The em_sysenter function in arch/x86/kvm/emulate.c in the Linux kernel before 3.18.5, when the guest OS lacks SYSENTER MSR initialization, allows guest OS users to gain guest OS privileges or cause a denial of service (guest OS crash) by triggering use of a 16-bit code segment for emulation of a SYSENTER instruction.
Monthly Archives: March 2015
SB15-061: Vulnerability Summary for the Week of February 23, 2015
Original release date: March 02, 2015
The US-CERT Cyber Security Bulletin provides a summary of new vulnerabilities that have been recorded by the National Institute of Standards and Technology (NIST) National Vulnerability Database (NVD) in the past week. The NVD is sponsored by the Department of Homeland Security (DHS) National Cybersecurity and Communications Integration Center (NCCIC) / United States Computer Emergency Readiness Team (US-CERT). For modified or updated entries, please visit the NVD, which contains historical vulnerability information.
The vulnerabilities are based on the CVE vulnerability naming standard and are organized according to severity, determined by the Common Vulnerability Scoring System (CVSS) standard. The division of high, medium, and low severities correspond to the following scores:
-
High – Vulnerabilities will be labeled High severity if they have a CVSS base score of 7.0 – 10.0
-
Medium – Vulnerabilities will be labeled Medium severity if they have a CVSS base score of 4.0 – 6.9
-
Low – Vulnerabilities will be labeled Low severity if they have a CVSS base score of 0.0 – 3.9
Entries may include additional information provided by organizations and efforts sponsored by US-CERT. This information may include identifying information, values, definitions, and related links. Patch information is provided when available. Please note that some of the information in the bulletins is compiled from external, open source reports and is not a direct result of US-CERT analysis.
High Vulnerabilities
| Primary Vendor — Product |
Description | Published | CVSS Score | Source & Patch Info |
|---|---|---|---|---|
| adobe — flash_player | Use-after-free vulnerability in Adobe Flash Player before 13.0.0.269 and 14.x through 16.x before 16.0.0.305 on Windows and OS X and before 11.2.202.442 on Linux allows attackers to execute arbitrary code via unspecified vectors, a different vulnerability than CVE-2015-0313, CVE-2015-0315, CVE-2015-0320, and CVE-2015-0322. | 2015-02-21 | 10.0 | CVE-2015-0331 BID |
| apptha — wordpress_video_gallery | SQL injection vulnerability in videogalleryrss.php in the Apptha WordPress Video Gallery (contus-video-gallery) plugin before 2.8 for WordPress allows remote attackers to execute arbitrary SQL commands via the vid parameter in a rss action to wp-admin/admin-ajax.php. | 2015-02-24 | 7.5 | CVE-2015-2065 CONFIRM OSVDB EXPLOIT-DB MISC |
| cisco — carrier_routing_system | Cisco IOS XR 5.0.1 and 5.2.1 on Network Convergence System (NCS) 6000 devices and 5.1.3 and 5.1.4 on Carrier Routing System X (CRS-X) devices allows remote attackers to cause a denial of service (line-card reload) via malformed IPv6 packets with extension headers, aka Bug ID CSCuq95241. | 2015-02-21 | 7.1 | CVE-2015-0618 SECTRACK BID |
| cisco — ips_sensor_software | Race condition in the SSL implementation on Cisco Intrusion Prevention System (IPS) devices allows remote attackers to cause a denial of service by making many management-interface HTTPS connections during the key-regeneration phase of an upgrade, aka Bug ID CSCui25688. | 2015-02-21 | 7.1 | CVE-2015-0631 BID |
| d-link — dcs-931l_firmware | Unrestricted file upload vulnerability in D-Link DCS-931L with firmware 1.04 and earlier allows remote authenticated users to execute arbitrary code by uploading a file with an executable extension. | 2015-02-23 | 9.0 | CVE-2015-2049 |
| d-link — dap-1320_firmware | D-Link DAP-1320 Rev Ax with firmware before 1.21b05 allows attackers to execute arbitrary commands via unspecified vectors. | 2015-02-23 | 10.0 | CVE-2015-2050 |
| d-link — dir-645_firmware | The D-Link DIR-645 Wired/Wireless Router Rev. Ax with firmware 1.04b12 and earlier allows remote attackers to execute arbitrary commands via a GetDeviceSettings action to the HNAP interface. | 2015-02-23 | 10.0 | CVE-2015-2051 |
| d-link — dir-645_firmware | Stack-based buffer overflow in the DIR-645 Wired/Wireless Router Rev. Ax with firmware 1.04b12 and earlier allows remote attackers to execute arbitrary code via a long string in a GetDeviceSettings action to the HNAP interface. | 2015-02-23 | 10.0 | CVE-2015-2052 |
| dell — asset_manager | Multiple SQL injection vulnerabilities in Dell ScriptLogic Asset Manager (aka Quest Workspace Asset Manager) before 9.5 allow remote attackers to execute arbitrary SQL commands via unspecified vectors to (1) GetClientPackage.aspx or (2) GetProcessedPackage.aspx. | 2015-02-24 | 7.5 | CVE-2015-1605 MISC MISC BID |
| dlguard — dlguard | SQL injection vulnerability in DLGuard 4.5 allows remote attackers to execute arbitrary SQL commands via the c parameter to index.php. | 2015-02-24 | 7.5 | CVE-2015-2066 MISC MISC FULLDISC |
