Multiple cross-site scripting (XSS) vulnerabilities in the TheCartPress eCommerce Shopping Cart (aka The Professional WordPress eCommerce Plugin) plugin for WordPress before 1.3.9.3 allow remote attackers to inject arbitrary web script or HTML via the (1) billing_firstname, (2) billing_lastname, (3) billing_company, (4) billing_tax_id_number, (5) billing_city, (6) billing_street, (7) billing_street_2, (8) billing_postcode, (9) billing_telephone_1, (10) billing_telephone_2, (11) billing_fax, (12) shipping_firstname, (13) shipping_lastname, (14) shipping_company, (15) shipping_tax_id_number, (16) shipping_city, (17) shipping_street, (18) shipping_street_2, (19) shipping_postcode, (20) shipping_telephone_1, (21) shipping_telephone_2, (22) shipping_fax to shopping-cart/checkout/; (23) search_by parameter in the admin/AddressesList.php page to wp-admin/admin.php; (24) address_id, (25) address_name, (26) firstname, (27) lastname, (28) street, (29) city, (30) postcode, or (31)
email parameter in the admin/AddressEdit.php page to wp-admin/admin.php; (32) post_id or (33) rel_type parameter in the admin/AssignedCategoriesList.php page to wp-admin/admin.php; or (34) post_type parameter in the admin/CustomFieldsList.php page to wp-admin/admin.php.
Monthly Archives: May 2015
CVE-2015-3301
Directory traversal vulnerability in the TheCartPress eCommerce Shopping Cart (aka The Professional WordPress eCommerce Plugin) plugin for WordPress before 1.3.9.3 allows remote administrators to read arbitrary files via a .. (dot dot) in the tcp_box_path parameter in the checkout_editor_settings page to wp-admin/admin.php.
CVE-2015-3427
Quassel before 0.12.2 does not properly re-initialize the database session when the PostgreSQL database is restarted, which allows remote attackers to conduct SQL injection attacks via a (backslash) in a message. NOTE: this vulnerability exists because of an incomplete fix for CVE-2013-4422.
CVE-2015-3983
The pcs daemon (pcsd) in PCS 0.9.137 and earlier does not include the HTTPOnly flag in a Set-Cookie header, which makes it easier for remote attackers to obtain potentially sensitive information via script access to this cookie. NOTE: this issue was SPLIT from CVE-2015-1848 per ADT2 due to different vulnerability types.
CVE-2015-3986
Cross-site request forgery (CSRF) vulnerability in the TheCartPress eCommerce Shopping Cart (aka The Professional WordPress eCommerce Plugin) plugin for WordPress before 1.3.9.3 allows remote attackers to hijack the authentication of administrators for requests that conduct directory traversal attacks via the tcp_box_path parameter in the checkout_editor_settings page to wp-admin/admin.php.
CVE-2015-3987
Multiple unquoted Windows search path vulnerabilities in the (1) Client Management and (2) Gateway in McAfee ePO Deep Command 2.1 and 2.2 before HF 1058831 allow local users to gain privileges via unspecified vectors.
Quick thinking hostage calls police via online pizza delivery
A quick-thinking Florida mother used an online takeaway order to raise the alarm, after her partner took the woman and her three children hostage.
The post Quick thinking hostage calls police via online pizza delivery appeared first on We Live Security.
![]()
Panda Security reached 100% protection rate in AV-Comparatives’ tests
We have great news! Panda Security has obtained excellent results in April’s Real World Protection Test! And we are not the ones that say it! ![]()
According to AV-Comparatives, we have achieved 100% detection rate in the tests conducted by this independent institute with a worldwide reputation.
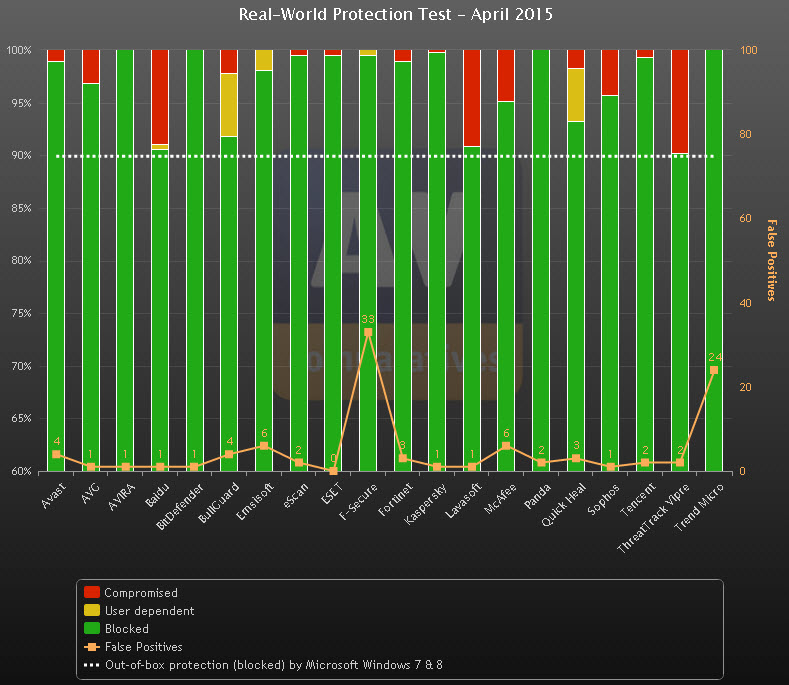
These results can only confirm the great results provided by the XMT™ scan engine, which is now included in all consume products.
Panda Security develops their products in response to the evolution of malware in recent years. Therefore, the XMT™ engine is the most effective response against threats like Cryptolocker and ransomware, of which we have all heard so much about in the last few months.

