When a response for a request with a request body is returned to the user agent before the request body is fully read, by default Tomcat swallows the remaining request body so that the next request on the connection may be processed. There was no limit to the size of request body that Tomcat would swallow. This permitted a limited denial of service as Tomcat would never close the connection and a processing thread would remain allocated to the connection. Versions affected include Apache Tomcat 8.0.0-RC1 to 8.0.8, 7.0.0 to 7.0.54, and 6.0.0 to 6.0.43.
Monthly Archives: May 2015
[ MDVSA-2015:230 ] squid
-----BEGIN PGP SIGNED MESSAGE----- Hash: SHA1 _______________________________________________________________________ Mandriva Linux Security Advisory MDVSA-2015:230 http://www.mandriva.com/en/support/security/ _______________________________________________________________________ Package : squid Date : May 6, 2015 Affected: Business Server 2.0 _______________________________________________________________________ Problem Description: Updated squid packages fix security vulnerability: Squid configured with client-first SSL-bump does not correctly validate X509 server certificate domain / hostname fields (CVE-2015-3455). _______________________________________________________________________ References: http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-3455 http://advisories.mageia.org/MGASA-2015-0191.html _______________________________________________________________________ Updated Packages: Mandriva Business Server 2/X86_64: 1b42519307a1a965
[ MDVSA-2015:229 ] net-snmp
-----BEGIN PGP SIGNED MESSAGE----- Hash: SHA1 _______________________________________________________________________ Mandriva Linux Security Advisory MDVSA-2015:229 http://www.mandriva.com/en/support/security/ _______________________________________________________________________ Package : net-snmp Date : May 6, 2015 Affected: Business Server 1.0, Business Server 2.0 _______________________________________________________________________ Problem Description: Updated net-snmp packages fix security vulnerability: It was discovered that the snmp_pdu_parse() function could leave incompletely parsed varBind variables in the list of variables. A remote, unauthenticated attacker could exploit this flaw to cause a crash or, potentially, execute arbitrary code. _______________________________________________________________________ References: http://advisories.mageia.org/MGASA-2015-0187.html ______________________________________________________________________
[ MDVSA-2015:228 ] nodejs
-----BEGIN PGP SIGNED MESSAGE----- Hash: SHA1 _______________________________________________________________________ Mandriva Linux Security Advisory MDVSA-2015:228 http://www.mandriva.com/en/support/security/ _______________________________________________________________________ Package : nodejs Date : May 6, 2015 Affected: Business Server 2.0 _______________________________________________________________________ Problem Description: Updated nodejs package fixes security vulnerability: It was found that libuv does not call setgoups before calling setuid/setgid. This may potentially allow an attacker to gain elevated privileges (CVE-2015-0278). The libuv library is bundled with nodejs, and a fixed version of libuv is included with nodejs as of version 0.10.37. The nodejs package has been updated to version 0.10.38 to fix this issue, as well as several other bugs. _______________________________________________________________________ References: h
Smartphone Authentication: the Passing of the Passcode?
Smartphone authentication: is biometric technology ready to replace PINs and passwords?
The post Smartphone Authentication: the Passing of the Passcode? appeared first on We Live Security.
![]()
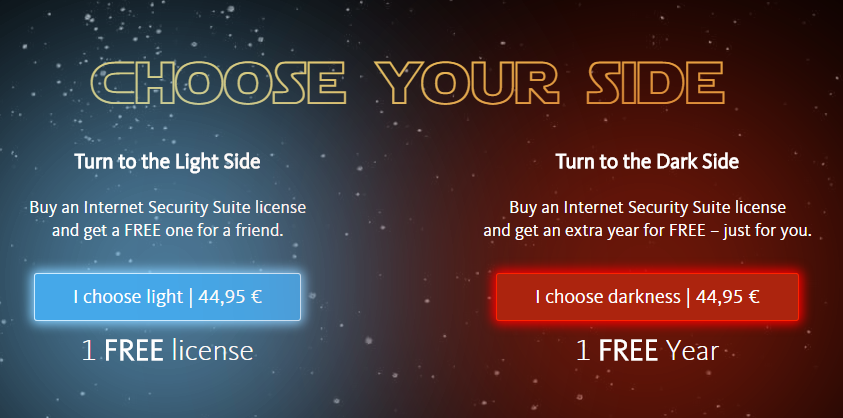
How we celebrated Star Wars Day
May the 4th be with you!
