Ride-sharing taxi apps Uber, Lyft and Sidecar have been asked by US lawmakers to adopt fingerprint-based background checks for their drivers,
The post US lawmakers want taxi apps to check driver fingerprints appeared first on We Live Security.
Ride-sharing taxi apps Uber, Lyft and Sidecar have been asked by US lawmakers to adopt fingerprint-based background checks for their drivers,
The post US lawmakers want taxi apps to check driver fingerprints appeared first on We Live Security.
Kguard SHA104 and SHA108 DVRs suffer from command injection, insufficient authentication and authorization, password disclosure, denial of service, and missing transport security vulnerabilities.
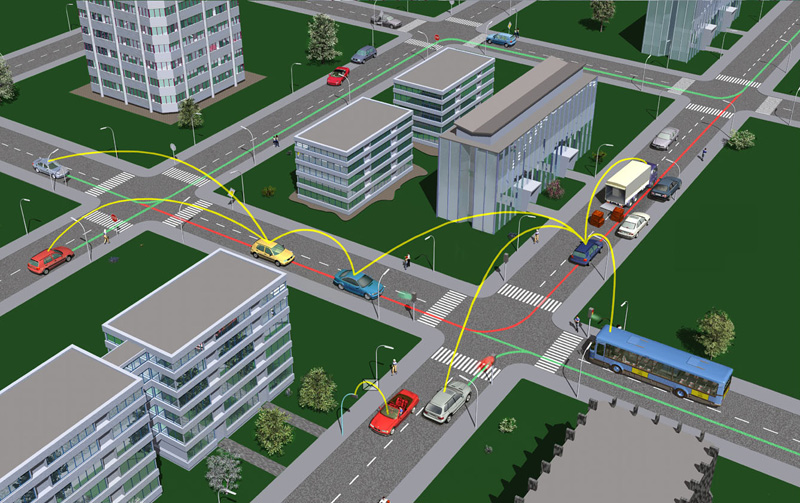
Smartphones, watches and a thousand home appliances. More day-to-day objects are connected every day. But the Internet of Things also runs on four wheels. Tomorrow’s cars will not be flying cars, as science fiction movies have told us, but their future lies in the Internet.
Cars will connect to one another to share information and they will also be connected to infrastructures to obtain data of interest in real time.
If the next revolution in automobiles will come from Car-to-Car (C2C) and Car-to-Infrastructure (C2I) connections, automakers will need an army of cyber-security experts to safeguard the cars of the future. If they can connect to one another, they will also be vulnerable to cyber-attacks.
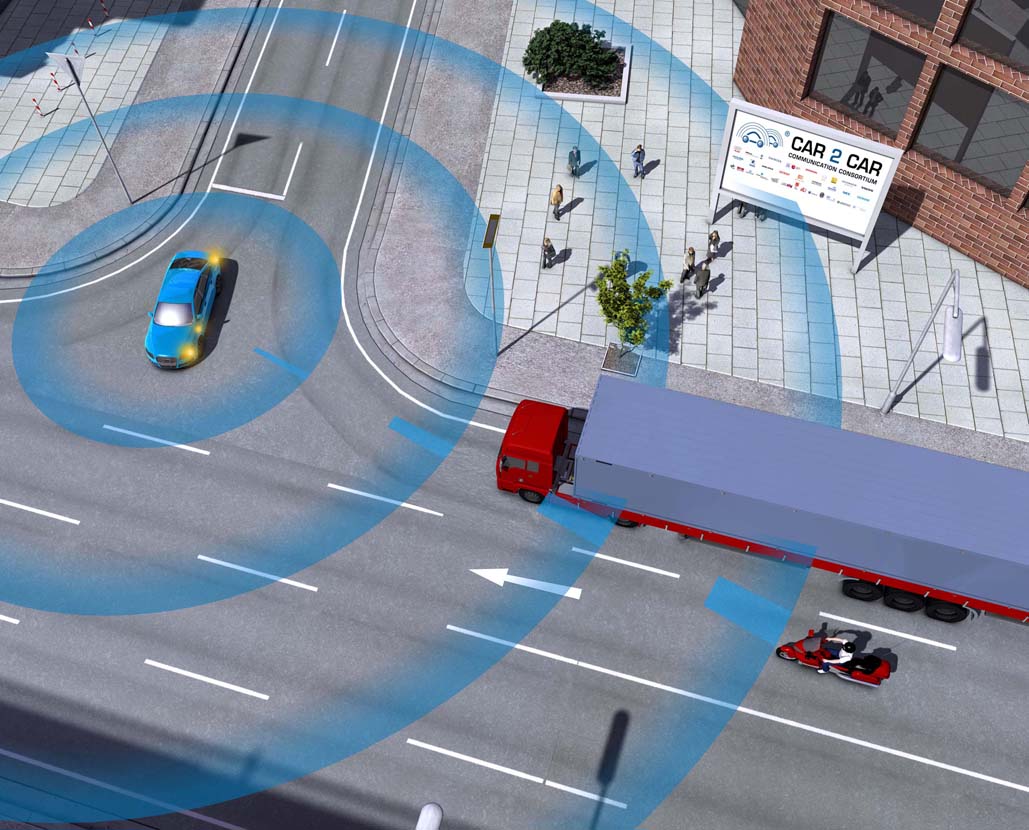
So far, cyber-security does not seem to be a strong point of the intelligent cars currently on the market. For example, a 14-year-old boy managed to gain wireless access to the brain of one of these cars using a $15 (just over €13) circuit board.
