Monthly Archives: June 2015
CEBA-2015:1079 CentOS 7 libkkc FASTTRACK BugFixUpdate
CentOS Errata and Bugfix Advisory 2015:1079 Upstream details at : https://rhn.redhat.com/errata/RHBA-2015-1079.html The following updated files have been uploaded and are currently syncing to the mirrors: ( sha256sum Filename ) x86_64: f72ca297b82c1c64820422ed9f647ace9fe50446bf38fc3abb3991b632f239e1 libkkc-0.3.1-8.el7.i686.rpm f494db421c0bbcfd8e24de7289d5df99dbdb98a39bdc312ea184fde4193852af libkkc-0.3.1-8.el7.x86_64.rpm fb4d6fc9d750336d8f1879853bc8c50dd9cd06fec252ba6c8c85540a1b400977 libkkc-common-0.3.1-8.el7.noarch.rpm ed56e7c8d649e0a5dca0e78cde836456cea822ff8211cf00fe4110549d2e38e9 libkkc-data-0.3.1-8.el7.x86_64.rpm 0277cf9089f87e750f8eff694a09c66d74ea28921f0006d567cb40b76dd2dc3d libkkc-devel-0.3.1-8.el7.i686.rpm 8e9149c2477ea3cc3466df9057493a6e931a45713f08d0599438e90502a36762 libkkc-devel-0.3.1-8.el7.x86_64.rpm 7016a52b3ec0b7628fcb48bedf8073e39321a20412201f36c998d273570ff020 libkkc-tools-0.3.1-8.el7.x86_64.rpm Source: 07fc65cbb673afebf64d55cfbc87e3c67fed8956242da4a34def25c4264212a2 libkkc-0.3.1-8.el7.src.rpm
CEBA-2015:1080 CentOS 6 poppler BugFix Update
CentOS Errata and Bugfix Advisory 2015:1080 Upstream details at : https://rhn.redhat.com/errata/RHBA-2015-1080.html The following updated files have been uploaded and are currently syncing to the mirrors: ( sha256sum Filename ) i386: 8e8e76e53c0a4d9c2ed788c861c87febfcf47fef486a69ab6fbcf35b3458110d poppler-0.12.4-4.el6_6.1.i686.rpm 5f95e17deba7a0ad146a869f4d92b43f9e793a1ba4423128d01cd6243dbff34e poppler-devel-0.12.4-4.el6_6.1.i686.rpm c7d016163896282784b4809f5eb7bd80f769eb963a09c19c70da5e11d6390374 poppler-glib-0.12.4-4.el6_6.1.i686.rpm cab1dea9ae253058c7710a6735c93c2ed7411dc8c3508ca8fb6bbdcc54e64561 poppler-glib-devel-0.12.4-4.el6_6.1.i686.rpm a25d43ed8a3b788aadc6823d2ff4d92802596dfd2581b26da001eab43086ff08 poppler-qt-0.12.4-4.el6_6.1.i686.rpm 38a390e5646075692625dd27d365a416ee18d1b6687a4e4a61449a77b512cf1d poppler-qt4-0.12.4-4.el6_6.1.i686.rpm 2530f0f0908fd8dc9edbb48ecd63fa9d933759703d3dbaa6b5a90e7a1a60edca poppler-qt4-devel-0.12.4-4.el6_6.1.i686.rpm cedcdaed307c77deb0065432db5e938ca7f8f133365acfe6f1e4960ef14fbf82 poppler-qt-devel-0.12.4-4.el6_6.1.i686.rpm 0f88be29e2dc32dbb10fc4605751b52b35b544f82fd92c0f4bdde0ed08b36044 poppler-utils-0.12.4-4.el6_6.1.i686.rpm x86_64: 8e8e76e53c0a4d9c2ed788c861c87febfcf47fef486a69ab6fbcf35b3458110d poppler-0.12.4-4.el6_6.1.i686.rpm 45380d87713a77213843d347de2f75a3f590266dafaa90364ccc642b731c8d0c poppler-0.12.4-4.el6_6.1.x86_64.rpm 5f95e17deba7a0ad146a869f4d92b43f9e793a1ba4423128d01cd6243dbff34e poppler-devel-0.12.4-4.el6_6.1.i686.rpm 782d8fb3d989c2e2696ea2170196e4e88b1fa16eab8a98dac46f92fcd20d6e37 poppler-devel-0.12.4-4.el6_6.1.x86_64.rpm c7d016163896282784b4809f5eb7bd80f769eb963a09c19c70da5e11d6390374 poppler-glib-0.12.4-4.el6_6.1.i686.rpm 