Red Hat Security Advisory 2014-1371-01 – Network Security Services is a set of libraries designed to support the cross-platform development of security-enabled client and server applications. Netscape Portable Runtime provides platform independence for non-GUI operating system facilities. A flaw was found in the way NSS parsed ASN.1 input from certain RSA signatures. A remote attacker could use this flaw to forge RSA certificates by providing a specially crafted signature to an application using NSS.
Monthly Archives: October 2014
Fedora EPEL 6 Security Update: php-ZendFramework-1.12.9-1.el6
Resolved Bugs
1151279 – php-ZendFramework: various flaws [epel-6]
1151276 – CVE-2014-8088 php-ZendFramework: null byte issue, connect to LDAP without knowing the password (ZF2014-05)
1151277 – CVE-2014-8089 php-ZendFramework: SQL injection issue when using the sqlsrv PHP extension (ZF2014-06)<br
Contains fixes for two security relevant bugs:
* “ZF2014-05: Anonymous authentication in ldap_bind() function of PHP, using null byte” (http://framework.zend.com/security/advisory/ZF2014-05)
* “ZF2014-06: SQL injection vector when manually quoting values for sqlsrv extension, using null byte” (http://framework.zend.com/security/advisory/ZF2014-06)
Fedora EPEL 7 Security Update: php-ZendFramework2-2.3.3-1.el7
Resolved Bugs
1151281 – php-ZendFramework2: various flaws [epel-7]
1151276 – CVE-2014-8088 php-ZendFramework: null byte issue, connect to LDAP without knowing the password (ZF2014-05)
1151277 – CVE-2014-8089 php-ZendFramework: SQL injection issue when using the sqlsrv PHP extension (ZF2014-06)<br
Security release
* ZF2014-05, which mititages null byte poisoning of the password provided for LDAP authentication, thus prevening unauthorized LDAP binding. This corrects for unpatched versions of PHP (versions 5.5.11 and below, 5.4.27 and below, and any prior releases).
* ZF2014-06, which mitigates null byte poisoning of quoted SQL values provided to the sqlsrv extension, thus preventing a potential SQL injection vector.
SAP BusinessObjects Explorer 14.0.5 Information Disclosure
SAP BusinessObjects Explorer version 14.0.5 does not validate the user defined inputs of parameter CMS name, which consists of a host name and port number. This can be used to perform a port scan within the network range where the BusinessObject Explorer server is located. This vulnerability could be triggered as unauthenticated user.
Fedora EPEL 6 Security Update: getmail-4.46.0-2.el6
Resolved Bugs
1149728 – CVE-2014-7273 CVE-2014-7274 CVE-2014-7275 getmail: various flaws related to IMAP4-over-SSL certificate validation<br
update to 4.46.0
SAP BusinessObjects Explorer 14.0.5 Cross Site Flashing
SAP BusinessObjects Explorer 14.0.5 suffers from a cross site flashing vulnerability. It is possible to directly load and display the com_businessobjects_polestar_bootstrap.swf Flash file and specify a configUrl. This requires the victim to be logged and the attacker needs to know the /webres/ URL, which is known as soon as the attacker is in possession of valid credentials. The configuration file specified in the configURL parameter may reside on a foreign host. The configuration file itself may contain URLs of further Flash files residing on a foreign domain. If successful, the victim loads foreign Flash files, which leads to Cross Site Flashing.
The Ebola virus becomes the latest bait used by fraudsters
The Spanish Civil Guard has warned via Twitter of a number of Ebola-related hoaxes that have appeared over recent days.
Once again, WhatsApp has become the main channel for such scams, which include bogus reports of new cases of Ebola or the canceling of classes at the CEU San Pablo University in Madrid due to a possible infection.
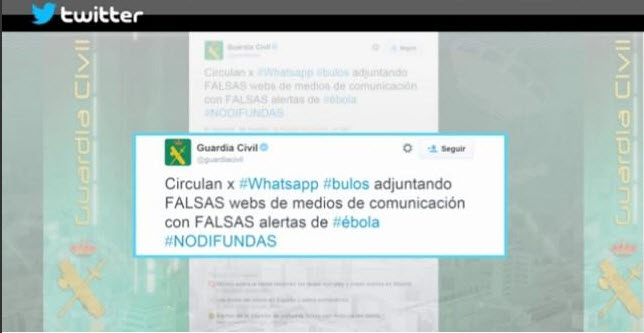
Hackers often exploit such situations for financial gain, and it was never in doubt that the first confirmed case of Ebola in Spain would give rise to these types of scams.
The Spanish Civil Guard have asked users to help avoid generating panic by not distributing these messages. They also encourage people to get their information through what they refer to as “serious channels of communication.”
The post The Ebola virus becomes the latest bait used by fraudsters appeared first on MediaCenter Panda Security.
Week in security: Dubai Police use Google Glass facial recognition, Bugzilla gets bugged and ‘Unpatchable’ USB exploit lands on GitHub
This week in security, we covered a full range of privacy and malware, with controversial plans to equip police officers with facial recognition packed Google Glass in Dubai, and the BadUSB malware finding its way on to GitHub.
The post Week in security: Dubai Police use Google Glass facial recognition, Bugzilla gets bugged and ‘Unpatchable’ USB exploit lands on GitHub appeared first on We Live Security.
![]()
Dairy Queen hit by card data stealing malware
Dairy Queen has become the latest company to be hit by payment card stealing malware, reports the Wall Street Journal. The breach is said to have affected 395 of its 4,500 American locations.
The post Dairy Queen hit by card data stealing malware appeared first on We Live Security.
![]()