Cross-site scripting (XSS) vulnerability in the administrative web interface in Cisco Unified MeetingPlace 8.6(1.9) allows remote attackers to inject arbitrary web script or HTML via unspecified vectors, aka Bug ID CSCus95857.
Monthly Archives: April 2015
DSA-3231 subversion – security update
Several vulnerabilities were discovered in Subversion, a version control
system. The Common Vulnerabilities and Exposures project identifies the
following problems:
RHSA-2015:0858-1: Important: java-1.6.0-sun security update
Red Hat Enterprise Linux: Updated java-1.6.0-sun packages that fix several security issues are now
available for Oracle Java for Red Hat Enterprise Linux 5, 6, and 7.
Red Hat Product Security has rated this update as having Important security
impact. Common Vulnerability Scoring System (CVSS) base scores, which give
detailed severity ratings, are available for each vulnerability from the
CVE links in the References section.
CVE-2005-1080, CVE-2015-0458, CVE-2015-0459, CVE-2015-0460, CVE-2015-0469, CVE-2015-0477, CVE-2015-0478, CVE-2015-0480, CVE-2015-0488, CVE-2015-0491
RHSA-2015:0857-1: Critical: java-1.7.0-oracle security update
Red Hat Enterprise Linux: Updated java-1.7.0-oracle packages that fix several security issues are now
available for Oracle Java for Red Hat Enterprise Linux 5, 6, and 7.
Red Hat Product Security has rated this update as having Critical security
impact. Common Vulnerability Scoring System (CVSS) base scores, which give
detailed severity ratings, are available for each vulnerability from the
CVE links in the References section.
CVE-2005-1080, CVE-2015-0458, CVE-2015-0459, CVE-2015-0460, CVE-2015-0469, CVE-2015-0477, CVE-2015-0478, CVE-2015-0480, CVE-2015-0484, CVE-2015-0488, CVE-2015-0491, CVE-2015-0492
RHSA-2015:0856-1: Moderate: postgresql92-postgresql security update
RHN Satellite and Proxy: Updated postgresql packages that fix multiple security issues are now
available for Red Hat Satellite 5.7.
Red Hat Product Security has rated this update as having Moderate security
impact. Common Vulnerability Scoring System (CVSS) base scores, which give
detailed severity ratings, are available for each vulnerability from the
CVE links in the References section.
CVE-2014-8161, CVE-2015-0241, CVE-2015-0243, CVE-2015-0244
USN-2572-1: PHP vulnerabilities
Ubuntu Security Notice USN-2572-1
20th April, 2015
php5 vulnerabilities
A security issue affects these releases of Ubuntu and its
derivatives:
- Ubuntu 14.10
- Ubuntu 14.04 LTS
- Ubuntu 12.04 LTS
- Ubuntu 10.04 LTS
Summary
Several security issues were fixed in PHP.
Software description
- php5
– HTML-embedded scripting language interpreter
Details
It was discovered that PHP incorrectly handled cleanup when used with
Apache 2.4. A remote attacker could use this issue to cause PHP to crash,
resulting in a denial of service, or possibly execute arbitrary code.
(CVE-2015-3330)
It was discovered that PHP incorrectly handled opening tar, zip or phar
archives through the PHAR extension. A remote attacker could use this issue
to cause PHP to crash, resulting in a denial of service, or possibly
execute arbitrary code. (CVE-2015-3329)
It was discovered that PHP incorrectly handled regular expressions. A
remote attacker could use this issue to cause PHP to crash, resulting in a
denial of service, or possibly execute arbitrary code. (CVE-2015-2305)
Paulos Yibelo discovered that PHP incorrectly handled moving files when a
pathname contained a null character. A remote attacker could use this issue
to possibly bypass filename restrictions. This issue only applied to
Ubuntu 14.04 LTS and Ubuntu 14.10. (CVE-2015-2348)
It was discovered that PHP incorrectly handled unserializing PHAR files. A
remote attacker could use this issue to cause PHP to possibly expose
sensitive information. (CVE-2015-2783)
Taoguang Chen discovered that PHP incorrectly handled unserializing certain
objects. A remote attacker could use this issue to cause PHP to crash,
resulting in a denial of service, or possibly execute arbitrary code.
