Mandriva Linux Security Advisory 2014-174 – The mod_headers module in the Apache HTTP Server 2.2.22 allows remote attackers to bypass RequestHeader unset directives by placing a header in the trailer portion of data sent with chunked transfer coding. NOTE: the vendor states this is not a security issue in httpd as such. The updated packages have been upgraded to the latest 2.2.29 version which is not vulnerable to this issue.
Monthly Archives: September 2014
Red Hat Security Advisory 2014-1162-01
Red Hat Security Advisory 2014-1162-01 – Red Hat JBoss Enterprise Application Platform 6 is a platform for Java applications based on JBoss Application Server 7. It was found that the fix for CVE-2012-5783 was incomplete: the code added to check that the server host name matches the domain name in a subject’s Common Name field in X.509 certificates was flawed. A man-in-the-middle attacker could use this flaw to spoof an SSL server using a specially crafted X.509 certificate. It was discovered that the HttpClient incorrectly extracted host name from an X.509 certificate subject’s Common Name field. A man-in-the-middle attacker could use this flaw to spoof an SSL server using a specially crafted X.509 certificate.
Ubuntu Security Notice USN-2340-1
Ubuntu Security Notice 2340-1 – Tavis Ormandy discovered that the formail tool incorrectly handled certain malformed mail headers. An attacker could use this flaw to cause formail to crash, resulting in a denial of service, or possibly execute arbitrary code.
Red Hat Security Advisory 2014-1163-01
Red Hat Security Advisory 2014-1163-01 – Red Hat JBoss Enterprise Application Platform 6 is a platform for Java applications based on JBoss Application Server 7. It was found that the fix for CVE-2012-5783 was incomplete: the code added to check that the server host name matches the domain name in a subject’s Common Name field in X.509 certificates was flawed. A man-in-the-middle attacker could use this flaw to spoof an SSL server using a specially crafted X.509 certificate. It was discovered that the HttpClient incorrectly extracted host name from an X.509 certificate subject’s Common Name field. A man-in-the-middle attacker could use this flaw to spoof an SSL server using a specially crafted X.509 certificate.
Red Hat Security Advisory 2014-1161-01
Red Hat Security Advisory 2014-1161-01 – Red Hat Enterprise Virtualization Manager is a visual tool for centrally managing collections of virtual servers running Red Hat Enterprise Linux and Microsoft Windows. This package also includes the Red Hat Enterprise Virtualization Manager API, a set of scriptable commands that give administrators the ability to perform queries and operations on Red Hat Enterprise Virtualization Manager.
Red Hat Security Advisory 2014-1143-01
Red Hat Security Advisory 2014-1143-01 – The kernel packages contain the Linux kernel, the core of any Linux operating system. An out-of-bounds memory access flaw was found in the Linux kernel’s system call auditing implementation. On a system with existing audit rules defined, a local, unprivileged user could use this flaw to leak kernel memory to user space or, potentially, crash the system.
WordPress Releases Security Update
Original release date: September 04, 2014
WordPress 3.9.2 has been released to address multiple vulnerabilities, one of which could allow a possible denial of service issue in PHP’s XML processing. WordPress 3.7.3 or 3.8.3 users will be updated to 3.7.4 or 3.8.4. Users operating older, unsupported versions of WordPress are encouraged to upgrade to 3.9.2.
US-CERT recommends users and administrators review the WordPress Maintenance and Security Release blog  and apply the necessary updates.
This product is provided subject to this Notification and this Privacy & Use policy.
Now your LinkedIn account can be better protected than ever before
Let’s be honest. LinkedIn doesn’t have the most spotless record when it comes to security and privacy.
In the past, LinkedIn has been hacked (Who can forget when 6.5 million stolen LinkedIn passwords were found on a Russian web server?)
Or maybe you recall hearing about how LinkedIn was scooping up the contents of iOS calendars, including sensitive information such as confidential meeting notes and call-in numbers, and transmitting them unencrypted in plaintext.
Or how about the time that LinkedIn controversially introduced (and then rapidly withdrew) a widget that meddled with the standard iOS Mail app, with the side effect of compromising the entire security of your email inbox, allowing LinkedIn to read every message you sent or received *outside* of the site?
I could go on, but you get the idea – and, anyway, I like to think that companies can learn. And, on this occasion, LinkedIn has done something that should be applauded.
