FireHOL a simple yet powerful way to configure stateful iptables firewalls. It can be used for almost any purpose, including control of any number of internal/external/virtual interfaces, control of any combination of routed traffic, setting up DMZ routers and servers, and all kinds of NAT. It provides strong protection (flooding, spoofing, etc.), transparent caches, source MAC verification, blacklists, whitelists, and more. Its goal is to be completely abstracted and powerful but also easy to use, audit, and understand.
Monthly Archives: February 2015
Fat Free CRM 0.13.5 Cross Site Request Forgery
Fat Free CRM version 0.13.5 suffers from a cross site request forgery vulnerability.
How to activate Two Factor Authentication on Apple services
This February Apple announced that they would be making Two Factor Authentication available on iMessage and FaceTime in a bid to help users secure their online identities.
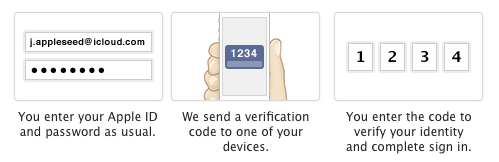
What is Two Factor Authentication?
Two Factor Authentication is method of securing your online accounts or services through the addition of another layer of security when you login. This is usually a code which is sent to your mobile device, either in form of a text message or via an app.
Activating Apple’s Two Factor Authentication
Implementing Two Factor Authentication on Apple services is very straightforward.
- Go to My Apple ID.
- Select Manage your Apple ID and sign in.
- Select Password and Security.
- Under Two-Step Verification, select Get Started and follow the onscreen instructions.
For help and advice on implementing Two Factor Authentitcation on Apple services, I’d recommend visiting the official Apple FAQ page.
Russia seeks VPN and Tor ban in anonymity clamp down
Russian authorities have indicated that VPNs and online anonymising software Tor could soon be banned for the country’s 143.5 million residents.
The post Russia seeks VPN and Tor ban in anonymity clamp down appeared first on We Live Security.
Siemens SIMATIC WinCC (TIA Portal) V13 Privilege Escalation
The latest update for SIMATIC WinCC (TIA Portal) V13 fixes two vulnerabilities. The remote management module of WinCC (TIA Portal) Multi Panels and Comfort Panels, and WinCC RT Advanced transmits weakly protected credentials over the network. Attackers capturing network traffic of the remote management module could possibly reconstruct used passwords. A hard coded encryption key used in WinCC RT Professional could allow attackers to escalate their privileges if the application’s network communication with an authenticated user was captured.
Siemens SIMATIC STEP 7 (TIA Portal) V13 Privilege Escalation
The latest update for SIMATIC STEP 7 (TIA Portal) V13 fixes two vulnerabilities. Device user passwords in TIA portal project files are stored using a weak hashing algorithm. Attackers with read access to the project file could possibly reconstruct the passwords for device users. Privilege information for device users is stored unprotected in the TIA portal projects. Attackers with access to the project file could possibly read and modify the permissions for device users in the project file. If unsuspecting users are tricked to download the manipulated project files to the device, the user permissions become active.
Gentoo Linux Security Advisory 201502-12
Gentoo Linux Security Advisory 201502-12 – Multiple vulnerabilities have been found in Oracle’s Java SE Development Kit and Runtime Environment, the worst of which could lead to execution of arbitrary code. Versions less than 1.7.0.71 are affected.
Gentoo Linux Security Advisory 201502-10
Gentoo Linux Security Advisory 201502-10 – Two vulnerabilities have been found in libpng, possibly resulting in execution of arbitrary code. Versions less than 1.6.16 are affected.
Gentoo Linux Security Advisory 201502-11
Gentoo Linux Security Advisory 201502-11 – Two vulnerabilities have been found in GNU cpio, the worst of which could result in execution of arbitrary code. Versions less than 2.11-r3 are affected.