Monthly Archives: February 2015
Hackers Steal Up to $1 Billion from 100 Banks Worldwide – NBC Nightly News
Bank Hackers Pull off $1 Billion Cyberheist – CBS Evening News
Lenovo apologizes over pre-installed tracking software
Lenovo has issued a public apology, admitting it “messed up badly” by selling laptops with a controversial tracking software pre-installed.
The post Lenovo apologizes over pre-installed tracking software appeared first on We Live Security.
Hackers Stole from 100 Banks and Rigged ATMs to Spew Cash – CNN
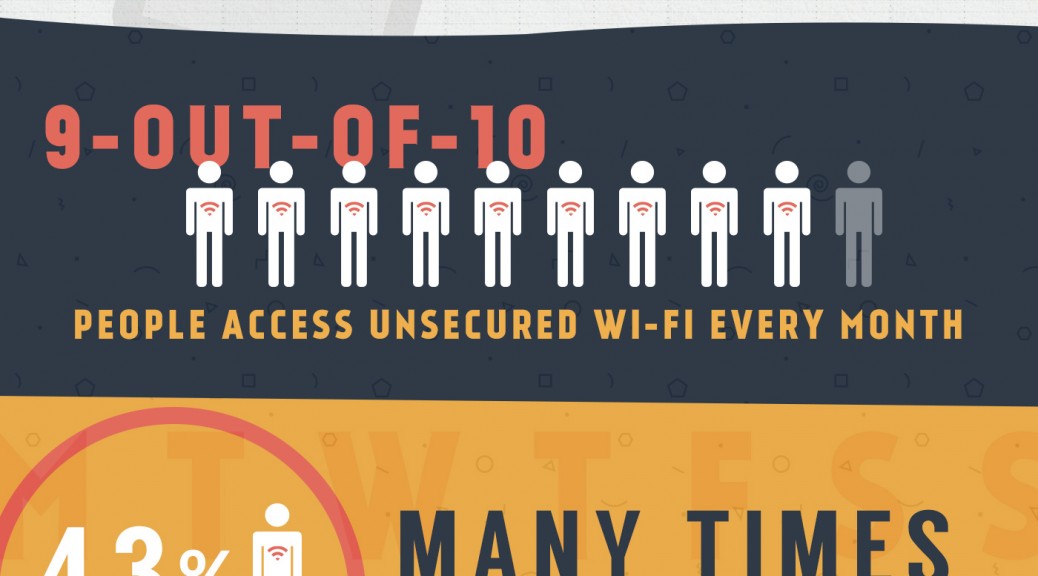
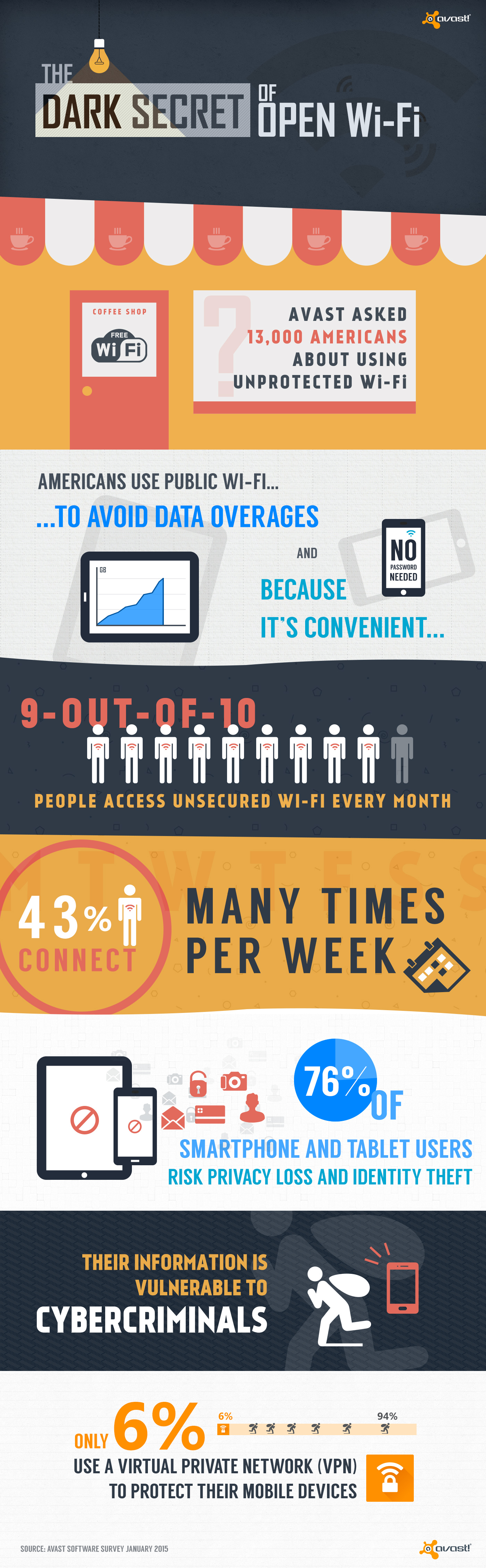
Americans willingly risk privacy and identity on open Wi-Fi
Is the convenience of open Wi-Fi worth the risk of identity theft? Most Americans think so.
