-----BEGIN PGP SIGNED MESSAGE----- Hash: SHA1 Due to a hardware replacement, we'll have to move the existing CentOS Bug tracker solution (aka https://bugs.centos.org) to a new node. Migration is scheduled for Friday November 7th, 1:00 pm UTC time. You can convert to local time with $(date -d '2014-11-7 13:00 UTC') The expected "downtime" is estimated to ~30 minutes , time needed to update/propagate updated dns A record + last mysql dump/restore on the new node. Thanks for your comprehending and patience. on behalf of the Infra team, - -- Fabian Arrotin The CentOS Project | http://www.centos.org gpg key: 56BEC54E | twitter: < at >arrfab -----BEGIN PGP SIGNATURE----- Version: GnuPG v2.0.22 (GNU/Linux) iEYEARECAAYFAlRaN6oACgkQnVkHo1a+xU5t2wCfaEsAFNKx88yh6HMk1D2SLue7 YTUAnjUi56KESP4GwaGxNNI3k9MyHbvH =2yPP -----END PGP SIGNATURE-----
Monthly Archives: November 2014
Fedora 21 Security Update: fedup-0.9.0-2.fc21
Resolved Bugs
1159292 – Machine automatically shutdown during upgrade in less than 15 minutes
1038413 – fedup stage2 keymap will always be US again for F20-F21 due to anaconda not writing vconsole.keymap kernel parameter any more (#1035316)
1153816 – Fedup needs to support upgrading into a Productized Fedora 21
1066679 – CVE-2013-6494 fedup: /var/tmp/fedora-upgrade temporary directory creation vulnerability<br
This update works around a serious problem in Fedora 21 Beta which makes systems automatically shut down 15 minutes into the upgrade.
Other improvements:
* Adds `–product=PRODUCT` flag, required for upgrades to F21
* Uses host’s config files in `upgrade.img`, which should fix various upgrade problems (e.g. incorrect keyboard layout when unlocking disks due to missing `vconsole.conf`)
* Logging improvements: complete upgrade log should appear in system journal
Fedora 21 Security Update: curl-7.37.0-9.fc21
Resolved Bugs
1154941 – CVE-2014-3707 curl: incorrect handle duplication after COPYPOSTFIELDS<br
– fix handling of CURLOPT_COPYPOSTFIELDS in curl_easy_duphandle (CVE-2014-3707)
Fedora 21 Security Update: aircrack-ng-1.2-0.5rc1.fc21
Resolved Bugs
1159812 – CVE-2014-8321 CVE-2014-8322 CVE-2014-8323 CVE-2014-8324 aircrack-ng: multiple vulnerabilities
1159813 – CVE-2014-8324 CVE-2014-8321 CVE-2014-8323 CVE-2014-8322 aircrack-ng: multiple vulnerabilities [fedora-all]
984478 – aircrack-ng-1.2-rc1 is available<br
Security fix for CVE-2014-8321, CVE-2014-8322, CVE-2014-8323, CVE-2014-8324
Your home network is at risk of cybersecurity attacks
Router vulnerabilities and weak passwords allow cybercrooks easy access to your home network
That little router box provided by your ISP or that you bought at Radio Shack and forgot about, is a weak link in your Internet-connected household. Many homes in the United States use a wireless router to connect multiple devices, but unsecured routers can create an easy access point for hackers.
Think for a second – do you know what your wifi router password is? Did you know that your wireless router even has a password? If you are not sure, you are not alone.
What do you have to lose?
Only everything on your computer! That includes banking or financial information, personal information, browsing history, and photos.
Why is this an issue now?
â€Today’s router security situation is very reminiscent of PCs in the 1990s, with lax attitudes towards security combined with new vulnerabilities being discovered every day creating an easily exploitable environment, ” said Vince Steckler, chief executive officer of Avast. “The main difference is people have much more personal information stored on their devices today than they did back then.”
We did a study of this issue and found that 4 out of 5 Internet-connected households in the U.S. are at risk of getting attacked through their wireless router. And 16 out of 100 surveyed said they have already been victimized by hackers. T
The problem – PASSWORDS.
Avast found that more than half of all routers are poorly protected by default or easily-hacked password combinations. When you check yours, this could be what you find:
- admin/admin
- admin/password
- admin/<no-password>
The 25% of consumers we surveyed that are using a “unique†password use their address, name, phone number, street name, or other easily-guessed terms as their passwords. Not too much better…
What is the risk?