| etouch — samepage | SQL injection vulnerability in eTouch SamePage Enterprise Edition 4.4.0.0.239 allows remote attackers to execute arbitrary SQL commands via the catId parameter to cm/blogrss/feed. | 2015-02-24 | 7.5 | CVE-2015-2070 EXPLOIT-DB FULLDISC MISC OSVDB |
| gnu — glibc | The nss_dns implementation of getnetbyname in GNU C Library (aka glibc) before 2.21, when the DNS backend in the Name Service Switch configuration is enabled, allows remote attackers to cause a denial of service (infinite loop) by sending a positive answer while a network name is being process. | 2015-02-24 | 7.8 | CVE-2014-9402 CONFIRM MLIST SUSE |
| ibm — tivoli_storage_manager | Stack-based buffer overflow in dsmtca in the client in IBM Tivoli Storage Manager (TSM) 5.4 through 5.4.3.6, 5.5 through 5.5.4.3, 6.1 through 6.1.5.6, 6.2 before 6.2.5.4, and 6.3 before 6.3.2.3 on UNIX, Linux, and OS X allows local users to gain privileges via unspecified vectors. | 2015-02-21 | 7.2 | CVE-2014-6184 AIXAPAR |
| info-zip — unzip | Buffer overflow in the charset_to_intern function in unix/unix.c in Info-Zip UnZip 6.10b allows remote attackers to execute arbitrary code via a crafted string, as demonstrated by converting a string from CP866 to UTF-8. | 2015-02-23 | 7.5 | CVE-2015-1315 MISC MLIST MISC |
| mozilla — firefox | Multiple use-after-free vulnerabilities in OpenType Sanitiser, as used in Mozilla Firefox before 36.0, might allow remote attackers to trigger problematic Developer Console information or possibly have unspecified other impact by leveraging incorrect macro expansion, related to the ots::ots_gasp_parse function. | 2015-02-25 | 7.5 | CVE-2015-0823 CONFIRM CONFIRM SECTRACK BID |
| mozilla — firefox | Multiple unspecified vulnerabilities in the browser engine in Mozilla Firefox before 36.0 allow remote attackers to cause a denial of service (memory corruption and application crash) or possibly execute arbitrary code via unknown vectors. | 2015-02-25 | 7.5 | CVE-2015-0835 CONFIRM CONFIRM CONFIRM CONFIRM CONFIRM CONFIRM CONFIRM CONFIRM CONFIRM CONFIRM SECTRACK SECTRACK BID |
| mozilla — firefox | Multiple unspecified vulnerabilities in the browser engine in Mozilla Firefox before 36.0, Firefox ESR 31.x before 31.5, and Thunderbird before 31.5 allow remote attackers to cause a denial of service (memory corruption and application crash) or possibly execute arbitrary code via unknown vectors. | 2015-02-25 | 7.5 | CVE-2015-0836 CONFIRM CONFIRM CONFIRM CONFIRM CONFIRM CONFIRM CONFIRM CONFIRM CONFIRM CONFIRM SECTRACK SECTRACK BID |
| network_vision — intravue | Network Vision IntraVue before 2.3.0a14 on Windows allows remote attackers to execute arbitrary OS commands via unspecified vectors. | 2015-02-26 | 10.0 | CVE-2015-0977 |
| redhat — jboss_jbpm-designer | XML external entity (XXE) vulnerability in the JBPMBpmn2ResourceImpl function in designer/bpmn2/resource/JBPMBpmn2ResourceImpl.java in jbpm-designer 6.0.x and 6.2.x allows remote attackers to read arbitrary files and possibly have other unspecified impact by importing a crafted BPMN2 file. | 2015-02-20 | 7.5 | CVE-2014-3682 CONFIRM CONFIRM CONFIRM CONFIRM |
| samba — samba | The Netlogon server implementation in smbd in Samba 3.5.x and 3.6.x before 3.6.25, 4.0.x before 4.0.25, 4.1.x before 4.1.17, and 4.2.x before 4.2.0rc5 performs a free operation on an uninitialized stack pointer, which allows remote attackers to execute arbitrary code via crafted Netlogon packets that use the ServerPasswordSet RPC API, as demonstrated by packets reaching the _netr_ServerPasswordSet function in rpc_server/netlogon/srv_netlog_nt.c. | 2015-02-23 | 10.0 | CVE-2015-0240 CONFIRM CONFIRM CONFIRM UBUNTU SECTRACK DEBIAN REDHAT REDHAT REDHAT REDHAT REDHAT REDHAT REDHAT REDHAT REDHAT SUSE |
| sympies — wordpress_survey_and_poll | SQL injection vulnerability in the ajax_survey function in settings.php in the WordPress Survey and Poll plugin 1.1.7 for WordPress allows remote attackers to execute arbitrary SQL commands via the survey_id parameter in an ajax_survey action to wp-admin/admin-ajax.php. | 2015-02-26 | 7.5 | CVE-2015-2090 MISC EXPLOIT-DB MISC OSVDB |
| zhone_technologies — gpon_2520_firmware | Zhone GPON 2520 with firmware R4.0.2.566b allows remote attackers to cause a denial of service via a long string in the oldpassword parameter. | 2015-02-23 | 7.8 | CVE-2015-2055 EXPLOIT-DB |
Medium Vulnerabilities
| Primary Vendor — Product |
Description | Published | CVSS Score | Source & Patch Info |
|---|---|---|---|---|
| acobot_live_chat_&_contact_form_project — acobot_live_chat_&_contact_form | Multiple cross-site request forgery (CSRF) vulnerabilities in the Acobot Live Chat & Contact Form plugin 2.0 for WordPress allow remote attackers to hijack the authentication of administrators for requests that (1) change plugin settings or (2) conduct cross-site scripting (XSS) attacks via the acobot_token parameter in the acobot page to wp-admin/options-general.php. | 2015-02-20 | 6.8 | CVE-2015-2039 XF XF MISC |
