
Goodbye CD, DVD and pen drive. When you need to share a document with a work colleague or you have to take work home, you no longer need to use physical storage devices: the cloud has everything you need.
Services like Dropbox, Mega or Box have become more popular recently, gradually sending physical storage drives into oblivion.
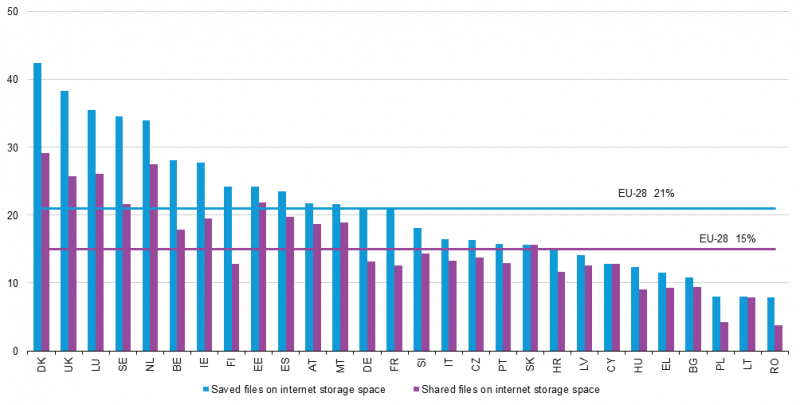
More specifically, and according to Eurostat, 21 percent of European Union citizens used the cloud as storage space in 2014. In fact, this figure is only the average for EU countries and in some countries, like Denmark and the United Kingdom, the percentage of citizens who use the cloud to store files greatly exceeds 30 percent.
There is no doubt that the business world is largely responsible for the growing use of the cloud for storing and sharing files. More convenient than using physical devices and more economical than installing internal servers, the cloud seems to have gotten into our offices too.
The advantages of services like Dropbox are obvious. However, when using virtual storage spaces to store and share your company’s information their security measures could leave much to be desired.
A few months ago, a vulnerability was discovered in Dropbox that disclosed personal files, and at the end of 2014, 7 million passwords for this service were leaked. If the fact that confidential corporate information is one of the main targets of cyber-criminals is added to these serious security flaws, the conclusion is obvious: your company’s files are not completely secure in the cloud.
However, your company does not need to steer clear of these services from fear that a cyber-criminal will steal its document, but you will have to take certain precautions before using them. The key is in passwords, file encryption, two-step verification and the best enterprise antivirus solution.
In this case, Panda Cloud Fusion can protect, manage and provide remote support for all the devices in your company’s network anytime and anywhere.

Firstly, it is essential to follow the tips on how to create strong passwords, like any other service. You know: letters, numbers, uppercase, lowercase, a symbol or two and if possible, never use the same password as the one you use for your email, Facebook and other services.
As regards file encryption, some virtual storage services store our documents encrypted. Although Dropbox does not, Mega, the cloud platform of the controversial Kim Dotcom, does encrypt your files. However, nothing is perfect. Mega stores on its servers a copy of the key for decrypting your files, so it is not 100% secure either. One of the best options is for you to encrypt your files before uploading them to the cloud using one of the services that allows you to do this.
Finally, some of these services (like Dropbox or Google Drive) allow you to enable two-step verification of your account. This system combines the password that you choose with a password that the service sends to one of your devices (almost always to your phone in a text message or an app). This adds a second layer of security that makes it difficult for someone to access your account.
The cloud is convenient, yes, but you have to pay attention to security.
The post How to secure the files your company stores in the cloud appeared first on MediaCenter Panda Security.