It might come as no surprise that some of the Avira team members are proud to be part of the beautiful community of Star Wars fans. It thus proved to be an absolute pleasure putting together a plan on how we can celebrate Star Wars Day with our users. Since fighting the bad side of the Internet is kind of what we’re really great at, we wanted to see how many of our users would choose light over darkness in a really fun campaign.
It all started last week with a teaser page that allowed people to do the countdown with us before releasing the official campaign page.
Light vs. Darkness: who won?
We offered users the possibility to choose a side: buy an Avira Internet Security Suite license and get a FREE one for a friend (the light side) or buy the same product and benefit from an extra year of protection for FREE, just for them (the dark side).
75% of the Avira users chose the dark side in the Star Wars Day Campaign while only 25% turned to the light side.
What we won? Lovely hours spent in cool brainstorming sessions, some one on one training for our colleagues who couldn’t tell the difference between Star Wars and Star Trek and a bunch of new users who will be protected against all the dark forces of the Internet thanks to the Avira Internet Security Suite.
Over 20.000 people visited our Campaign page and we would also like to thank them for the support shown on social media. We were excited to discover the amazing feedback coming from our friends and followers on all social media networks.
Passez voir le site d’@Avira ! Ils ont fait un super boulot pour le 4 mai
— Martin ~ Gogo (@GogocraftFR) May 4, 2015
My avira anti-virus is awesome!They even celebrate May The 4th Be With You!The blue square offers “upgrade ur powers” pic.twitter.com/RI1HcIMsyP
— Addina Naufalia H. (@AddinaNaufa) May 4, 2015
Mine antivirus use the force too!!! XD
@Avira and you too!!#MayThe4thBeWithYou #StarWarsDay pic.twitter.com/ML9YYW6pXx
— Giorgio Leonarduzzi (@ghorgho) May 4, 2015
Os recomiendo @Avira, un antivirus con un analizador llamado “Luke Filewalker” y te recuerda el #MayThe4thBeWithYou pic.twitter.com/yimFTMdy9K
— FBLupi (@fboli94) May 4, 2015
The post How we celebrated Star Wars Day appeared first on Avira Blog.
Your likes in Facebook can be the passwords of the future

Do you remember, who was the last person you spoke on the phone with? And the first one you sent a WhatsApp message this morning? If the answer is yes, you might want to change your usual passwords for the answers to this questions.
Do you imagine your passwords changing depending on your last ‘Like’ in Facebook? Anything you have done with your smartphone or your computer during the last few hours can be used as a password by ActivPass. A system developed by researchers of the universities of Illinois and Texas and the Indian Institute of Technology Kharagpur, in India.
These researchers have developed a new method of authentication to unlock applications for which users had to answer correctly questions about recently completed actions. Something that it has proven to be possible, despite of what our absent minds might think. In fact, those who took part in this study answer correctly 95 percent of the questions.
ActivPass could be a possible solution to the many times a user forgets his password and clicks on “forgot your password”. In fact, they hope to reduce the amount of passwords we have to remember thanks to their tool, as the questions will be about recent topics and will change overnight.
They first thought of it as an evolution to the questions about our past which are already used as security measures in many platforms. Questions like: “What was your first pet’s name?” or “What was the first name of your favorite teacher?”
“Whenever there’s something you and your phone share and no one else knows, that’s a secret, and that can be used as a key” says professor Choudhury, University of Illinois. However, this new security method is not foolproof yet. Still raises some unknowns, like what would happen if a long period of time passes and the user can’t remember what he did last time.
Researchers are working to improve it, but for now they just conceive it as a part of a user’s authentication on a platform. Also, during the firsts test they found other disadvantages. Those who volunteered to take part in the tests not only had a high percentage of success in the questions about their own activities, but also were able to answer question about other people less than 6 percent of the time, which is quite disturbing.
As the research conducted by Jason Hong, a professor at Carnegie Mellon University, demonstrated the percentage of users correctly answering questions about other people is low.