| archmage_project — archmage | Directory traversal vulnerability in arCHMage 0.2.4 allows remote attackers to write to arbitrary files via a .. (dot dot) in a CHM file. | 2015-02-23 | 5.0 | CVE-2015-1589 CONFIRM XF MLIST MLIST |
| avatar_uploader_project — avatar_uploader | Unrestricted file upload vulnerability in the Avatar Uploader module before 6.x-1.3 for Drupal allows remote authenticated users to execute arbitrary PHP code by uploading a file with a PHP extension, then accessing it via unspecified vectors. | 2015-02-26 | 6.5 | CVE-2015-2087 BID |
| cfdbplugin — contact_form_db | Cross-site scripting (XSS) vulnerability in the Contact Form DB (aka CFDB and contact-form-7-to-database-extension) plugin 2.8.26 for WordPress allows remote attackers to inject arbitrary web script or HTML via the submit_time parameter in the CF7DBPluginSubmissions page to wp-admin/admin.php. | 2015-02-20 | 4.3 | CVE-2015-2040 XF MISC |
| cisco — ios | The Authentication Proxy feature in Cisco IOS does not properly handle invalid AAA return codes from RADIUS and TACACS+ servers, which allows remote attackers to bypass authentication in opportunistic circumstances via a connection attempt that triggers an invalid code, as demonstrated by a connection attempt with a blank password, aka Bug IDs CSCuo09400 and CSCun16016. | 2015-02-26 | 5.8 | CVE-2014-2188 |
| cisco — prime_lan_management_solution | Multiple cross-site scripting (XSS) vulnerabilities in the help pages in Cisco Common Services, as used in Cisco Prime LAN Management Solution (LMS) and Cisco Security Manager, allow remote attackers to inject arbitrary web script or HTML via unspecified parameters, aka Bug IDs CSCuq54654 and CSCun18263. | 2015-02-26 | 4.3 | CVE-2015-0594 |
| cisco — content_security_management_appliance | The web framework in Cisco AsyncOS on Email Security Appliance (ESA), Content Security Management Appliance (SMA), and Web Security Appliance (WSA) devices allows remote attackers to trigger redirects via a crafted HTTP header, aka Bug IDs CSCur44412, CSCur44415, CSCur89630, CSCur89636, CSCur89633, and CSCur89639. | 2015-02-21 | 4.3 | CVE-2015-0624 SECTRACK SECTRACK BID |
| cisco — ios | Race condition in the Neighbor Discovery (ND) protocol implementation in Cisco IOS and IOS XE allows remote attackers to cause a denial of service via a flood of Router Solicitation messages on the local network, aka Bug ID CSCuo67770. | 2015-02-26 | 5.7 | CVE-2015-0632 |
| cisco — unified_computing_system | The Integrated Management Controller (IMC) in Cisco Unified Computing System (UCS) 1.4(7h) and earlier on C-Series servers allows remote attackers to bypass intended access restrictions by sending crafted DHCP response packets on the local network, aka Bug ID CSCuf52876. | 2015-02-25 | 6.8 | CVE-2015-0633 |
| cisco — application_networking_manager | Cross-site request forgery (CSRF) vulnerability in the web GUI in Cisco Application Networking Manager (ANM), and Device Manager (DM) on Cisco 4710 Application Control Engine (ACE) appliances, allows remote attackers to hijack the authentication of arbitrary users, aka Bug ID CSCuo99753. | 2015-02-26 | 6.8 | CVE-2015-0651 |
| crossslide_jquery_project — crossslide_jquery | Multiple cross-site request forgery (CSRF) vulnerabilities in the CrossSlide jQuery (crossslide-jquery-plugin-for-wordpress) plugin 2.0.5 for WordPress allow remote attackers to hijack the authentication of administrators for requests that (1) change plugin settings or conduct cross-site scripting (XSS) attacks via the (2) csj_width, (3) csj_height, (4) csj_sleep, (5) csj_fade, or (6) upload_image parameter in the thisismyurl_csj.php page to wp-admin/options-general.php. | 2015-02-26 | 6.8 | CVE-2015-2089 MISC |
| cybernetikz — easy_social_icons | Cross-site request forgery (CSRF) vulnerability in the Easy Social Icons plugin before 1.2.3 for WordPress allows remote attackers to hijack the authentication of administrators for requests that conduct cross-site scripting (XSS) attacks via the image_file parameter in an edit action in the cnss_social_icon_add page to wp-admin/admin.php. | 2015-02-25 | 6.8 | CVE-2015-2084 CONFIRM EXPLOIT-DB FULLDISC MISC |
| d-link — dcs-931l_firmware | Cross-site request forgery (CSRF) vulnerability in D-Link DCS-931L with firmware 1.04 and earlier allows remote attackers to hijack the authentication of unspecified victims via unknown vectors. | 2015-02-23 | 6.8 | CVE-2015-2048 |
| dlguard — dlguard | Multiple cross-site scripting (XSS) vulnerabilities in DLGuard 5, 4.6, and 4.5 allow remote attackers to inject arbitrary web script or HTML via the (1) page, (2) c, or (3) redirect parameter to index.php or (4) search field (searchTerm parameter) in the main page. | 2015-02-24 | 4.3 | CVE-2015-2064 MISC MISC FULLDISC |
| e2fsprogs_project — e2fsprogs | Heap-based buffer overflow in closefs.c in the libext2fs library in e2fsprogs before 1.42.12 allows local users to execute arbitrary code by causing a crafted block group descriptor to be marked as dirty. NOTE: this vulnerability exists because of an incomplete fix for CVE-2015-0247. | 2015-02-24 | 4.6 | CVE-2015-1572 UBUNTU DEBIAN |