5c43eb94a9ab48b14d2e686537384e9cefa34e25a89b4e7ee717bcdceaf2a80a poppler-glib-0.12.4-4.el6_6.1.x86_64.rpm cab1dea9ae253058c7710a6735c93c2ed7411dc8c3508ca8fb6bbdcc54e64561 poppler-glib-devel-0.12.4-4.el6_6.1.i686.rpm 3e01b811e994d1bf79be049c6e271e30b45666b207e8559c6bfc1a44a2a283c2 poppler-glib-devel-0.12.4-4.el6_6.1.x86_64.rpm a25d43ed8a3b788aadc6823d2ff4d92802596dfd2581b26da001eab43086ff08 poppler-qt-0.12.4-4.el6_6.1.i686.rpm 5c543f1e90f5b67d462e18deec23ac3973069d9eff6d544177387e632b28c09d poppler-qt-0.12.4-4.el6_6.1.x86_64.rpm 38a390e5646075692625dd27d365a416ee18d1b6687a4e4a61449a77b512cf1d poppler-qt4-0.12.4-4.el6_6.1.i686.rpm 4a16705af06046de087e904cd4fa47d1c6ba17ddbec70dbe3cac5c5d4f96f710 poppler-qt4-0.12.4-4.el6_6.1.x86_64.rpm 2530f0f0908fd8dc9edbb48ecd63fa9d933759703d3dbaa6b5a90e7a1a60edca poppler-qt4-devel-0.12.4-4.el6_6.1.i686.rpm ad816c4ac8c762eb8a86224210352074a5a75199d594fa49e4d10061429a711f poppler-qt4-devel-0.12.4-4.el6_6.1.x86_64.rpm cedcdaed307c77deb0065432db5e938ca7f8f133365acfe6f1e4960ef14fbf82 poppler-qt-devel-0.12.4-4.el6_6.1.i686.rpm fceee9f1a5be602e2c3ed6b44e9f0ad4e4e851c1ec734920d029bdadc5088354 poppler-qt-devel-0.12.4-4.el6_6.1.x86_64.rpm 1bedfd17f316dedc395a9a0a90e7f8237350f1bc223f8641b197a2069cc5bbe7 poppler-utils-0.12.4-4.el6_6.1.x86_64.rpm Source: 865b1d2c28241190a131aace26b8eebfd481aa27e600e13bc80f6721d01ec157 poppler-0.12.4-4.el6_6.1.src.rpm
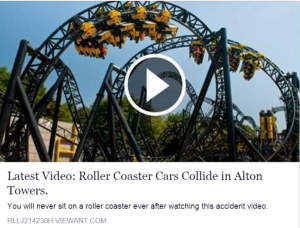
Alton Towers Facebook Scam
Following an accident at Alton Towers – a theme and water park in the United Kingdom, a Facebook scam has emerged that purports to show video footage of the accident. Beware: this is a scam, which we shall now dissect for you.
Step 1: The hook
This teaser Facebook post is supposedly taken from the accident (it is not). If you click on it with the (macabre) hope of seeing a video of the crash, you will be taken to a website that has been designed to look just like YouTube.
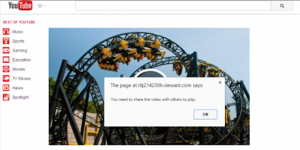
Step 2: The fake look-alike
Once on that page, you will be asked to post a link to the video on your Facebook timeline…
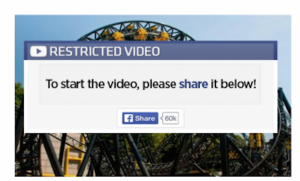
Step 3: The redirect
Once you accept to post the video to Facebook, you will be redirected to another website, where you will be told that to finally see that video, you need to download a video player update…
The downloaded file contains adware, that display advertisements and collects information about your browsing habits. The crooks almost certainly make money by getting a percentage of all sales on these third party ads you will be seeing in your browser.
If you see this Alton Towers scam on Facebook, avoid it. If you click on a post that tells you to download a plugin or update to watch the video, exit the page immediately. And for additional security, use Avira Free Antivirus, which blocks adware.