So, despite of having to fix some details, it doesn’t seem far away when we will use a system like ActivPass instead of standard passwords. An option that is gaining popularity among platforms where you can share content with our friends and family. If, for example, you were to be subscribed to Wuaki.tv, you can give access to your cousin one night without having to worry about changing the password the next day. The password will change depending on what we have done that day, something our cousin would not know, unless you told him.
Passwords that change every day. A method of discouraging those who want to access others accounts, but also a challenge to the absentminded. Would we be able to remember the first thing we did with our phone?
The post Your likes in Facebook can be the passwords of the future appeared first on MediaCenter Panda Security.
CEEA-2015:0951 CentOS 6 resource-agentsEnhancement Update
CentOS Errata and Enhancement Advisory 2015:0951 Upstream details at : https://rhn.redhat.com/errata/RHEA-2015-0951.html The following updated files have been uploaded and are currently syncing to the mirrors: ( sha256sum Filename ) i386: 73d3f2924f5fada52153c6410c26b05304ed345be0ce15068a7623b26990bf28 resource-agents-3.9.5-12.el6_6.5.i686.rpm x86_64: 275d33edcefb85769b8aaea5f1214f3522444ff49ad88a24725f8a1708b105d0 resource-agents-3.9.5-12.el6_6.5.x86_64.rpm 167960cfa378a8c73462a7c15a21defdb011b028b81a36e6e7381157370a8c37 resource-agents-sap-3.9.5-12.el6_6.5.x86_64.rpm 9fd5c8e7b43ec4a2fd549812578ed4756c402b7c20084f11510b8bb93541ad9a resource-agents-sap-hana-3.9.5-12.el6_6.5.x86_64.rpm Source: af9977933892b02d4b55b29ac28a97f16f6cd8f8d8be3594e960808208534207 resource-agents-3.9.5-12.el6_6.5.src.rpm
CEBA-2015:0950 CentOS 6 lvm2 BugFix Update
CentOS Errata and Bugfix Advisory 2015:0950 Upstream details at : https://rhn.redhat.com/errata/RHBA-2015-0950.html The following updated files have been uploaded and are currently syncing to the mirrors: ( sha256sum Filename ) i386: eca144b3a845aa3a67d8615812619c5e3869f4d4a6ff26c2e82a53d30e1abe5c cmirror-2.02.111-2.el6_6.2.i686.rpm 149541e31e0d09152e70f05a2e4158c179198f20707c8c24ba5fe89098cc93bf device-mapper-1.02.90-2.el6_6.2.i686.rpm 85f1e0b313642b727796638b5a8841517e6d9dc58a1683e34b8ec53f1214b223 device-mapper-devel-1.02.90-2.el6_6.2.i686.rpm c16a6150c407a941dd1183208a3c67110c3424a8dae0388a4ab1ef78747f5e5b device-mapper-event-1.02.90-2.el6_6.2.i686.rpm 935bea5ca4ddc1b2f97f8fe76bc97f11c11a493c62b738ad9a6251d56cd6ecd2 device-mapper-event-devel-1.02.90-2.el6_6.2.i686.rpm c78bbdac5d3e6f6ea7bb2be2ab9512658e5342687eb339a8b4691f45eb4a1fc3 device-mapper-event-libs-1.02.90-2.el6_6.2.i686.rpm a091debdfbd571b555dbb8eabfe181ff973f0c68b95c27a75b54c9dd58675b5f device-mapper-libs-1.02.90-2.el6_6.2.i686.rpm 009241526c636cbbc48699b6322e31cc0f0cb1c2ef5972d328a6fb8b97e9d4e9 lvm2-2.02.111-2.el6_6.2.i686.rpm