| etouch — samepage | Directory traversal vulnerability in cm/newui/blog/export.jsp in eTouch SamePage Enterprise Edition 4.4.0.0.239 allows remote authenticated users to read arbitrary files via a .. (dot dot) in the filepath parameter. | 2015-02-24 | 4.0 | CVE-2015-2071 EXPLOIT-DB FULLDISC MISC OSVDB |
| gnu — glibc | The send_dg function in resolv/res_send.c in GNU C Library (aka glibc or libc6) before 2.20 does not properly reuse file descriptors, which allows remote attackers to send DNS queries to unintended locations via a large number of request that trigger a call to the getaddrinfo function. | 2015-02-24 | 5.0 | CVE-2013-7423 CONFIRM CONFIRM MLIST |
| google — play_services_sdk | The GoogleAuthUtil.getToken method in the Google Play services SDK before 2015 sets parameters in OAuth token requests upon finding a corresponding _opt_ parameter in the Bundle extras argument, which allows attackers to bypass an intended consent dialog and retrieve tokens for arbitrary OAuth scopes including the SID and LSID scopes, and consequently obtain access to a Google account, via a crafted application, as demonstrated by setting the has_permission=1 parameter value upon finding _opt_has_permission in that argument. | 2015-02-22 | 4.3 | CVE-2014-7922 MISC MISC |
| ibm — rational_insight | IBM Rational Insight 1.1.1.5 allows remote attackers to bypass authentication and obtain sensitive information via a crafted request to a Jazz Reporting Service (JRS) report URL. | 2015-02-24 | 5.0 | CVE-2014-6115 |
| ilch — cms | Cross-site request forgery (CSRF) vulnerability in Ilch CMS allows remote attackers to hijack the authentication of administrators for requests that add a value to a profile field via a profilefields request to admin.php. | 2015-02-25 | 6.8 | CVE-2015-2083 MISC |
| komodia — redirector_sdk | The SDK for Komodia Redirector with SSL Digestor, as used in Lavasoft Ad-Aware Web Companion 1.1.885.1766 and Ad-Aware AdBlocker (alpha) 1.3.69.1, Qustodio for Windows, Atom Security, Inc. StaffCop 5.8, and other products, uses the same X.509 certificate private key for a root CA certificate across different customers’ installations, which makes it easier for man-in-the-middle attackers to spoof SSL servers by leveraging knowledge of this key, as originally reported for Superfish VisualDiscovery on certain Lenovo Notebook laptop products. | 2015-02-24 | 5.0 | CVE-2015-2077 MISC MISC MISC MISC SECTRACK CONFIRM CONFIRM MISC MISC MISC |
| komodia — redirector_sdk | The SDK for Komodia Redirector with SSL Digestor, as used in Lavasoft Ad-Aware Web Companion 1.1.885.1766 and Ad-Aware AdBlocker (alpha) 1.3.69.1, Qustodio for Windows, Atom Security, Inc. StaffCop 5.8, and other products, does not properly verify X.509 certificates from SSL servers, which allows man-in-the-middle attackers to spoof servers, a different vulnerability than CVE-2015-2077. | 2015-02-24 | 5.0 | CVE-2015-2078 MISC MISC SECTRACK MISC MISC |
| kony — enterprise_mobile_management | Kony Management (aka Enterprise Mobile Management or EMM) 1.2 and earlier allows remote authenticated users to read (1) arbitrary messages via the messageId parameter to selfservice/managedevice/getMessageBody or (2) requests via the requestId parameter to selfservice/devicemgmt/getDeviceInfoTab.htm. | 2015-02-24 | 4.0 | CVE-2014-8487 BID BUGTRAQ |
| magmi — magmi | Directory traversal vulnerability in web/ajax_pluginconf.php in the MAGMI (aka Magento Mass Importer) plugin for Magento Server allows remote attackers to read arbitrary files via a .. (dot dot) in the file parameter. | 2015-02-24 | 5.0 | CVE-2015-2067 EXPLOIT-DB MISC |
| magmi — magmi | Multiple cross-site scripting (XSS) vulnerabilities in the MAGMI (aka Magento Mass Importer) plugin for Magento Server allow remote attackers to inject arbitrary web script or HTML via the (1) profile parameter to web/magmi.php or (2) QUERY_STRING to web/magmi_import_run.php. | 2015-02-24 | 4.3 | CVE-2015-2068 EXPLOIT-DB MISC |
| mcafee — mcafee_agent | The log viewer in McAfee Agent (MA) before 4.8.0 Patch 3 and 5.0.0, when the “Accept connections only from the ePO server” option is disabled, allows remote attackers to conduct clickjacking attacks via a crafted web page, aka an “http-generic-click-jacking” vulnerability. | 2015-02-23 | 4.3 | CVE-2015-2053 |
| mozilla — firefox | The UITour::onPageEvent function in Mozilla Firefox before 36.0 does not ensure that an API call originates from a foreground tab, which allows remote attackers to conduct spoofing and clickjacking attacks by leveraging access to a UI Tour web site. | 2015-02-25 | 4.3 | CVE-2015-0819 CONFIRM SECTRACK BID |
| mozilla — firefox | Mozilla Firefox before 36.0 allows user-assisted remote attackers to read arbitrary files or execute arbitrary JavaScript code with chrome privileges via a crafted web site that is accessed with unspecified mouse and keyboard actions. | 2015-02-25 | 6.8 | CVE-2015-0821 CONFIRM SECTRACK BID |