For example, in Spain, people are receiving an email that supposedly comes from the national post service informing you that a package has arrived and you have to collect it. But once you download it, it kidnaps your computer’s and asks you for a ransom if you want it back.
But we are not satisfied with these great results. Our objective is to keep up with the latest threats, so we can build a safer world. Try our free antivirus and enjoy the maximum protection!
The post Panda Security reached 100% protection rate in AV-Comparatives’ tests appeared first on MediaCenter Panda Security.
CryptoLocker: What Is and How to Avoid it
CryptoLocker is a new family of ransomware whose business model (yes, malware is a business to some!) is based on extorting money from users. This continues the trend started by another infamous piece of malware which also extorts its victims, the so-called ‘Police Virus’, which asks users to pay a ‘fine’ to unlock their computers. However, unlike the Police Virus, CryptoLocker hijacks users’ documents and asks them to pay a ransom (with a time limit to send the payment).
Malware installation
CryptoLocker uses social engineering techniques to trick the user into running it. More specifically, the victim receives an email with a password-protected ZIP file purporting to be from a logistics company.
The Trojan gets run when the user opens the attached ZIP file, by entering the password included in the message, and attempts to open the PDF it contains. CryptoLocker takes advantage of Windows’ default behavior of hiding the extension from file names to disguise the real .EXE extension of the malicious file.
As soon as the victim runs it, the Trojan goes memory resident on the computer and takes the following actions:
- Saves itself to a folder in the user’s profile (AppData, LocalAppData).
- Adds a key to the registry to make sure it runs every time the computer starts up.
- Spawns two processes of itself: One is the main process, whereas the other aims to protect the main process against termination.
File encryption
The Trojan generates a random symmetric key for each file it encrypts, and encrypts the file’s content with the AES algorithm, using that key. Then, it encrypts the random key using an asymmetric public-private key encryption algorithm (RSA) and keys of over 1024 bits (we’ve seen samples that used 2048-bit keys), and adds it to the encrypted file. This way, the Trojan makes sure that only the owner of the private RSA key can obtain the random key used to encrypt the file. Also, as the computer files are overwritten, it is impossible to retrieve them using forensic methods.
Once run, the first thing the Trojan does is obtain the public key (PK) from its C&C server. To find an active C&C server, The Trojan incorporates a domain generation algorithm (DGA) known as ‘Mersenne twister’ to generate random domain names. This algorithm uses the current date as seed and can generate up to 1,000 different fixed-size domains every day.

After the Trojan has downloaded the PK, it saves it inside the following Windows registry key: HKCUSoftwareCryptoLockerPublic Key. Then, it starts encrypting files on the computer’s hard disk and every network drive the infected user has access to.
CryptoLocker doesn’t encrypt every file it finds, but only non-executable files with the extensions included in the malware’s code:

Additionally, CryptoLocker logs each file encrypted to the following registry key:
HKEY_CURRENT_USERSoftwareCryptoLockerFiles
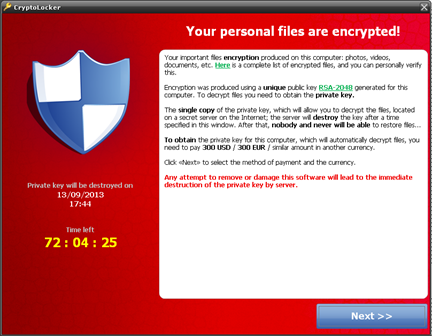
When the Trojan finishes encrypting every file that meets the aforementioned conditions, it displays the following message asking the user to make a ransom payment, with a time limit to send the payment before the private key kept by the malware writer is destroyed.

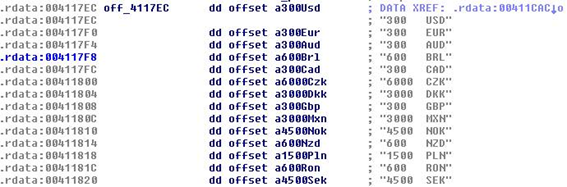
Curiously enough, the malware doesn’t ask users for the same amount of money, but incorporates its own currency conversion table.
How to avoid CryptoLocker
This malware spreads via email by using social engineering techniques. Therefore, our recommendation are:
- Being particularly wary of emails from senders you don’t know, especially those with attached files.
- Disabling hidden file extensions in Windows will also help recognize this type of attack.
- We’d like to remind you of the importance of having a backup system in place for your critical files. This will help mitigate the damage caused not only by malware infections, but hardware problems or any other incidents as well.
- If you become infected and don’t have a backup copy of your files, our recommendation is not to pay the ransom. That’s NEVER a good solution, as it turns the malware into a highly profitable business model and will contribute to the flourishing of this type of attack.
The post CryptoLocker: What Is and How to Avoid it appeared first on MediaCenter Panda Security.
Sofa & chair quote
Dear Director, Have a good day! We are leather/fabric chair and sofa factory from Foshan city, China. Our booth No. in Guangzhou Furniture Fair is: S11.2 A06 last month. Do you visit this fair every year? Our fabric sofa and chesterfield sofa are very hot sale, high quality leather chairs are with low price. Reply this email to get our updated wholesale price list with photos, welcome related inquiry, we will do the best to quote you good price ASAP. -- Best Rgds. Jackie Mobile:+86 186 765 12539 ( Wechat app ID ) KANGYU FURNITURE CO.,LTD Add:Baili Building,NO.1 Shangtang Yuxiu Road, Paisha Industrial Zone,Longjiang Town,Shunde District,Foshan City,Guangdong Prov.China. Tel:0086-757-28682885 Fax:0086-757-28682887 Skype ID: kyseating