Module::Signature before 0.74 allows remote attackers to execute arbitrary shell commands via a crafted SIGNATURE file which is not properly handled when generating checksums from a signed manifest.
Monthly Archives: May 2015
CVE-2015-3409
Untrusted search path vulnerability in Module::Signature before 0.75 allows local users to gain privileges via a Trojan horse module under the current working directory, as demonstrated by a Trojan horse Text::Diff module.
CVE-2015-3885
Integer overflow in the ljpeg_start function in dcraw 7.00 and earlier allows remote attackers to cause a denial of service (crash) via a crafted image, which triggers a buffer overflow, related to the len variable.
CVE-2015-3988
Multiple cross-site scripting (XSS) vulnerabilities in OpenStack Dashboard (Horizon) 2015.1.0 allow remote authenticated users to inject arbitrary web script or HTML via the metadata to a (1) Glance image, (2) Nova flavor or (3) Host Aggregate.
Details Surface on Unpatched KCodes NetUSB Bug
KCodes NetUSB, a Linux kernel module that provides USB services over IP, contains unpatched vulnerabilities according to an alert from CERT/CC and Sec Consult
Clickheat 1.13 Remote Command Execution
Clickheat version 1.13 suffers from a remote command execution vulnerability.
Google Fixes Sandbox Escape in Chrome
Google has patched a high-risk vulnerability in its Chrome browser that allows an attacker to escape the Chrome sandbox. That vulnerability is one of 37 bugs fixed in version 43 of Chrome. Six of those flaws are rated as high risks and Google paid out more than $38,000 in rewards to researchers who reported vulnerabilities […]
Google and Apple among tech giants urging Obama to block phone surveillance
Google and Apple have signed a letter to President Barack Obama urging him to reject any proposal that would grant police access to encrypted phone data.
The post Google and Apple among tech giants urging Obama to block phone surveillance appeared first on We Live Security.
![]()
Wise-FTP 8.0.2 DLL Hijack
Wise-FTP version 8.0.2 suffers from a dll hijacking vulnerability.
Venom: the security vulnerability in your floppy drive

A new security vulnerability is putting at risk computers all over the world.
It is called “Venom” and the most odd thing is that exploits a vulnerability in something that almost no one uses anymore: the floppy drive.
The bug itself is quite dangerous as it allows the owner of a virtual machine to execute code in the host machine and from there move on to the network.
In other words, Venom takes advantage from a vulnerability in the virtual floppy drive controller to enter the system and obtain root privileges, as high as possible, not only of that machine in particular but also for all those connected to the same network.
The chart published in the web page created to gather information about Venom explains it very well.
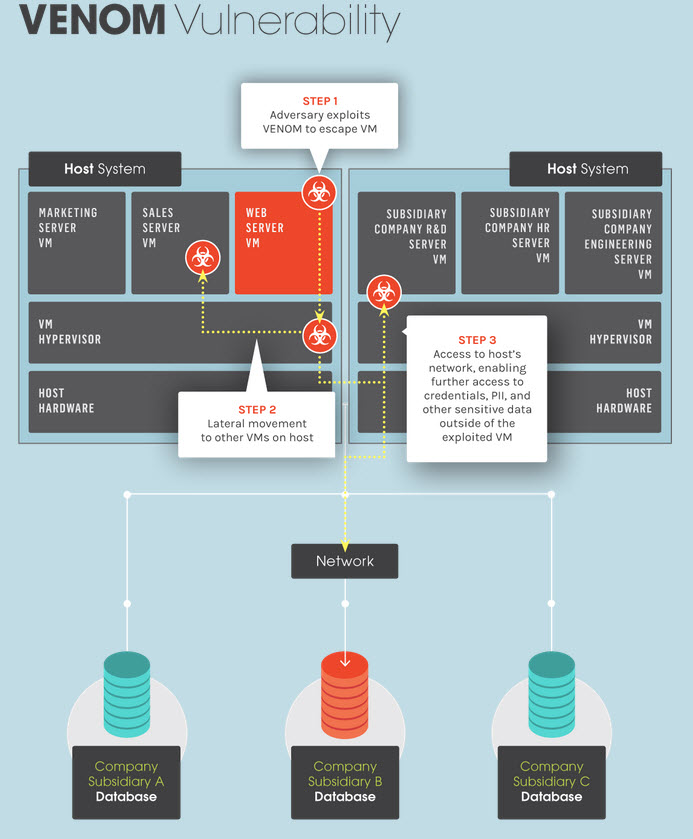
The greater risk is that this vulnerability enables the cybercriminal to access the host system through his virtual machine. Once he is inside the physical machine, he will be able to access any virtual machine running in this system.
If you want to prevent Venom, you can download the already published patches here.
We will keep you updated!
The post Venom: the security vulnerability in your floppy drive appeared first on MediaCenter Panda Security.