d9efc5fbc8f62bd5c81493be6a91aa79d6626f3e51ba50b89c9400e8c171d34b lvm2-cluster-2.02.111-2.el6_6.2.i686.rpm 94f43806750a541c03403c89b36f89247c8287057767f08013974fa0688d6307 lvm2-devel-2.02.111-2.el6_6.2.i686.rpm e199bb4535dd856f4fc0f7ea9eb5250c64bd95032264119d3e5f2869011c6013 lvm2-libs-2.02.111-2.el6_6.2.i686.rpm x86_64: 6b7c73ee4965b1bb88b52652312fb80deea63f44062ece5216e5d9f252d6e452 cmirror-2.02.111-2.el6_6.2.x86_64.rpm 3c0a05a5356ed490d3763bb7f177ed223f62f46a410d185426a7c2fa29a32fc1 device-mapper-1.02.90-2.el6_6.2.x86_64.rpm 85f1e0b313642b727796638b5a8841517e6d9dc58a1683e34b8ec53f1214b223 device-mapper-devel-1.02.90-2.el6_6.2.i686.rpm 9bbfbdfe7088640820586bfbc3fd36003010e8c2040f6b64324d05b76ba6e06c device-mapper-devel-1.02.90-2.el6_6.2.x86_64.rpm 40b406ed791e41628d2137e48fe7f2c6fc9769bdfdbacbfaea3acb7c4acb98d9 device-mapper-event-1.02.90-2.el6_6.2.x86_64.rpm 935bea5ca4ddc1b2f97f8fe76bc97f11c11a493c62b738ad9a6251d56cd6ecd2 device-mapper-event-devel-1.02.90-2.el6_6.2.i686.rpm d3caae838b51755dcbe0ca9260a6d9e6b9cceb6e81afd80a7b4c5a84f584e8c8 device-mapper-event-devel-1.02.90-2.el6_6.2.x86_64.rpm c78bbdac5d3e6f6ea7bb2be2ab9512658e5342687eb339a8b4691f45eb4a1fc3 device-mapper-event-libs-1.02.90-2.el6_6.2.i686.rpm 4ee3206f9a2281cadfa5d59fa27a39cc2f9e170a1637bc70fce39c2c45422041 device-mapper-event-libs-1.02.90-2.el6_6.2.x86_64.rpm a091debdfbd571b555dbb8eabfe181ff973f0c68b95c27a75b54c9dd58675b5f device-mapper-libs-1.02.90-2.el6_6.2.i686.rpm b84760afc5c3d12bfb872bd177c88f38b946492e4a78be3389f9a8458fbb0881 device-mapper-libs-1.02.90-2.el6_6.2.x86_64.rpm d1feca5e2b3f00f1b3e3a2662df601d20fa187f6c43c46c6971f943e82411e8f lvm2-2.02.111-2.el6_6.2.x86_64.rpm bcf2153ec01262a0cf4f46d1f20a5d3d63fe4d62e4689d05f37ba90a08ac3de6 lvm2-cluster-2.02.111-2.el6_6.2.x86_64.rpm 94f43806750a541c03403c89b36f89247c8287057767f08013974fa0688d6307 lvm2-devel-2.02.111-2.el6_6.2.i686.rpm 9c380193c330b99756724a2fcef7b3afb82208dfcfdbdd76c46b73a67cc23531 lvm2-devel-2.02.111-2.el6_6.2.x86_64.rpm e199bb4535dd856f4fc0f7ea9eb5250c64bd95032264119d3e5f2869011c6013 lvm2-libs-2.02.111-2.el6_6.2.i686.rpm e8c9913b8a2aac2cae63f784492c2ac39ecb035d2eff9cc91140561c2e1aaecc lvm2-libs-2.02.111-2.el6_6.2.x86_64.rpm Source: ddea0f18353585b4eb18ca6670c88375f20b191b26327bc16f682002b22d99aa lvm2-2.02.111-2.el6_6.2.src.rpm
CEBA-2015:0949 CentOS 5 nfs-utils BugFix Update
CentOS Errata and Bugfix Advisory 2015:0949 Upstream details at : https://rhn.redhat.com/errata/RHBA-2015-0949.html The following updated files have been uploaded and are currently syncing to the mirrors: ( sha256sum Filename ) i386: 37fa09be533c338fb4ba49e1712e3ba2b3bdb057ff2fa78e63e8628f7e2928cf nfs-utils-1.0.9-71.el5_11.i386.rpm x86_64: 700f52a428a75d033f7727e8da84ef0afb435999d097a51d2aed166ffbc78d7d nfs-utils-1.0.9-71.el5_11.x86_64.rpm Source: 237ca358a513db496c4a99010b0d1fcb1ef6830957028f13a2ca7e7d74c716e6 nfs-utils-1.0.9-71.el5_11.src.rpm