Monthly Archives: May 2015
US Navy Sets Out Five-Year Cyber Security Plan
A JPEG may jeopardize your company’s network

We daily capture them on our phones. We have dozens of them stored on our computers. We share them on social networks and we love to see those of others. We are talking about the images in JPEG format, the most used one because when compressed the pictures don’t lose much quality. Indispensables, and yet, could be the tool used by a cybercriminal to access any corporate or institution network.
This was proven by security expert Marcus Murray, who researched a new way a cyber-attacker could exploit a malicious JPEG to compromise Windows servers and access any company’s sensitive information.
The researcher demonstrated how someone could performed this attack during the RSA Conference in San Francisco, an event that gathers dozens of experts in computer security every year. Murray implemented a ‘demo’ to compromise a similar security network to any US government agency network.
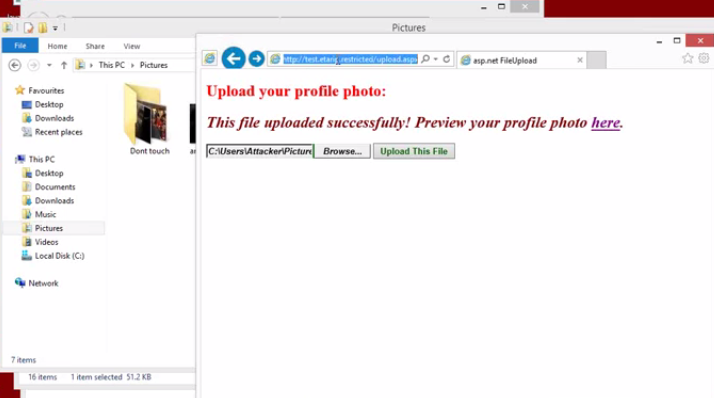
Murray changed the attributes or metadata that any JPEG file stores including in it a malicious code. Then he got this image to infect the corporate network. How did he do it? By a form that allowed users to upload a profile picture to the alleged government agency web page. Once inside, the file became a gateway for the attacker.
Thanks to the malicious JPEG, the cyber-criminal’s administration permissions over the network grew more and more, reaching a point at which he could steal sensitive information or even take control over the network.
The rest of the process is simpler: the criminal only has to exploit his advantage to install malicious software that infects the computers to spy the corporation or steal confidential information. According to Murray, this attack can be performed in “even mixed environments” with Windows and Linux.

On the conference in San Francisco, he showed how to introduce a remotely accessed Trojan he created using Metasploit, the popular open source project that allows trying different kinds of attacks as part of a ‘pentest’ (penetration test).
That’s how he prove that only with a picture you can access any company’s network and steal their confidential information, without the employees realizing the damage a file so seemingly harmless could make.
The post A JPEG may jeopardize your company’s network appeared first on MediaCenter Panda Security.
Artnana Webboard 1.4 Cross Site Scripting
Artnana Webboard version 1.4 suffers from multiple cross site scripting vulnerabilities.
Mt. Vernon Media 1.12 SQL Injection
Mt. Vernon Media web design products version 1.12 suffer from multiple remote SQL injection vulnerabilities.
Mt. Vernon Media 1.12 Cross Site Scripting
Mt. Vernon Media web design products version 1.12 suffer from multiple cross site scripting vulnerabilities.
Mt. Vernon Media 1.12 HTML Injection
Mt. Vernon Media web design products version 1.12 suffer from a html injection vulnerability.
Highlights from CeBIT Australia 2015
This week Sydney put on its finest weather for the CeBIT Australia 2015 trade show held at the famous city’s Olympic Park. Featuring a diverse mix of technologies and innovation from the APAC region there was something for everyone, from 3D printing, robotics, low-power LED lighting, to enterprise and business computing.
The Australian-based AVG Business team was also there for the 8th consecutive year to capture the action and showcase AVG’s Secure-Sign-On, identity as a service, cloud, backup and IT management platforms.
On the security side, a particular highlight was the keynote talk from infamous black-hat turned white-hat hacker, Kevin Mitnick. Mitnick captivated the audience with shocking revelations of devastatingly simple social engineering antics.

As is common-place at technology conventions these days, there were plenty of drones, and they’re getting smarter too. One demonstrator walked in a circle around his drone while it faithfully hovered mid-air – and as he circled it, the drone rotated itself automatically, sensing where he was.

And while we’re talking about smart gadgets, a return visitor to CeBIT was the kid-size humanoid robot soccer league – or more specifically the NUbot team from Newcastle University who are previous RoboCup world champions.