| mozilla — firefox | The Form Autocompletion feature in Mozilla Firefox before 36.0, Firefox ESR 31.x before 31.5, and Thunderbird before 31.5 allows remote attackers to read arbitrary files via crafted JavaScript code. | 2015-02-25 | 4.3 | CVE-2015-0822 CONFIRM SECTRACK SECTRACK BID |
| mozilla — firefox | The mozilla::layers::BufferTextureClient::AllocateForSurface function in Mozilla Firefox before 36.0 allows remote attackers to cause a denial of service (out-of-bounds write of zero values, and application crash) via vectors that trigger use of DrawTarget and the Cairo library for image drawing. | 2015-02-25 | 5.0 | CVE-2015-0824 CONFIRM SECTRACK BID |
| mozilla — firefox | Stack-based buffer underflow in the mozilla::MP3FrameParser::ParseBuffer function in Mozilla Firefox before 36.0 allows remote attackers to obtain sensitive information from process memory via a malformed MP3 file that improperly interacts with memory allocation during playback. | 2015-02-25 | 4.3 | CVE-2015-0825 CONFIRM SECTRACK BID |
| mozilla — firefox | The nsTransformedTextRun::SetCapitalization function in Mozilla Firefox before 36.0 allows remote attackers to execute arbitrary code or cause a denial of service (out-of-bounds read of heap memory) via a crafted Cascading Style Sheets (CSS) token sequence that triggers a restyle or reflow operation. | 2015-02-25 | 6.8 | CVE-2015-0826 CONFIRM SECTRACK BID |
| mozilla — firefox | Heap-based buffer overflow in the mozilla::gfx::CopyRect function in Mozilla Firefox before 36.0, Firefox ESR 31.x before 31.5, and Thunderbird before 31.5 allows remote attackers to obtain sensitive information from uninitialized process memory via a malformed SVG graphic. | 2015-02-25 | 4.3 | CVE-2015-0827 CONFIRM SECTRACK SECTRACK BID |
| mozilla — firefox | Double free vulnerability in the nsXMLHttpRequest::GetResponse function in Mozilla Firefox before 36.0, when a nonstandard memory allocator is used, allows remote attackers to execute arbitrary code or cause a denial of service (heap memory corruption) via crafted JavaScript code that makes an XMLHttpRequest call with zero bytes of data. | 2015-02-25 | 6.8 | CVE-2015-0828 CONFIRM CONFIRM SECTRACK BID |
| mozilla — firefox | Buffer overflow in libstagefright in Mozilla Firefox before 36.0 allows remote attackers to execute arbitrary code via a crafted MP4 video that is improperly handled during playback. | 2015-02-25 | 6.8 | CVE-2015-0829 CONFIRM SECTRACK BID |
| mozilla — firefox | The WebGL implementation in Mozilla Firefox before 36.0 does not properly allocate memory for copying an unspecified string to a shader’s compilation log, which allows remote attackers to cause a denial of service (application crash) via crafted WebGL content. | 2015-02-25 | 5.0 | CVE-2015-0830 CONFIRM SECTRACK BID |
| mozilla — firefox | Use-after-free vulnerability in the mozilla::dom::IndexedDB::IDBObjectStore::CreateIndex function in Mozilla Firefox before 36.0, Firefox ESR 31.x before 31.5, and Thunderbird before 31.5 allows remote attackers to execute arbitrary code or cause a denial of service (heap memory corruption) via crafted content that is improperly handled during IndexedDB index creation. | 2015-02-25 | 6.8 | CVE-2015-0831 CONFIRM SECTRACK SECTRACK BID |
| mozilla — firefox | Mozilla Firefox before 36.0 does not properly recognize the equivalence of domain names with and without a trailing . (dot) character, which allows man-in-the-middle attackers to bypass the HPKP and HSTS protection mechanisms by constructing a URL with this character and leveraging access to an X.509 certificate for a domain with this character. | 2015-02-25 | 5.0 | CVE-2015-0832 CONFIRM BID |
| mozilla — firefox | Multiple untrusted search path vulnerabilities in updater.exe in Mozilla Firefox before 36.0, Firefox ESR 31.x before 31.5, and Thunderbird before 31.5 on Windows, when the Maintenance Service is not used, allow local users to gain privileges via a Trojan horse DLL in (1) the current working directory or (2) a temporary directory, as demonstrated by bcrypt.dll. | 2015-02-25 | 6.9 | CVE-2015-0833 CONFIRM SECTRACK SECTRACK BID |
| mozilla — firefox | The WebRTC subsystem in Mozilla Firefox before 36.0 recognizes turns: and stuns: URIs but accesses the TURN or STUN server without using TLS, which makes it easier for man-in-the-middle attackers to discover credentials by spoofing a server and completing a brute-force attack within a short time window. | 2015-02-25 | 4.3 | CVE-2015-0834 CONFIRM SECTRACK BID |
| openstack — image_registry_and_delivery_service_(glance) | OpenStack Image Registry and Delivery Service (Glance) 2014.2 through 2014.2.2 does not properly remove images, which allows remote authenticated users to cause a denial of service (disk consumption) by creating a large number of images using the task v2 API and then deleting them before the uploads finish, a different vulnerability than CVE-2015-1881. | 2015-02-24 | 4.0 | CVE-2014-9684 CONFIRM |
