Home-based jobs are attractive to people who are looking to supplement their regular or retirement income, those who want part-time employment, or those who want to save money on child care or gas. Many people have dreams of being entrepreneurs and working independently of traditional businesses. Cybercrooks take advantage of this to create fake offers for work-from-home opportunities.
Home-based jobs are attractive to people who are looking to supplement their regular or retirement income, those who want part-time employment, or those who want to save money on child care or gas. Many people have dreams of being entrepreneurs and working independently of traditional businesses. Cybercrooks take advantage of this to create fake offers for work-from-home opportunities.
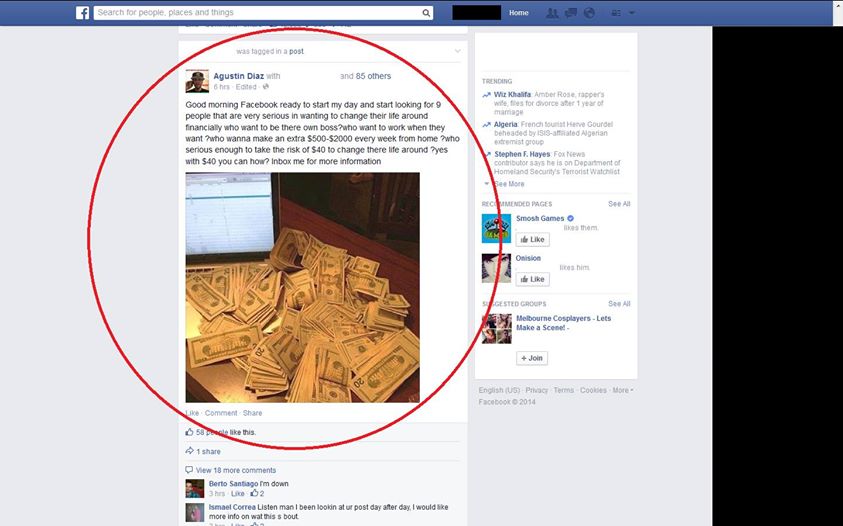
Sharp-eyed avast! Facebook fan, Timothy B., shared a post that he received for a work-from-home scam.
The post says,
Good morning Facebook ready to start my day and start looking for 9 people that are very serious in wanting to change their live around financially who want to be there own boss?who want to work when they want ?who wanna make an extra $500-$2000 every week from home ?who serious enough to take the risk of $40 to change there life around ?yes with $40 you can how? Inbox me for more information
Work-at-home and get-rich-quick schemes have been around for a long time, first appearing in people’s real mailboxes, on TV, and in magazine advertisements. Cybercrooks have created variations of this scam to harvest email addresses and contact lists from Facebook. Social networking makes it easy to create fake profiles and identities quickly.
The grammatically-challenged swindler from Timothy B.’s newsfeed entices potential victims with the ease and flexibility of working from home whenever they want. The message promises big earnings, and all you need to do is make a $40 investment to find out how. This scammer will most likely try to get you to wire money and then collect your personal information.
Warning signs of a work-from-home scam
- No business name or contact address – No legitimate company will advertise for jobs without stating their name, brand identity and physical contact address.
- You’re required to pay a fee for additional information. Legitimate employers don’t charge a fee to hire you or to get you started. Don’t send money for directories or start-up kits.
- Promises of exceptional earnings.
- Claims that no experience is necessary or resume is required.
- Asks for personal information like a Social Security or bank account number over the Internet.
How to report a scam
File a report with the Internet Crime Complaint Center – In order to file a report, you’ll need to provide the following information:
- Your name, mailing address, and telephone number.
- The name, address, telephone number, and web address, if available, of the individual or organization you believe defrauded you.
- Specific details on how, why, and when you believe you were defrauded.
Report the company to the Better Business Bureau (BBB) – If you have a company name or web address, use the BBB’s search tool to find out if there have been complaints filed. You can file your own complaint online.
Report spam on Facebook – The best way to report abusive content or spam on Facebook is by using the Report link that appears near the content itself. To report something someone posted on your Timeline:
- 1. In the top right of the post, click the down-pointing arrow
- 2. Select I don’t like this post
- 3. Select I think it shouldn’t be on Facebook and follow the on-screen instructions
Thank you for using avast! Antivirus and recommending us to your friends and family. For all the latest news, fun and contest information, please follow us on Facebook, Twitter and Google+. Business owners – check out our business products.