(CVE-2015-2787)
Update instructions
The problem can be corrected by updating your system to the following
package version:
- Ubuntu 14.10:
-
php5-cli
5.5.12+dfsg-2ubuntu4.4
-
php5-cgi
5.5.12+dfsg-2ubuntu4.4
-
libapache2-mod-php5
5.5.12+dfsg-2ubuntu4.4
-
php5-fpm
5.5.12+dfsg-2ubuntu4.4
- Ubuntu 14.04 LTS:
-
php5-cli
5.5.9+dfsg-1ubuntu4.9
-
php5-cgi
5.5.9+dfsg-1ubuntu4.9
-
libapache2-mod-php5
5.5.9+dfsg-1ubuntu4.9
-
php5-fpm
5.5.9+dfsg-1ubuntu4.9
- Ubuntu 12.04 LTS:
-
php5-cli
5.3.10-1ubuntu3.18
-
php5-cgi
5.3.10-1ubuntu3.18
-
libapache2-mod-php5
5.3.10-1ubuntu3.18
-
php5-fpm
5.3.10-1ubuntu3.18
- Ubuntu 10.04 LTS:
-
php5-cli
5.3.2-1ubuntu4.30
-
php5-cgi
5.3.2-1ubuntu4.30
-
libapache2-mod-php5
5.3.2-1ubuntu4.30
To update your system, please follow these instructions:
https://wiki.ubuntu.com/Security/Upgrades.
In general, a standard system update will make all the necessary changes.
References
Remote Code Execution Hole Patched in Magento eCommerce Platform
A nasty remote code execution vulnerability was recently patched in Magento, eBay’s eCommerce platform
Why some people would rather be right than believe a malware warning

This innocent looking USB drive could lead to infection – but only if you second-guess Avast warnings!
Would you rather trust the virus experts or your instincts?
Every day 140,000 people connect their USB flash drive or mobile phone to a computer, and get a warning from Avast about an infection called LNK:Jenxcus.
Which kind of person are you?
Many of them act on that information from their trusted Avast Antivirus security software and as a result, they scan their USB device for malware and they wipe it away. Crisis over.
But there is another group of people who keep this infection alive and active, because they refuse to believe it is a real or dangerous threat. In other words, because something has always been one way, they assume it can’t change, therefore Avast must be wrong.
As a result, they decide to turn off their antivirus shield and by doing so, they create an obstacle-free way for malware to enslave their computer and steal data or valuable computing time.
A perfectly good reason. Or is it?
One of the most frequent reasons people use for disabling shields and allowing malware to spread in their computer is
“I use this file all the time and it is safe.”
Another variation is,
“I created this file, it’s only a picture.”
Do you find this situation familiar? Are you guilty of over-riding the security software you installed to protect yourself?
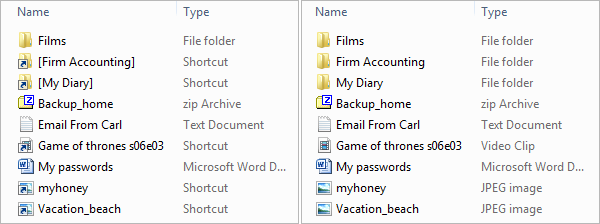
If your answer is yes, then test your virus detection knowledge with the image below. There are two screenshots of a directory from a USB stick; one is infected and the other is clean. Can you tell the difference?
It’s difficult to tell, isn’t it?
