Monthly Archives: March 2015
Microsoft Admits Freak Affects All Versions Of Windows
Mandarin Oriental Hotel Group Is Investigating A Credit Card Breach
Adobe Launches Cashless Bug Bounty
Air traffic control vulnerability could allow criminals to hack the skies
The Federal Aviation Administration must tighten the security around air traffic control in the United States, according to a new report filed by the Government Accountability Office (GAO).
The post Air traffic control vulnerability could allow criminals to hack the skies appeared first on We Live Security.
RHBA-2015:0646-1: libvirt-python bug fix update
Red Hat Enterprise Linux: Updated libvirt-python packages that fix one bug are now available for Red Hat
Enterprise Linux 7.
Lysa Myers: “There are still only a handful of women in the security fieldâ€
There are many female researchers and computer experts who contribute to the field, helping everyone enjoy safer technology. We spoke to one of the most prominent: Lysa Myers, a member of our research team in the US.
The post Lysa Myers: “There are still only a handful of women in the security field” appeared first on We Live Security.
USN-2522-1: ICU vulnerabilities
Ubuntu Security Notice USN-2522-1
5th March, 2015
icu vulnerabilities
A security issue affects these releases of Ubuntu and its
derivatives:
- Ubuntu 14.10
- Ubuntu 14.04 LTS
- Ubuntu 12.04 LTS
Summary
ICU could be made to crash or run programs as your login if it processed
specially crafted data.
Software description
- icu
– International Components for Unicode library
Details
It was discovered that ICU incorrectly handled memory operations when
processing fonts. If an application using ICU processed crafted data, an
attacker could cause it to crash or potentially execute arbitrary code with
the privileges of the user invoking the program. This issue only affected
Ubuntu 12.04 LTS. (CVE-2013-1569, CVE-2013-2383, CVE-2013-2384,
CVE-2013-2419)
It was discovered that ICU incorrectly handled memory operations when
processing fonts. If an application using ICU processed crafted data, an
attacker could cause it to crash or potentially execute arbitrary code with
the privileges of the user invoking the program. (CVE-2014-6585,
CVE-2014-6591)
It was discovered that ICU incorrectly handled memory operations when
processing regular expressions. If an application using ICU processed
crafted data, an attacker could cause it to crash or potentially execute
arbitrary code with the privileges of the user invoking the program.
(CVE-2014-7923, CVE-2014-7926, CVE-2014-9654)
It was discovered that ICU collator implementation incorrectly handled
memory operations. If an application using ICU processed crafted data, an
attacker could cause it to crash or potentially execute arbitrary code with
the privileges of the user invoking the program. (CVE-2014-7940)
Update instructions
The problem can be corrected by updating your system to the following
package version:
- Ubuntu 14.10:
-
libicu52
52.1-6ubuntu0.2
- Ubuntu 14.04 LTS:
-
libicu52
52.1-3ubuntu0.2
- Ubuntu 12.04 LTS:
-
libicu48
4.8.1.1-3ubuntu0.3
To update your system, please follow these instructions:
https://wiki.ubuntu.com/Security/Upgrades.
In general, a standard system update will make all the necessary changes.
References
Skype worm reloaded Â

Skype worms are not exactly new anymore (unfortunately).
Scenario is simply: someone on your friends list got infected and is now sending you a link to a ‘funny image’ or pictures of you. In this case, you are being baited by a video of you. Let’s just hope it’s nothing embarrassing ![]()
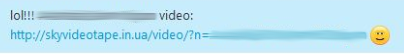
Lol! Seems like there’s a cool new video of you going around.
When visiting the (totally not malicious looking) link, you get a video, but apparently you need to download a plugin first:
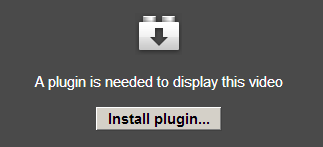
When you click on Install plugin… a new file called ‘setup.exe’ gets downloaded. It’s actually simply a self-extracting archive which contains a file named: ‘setup_BorderlineRunner_142342569355180.exe’
When running the setup.exe file:
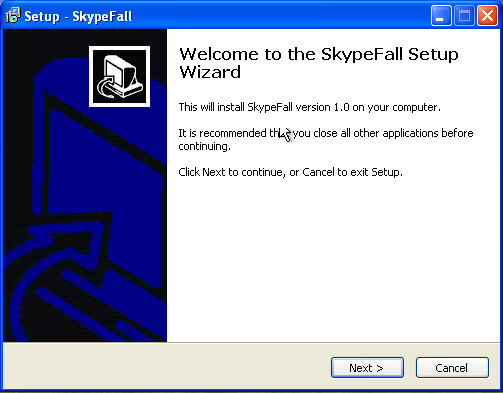
It almost seems like we’re installing legitimate software, SkypeFall version 1.0. Almost.
Clicking Next, Next, Next in the setup wizard, nothing much seems to be happening, but in the background there’s quite a lot going on:
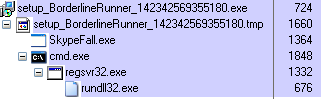
A new file called ‘SkypeFall’ is dropped and a new DLL is being registered. Afterwards, two new processes are now active in memory: SkypeFall.exe and rundll32.exe, in which the latter is actually running the DLL BorderlineRunner.dll.
Files are being created in both respectively %programfiles%BorderlineRunner and %appdata%SkypeFall. A new service is also registered:
HKLMSystemCurrentControlSetServices6b57ae94
Afterwards you’ll spam all your friends with the same message as well, following the pattern:![]()
We detect this malware as:
W32/Skyper.A.worm
IOCs
Domains:
hxxp://24onlineskyvideo.info
hxxp://24videotur.in.ua
hxxp://deepskype.net
hxxp://factorygood.net
hxxp://ironskype.net
hxxp://letitskype.info
hxxp://letskype.net
hxxp://popskypevideo.net
hxxp://popvideoskype.com
hxxp://popvideoskype.info
hxxp://popvideoskype.net
hxxp://skypepopvideo.net
hxxp://skypepopvideo.net
hxxp://skyvideo24.in.ua
hxxp://skyvideo24online.in.ua
hxxp://skyvideo24online.ru
hxxp://skyvideotape.in.ua
hxxp://skyvideotape.ru
hxxp://someskype.com
hxxp://someskype.net
hxxp://techine.info
hxxp://techine.net
hxxp://videosk.in.ua
hxxp://videosk.info
hxxp://videoskype.ru
hxxp://videoskype24.ru
hxxp://videoss.in.ua
Hashes (SHA1):
b6f690849e9ed71b3f956078934da5ed88887aa3
42c685ac60555beaacd5e07d5234a6600845e208
dfb9bfb274e9df857bb0fae02ba711e62a2a9eb6
726db7f1c956db8c5e94d21558cbbe650b949b7e
How to avoid the malware W32/Skyper.A.worm
- Never click on unknown links, especially when a friend sends you a generic text saying there are pictures or videos of you going around. If you’re really curious, ask them first what’s it about. Better be safe than sorry.
- Don’t be fooled by known icons or “legit” file descriptions, this can easily be altered.
- Even if you clicked the link and you’re not suspicious, you should be when a file is downloaded and no pictures are shown, but just an EXE file.
The post Skype worm reloaded appeared first on MediaCenter Panda Security.
Adobe crowdsources its bug-hunting, but no rewards offered
Adobe, the company behind Flash, Photoshop and Adobe Reader, has launched a program encouraging security researchers to find and report possible vulnerabilities to the firm.
The post Adobe crowdsources its bug-hunting, but no rewards offered appeared first on We Live Security.