In a recent survey, we found that only 6% of Americans protect their data by using a virtual private network (VPN) when using public Wi-Fi with their smartphone or tablet. That leaves a whopping 94% unprotected. Why is this?
Do people not know the risks of using unsecured public Wi-Fi?
Is avoiding data overages or the convenience of no password more important than the data on their devices?
Are they not aware that there is protection available?
Are they scared they won’t understand how to use VPN because of the technical sounding name?
The truth about open, public Wi-Fi
The truth is that using unprotected Wi-Fi networks could end up costing you your privacy and identity when you use them without protection like Virtual Private Network (VPN) software. This is because unsecured networks, those are the ones that do not require registration or a password, give cybercrooks easy access to sensitive personal information.
“As mobile cloud storage becomes more popular and the quest for free Wi-Fi continues to grow, open networks that require no passwords place unprotected consumers at great risk of compromising sensitive personal data,” said Jude McColgan, president of mobile at Avast.
“The majority of Americans don’t realize that all the personal information on their mobile devices becomes defenseless over public Wi-Fi if used without protection. These networks create an easy entry point for hackers to attack millions of American consumers on a daily basis.”
Avast can protect you and it’s not hard or expensive
“Unfortunately hacking isn’t a complicated process – there are tools available online that anyone can easily use to steal personal data,” says Ondrej Vlček, Chief Operating Officer at Avast. “Avast SecureLine VPN allows users to browse the web anonymously and safely, especially while using open Wi-Fi.”
Avast SecureLine VPN protects your Internet connections with military-grade encryption and hides your IP address. If that sounds like mumbo-jumbo to you, what it means is that essentially our VPN protection makes your device invisible to cybercriminals. In addition to that, using the VPN hides your browsing history, so no one can monitor your behavior online. We assure you, it’s as easy as can be to use.
Avast SecureLine VPN is available for Android phones and tablets on Google Play and for iOS devices in the Apple App Store. We also have VPN available for Windows PCs.
CVE-2014-0005
PicketBox and JBossSX, as used in Red Hat JBoss Enterprise Application Platform (JBEAP) 6.2.2 and JBoss BRMS before 6.0.3 roll up patch 2, allows remote authenticated users to read and modify the application sever configuration and state by deploying a crafted application.
CVE-2014-3682
XML external entity (XXE) vulnerability in the JBPMBpmn2ResourceImpl function in designer/bpmn2/resource/JBPMBpmn2ResourceImpl.java in jbpm-designer 6.0.x and 6.2.x allows remote attackers to read arbitrary files and possibly have other unspecified impact by importing a crafted BPMN2 file.
CVE-2014-8114
The UberFire Framework 0.3.x does not properly restrict paths, which allows remote attackers to (1) execute arbitrary code by uploading crafted content to FileUploadServlet or (2) read arbitrary files via vectors involving FileDownloadServlet.
CVE-2014-8115
The default authorization constrains in KIE Workbench 6.0.x allows remote authenticated users to read or write to arbitrary files, bypass intended access restrictions, and possibly have other unspecified impact via unknown vectors.