He achieved this feat at a hackathon organized a few weeks ago by Delphi, a US company that makes electronic systems for vehicles.
During this hackathon, the participants —the majority of them students— demonstrated that intelligent vehicles are not immune to IT attacks. They also showed that some of these vehicles can be opened (or even started) even though they are locked.
The cars of the future will be a clear target for cyber-criminals, as not only will they be able to cause a large number of accidents by hacking the brain of these vehicles or steal them without needing to break the windows and hotwire them; the vulnerability of these cars will allow them to steal large amounts of data and wreak havoc in cities.
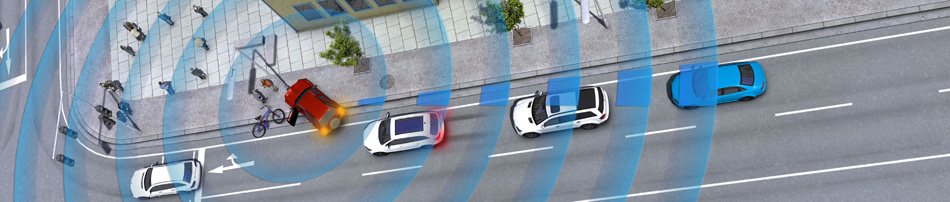
C2C and C2I systems will allow vehicles to constantly share information. Sharp breaking, breakdowns, traffic jams or the duration of traffic lights will be some of the data that could circulate through short-range wireless networks or simply through the car’s Internet connection.
A cyber-attack could turn one of these intelligent cars into the gateway to any information network connected to the vehicles, from the power grid to the system used by the police or the traffic light network in a city.
The solution lies in manufacturers of intelligent cars considering security and developing systems that detect which cars have been hacked in order to isolate them from the rest of the network.
There are many suggestions, such as installing security chips like those used on credits cards, or creating new software or hardware that establishes secure connections.
The post Car to car: Internet-connected cars. Will they be the main cause of accidents in the future? appeared first on MediaCenter Panda Security.
Codoforum version 2.5.1 suffers from an arbitrary file download vulnerability.
WordPress Fraction Theme version 1.1.1 suffers from a privilege escalation vulnerability.
Manage Engine AD Audit Manager Plus versions below build 6270 suffer from a cross site scripting vulnerability.
Ubuntu Security Notice 2521-1 – Several out-of-bounds write bugs were discovered in Skia. If a user were tricked in to opening a specially crafted website, an attacker could potentially exploit these to cause a denial of service via application crash or execute arbitrary code with the privileges of the user invoking the program. A use-after-free was discovered in the V8 bindings in Blink. If a user were tricked in to opening a specially crafted website, an attacker could potentially exploit this to cause a denial of service via renderer crash, or execute arbitrary code with the privileges of the sandboxed render process. Various other issues were also addressed.
Mandriva Linux Security Advisory 2015-057 – The Crypto API in the Linux kernel before 3.18.5 allows local users to load arbitrary kernel modules via a bind system call for an AF_ALG socket with a parenthesized module template expression in the salg_name field, as demonstrated by the vfat expression, a different vulnerability than CVE-2013-7421. net/netfilter/nf_conntrack_proto_generic.c in the Linux kernel before 3.18 generates incorrect conntrack entries during handling of certain iptables rule sets for the SCTP, DCCP, GRE, and UDP-Lite protocols, which allows remote attackers to bypass intended access restrictions via packets with disallowed port numbers. The Crypto API in the Linux kernel before 3.18.5 allows local users to load arbitrary kernel modules via a bind system call for an AF_ALG socket with a module name in the salg_name field, a different vulnerability than CVE-2014-9644. The updated packages provides a solution for these security issues.
Ubuntu Security Notice 2523-1 – Martin Holst Swende discovered that the mod_headers module allowed HTTP trailers to replace HTTP headers during request processing. A remote attacker could possibly use this issue to bypass RequestHeaders directives. Mark Montague discovered that the mod_cache module incorrectly handled empty HTTP Content-Type headers. A remote attacker could use this issue to cause the server to stop responding, leading to a denial of service. This issue only affected Ubuntu 14.04 LTS and Ubuntu 14.10. Various other issues were also addressed.
Cisco Security Advisory – On March 9, 2015, new research was published that takes advantage of a flaw in double data rate type 3 (DDR3) synchronous dynamic random-access memory (SDRAM) to perform privilege escalation attacks on systems that contain the affected hardware. The flaw is known as Row Hammer. To attempt an attack, the attacker must execute a malicious binary on an affected system. In addition, the research focused on consumer hardware that did not have a number of mitigations and memory protections that have been integrated into chipsets and memory modules used in Cisco server-class products. Of note in the paper is that the researchers were unable, in their testing, to exploit devices that use Error-Correcting Code (ECC) memory. Cisco offers a limited number of products that allow an unprivileged user to load and execute binaries.