Debian Linux Security Advisory 3090-1 – Multiple security issues have been found in Iceweasel, Debian’s version overflows, use-after-frees and other implementation errors may lead to the execution of arbitrary code, the bypass of security restrictions or denial of service.
Monthly Archives: December 2014
Red Hat Security Advisory 2014-1959-01
Red Hat Security Advisory 2014-1959-01 – The kernel packages contain the Linux kernel, the core of any Linux operating system. It was found that the permission checks performed by the Linux kernel when a netlink message was received were not sufficient. A local, unprivileged user could potentially bypass these restrictions by passing a netlink socket as stdout or stderr to a more privileged process and altering the output of this process.
Ubuntu Security Notice USN-2432-1
Ubuntu Security Notice 2432-1 – Siddhesh Poyarekar discovered that the GNU C Library incorrectly handled certain multibyte characters when using the iconv function. An attacker could possibly use this issue to cause applications to crash, resulting in a denial of service. This issue only affected Ubuntu 10.04 LTS and Ubuntu 12.04 LTS. Adhemerval Zanella Netto discovered that the GNU C Library incorrectly handled certain multibyte characters when using the iconv function. An attacker could possibly use this issue to cause applications to crash, resulting in a denial of service. Various other issues were also addressed.
Debian Security Advisory 3088-1
Debian Linux Security Advisory 3088-1 – Paolo Bonzini of Red Hat discovered that the blit region checks were insufficient in the Cirrus VGA emulator in qemu-kvm, a full virtualization solution on x86 hardware. A privileged guest user could use this flaw to write into qemu address space on the host, potentially escalating their privileges to those of the qemu host process.
Fake free codes scam affects PSN and Steam users
Some webpages are giving away free codes for Playstation Network and Steam but, are they reliable?
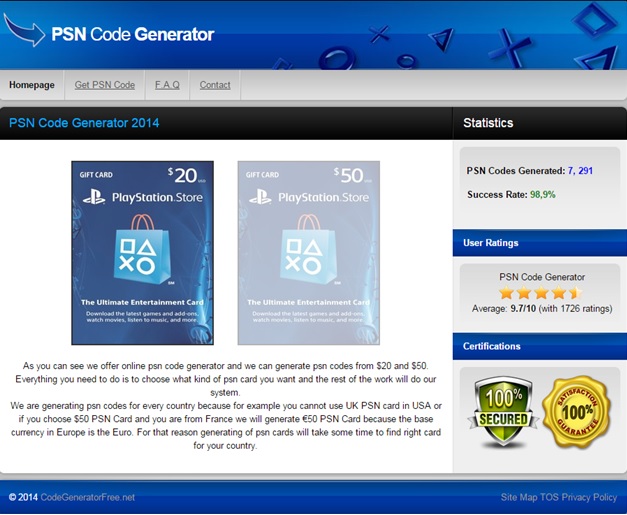
At Avast we discovered a lot of webpages offering free codes, with a value from $20 to $50, for Playstation Network and Steam, two of the most important internet-based digital distribution platforms. Those webpages look very suspicious so we decided to analyze them.
We chose one of those webpages and followed all the steps required in order to get our “free code” for Playstation Network or Steam.
After a first look at the main page, we found some suspicious items. To prove how trustworthy the transaction is, the webpage placed two security “certifications” in a visible location, but as we discovered, no security companies are associated with those certifications. They are completely fake!
Also, there’s a label with user ratings (4 ½ stars!), but we cannot rate the webpage; it’s just an image. Both fake images make the users think that they are in a safe and reliable website.
What happens when we click on a gift card? Are we going to receive the code?
The answer is no.