In a blog post published yesterday, LinkedIn explained that it was introducing three new tools which go some way to boosting security, and granting members more control over their data.
First up, you can now check where (if anywhere) else you are currently logged into LinkedIn.
It’s all very well being logged into your LinkedIn account at home, but are you sure you logged off in the office? Alternatively, is it possible that a hacker has stolen your password and is currently messing around with your LinkedIn account on the other side of the world?
Now there’s an easy way to check.
Go to your settings and click on See where you are logged in to view a complete list of the devices that you are signed into the site.
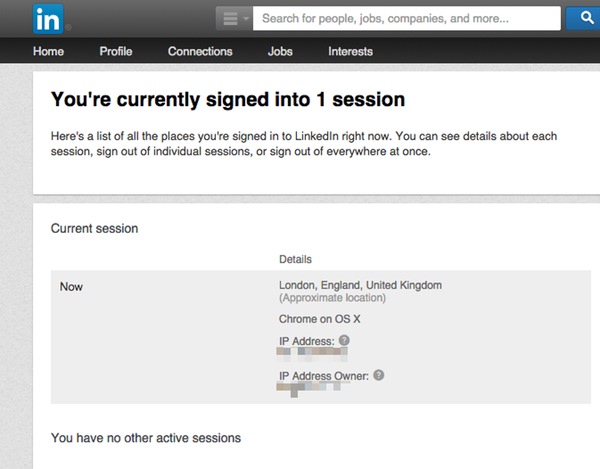
In the above screenshot, you can see that I have nothing to fear. There’s only one computer currently logged into my LinkedIn account, and I feel fairly comfortable that that’s me.
But if there had been additional sessions displayed, I would have been able check what browser and operating system is being used in each case, and the approximate location of the activity. Then, if I chose, logging them out remotely is just a mouse click away.
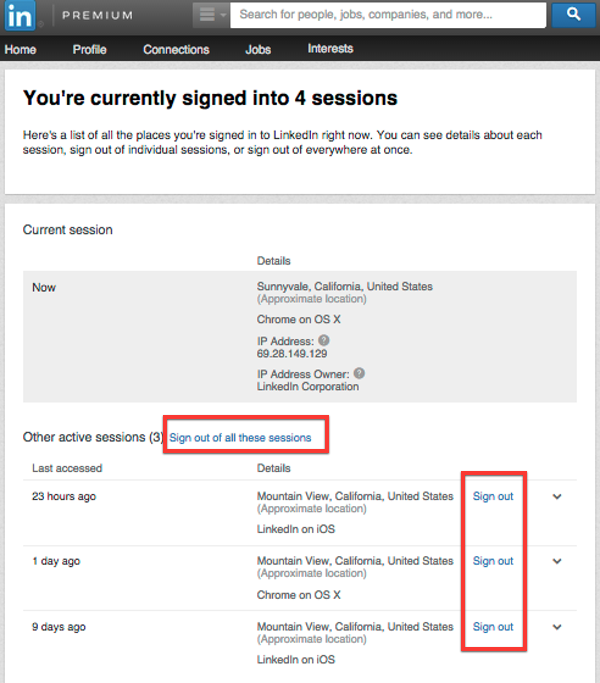
And, of course, if the other sessions were at locations or on devices I didn’t recognise then that might be a good time to consider changing my password and enabling LinkedIn’s two-factor authentication.
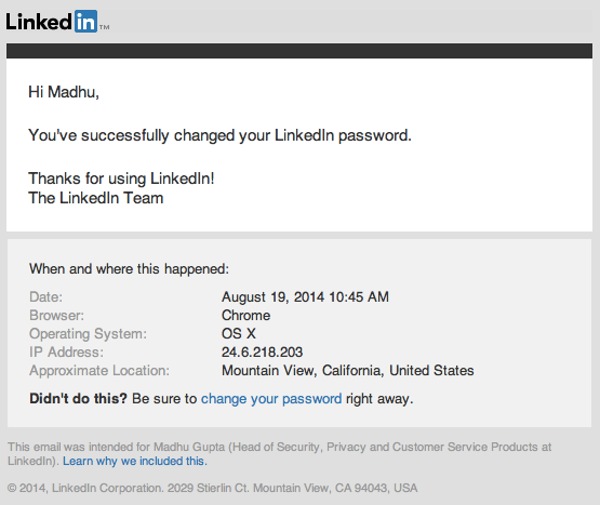
Next up, LinkedIn is offering more information to users in its password change email notifications – telling them, for the first time, when and where an account’s password change occurred.