One of the biggest risks on any wifi network is DNS hijacking. This happens when malware gets in your unprotected router and sneakily redirects you from a known site, such as your bank’s website, to a fake site that looks just like the real thing. When you log in, cyberthieves capture your login credentials and then use them to access the real site. Scary stuff.
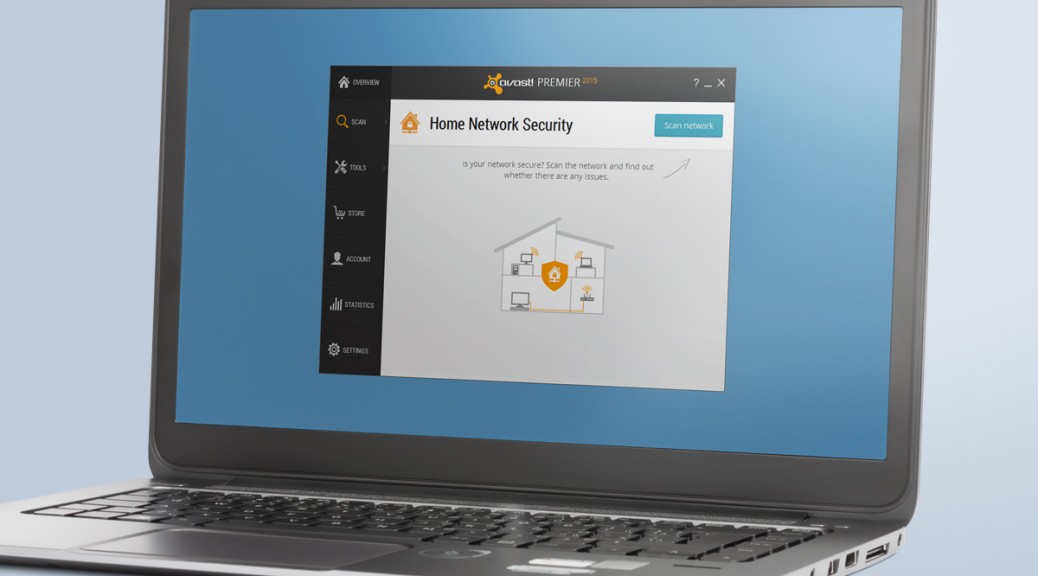
Avast 2015 reacts to home network vulnerabilities
To address these issues, Avast recently introduced Avast 2015, which includes the world’s first Home Network Security Solution that protects users from home network threats including DNS hijacking and weak passwords.
The Home Network Security Solution is available in free and paid versions of Avast. Get it at www.avast.com.
Avast Software’s security applications for PC, Mac, and Android are trusted by more than 200-million people and businesses. Please follow us on Facebook, Twitter and Google+.
Packet Storm New Exploits For October, 2014
This archive contains all of the 161 exploits added to Packet Storm in October, 2014.
FreeBSD Security Advisory – ftp Remote Command Execution
FreeBSD Security Advisory – A malicious HTTP server could cause ftp(1) to execute arbitrary commands. When operating on HTTP URIs, the ftp(1) client follows HTTP redirects, and uses the part of the path after the last ‘/’ from the last resource it accesses as the output filename if ‘-o’ is not specified. If the output file name provided by the server begins with a pipe (‘|’), the output is passed to popen(3), which might be used to execute arbitrary commands on the ftp(1) client machine.
FreeBSD Security Advisory – Kernel Stack Disclosure
FreeBSD Security Advisory – When setlogin(2) is called while setting up a new login session, the login name is copied into an uninitialized stack buffer, which is then copied into a buffer of the same size in the session structure. The getlogin(2) system call returns the entire buffer rather than just the portion occupied by the login name associated with the session. An unprivileged user can access this memory by calling getlogin(2) and reading beyond the terminating NUL character of the resulting string. Up to 16 (FreeBSD 8) or 32 (FreeBSD 9 and 10) bytes of kernel memory may be leaked in this manner for each invocation of setlogin(2). This memory may contain sensitive information, such as portions of the file cache or terminal buffers, which an attacker might leverage to obtain elevated privileges.
HelpDEZk 1.0.1 Unrestricted File Upload
HelpDEZk version 1.0.1 suffers from a remote unrestricted file upload vulnerability.
Forma Lms 1.2.1 Cross Site Scripting
Forma Lms version 1.2.1 suffers from a cross site scripting vulnerability.