What is RoboCup I hear you ask? Well, imagine foot-high robots running (okay, shuffling) around a ridiculously undersized soccer pitch kicking a ball trying to score goals. Hilariously, some of them kept falling over, as if to feign an injury (or so I imagined), and I found myself wondering if there had been any Italian inspired coding involved.
Green tech was once again a major feature at CeBIT with San Francisco based electric car manufacturer Tesla displaying one of their cars, a Model 85 – accompanied by a constant queue of people wanting to sit in the driver’s seat for a selfie!

Traditional and Tech Gifts for Mother’s Day 2015
My personal favorites –and the gifts that many busy moms I know say they value most— have more to do with personal/family time, family memories, and personalized reminders of how much our moms means to us.
Here are some of my picks of intriguing tech and non-tech products, apps and services for this Mother’s Day.
Traditional gifts:
If you want to do flowers for Mom, by all means go ahead! But how about adding a twist this year? You can order an eco-friendly bouquet from The Bouqs Flowers, which ships directly from eco-friendly farms (certified by third-party agencies such as The Rainforest Alliance) to anywhere in the U.S.
Make a spa day experience for Mom everyday. What to give the busy Moms – those who are working, managing families, networking, volunteering, doing it all? Ease the stress on her back with a massage seat cushion from HoMedics. This is a great idea for moms who must be at their desk all day, either at the office or while working from home. Products range from $99 to $199.
Gifts of Time:
For new moms – even Catherine, the Duchess of Cambridge welcoming Charlotte Elizabeth Diana–Baby Tracker journals make a perfect gift to reduce stress, and help parents and child care providers stay on top of baby’s ever-changing world. Baby Tracker is available online at timetoo.com and through Amazon. The TimeToo website also offers parents additional resources, free checklists and printable templates to help organize family travel, school communication and baby records and a parenting blog.

A robot vacuum is one of my favorite ideas to give busy moms more family time and “me” time. This one is especially good for moms of/with pets! Neato Robotics, the maker of the popular Neato robot vacuums, recently surveyed American mothers to find out first hand whether any vacuum, specifically a robot vacuum, is ever a thoughtful Mother’s Day gift. Prices vary, from approximately $200 to $500.
Keeping Memories
Memory books have long been a popular gift for Mother’s Day. They have also been a labor of love to collect and assemble. Now the digital equivalents such as the ScrapPad app for iPad makes organizing these a breeze. ScrapPad is an easy photo journal creator that offers pre-set designs and customized options. And of course, you can print hard copies of the scrapbooks. (Available on the iOS platform only. $4.99)
Give-Back Gift Ideas
Mother’s Day can also be a great day to give back to moms who are struggling. Here are a few ideas:
Moms Helping Moms Foundation offers a network of partnerships with local service organizations that distribute donated baby supplies and essentials to local families in need of assistance. You can donate money, items, or, find out how you can volunteer in your local area.
Another organization, Helping Hands for Single Moms, is a community-based nonprofit assists impoverished single mom families while the moms are pursuing a college education and financial independence. This year, they’ve come up with a unique way to celebrate your mom and donate to their program, called MomApplause. Create a 30 – 60 second video of your Mother’s Day tribute, post it on social media using #MOMMApplause, and ask your friends to like and share your tribute. In the video, announce that you are donating $5 at MOMMApplause.com (about the price of buying a card and mailing it). And if you have a business, Helping Hands says you are free to add your company name to the end of the #. You can find our more here.
Bonus idea:
Finally, moms obviously care about the security of their family. Increasingly, this extends to the digital world.
Give your mom the gift of AVG’s Zen on her devices. It can help mom keep her laptop running virus-free, and protect the whole family from viruses and malware…and this includes mobile devices. With AVG Zen, you can add unlimited PC, Mac and Android devices—in any combination—and easily keep tabs on them all from a single screen. Learn more about AVG Zen here.
I hope these provide some original, fun and inspiring ideas to help you celebrate the special mom in your life.
![]()
![]()
[ MDVSA-2015:232 ] libtasn1
-----BEGIN PGP SIGNED MESSAGE----- Hash: SHA1 _______________________________________________________________________ Mandriva Linux Security Advisory MDVSA-2015:232 http://www.mandriva.com/en/support/security/ _______________________________________________________________________ Package : libtasn1 Date : May 8, 2015 Affected: Business Server 1.0, Business Server 2.0 _______________________________________________________________________ Problem Description: Updated libtasn1 packages fix security vulnerability: A malformed certificate input could cause a heap overflow read in the DER decoding functions of Libtasn1. The heap overflow happens in the function _asn1_extract_der_octet() (CVE-2015-3622). _______________________________________________________________________ References: http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-3622 http://advisories.mageia.org/MGASA-2015-0200.html _________________________________________________________________