Finally, LinkedIn has taken a leaf out of Facebook and Google’s book and provided a way for users to easily export all of the data that the site stores about you, by requesting your data archive.
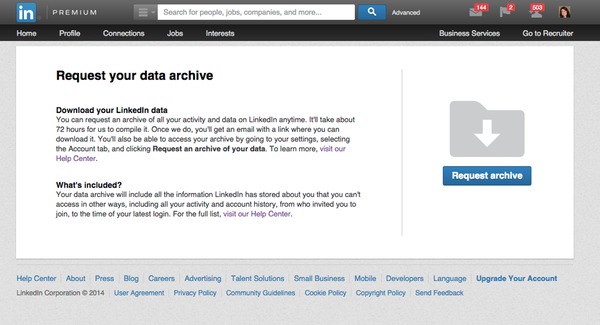
Once requested, it takes LinkedIn approximately 72 hours to collate the data that it holds on you, but never fear because you will be sent an email once the data is available for download.
None of these new features can really be considered rocket science, but it’s good to see LinkedIn introduce them and putting more power into the hands of its millions of users, who would feel pretty dreadful if their account was ever compromised.
It’s essential to keep your LinkedIn account out of the hands of fraudsters and internet criminals, precisely because it is the “business social network”.
In the past hackers have taken over accounts and posted poisoned links, and it’s easy to imagine the fraudulent behaviour that could take place if a worker’s colleagues and industry peers believed that it was John Doe communicating with them rather than a malicious attacker.
Of course, there’s no point to these tools if they aren’t actually used in the way that they’re designed.
Read LinkedIn’s blog, ensure that you’re familiar with these new features and the site’s two-factor authentication facility, and you will be better placed to protect both yourself and your fellow workers.
The post Now your LinkedIn account can be better protected than ever before appeared first on We Live Security.
![]()
IFA 2014: Huawei phablet has ‘iPhone-like’ fingerprint ID
Another major phone brand has added biometric security to a flagship smartphone as Huawei unveiled the ultra-thin Mate P7, complete with a rather unique fingerprint scanner, at Berlin’s IFA 2014 show.
The ultra-slim 6-inch phablet device uses an interesting biometric scanner – just like TouchID on the iPhone 5S, the user simply places a digit on the scanner, according to Tech Radar’s report.
This marks it out from the scanners found on the Samsung Galaxy S5 and HTC One Max, where the user has to swipe a digit over the scanner in a certain direction according to Digital Trends.
IFA 2014: Unique ‘iPhone-like’ scanner
Huawei is the largest telecoms equipment maker in the world. Biometrics has been one of the big tech trends for 2014, with devices as diverse as an iris-scanning smartwatch and earbuds which ‘read’ a wearer’s heartbeat using flashes of light in development, as reported by We Live Security.
Fingerprint scanners – and other biometric scans – have been predicted as “likely to become commonplace†in smartphones by MIT’s Technology Review.
Pocket-Lint says that the Ascend Mate P7 is a high-end handset with a polished metal finish just like the iPhone 5S, and a high-quality forward-facing 5-megapixel camera for “selfies.”
Digital Trends says, “Most importantly though, the Mate 7 has a fingerprint scanner that works exactly like the one on the iPhone 5S. Instead of having to swipe your finger across it like you do with Samsung’s Galaxy S5, you can simply place your digit on the scanner to unlock your phone and perform other tasks. The fingerprint sensor is located on the back of the phone below the camera.â€
No swiping required
The early part of this week has seen companies such as Samsung unveil new gadgets at IFA 2014 – but the show floor proper will open tomorrow, with more biometric gadgets expected. Read the report on We Live Security this week.
Smartphones are increasingly being used both in the home and the workplace as a security measure in their own right, with mobile workers accessing networks via “two factor authentication†software such as ESET Secure Authentication.
Adding fingerprint security to the handsets provides another layer of security for data.
The post IFA 2014: Huawei phablet has ‘iPhone-like’ fingerprint ID appeared first on We Live Security.
![]()
Feared Home Depot Breach Sparks More Interest in Backoff PoS Malware
Security experts are digging into point-of-sale malware, Backoff in particular, as speculation rages on about how hackers pulled off the Home Depot data breach.