Multiple SQL injection vulnerabilities in Zoph (aka Zoph Organizes Photos) 0.9.1 and earlier allow remote authenticated users to execute arbitrary SQL commands via the (1) _action parameter to group.php or (2) user.php or the (3) location_id parameter to photos.php in php/.
Monthly Archives: December 2014
CVE-2014-9236
Cross-site scripting (XSS) vulnerability in php/edit_photos.php in Zoph (aka Zoph Organizes Photos) 0.9.1 and earlier allows remote attackers to inject arbitrary web script or HTML via the (1) photographer_id or (2) _crumb parameter.
CVE-2014-9237
SQL injection vulnerability in Proticaret E-Commerce 3.0 allows remote attackers to execute arbitrary SQL commands via a tem:Code element in a SOAP request.
CVE-2014-9238
D-link IP camera DCS-2103 with firmware 1.0.0 allows remote attackers to obtain the installation path via the file parameter to cgi-bin/sddownload.cgi, as demonstrated by a / (forward slash) character.
CVE-2014-9239
SQL injection vulnerability in the IPS Connect service (interface/ipsconnect/ipsconnect.php) in Invision Power Board (aka IPB or IP.Board) 3.3.x and 3.4.x through 3.4.7 before 20141114 allows remote attackers to execute arbitrary SQL commands via the id[] parameter.
CVE-2014-9240
SQL injection vulnerability in member.php in MyBB (aka MyBulletinBoard) 1.8.x before 1.8.2 allows remote attackers to execute arbitrary SQL commands via the question_id parameter in a do_register action.
CVE-2014-9241
Multiple cross-site scripting (XSS) vulnerabilities in MyBB (aka MyBulletinBoard) 1.8.x before 1.8.2 allow remote attackers to inject arbitrary web script or HTML via the (1) type parameter to report.php, (2) signature parameter in a do_editsig action to usercp.php, or (3) title parameter in the style-templates module in an edit_template action or (4) file parameter in the config-languages module in an edit action to admin/index.php.
CVE-2014-9242
SQL injection vulnerability in admin/pages/modify.php in WebsiteBaker 2.8.3 allows remote attackers to execute arbitrary SQL commands via the page_id parameter.
CVE-2014-9243
Multiple cross-site scripting (XSS) vulnerabilities in WebsiteBaker 2.8.3 allow remote attackers to inject arbitrary web script or HTML via the (1) QUERY_STRING to wb/admin/admintools/tool.php or (2) section_id parameter to edit_module_files.php, (3) news/add_post.php, (4) news/modify_group.php, (5) news/modify_post.php, or (6) news/modify_settings.php in wb/modules/.
Three essential tips for new Android devices
Unfortunately, with today’s smartphones (which have the capacity and the feature-set of a high-end PC from about 10 years ago) it’s no longer a matter of popping in the SIM and using it.
There are a million things to watch out for and set up. In this week’s blog, we’ve compiled the three most useful steps you need to take besides running through the initial setup and downloading your favorite apps.
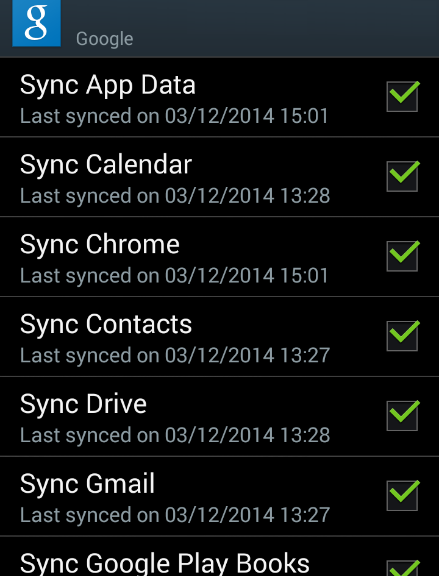
Sign into your Google Account:
One of the first things your new Android will ask you to do is sign into your Google account. Now, you could technically go without a Google account, but the benefits outweigh a lot of the worries some users have: once you sign in, it will back-up your phone’s settings, installed apps, account data and more – plus it allows you to purchase apps on the Google Play Store.
If you’re worried about privacy, simply create a new account and leave out information you don’t want to be shared with Google.
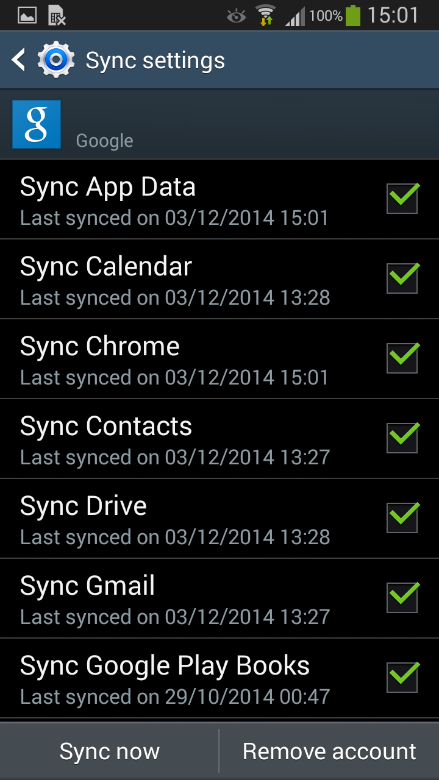
Get the latest update:
Most phones come with outdated software right out of the gate (as software continues to improve after devices come off the production line). We suggest checking for updates in your “Settings” app under “About device” (or similar).
Do the same for your apps so you don’t have to go into the Google Play store all the time. Go to Settings again and look for the “Auto-update apps” checkbox.
Get rid of preinstalled bloatware:
As we discovered last month in our AVG App Consumption report, one of the top reasons for battery drain, storage consumption and data traffic are the preinstalled apps on your phone.
We’ve actually made a free app, AVG Cleaner for Android, which lets you view the most draining apps on your phone and helps you get rid of them: Open it up and go to the App Uninstaller.
This will list all your currently running apps. If you tap on the little blue arrow in the top right, you can then sort the list by:
- App Usage – how often you use each of your apps
- Storage Usage – how much space your apps use
- Battery Usage – how demanding each app is on your battery
- Data Usage – the apps that send and receive the most data (to help avoid hitting your data plan limit)