Let’s see what’s next:
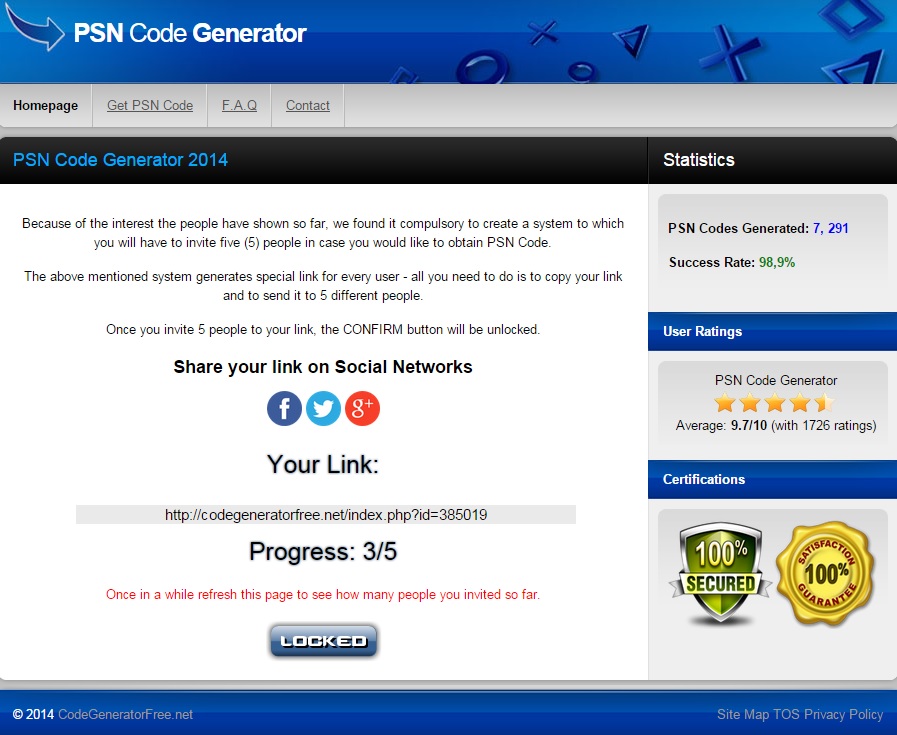
When we click on a gift card¸ instead of receiving the promised free code, we are asked to share a link with our friends in order to unlock the code.
Why do they do that?
When we share the link we are contributing to an increase in the number of visitors and, of course, the number of people that will try to redeem the “free code.” Keep this in mind, it will be important at the end of this post.
Ok, we already invited 5 of our friends and, in theory, we unlocked the code. Is this the last step? Are we going to receive the code now?
Again, the answer is no.
Looks like they don’t want to give us the code. Suspicious, right? So, what do they want now?
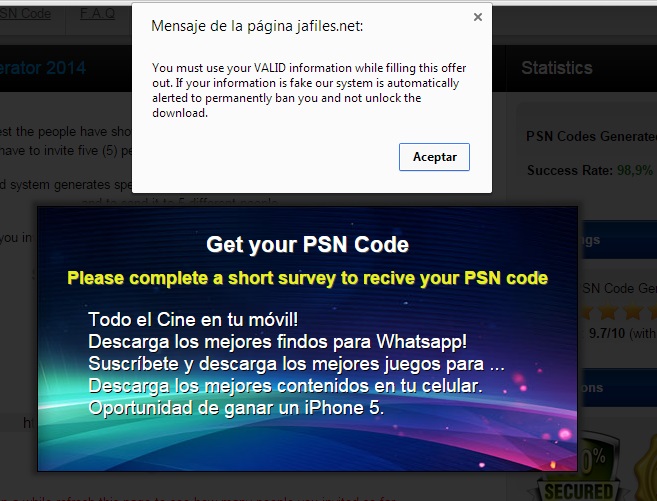
As we can see in the image, in order to receive our PSN code, we need to complete a short survey (like inviting 5 friends wasn’t already enough?!).
When we click on one of the surveys, a little pop-up with a message appears on the top of the screen. The message says: “You must use your VALID information while filling this offer out”.
Why do they need our VALID information?