| openstack — image_registry_and_delivery_service_(glance) | OpenStack Image Registry and Delivery Service (Glance) 2014.2 through 2014.2.2 does not properly remove images, which allows remote authenticated users to cause a denial of service (disk consumption) by creating a large number of images using the task v2 API and then deleting them, a different vulnerability than CVE-2014-9684. | 2015-02-24 | 4.0 | CVE-2015-1881 CONFIRM |
| piwigo — piwigo | SQL injection vulnerability in Piwigo before 2.7.4, when all filters are activated, allows remote authenticated users to execute arbitrary SQL commands via the filter_level parameter in a “Refresh photo set” action in the batch_manager page to admin.php. | 2015-02-20 | 6.0 | CVE-2015-1517 BID BUGTRAQ MISC |
| piwigo — piwigo | Cross-site scripting (XSS) vulnerability in the administrative backend in Piwigo before 2.7.4 allows remote attackers to inject arbitrary web script or HTML via the page parameter to admin.php. | 2015-02-20 | 4.3 | CVE-2015-2034 MISC MISC FULLDISC MISC |
| piwigo — piwigo | SQL injection vulnerability in the administrative backend in Piwigo before 2.7.4 allows remote adminsitrators to execute arbitrary SQL commands via the user parameter in the history page to admin.php. | 2015-02-20 | 6.5 | CVE-2015-2035 MISC MISC FULLDISC MISC |
| redhat — jboss_uberfire | The UberFire Framework 0.3.x does not properly restrict paths, which allows remote attackers to (1) execute arbitrary code by uploading crafted content to FileUploadServlet or (2) read arbitrary files via vectors involving FileDownloadServlet. | 2015-02-20 | 6.8 | CVE-2014-8114 CONFIRM |
| redhat — jboss_kie_workbench | The default authorization constrains in KIE Workbench 6.0.x allows remote authenticated users to read or write to arbitrary files, bypass intended access restrictions, and possibly have other unspecified impact via unknown vectors. | 2015-02-20 | 6.5 | CVE-2014-8115 CONFIRM |
| samsung — ipolis_device_manager | Buffer overflow in the XnsSdkDeviceIpInstaller.ocx ActiveX control in Samsung iPOLiS Device Manager 1.12.2 allows remote attackers to execute arbitrary code via a long string in the first argument to the (1) ReadConfigValue or (2) WriteConfigValue function. | 2015-02-24 | 6.8 | CVE-2015-0555 FULLDISC |
| sierra_wireless — sierra_wireless_aircard_760s | CRLF injection vulnerability in export.cfg in the web-based administrative console for Sierra Wireless AirCard 760S, 762S, and 763S allows remote attackers to inject arbitrary headers via CRLF sequences in the save parameter. | 2015-02-23 | 4.3 | CVE-2015-2054 FULLDISC |
| speed_software — explorer | Directory traversal vulnerability in the Speed Root Explorer application before 3.2 for Android and the Speed Explorer application before 2.2 for Android allows remote attackers to write to arbitrary files via a crafted filename. | 2015-02-24 | 5.0 | CVE-2014-9282 |
| synck_graphica — mailform_pro_cgi | SYNCK GRAPHICA Mailform Pro CGI 4.1.4 and 4.1.5, when the mailauth module is enabled, does not properly send e-mail messages, which allows remote attackers to execute arbitrary code via unspecified vectors. | 2015-02-26 | 6.8 | CVE-2015-0883 CONFIRM |
| term_queue_project — term_queue | Cross-site scripting (XSS) vulnerability in unspecified administration pages in the Term Queue module before 6.x-1.1 for Drupal allows remote attackers to inject arbitrary web script or HTML via unknown vectors. | 2015-02-26 | 4.3 | CVE-2015-2088 BID |
| textangular — textangular | Cross-site scripting (XSS) vulnerability in textAngular-sanitize.js in textAngular before 1.3.7 allows remote attackers to inject arbitrary web script or HTML via unspecified vectors to the editor. | 2015-02-20 | 4.3 | CVE-2015-0167 XF |
| unit4 — prosoft_hrms | Cross-site scripting (XSS) vulnerability in Login.aspx in UNIT4 Prosoft HRMS before 8.14.330.43 allows remote attackers to inject arbitrary web script or HTML via the txtUserID parameter. | 2015-02-25 | 4.3 | CVE-2015-2082 BUGTRAQ MISC |
| vanillaforums — vanilla_forums | Multiple cross-site scripting (XSS) vulnerabilities in Vanilla Forums before 2.0.18.13 and 2.1.x before 2.1.1 allow remote attackers to inject arbitrary web script or HTML via unspecified vectors. | 2015-02-25 | 4.3 | CVE-2014-9685 |
| visualware — myconnection_server | Multiple cross-site scripting (XSS) vulnerabilities in Visualware MyConnection Server 8.2b allow remote attackers to inject arbitrary web script or HTML via the (1) bt, (2) variable, or (3) et parameter to myspeed/db/historyitem. | 2015-02-25 | 4.3 | CVE-2015-2043 MISC |
| woothemes — woocommerce | Cross-site scripting (XSS) vulnerability in the WooCommerce plugin before 2.2.11 for WordPress allows remote attackers to inject arbitrary web script or HTML via the QUERY_STRING in the wc-reports page to wp-admin/admin.php. | 2015-02-24 | 4.3 | CVE-2015-2069 CONFIRM FULLDISC |
| zen-cart.jp — zen_cart | Multiple cross-site scripting (XSS) vulnerabilities in zencart-ja (aka Zen Cart Japanese edition) 1.3 jp through 1.3.0.2 jp8 and 1.5 ja through 1.5.1 ja allow remote attackers to inject arbitrary web script or HTML via a crafted parameter, related to admin/includes/init_includes/init_sanitize.php and includes/init_includes/init_sanitize.php. | 2015-02-26 | 4.3 | CVE-2015-0882 CONFIRM JVN |