The one on the left is infected. The most visible differences are on the icons, but there is another clue in the file types. Some files and directories on the left side changed their type into a shortcut. This happened because a malicious script installed itself onto a USB drive and replaced legitimate files with links. If the owner of the USB opens the directory Firm Accounting, for example, he executes malware that in the end opens the real Firm Accounting directory, so it looks like everything is normal. But it is not, because in the background all the computer’s drives are getting infected over and over again.
Avast detects LNK:Jenxcus and warns you.
The trick is; you have to heed the warning.
Source of infection
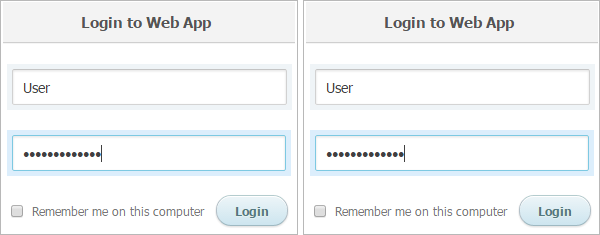
Except from other infected drives, this malware is downloaded onto your computer from hacked websites. The screenshot below shows an example of a hacked website waiting for random users with a vulnerable internet browser. Can you tell the difference this time?
If you answered no, you are absolutely right, because for the normal user there is no visible change. That is probably the reason for another frequent excuse before disabling the shields,
“I visit this page every day. It doesn’t have malware.”
That’s just not good enough, because the fact that the page is clean most of the time, does not mean it is not vulnerable to attacks. In fact most small and medium-sized business (SMB) pages have some exploitable vulnerability and when they get targeted by exploit kit authors, your best chance to stay safe are updated applications and active antivirus. With the shields ON!
Extermination
If you are comfortable with computers, then you may want to clean this infection manually. Start with your computer and look for links (.lnk) and visual basic script (.vbs .vba .vbe) or batch files (.bat). Links usually point to this hidden script files so it is not hard to find them. If you wonder where the original files are, you can find this information in links too. They were not moved in most cases, just marked as hidden so they are not visible on computers with standard configuration. When you are sure all hard drives are clean, it is time to go through all your removable ones and go through the same procedure.
An easier way to clean an infection is by using a good cleaning tool. If you need help searching for such tool, visit our Avast forum and read what others do in your situation, or ask nicely for help from Evangelists, who dedicate their free time to helping users and researching security problems.
Suspect a false positive?
If you think it’s a false positive, do a little checking first. The Avast forum is a good place to start. You can read about LNK:Jenxcus, or you can start a new thread with your own question. If you are still convinced that you have a false positive, then please report it so the Avast Virus Lab can determine how/why it’s detected,. This video tells you how,
Fedora EPEL 5 Security Update: mksh-50f-1.el5
R50f is a required security and bugfix release:
* Add a patch marker for vendor patch versioning to mksh.1
* SECURITY: make unset HISTFILE actually work
* Document some more issues with the current history code
* Remove some unused code
* RCSID-only sync with OpenBSD, for bogus and irrelevant changes
* Also disable field splitting for alias ‘local= ypeset’
* Fix read -n-1 to not be identical to read -N-1
* Several fixes and improvements to lksh(1) and mksh(1) manpages
* More code (int → size_t), comment and testsuite fixes
* Make dot.mkshrc more robust (LP#1441853)
* Fix issues with IFS=” read, found by edualbus
* Fix integer overflows related to file descriptor parsing, found by Pawel Wylecial (LP#1440685); reduce memory usage for I/O redirs
* Document in the manpage how to set ±U according to the current locale settings via LANG/LC_* parameters (cf. Debian #782225)
* Some code cleanup and restructuring
* Handle number parsing and storing more carefully
Australian infosec body lobbies for mandatory security baseline
Australia’s infosec industry is lobbying for a mandatory security baseline to ensure basic IT standards are met across the country, with penalties issued to those that don’t comply.
The post Australian infosec body lobbies for mandatory security baseline appeared first on We Live Security.
![]()