Here’s the reason:
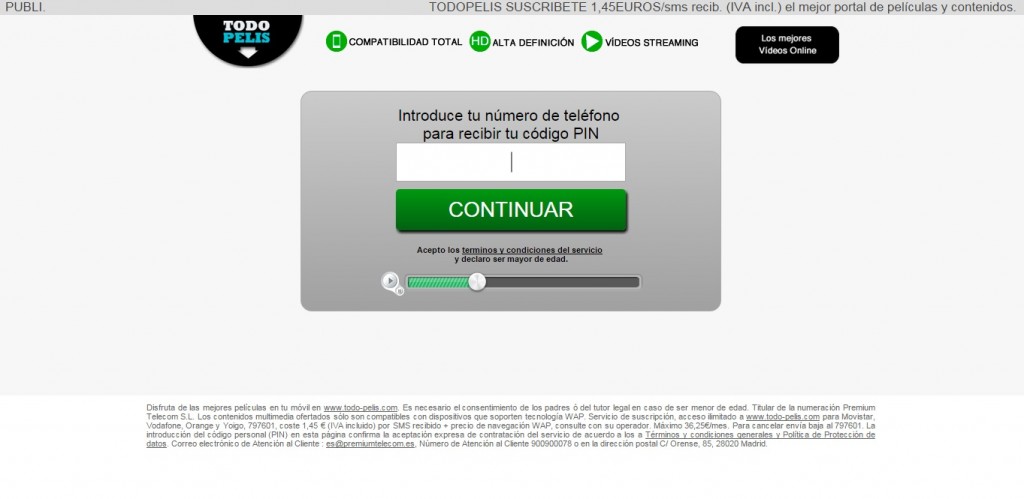
In order to receive the code, we need to introduce our phone number – our VALID phone number. But wait, before doing that, let’s read the text at the bottom of the page.
Surprise! It’s a premium SMS service with a total amount of 36,25€/month (>$40/month)! If we enter our phone number, we will be automatically subscribed to this premium service.
Remember the 5 friends you sent the link to? Well, now imagine how many people can fall into this scam just by sharing a link to 5 friends: 5+(5*5)+(5*5*5)+… creepy, right?
And of course, there’s no free code for your PSN or Steam accounts.
Unfortunately, there’s a lot of webpages using the same method to get user’s money. Also, there are other webpages offering software to generate codes. Cybercrooks create those
fake apps and get money from “download servers” because they bring
them users.
Tonda Hýža, from the AVAST Virus Lab, described those webpages as Adware due to the big amount of lies, advertisements and weird privacy policies.
Make sure you share this alert with your gamer friends J
Avast Software’s security applications for PC, Mac, and Android are trusted by more than 200-million people and businesses. Please follow us on Facebook, Twitter and Google+.
SpoofedMe – Social Login Impersonation Attack
Posted by Or Peles on Dec 04
Hi,
We have discovered an impersonation attack on social login protocols (e.g.
Oauth 1.0 / 2.0 used for authentication) based on a combination of an
implementation vulnerability existing in some identity providers (e.g.
LinkedIn, which has fixed the issue) and a known design problem in the
relying (third-party) website side.
The identity provider vulnerability is allowing the use of un-verified
email in the social login authentication…
IBM Releases Security Update for MDM
Original release date: December 04, 2014
IBM has released Tivoli Endpoint Manager Mobile Device Management (MDM) version 9.0.60100 to address a vulnerability which may allow a remote attacker to gain control of an affected system.
Users and administrators are encouraged to review the IBM Security Bulletin and apply the necessary updates.
This product is provided subject to this Notification and this Privacy & Use policy.
Re: XSS (in 20 chars) in Microsoft IIS 7.5 error message
Posted by Barry Dorrans on Dec 04
I believe that’s the asp.net error page you’re seeing (Was it yellow?)
That exception is from Request Validation (which we don’t consider a security boundary any more, and we advise folks to
validate themselves, as validation is context specific).
You’re seeing the dev error page, which by default is only shown if you’re accessing via //localhost. Developers can
override that setting to always show the default…
Offset2lib: bypassing full ASLR on 64bit Linux
Posted by Hector Marco on Dec 04
Hi,
This is a disclosure of a weakness of the ASLR Linux implementation.
The problem appears when the executable is PIE compiled and it has an
address leak belonging to the executable. We named this weakness:
offset2lib.
In this scenario, an attacker is able to de-randomize all mmapped
areas (libraries, mapped files, etc.) by knowing only an address
belonging to the application and the offset2lib value.
We have built a PoC which bypasses on a…
Critical Remote Code Execution Flaw Found in WordPress Plugin
There is an easily exploitable remote code execution vulnerability in a popular WordPress plugin that helps manage file downloads and researchers say the bug could be used by even a low-level attacker to run arbitrary code on a vulnerable site. The vulnerability is in the WP Download Manager, versions 2.7.4 and lower, and it could […]