Low Vulnerabilities
| Primary Vendor — Product |
Description | Published | CVSS Score | Source & Patch Info |
|---|---|---|---|---|
| ibm — tivoli_storage_manager | dsmtca in the client in IBM Tivoli Storage Manager (TSM) 5.4.x, 5.5.x, 6.x before 6.4.3, and 7.1.x before 7.1.2 allows local users to discover the backup/restore encryption-key password via unspecified vectors. | 2015-02-24 | 2.1 | CVE-2014-4818 SECTRACK AIXAPAR |
| mozilla — firefox | Mozilla Firefox before 36.0 does not properly restrict transitions of JavaScript objects from a non-extensible state to an extensible state, which allows remote attackers to bypass a Caja Compiler sandbox protection mechanism or a Secure EcmaScript sandbox protection mechanism via a crafted web site. | 2015-02-25 | 2.6 | CVE-2015-0820 CONFIRM BID |
| panopoly_magic_project — panopoly_magic | Cross-site scripting (XSS) vulnerability in the live preview in the Panopoly Magic module before 7.x-1.17 for Drupal allows remote authenticated users to inject arbitrary web script or HTML via a pane title. | 2015-02-26 | 3.5 | CVE-2015-2086 BID |
| puppetlabs — facter | Puppet Labs Facter 1.6.0 through 2.4.0 allows local users to obtains sensitive Amazon EC2 IAM instance metadata by reading a fact for an Amazon EC2 node. | 2015-02-23 | 2.1 | CVE-2015-1426 |
| redhat — jboss_enterprise_application_platform | PicketBox and JBossSX, as used in Red Hat JBoss Enterprise Application Platform (JBEAP) 6.2.2 and JBoss BRMS before 6.0.3 roll up patch 2, allows remote authenticated users to read and modify the application sever configuration and state by deploying a crafted application. | 2015-02-20 | 3.6 | CVE-2014-0005 |
| typo3 — typo3 | The rsaauth extension in TYPO3 4.3.0 through 4.3.14, 4.4.0 through 4.4.15, 4.5.0 through 4.5.39, and 4.6.0 through 4.6.18, when configured for the frontend, allows remote attackers to bypass authentication via a password that is casted to an empty value. | 2015-02-23 | 2.6 | CVE-2015-2047 CONFIRM MLIST MLIST DEBIAN |
This product is provided subject to this Notification and this Privacy & Use policy.
WordPress WP All 3.2.3 Shell Upload
WordPress WP All Import plugin versions 3.2.3 and below suffer from a remote shell upload vulnerability.
tmap 0.1
tmap is a fast multi-threaded port scanner that tunnels through TOR.
Slim Framework – (CVE-2015-2171, PHP Object Injection), Other Vulnerabilities
Posted by Scott Arciszewski on Mar 02
Product: Slim PHP Framework
Website: http://www.slimframework.com/
Affected versions: 2.5.0 and lower
Fixed in: 2.6.0 (released 2015-03-01)
CVSS Score: I don’t care. Does anybody really?
“””
Slim has super-secure cryptography using military-grade encryption. Slim
uses your unique key to encrypt session and cookie data before persisting
data to disk.
“””
Wow, sounds great. Let’s look under the hood….
CVE-2015-1187: D-Link DIR-636L Remote Command Injection – Incorrect Authentication
Posted by csirt on Mar 02
#############################################################################
#
# SWISSCOM CSIRT SECURITY ADVISORY – http://www.swisscom.com/security
#
#############################################################################
#
# CVE ID: CVE-2015-1187
# Product: D-Link DIR636L
# Vendor: D-Link
# Subject: Remote Command Injection – Incorrect Authentication
# Effect: Remotely exploitable
# Author: Tiago Caetano Henriques,…
PandaLabs neutralized 75 million new malware samples in 2014, twice as many as in 2013
PandaLabs, the anti-malware laboratory of Panda Security detected and neutralized 75 million malware samples in 2014. This figure more than doubles the number recorded in 2013: nearly 30 million new malware strains.
In all, the total number of malware specimens detected by PandaLabs throughout its history has reached 220 million, which means that 34 percent of all malware ever created was coded in 2014. In fact, last year Panda Security recorded an average of 200,000 new malware strains per day. The year 2014 can be considered the year of massive cyber-attacks, with some of the world’s biggest corporations falling victim to large-scale data breaches.
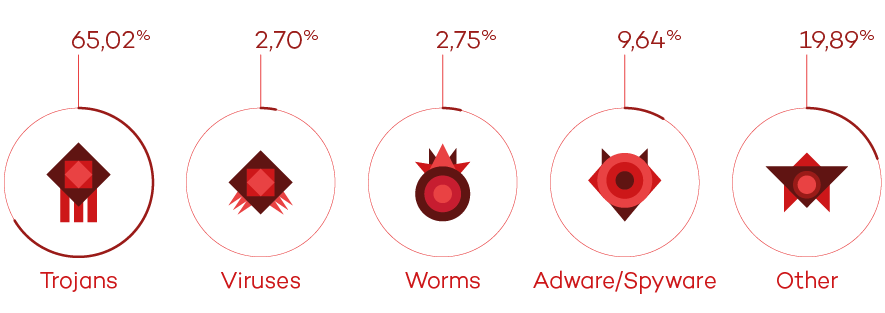
Trojans continue to account for most new malware
Trojans are still the most common type of malware way ahead of other malware specimens. In fact, in 2014 Trojans accounted for almost 70 percent of all new malware created, followed by viruses (12.33 percent), other malware (10 percent), worms (6 percent) and adware/spyware (3 percent). In this respect, CryptoLocker was one of the most destructive Trojans unleashed last year. “CryptoLocker is one of the nastiest pieces of malware to have targeted users in 2014. This ransomware encrypts victims’ files and requires a ransom in order to decrypt them. Thousands of computers have fallen victim to it, from home users to businesses and financial institutions”, said Luis Corrons, Technical Director of PandaLabs at Panda Security.
