Ansgar Burchardt discovered that the Git plugin for FusionForge, a
web-based project-management and collaboration software, does not
sufficiently validate user provided input as parameter to the method to
create secondary Git repositories. A remote attacker can use this flaw
to execute arbitrary code as root via a specially crafted URL.
Monthly Archives: May 2015
HP Security Bulletin HPSBMU03267 2
HP Security Bulletin HPSBMU03267 2 – Potential security vulnerabilities have been identified with the HP Matrix Operating Environment and HP CloudSystem Matrix running OpenSSL. These vulnerabilities comprise the SSLv3 vulnerability known as “Padding Oracle on Downgraded Legacy Encryption” or “POODLE”, which could be exploited remotely to allow disclosure of information. Revision 2 of this advisory.
HP Security Bulletin HPSBMU03261 2
HP Security Bulletin HPSBMU03261 2 – Potential security vulnerabilities have been identified with HP Systems Insight Manager running OpenSSL on Linux and Windows. These vulnerabilities are related to the SSLv3 vulnerability known as “Padding Oracle on Downgraded Legacy Encryption” or “POODLE”, which could be exploited remotely to allow disclosure of information. Revision 2 of this advisory.
HP Security Bulletin HPSBMU03223 1
HP Security Bulletin HPSBMU03223 1 – Several potential security vulnerabilities have been identified with HP Insight Control server provisioning running SSLv3. These are the SSLv3 vulnerabilities known as “Padding Oracle on Downgraded Legacy Encryption” also known as “Poodle”, which could be exploited remotely resulting in Denial of Service (DoS) or disclosure of information. Revision 1 of this advisory.
Debian Security Advisory 3274-1
Debian Linux Security Advisory 3274-1 – Jason Geffner discovered a buffer overflow in the emulated floppy disk drive, resulting in the potential privilege escalation.
HP Security Bulletin HPSBGN03332 1
HP Security Bulletin HPSBGN03332 1 – A potential security vulnerability has been identified in HP Operations Analytics running SSLv3. This is the SSLv3 vulnerability known as “Padding Oracle on Downgraded Legacy Encryption” or “Poodle”, which could be exploited remotely resulting in Denial of Service (DoS) or disclosure of information. Revision 1 of this advisory.
HP Security Bulletin HPSBMU03263 3
HP Security Bulletin HPSBMU03263 3 – Potential security vulnerabilities have been identified with HP Insight Control running OpenSSL. These vulnerabilities include the SSLv3 vulnerability known as “Padding Oracle on Downgraded Legacy Encryption” or “POODLE”, which could be exploited remotely to allow disclosure of information. Revision 3 of this advisory.
Avast Data Drives New Analytics Engine
Did you know that Californians are obsessed with Selfie Sticks from Amazon.com? Or that people in Maine buy lots of coconut oil?
Thanks to Jumpshot, a marketing analytics company, you can find this information – as well as more useful information – by using the tools available at Jumpshot.com.
What may be most interesting to you is that Jumpshot is using Avast data to drive these unique insights. We provide Jumpshot with anonymized and aggregated data that we collect from scanning the 150 billion URLs our users visit each month. Using Jumpshot’s patent-pending algorithm, all of the personally identifiable information is removed from the data before it leaves Avast servers. Nothing can be used to identify or target individuals. Avast COO Ondřej Vlček explains the data stripping algorithm in an Avast forum topic.
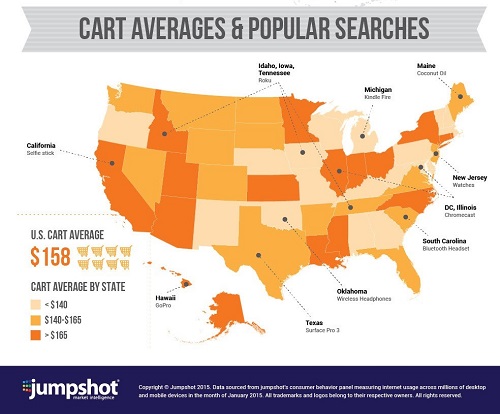
Jumpshot infographic showing Amazon.com shopping cart values by state. Anonymized and aggregated Avast browser data was used to create this information. Click here to see the full infographic.
Data security, of course, is very important to us. We go to great lengths to keep our users safe, and have never shared any data that can be used to identify them. We never have and never will.
We are aware that some users don’t want any data – no matter how generic and depersonalized it is – to be used in market analysis. This is why we clearly state during the installation of our products what information we collect and what we do with it, and offer our users the ability to opt out from having that data collected. We believe we are unique in our industry in offering an opt-out, but we do so because we respect that choice to be our users to make, not ours. We’re grateful that more than 100 million of our users, when given a clear choice, have chosen not to opt out, and we thank you.
The foundation of our business is trust, and trust only exists with honesty.
We have always strived to have an honest relationship with our users, and we will continue to do so. Currently we do not make any money from this relationship but it is an experiment as to whether we can fund our security products indirectly instead of nagging our users to upgrade. As most people are aware, most all products we use every day—Chrome, Facebook, Firefox, WhatsApp, Gmail, etc.—are indirectly funded by advertisements. In most cases though, the products directly examine what users are doing and provide them targeted advertisements. Although we suspect some security companies are doing this, we do not believe it is the proper approach. Instead, we think that this anonymized, aggregated approach is much better to maintain the trust relationship that we think is so important between us and you, our loyal users.
As always, thank you for your support and patronage. Together we continue to make the Internet a safer place for all of us.
Realtek SDK Miniigd UPnP SOAP Command Execution
Different devices using the Realtek SDK with the miniigd daemon are vulnerable to OS command injection in the UPnP SOAP interface. Since it is a blind OS command injection vulnerability, there is no output for the executed command. This Metasploit module has been tested successfully on a Trendnet TEW-731BR router with emulation.
Flash: Local SWF files can leak arbitrary local files to the internet
Posted by Jann Horn on May 29
Summary:
Flash by design allows local SWF files to read arbitrary local files, but
prevents communication with remote servers. By smuggling data through a timing
side-channel, this can be circumvented, allowing local SWF files to exfiltrate
the contents of arbitrary local files to the internet.
Some more details:
Flash runs normal local SWF files under local-with-file-system restrictions,
which are documented at
<…