The post Alton Towers Facebook Scam appeared first on Avira Blog.
US Army website defaced by Syrian Electronic Army hackers
Hackers, supportive of the Assad regime in Syria, have successfully compromised content displayed on the US Army’s website, popping up messages to visitors
The post US Army website defaced by Syrian Electronic Army hackers appeared first on We Live Security.
![]()
WhatsApp Trendy Blue, the program which signs you up to a premium rate. Watch out!
One more, there have been so many, we’ve lost track! WhatsApp Trendy Blue is the last hoax to deceive the users of this instant messaging application.

WhatsApp Trendy Blue, the new “version” that promises new options to customize the users’ WhatsApp. In fact, it is only subscribing the user to a premium rate service, which it is not exactly cheap.
From Movistar, a Spanish telephone company, they warn that for the program to work, it asks the user to invite at least 10 contacts, who will receive a message recommending them to sign up for this fraudulent website.
So please, don’t fall for these traps, only trust the versions offered by the official stores!
The post WhatsApp Trendy Blue, the program which signs you up to a premium rate. Watch out! appeared first on MediaCenter Panda Security.
Impact of Healthcare Data Breaches Goes Beyond Financial
This past week, CareFirst, a U.S. based BlueCross and BlueShield insurer with coverage in Mid-Atlantic States, revealed that 1.1 million user accounts were compromised. CareFirst is the third U.S. health insurance company to publicly acknowledge a data breach recently, following Premera Blue Cross and Anthem. It seems relatively small potatoes compared to the Premera (11 million people) and Anthem, which acknowledged that hackers broke into a database containing personal information for about 80 million of its customers and employees. But if you’re one of the 1.1 million, it isn’t small potatoes.
It can also hit very close to home. I just discovered friends of mine were among those caught up in the Anthem hack, which also led to them being part of the income tax fraud scheme that I and my fellow blogger, Tony Anscombe, have written about previously. My friends were tipped off when a new credit card arrived that they hadn’t ordered. Shortly after, they tried to file their income taxes and found they’d already been filed –and a substantial over-payment (not based on their calculations) had already been claimed by the perpetrator.
CareFirst said that the attackers gained limited, unauthorized access to a single CareFirst database. CareFirst said the attackers didn’t get access to Social Security numbers, employment info, financial data, medical data or consumer passwords –because those are encrypted and stored in a separate system.
However, attackers could have potentially acquired members’ names, birth dates, email addresses and subscriber identification number. (You can also see the full statement from CareFirst on its website.)
The attack occurred in June 2014, two months after the insurer detected an attack that the organization thought it had contained… But the hackers had left behind hidden back doors that let them re-enter later, undetected, according to reports, by the Baltimore Sun and others.
According to CareFirst, it has run comprehensive internal security tests, and hired an outside security company for further assessment, as well. It is offering two years of free credit monitoring and identity theft protection services for those members affected. Finally, it is letting those customers know who might be compromised. (Anthem did this also, though my friend was not among those notified…)
IT security has to be a priority for all businesses, but particularly for healthcare, where the stakes are so high. The healthcare industry needs to conduct extensive ongoing internal IT evaluations and adopt stricter policies – especially around what data they need to keep and for how long.
According to a new research by Ponemon Institute sponsored by IBM, “2015 Cost of Data Breaches Study”, data breaches in healthcare are the most expensive to remediate and only going up. The study covered 350 companies in 11 countries across 16 industries.
Consider the case of the UK-based Cottage Healthcare Systems. Hackers swiped 32,500 patient records and its customers sued Cottage for $4.1 million. Its insurance company, Columbia Casualty Company, settled the claims. But now Columbia has come back to Cottage to recoup the settlement, because it claims Cottage did not provide adequate and secure IT systems, so it wants its money back.
As consumers, we have to do more too. We need to monitor the activities on all of our accounts, financial and via our health care providers and insurance companies– and note anything that’s irregular or suspicious.
You can find some helpful information on the Federal Trade Commission (FTC) website to identify signs of medical identity theft, including these:
- A bill for medical services you didn’t receive
- A call from a debt collector about a medical debt you don’t owe
- A notice from your insurer saying you reached your benefit limit or denial of insurance for a condition you don’t have.
The FTC encourages visiting IdentityTheft.gov to report incidents and get information on how to recover from identity theft.
![]()
![]()