oclHashcat is an advanced GPU hash cracking utility that includes the World’s fastest md5crypt, phpass, mscash2 and WPA / WPA2 cracker. It also has the first and only GPGPU-based rule engine, focuses on highly iterated modern hashes, single dictionary-based attacks, and more. NVidia version.
Monthly Archives: April 2015
oclHashcat For AMD 1.36
oclHashcat is an advanced GPU hash cracking utility that includes the World’s fastest md5crypt, phpass, mscash2 and WPA / WPA2 cracker. It also has the first and only GPGPU-based rule engine, focuses on highly iterated modern hashes, single dictionary-based attacks, and more. AMD version.
Malware authors go a step further to access bank accounts
Malware authors like to play hide-and-seek. Hiding executable files inside PDFs and Microsoft Office documents then emailing them as attachments are nothing new, but sometimes one layer isn’t enough. This Avast Virus Lab analysis peels back the layers of a new threat.
Malware authors continually surprise us with their creativity. In an effort to trick banking customers into revealing the login credentials for their online account, cycbercrooks are using the trust people have in Microsoft Office to make them execute banking malware on their own computers. Here’s how it works:
Typically, spam emails contain executable files that can harm a victim’s computer and steal private information. In the layered version, they have PDFs or Microsoft Office documents attached that contain a malicious executable file. We recently found an email that had an added layer and decided to analyze the email.
The email, disguised as a financially-related message from a legitimate company, informed the recipient that an invoice was due and had a PDF file attached. Embedded inside the malicious PDF was a Microsoft Office document and simple java script that dropped and executed the DOC file.
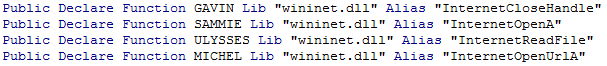
![]() Inside the DOC file we found malicious macro code, which users must activate, as the code is disabled by Microsoft Office by default. The code obfuscates DOC files by creating new documents with unique methods names, variable names, and URLs, making it difficult to detect the malicious files.
Inside the DOC file we found malicious macro code, which users must activate, as the code is disabled by Microsoft Office by default. The code obfuscates DOC files by creating new documents with unique methods names, variable names, and URLs, making it difficult to detect the malicious files.
When we analyzed the malicious macro code, we found some hints that helped us with our analysis. In this sample it was a function called MICHEL.
We already knew this function would open the URL with the malicious file, and when we found this function in one of the modules, we were able to find the download path.
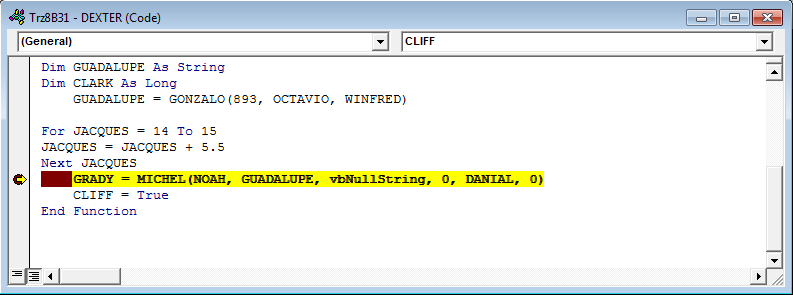
The address is stored as a GUADALUPE variable. The URL is unique for each sample and leads to the download of a malicious PE file.
![]()
The PE file would act as an information stealer, stealing login credentials from banking sites like
- Santander, whose principal market is in the Northeastern United States
- Ulster bank, based in Ireland
- From Google accounts
- Microsoft
How to protect yourself from banking malware
Our number 1 recommendation is keep your security software updated. Avast streams hundreds of updates every day to your devices, so you will stay protected. For example, the executable file downloaded by the malicious Microsoft Office document belongs to a banker family evolved from infamous Zeus. This variant is also known as a Dridex Botnet. At the time of writing this post, the botnet is still active, but the malware itself is inactive. Avast detects it as Win32: Pierre-A.
Clever cybercrooks use social engineering to manipulate their victims. Use extreme caution when opening emails related to your finances until you can verify the legitimacy.
Samples related to this analysis:
[ MDVSA-2015:212 ] java-1.7.0-openjdk
-----BEGIN PGP SIGNED MESSAGE----- Hash: SHA1 _______________________________________________________________________ Mandriva Linux Security Advisory MDVSA-2015:212 http://www.mandriva.com/en/support/security/ _______________________________________________________________________ Package : java-1.7.0-openjdk Date : April 27, 2015 Affected: Business Server 1.0 _______________________________________________________________________ Problem Description: Updated java-1.7.0 packages fix security vulnerabilities: An off-by-one flaw, leading to a buffer overflow, was found in the font parsing code in the 2D component in OpenJDK. A specially crafted font file could possibly cause the Java Virtual Machine to execute arbitrary code, allowing an untrusted Java application or applet to bypass Java sandbox restrictions (CVE-2015-0469). A flaw was found in the way the Hotspot component in OpenJDK handled phantom references. An untrusted Java application or applet cou
FireHOL 2.0.3
FireHOL a simple yet powerful way to configure stateful iptables firewalls. It can be used for almost any purpose, including control of any number of internal/external/virtual interfaces, control of any combination of routed traffic, setting up DMZ routers and servers, and all kinds of NAT. It provides strong protection (flooding, spoofing, etc.), transparent caches, source MAC verification, blacklists, whitelists, and more. Its goal is to be completely abstracted and powerful but also easy to use, audit, and understand.
CVE-2015-2115 (capture_and_route_software)
Unspecified vulnerability in HP Capture and Route Software (HPCR) 1.3 before Patch 7, 1.3 FP1 before Patch 1, and 1.4 before Patch 1 allows remote authenticated users to obtain sensitive information via unknown vectors.
Ubuntu Security Notice USN-2570-1
Ubuntu Security Notice 2570-1 – An issue was discovered in the HTML parser in Blink. If a user were tricked in to opening a specially crafted website, an attacker could potentially exploit this to bypass same-origin restrictions. An issue was discovered in the Web Audio API implementation in Blink. If a user were tricked in to opening a specially crafted website, an attacker could potentially exploit this to bypass same-origin restrictions. Various other issues were also addressed.
Open-Xchange Server 6 / OX AppSuite Cross Site Scripting
Open-Xchange Server 6 and OX AppSuite versions 7.6.1 and below suffer from multiple cross site scripting vulnerabilities.
Elasticsearch Directory Traversal
All Elasticsearch versions prior to 1.5.2 and 1.4.5 are vulnerable to a directory traversal attack that allows an attacker to retrieve files from the server running Elasticsearch.
WordPress 4.2 Cross Site Scripting
WordPress version 4.2 suffers from a persistent cross site scripting vulnerability.