Malware and infections
Trojans, once again, accounted for more infections (65 percent) than any other malware, although there was a notable increase in the ‘Other’ category. This category includes PUPs (Potentially Unwanted Programs): applications which, despite not being malicious per se, install unwanted software without properly informing the user.
China tops the list of infections
Despite being one of the worst years for IT security, the global infection rate in 2014 was 30.42 percent, a significant decrease on 2013’s figure. Country by country, China once again had the most infections with a rate of 49 percent, followed by Ecuador (42.33 percent) and Turkey (41.53 percent). Theses countries were also at the top of the infection rankings last year, although in a different order: China, Turkey and Ecuador.
Other countries with rates above the global average in 2014 include Colombia (33 percent), Uruguay (33 percent) and Chile (31 percent).
Sweden the safest country
Europe was the area with the lowest infection rate, with nine countries ranked among the ten least infected nations, whereas Japan was the only non-European country to appear in the ranking. The list was topped by Scandinavian countries: Sweden (20 percent), Norway (20 percent) and Finland (21 percent).
“We live in an Internet-connected world, and as such we are exposed to cyber-attacks now more than ever before. Security threats will increase in 2015, and both companies and home users must prepare themselves to respond to them. It is not a question of whether their security will be compromised but rather when and how, so in this case prevention is key”, concluded Corrons.
The full report is available here.
The post PandaLabs neutralized 75 million new malware samples in 2014, twice as many as in 2013 appeared first on MediaCenter Panda Security.
AVG Puts People First for Mobile Security
AMSTERDAM and SAN FRANCISCO – March, 2, 2015 – AVG® Technologies N.V. (NYSE: AVG), the online security company™ for 197 million active users, today previewed the next version of the AVG Zen™ platform to mobile operators and original equipment manufacturers (OEM). With the consumer launch currently planned for later this year, AVG Zen delivers a new family-first approach to security, including support for industry partner apps and wearables on customers’ devices, all in one place.
With digital lives becoming more complex in an Internet of Things world, security is now about protecting people as well as their devices and personal data. The next version of AVG Zen delivers three core pillars:
- A subscription security service for families that includes AVG AntiVirus and AVG Cleaner across their devices to give them confidence in their digital lifestyle. AVG AntiVirus for Android™ was the first mobile security product to enter the 100-500 million downloads category on the Google® Play™ store.
- A dedicated set of family products from Location Labs by AVG including phone controls and location services. Already offered by the top four US mobile operators, extending the availability of these products through AVG Zen makes it even easier for families to communicate and share location. Phone controls gives parents peace of mind when giving their children their first mobile device, allowing them to monitor and set limits.
- A platform for mobile operators to deliver context-aware solutions for core services. This could be, for example, notifying a user if they are running low on storage or approaching their data limit. AVG Zen is open to partners looking to expand their offerings directly to AVG’s 197 million end users.
With global smartphone subscribers reaching 3.5 billion by 2019, industry figures calculate suppliers of Internet of Things product and service providers will generate incremental revenue exceeding $300 billion by 2020. Research into data management and security services estimates these alone will drive revenues in excess of $1.8 billion in the same timeframe.
AVG Zen enables mobile operators to provide context-aware alerts, updates and information direct to the customer to give them control and transparency of their security across their family, data, and devices.
“People not only want their online rights to be recognized, they want more control and responsibility over their online actions and those of family members. But today, their online experience is still disconnected. In the 2015 consumer trust survey we carried out with MEF, 72 percent were not happy sharing personal data with apps, 40 percent named privacy and security as important when choosing a mobile device, and another 34 percent relied on dedicated security apps to protect them,” said Yuval Ben-Itzhak, Chief Technology Officer, AVG Technologies. “Mobile operators and online security companies hold a trusted position in consumers’ lives and we have the opportunity to transform their connected experience by bringing everything together all in one central place.”
About AVG Technologies
AVG is the online security company providing leading software and services to secure devices, data and people. Over 197 million active users, as of December 31, 2014, use AVG´s products and services. AVG’s Consumer portfolio includes internet security, performance optimization, and personal privacy and identity protection for mobile devices and desktops. The AVG Business portfolio – delivered by managed service providers, VARs and resellers – offers IT administration, control and reporting, integrated security, and mobile device management that simplify and protect businesses.
All trademarks are the property of their respective owners.
Contacts:
US
Katie Han
Waggener Edstrom for AVG
+ 1 (212) 551 4807
UK
Samantha Woodman
Waggener Edstrom for AVG
+ 44 (0)20 7632 3840
WordPress Slimstat Plugin SQL Injection
An SQL injection vulnerability has been reported in WordPress Slimstat Plugin. Successful exploitation of this vulnerability would allow a remote attacker to execute arbitrary SQL commands on the affected system.
WordPress Redirection Page Plugin Cross Site Request Forgery (CVE-2015-1580)
A cross-site request forgery (CSRF) vulnerability has been reported in WordPress Redirection Page Plugin. An attacker could exploit this vulnerability by convincing the user to follow a malicious link or visit an attacker controlled website.