libvirt before 1.2.12 allow remote authenticated users to obtain the VNC password by using the VIR_DOMAIN_XML_SECURE flag with a crafted (1) snapshot to the virDomainSnapshotGetXMLDesc interface or (2) image to the virDomainSaveImageGetXMLDesc interface.
Monthly Archives: January 2015
CVE-2015-1422
Multiple cross-site scripting (XSS) vulnerabilities in Gecko CMS 2.2 and 2.3 allow remote attackers to inject arbitrary web script or HTML via the (1) horder[], (2) jak_catid, (3) jak_content, (4) jak_css, (5) jak_delete_log[], (6) jak_email, (7) jak_extfile, (8) jak_file, (9) jak_hookshow[], (10) jak_img, (11) jak_javascript, (12) jak_lcontent, (13) jak_name, (14) jak_password, (15) jak_showcontact, (16) jak_tags, (17) jak_title, (18) jak_url, (19) jak_username, (20) real_hook_id[], (21) sp, (22) sreal_plugin_id[], (23) ssp, or (24) sssp parameter to admin/index.php or the (25) editor, (26) field_id, (27) fldr, (28) lang, (29) popup, (30) subfolder, or (31) type parameter to js/editor/plugins/filemanager/dialog.php.
CVE-2015-1423
Multiple SQL injection vulnerabilities in Gecko CMS 2.2 and 2.3 allow remote administrators to execute arbitrary SQL commands via the (1) jak_delete_log[] or (2) ssp parameter to admin/index.php.
CVE-2015-1424
Cross-site request forgery (CSRF) vulnerability in Gecko CMS 2.2 and 2.3 allows remote attackers to hijack the authentication of administrators for requests that add an administrator user via a newuser request to admin/index.php.
WordPress Geo Mashup 1.8.2 Cross Site Scripting
WordPress Geo Mashup plugin versions 1.8.2 and below suffer from a cross site scripting vulnerability.
Linux haunted by Ghost vulnerability
Security researchers have found a vulnerability inherent to a widely used component in most versions of Linux, reports Computer World.
The post Linux haunted by Ghost vulnerability appeared first on We Live Security.
WordPress Photo Gallery 1.2.8 Cross Site Scripting
WordPress Photo Gallery plugin version 1.2.8 suffers from a cross site scripting vulnerability.
WordPress Photo Gallery 1.2.8 SQL Injection
WordPress Photo Gallery plugin version 1.2.8 suffers from a remote SQL injection vulnerability.
25 Passwords You Should Avoid
As we approach February, and look forward to a year of stronger cybersecurity, there is still time to give your passwords a refresh and resolve to do so regularly.
Password protection is more important than ever, especially with so many devices, which provide ready access to so much of our personal information.
AVG’s own Tony Anscombe noted in his Safer Internet Day 2015 post recently, “Protecting your online world starts with devices and setting a passcode…”
It was interesting to find that in the annual list of Top 25 most common passwords on the Internet, as researched by the password management provider SplashData, the easy targets like “123456″ and “password” continue to hold the top two spots!

Other favorites in the research conducted by analyzing passwords that had been leaked in 2014: QWERTY and football. Their popularity makes them notoriously some of the “worst” passwords to use and the “easiest” for hackers to figure out.
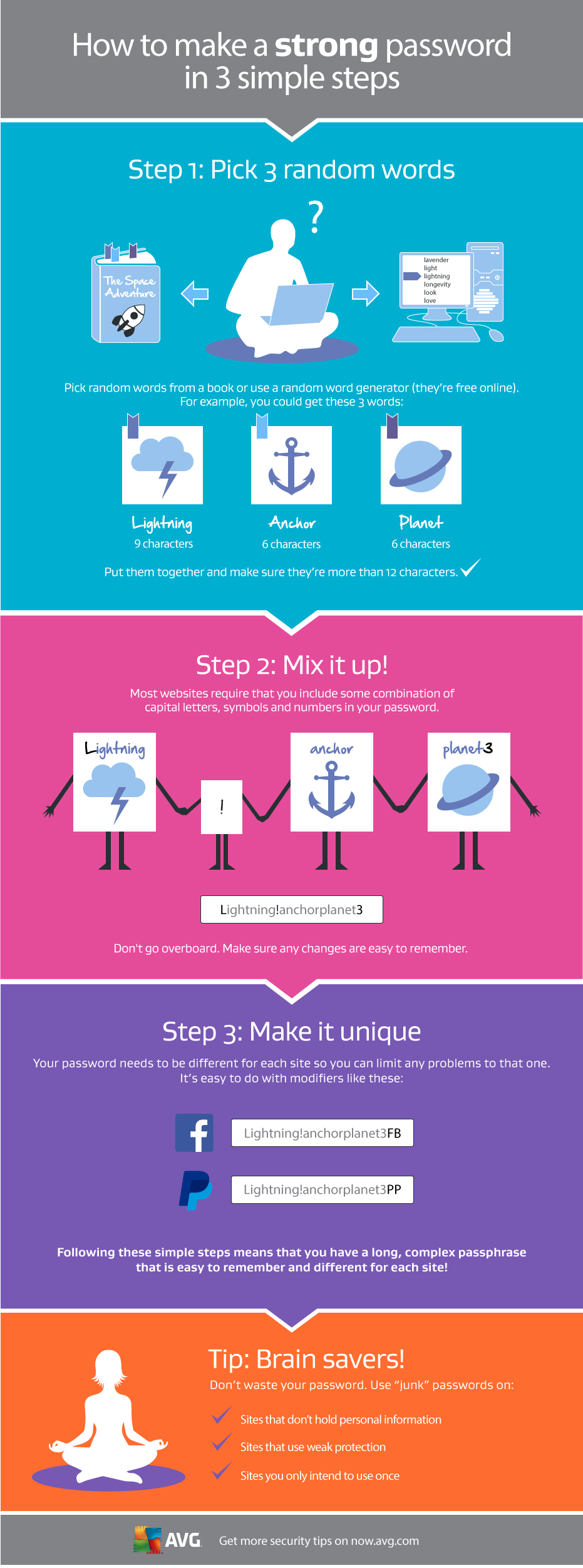
Creating a strong password
Picking a strong password doesn’t need to be difficult. We recently published an infographic on how to create a strong password that is also easy to remember.
Exim ESMTP GHOST Denial Of Service
Exim ESTMP denial of service exploit that leverages the GHOST glibc gethostbyname buffer overflow.