tie-ups with car brands and particular browsers, than it is for delivering value to the consumer.â€
“Google is, primarily, an advertising company. Google products are built to feed into Adwords. Self-driving cars are an incredible technology – but what is it for?â€
Safety first?
Car technology ignites passions from many sides. Last year a U.S senator urged auto manufacturers to change – and his open letter ignited a spate of commentary, with Market Oracle describing the crime as “cyberjackingâ€, and pointing out that the average family car contains 100 million lines of computer code, and that software can account for up to 40% of the cost of the vehicle, according to researchers at the University of Wisconsin-Madison.
Most in-car innovations have a clear point – car cameras are part of the technology revolution, but increase safety. Which Magazine writes “The importance of having these in-car cameras is becoming more obvious each day, with the devices not only providing UK drivers with an independent witness – but also as we see awareness of the product increase, we hope to see the road safety standards improve and fraudulent crashes and claims decline.
The importance of having these in-car cameras is becoming more obvious each day, with the devices not only providing UK drivers with an independent witness- but also as we see awareness of the product increase, we hope to see the road safety standards improve and fraudulent crashes and claims decline.â€
Other innovations bring less clear benefits, reports The Register. “The problem is that cars are becoming more heavily computerized and that leads to more networking so the driver and passengers can get access to up-to-date information while on the move: most newish cars have a Bluetooth system hidden inside, a connection to the cellular data network, and so on,†the site said.
On the researchers’ page, I am the Cavalry, they say, Modern cars are computers on wheels and are increasingly connected and controlled by software. Dependence on technology in vehicles has grown faster than effective means to secure it.
The post Will web browsers turn cars lethal? appeared first on We Live Security.
![]()