The Siemens HomeControl for Room Automation application before 2.0.1 for Android does not verify X.509 certificates from SSL servers, which allows man-in-the-middle attackers to spoof servers and obtain sensitive information or modify data via a crafted certificate.
Monthly Archives: May 2015
Millions of WordPress sites left vulnerable by plugin flaw
Millions of WordPress sites are vulnerable to a scripting flaw found in two popular plugins, one of which can be found in the default installation of the blogging platform.
The post Millions of WordPress sites left vulnerable by plugin flaw appeared first on We Live Security.
![]()
Russian models that fall in love with you… it’s a scam!
“I want to chat with you” if you have received an email with this subject, or something similar, with the picture of a beautiful Miss Russia, just ignore it! She is not contacting you because she has fallen deeply in love with you.
The Spanish Internet User Security Office and the Spanish Civil Guard have warned about these scams, because as you might think their only purpose is to take all your money.
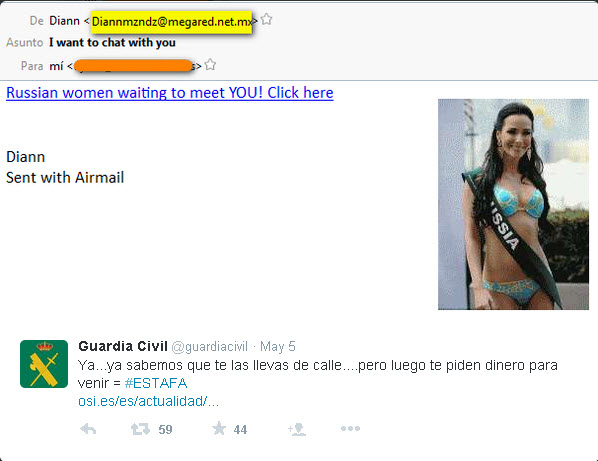
The Spanish Civil Guard warns via their Twitter account: Yes, we know that they are all crazy about you… but then they will ask you for money to come #SCAM
If you have already made some sort of contact, it is possible that they have already asked you for money so they can come to visit you, so you can finally meet in person,
In this case we recommend:
- Don’t send money to anyone.
- Stop all communications.
Spanish National Police warns us through their Twitter account about other kinds of scams similar to this one.
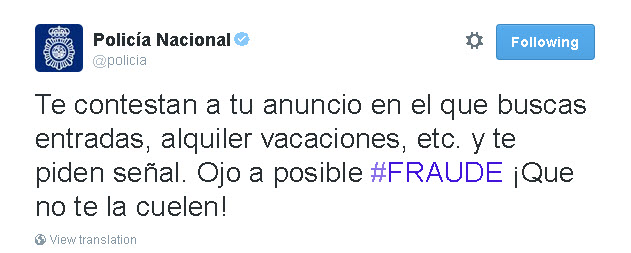
As the tweet above says: someone answers to your add in which you are looking for concert tickets, a home for renting, etc. and they ask you for a deposit. Watch out, possible scam! Don’t take the bait!
Don’t fall for it!
The post Russian models that fall in love with you… it’s a scam! appeared first on MediaCenter Panda Security.
[ MDVSA-2015:231 ] perl-XML-LibXML
-----BEGIN PGP SIGNED MESSAGE----- Hash: SHA1 _______________________________________________________________________ Mandriva Linux Security Advisory MDVSA-2015:231 http://www.mandriva.com/en/support/security/ _______________________________________________________________________ Package : perl-XML-LibXML Date : May 7, 2015 Affected: Business Server 1.0, Business Server 2.0 _______________________________________________________________________ Problem Description: Updated perl-XML-LibXML package fixes security vulnerability: Tilmann Haak from xing.com discovered that XML::LibXML did not respect the expand_entities parameter to disable processing of external entities in some circumstances. This may allow attackers to gain read access to otherwise protected ressources, depending on how the library is used (CVE-2015-3451). _______________________________________________________________________ References: http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-
WordPress Security and Maintenance Release
Original release date: May 07, 2015
WordPress 4.2 and prior versions contain critical cross-site scripting vulnerabilities. Exploitation of these vulnerabilities could allow a remote attacker to take control of an affected website.
Users and administrators are encouraged to review the WordPress Security and Maintenance Release and upgrade to WordPress 4.2.2.
This product is provided subject to this Notification and this Privacy & Use policy.
Apple Releases Security Updates for Safari
Original release date: May 07, 2015
Apple has released security updates for Safari to address multiple vulnerabilities. Exploitation of some of these vulnerabilities may allow a remote attacker to take control of the affected system.
Available updates include:
- Safari 8.0.6 for OS X Yosemite v10.10.3
- Safari 7.1.6 for OS X Mavericks v10.9.5
- Safari 6.2.6 for OS X Mountain Lion v10.8.5
US-CERT encourages users and administrators to review Apple security update HT204826 and apply the necessary updates.
This product is provided subject to this Notification and this Privacy & Use policy.
pydio vulnerabilities
Posted by Just A Fake on May 07
Does anyone have any info on the two pydio vulnerabilities announced today?
They have been given CVE-2015-3431 and CVE-2015-3432 but a search on mitre
just says those are reserved.
There is no information or explanation about what the issues are.
Thanks for any info anyone has.
Robot
WordPress 4.2.2 Security and Maintenance Release
WordPress 4.2.2 is now available. This is a critical security release for all previous versions and we strongly encourage you to update your sites immediately.
Version 4.2.2 addresses two security issues:
- The Genericons icon font package, which is used in a number of popular themes and plugins, contained an HTML file vulnerable to a cross-site scripting attack. All affected themes and plugins hosted on WordPress.org (including the Twenty Fifteen default theme) have been updated today by the WordPress security team to address this issue by removing this nonessential file. To help protect other Genericons usage, WordPress 4.2.2 proactively scans the wp-content directory for this HTML file and removes it. Reported by Robert Abela of Netsparker.
- WordPress versions 4.2 and earlier are affected by a critical cross-site scripting vulnerability, which could enable anonymous users to compromise a site. WordPress 4.2.2 includes a comprehensive fix for this issue. Reported separately by Rice Adu and Tong Shi.
The release also includes hardening for a potential cross-site scripting vulnerability when using the visual editor. This issue was reported by Mahadev Subedi.
Our thanks to those who have practiced responsible disclosure of security issues.
WordPress 4.2.2 also contains fixes for 13 bugs from 4.2. For more information, see the release notes or consult the list of changes.
Download WordPress 4.2.2 or venture over to Dashboard → Updates and simply click “Update Now.” Sites that support automatic background updates are already beginning to update to WordPress 4.2.2.
Thanks to everyone who contributed to 4.2.2:
Aaron Jorbin, Andrew Ozz, Andrew Nacin, Boone Gorges, Dion Hulse, Ella Iseulde Van Dorpe, Gary Pendergast, Hinaloe, Jeremy Felt, John James Jacoby, Konstantin Kovshenin, Mike Adams, Nikolay Bachiyski, taka2, and willstedt.
CVE-2015-0531
EMC SourceOne Email Management before 7.2 does not have a lockout mechanism for invalid login attempts, which makes it easier for remote attackers to obtain access via a brute-force attack.
CVE-2015-0538
ftagent.exe in EMC AutoStart 5.4.x and 5.5.x before 5.5.0.508 HF4 allows remote attackers to execute arbitrary commands via crafted packets.