Bug bounties and rewards programs provide researchers with a measure of income, and if the proposed Wassenaar rules are implemented in the U.S., that initiatives could be adversely impacted.
Monthly Archives: June 2015
The Weapons Pact Threatening IT Security Research
Hacker Can Send Fatal Dose To Hospital Drug Pumps
Why The "Biggest Government Hack Ever" Got Past The Feds
Release for CentOS Linux 7 x86_64 Vagrant Box
We are pleased to announce the immediate availability for CentOS Linux 7 x86_64 images for Vagrant. This image represents a minimal install set, that lines up with the user expectation for our Cloud Images, our ISO based Minimal installer and the default minimal install profile from the in-distro install options. Images are released for the VirtualBox and LibVirt providers ( more providers coming soon ). They are also available on the Vagrant Cloud / Atlas service at : https://atlas.hashicorp.com/centos/boxes/7 Anyone using vagrant already can get started with the following two commands : vagrant init centos/7 vagrant up -------- The backing files are available for direct download at : * LibVirt: http://cloud.centos.org/centos/7/vagrant/x86_64/images/CentOS-7-Vagrant-1505-x86_64-01.LibVirt.box sha256: 49ac77893c1609d9d79b1b3f1fd0526d77a01cb62563c7c507099c5ab785a6f1 * VirtualBox: http://cloud.centos.org/centos/7/vagrant/x86_64/images/CentOS-7-Vagrant-1505-x86_64-01.box sha256: 572c5ce3fc4e1a1efe274f5c30bc1645240bf1702fcdcd1976e67988d04df001 * Generic Qcow2: http://cloud.centos.org/centos/7/vagrant/x86_64/images/CentOS-7-Vagrant-1505-x86_64-01.qcow2 sha256: 70e703fa22f09dd0257bfe0e625a33f3cf2d7a98d5264ac75fdf1aa06336d1b3 Note: this generic qcow2 file is pre-seeded with the vagrant user, and can be used to setup backing instances for more providers. -------- If you intend to hardcode urls into automation scripts etc, I highly recommend using the short link urls, these point at the latest released image set and will be updated when backing media is updated for security issues, bugfix, feature upgrades. virtualbox: http://cloud.centos.org/centos/7/vagrant/x86_64/images/CentOS-7.box libvirt: http://cloud.centos.org/centos/7/vagrant/x86_64/images/CentOS-7.LibVirt.box -------- Update cycles for these images is currently set to once per month, but we might update out of band for major security issues. Every update will see a new image set released, with the short link urls pointed to the new images. all image updates will be announced to the centos-announce list. We welcome all feedback, find us on the CentOS-Devel list (http://lists.centos.org ), or in #centos-devel on irc.freenode.net or on our issue tracker at http://bugs.centos.org/ Enjoy,
What’s new in AVG AntiVirus for Android
At AVG we’re determined to keep listening to your feedback and improve our products. This week, we’re releasing an update to AVG AntiVirus for Android which we believe will give users a fresh new experience.
Anti-Theft Password Recovery
One of the most popular features in the existing version of AVG AntiVirus for Android is the Anti-Theft Password. Our users love the extra security that AVG provides by adding an extra security should their device be lost or stolen.
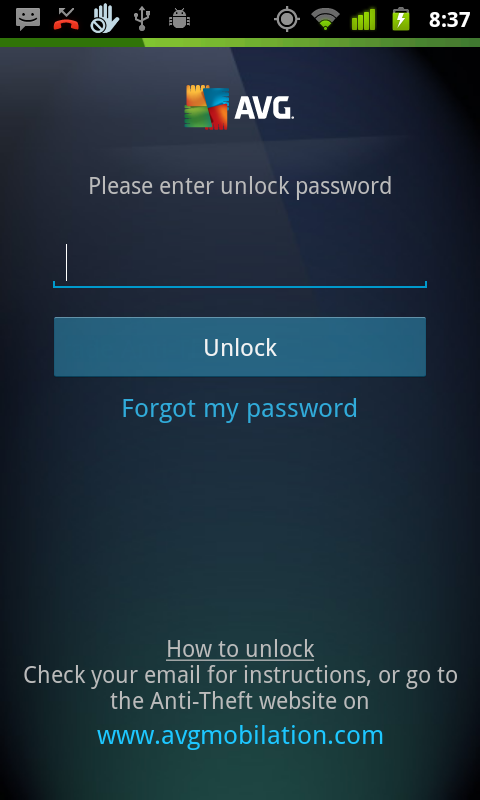
In the latest version, we’ve introduced a password recovery option to help users that may have forgotten their Anti-Theft password. This will help them secure their device with a minimum of stress.
Improved scanning experience
The main priority for any security app is to keep you safe and inform you of any threats on your device. That’s why we’ve revamped our scanning experience so that you can understand at a glance what we have found on your device.
What’s more, with our on the fly results, you don’t have to wait until the end of a scan to see any issues.
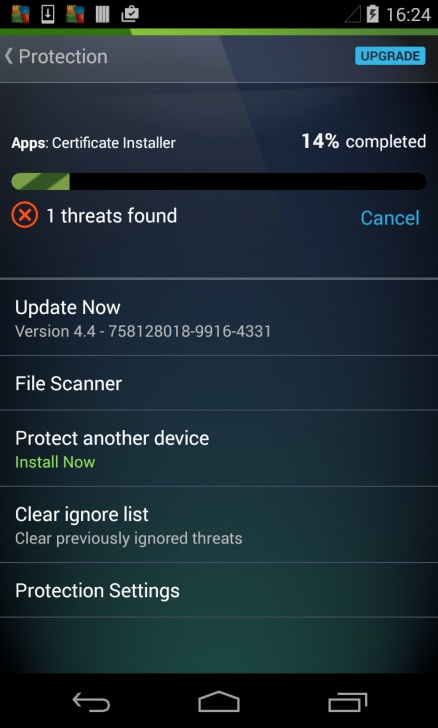
Additional changes
As well as these changes, we’ve included some additional bug fixes for improved performance and user experience.
![]()
![]()
CVE-2014-6284
SAP Adaptive Server Enterprise (ASE) before 15.7 SP132 and 16.0 before 16.0 SP01 allows remote attackers to bypass the challenge and response mechanism and obtain access to the probe account via a crafted response, aka SAP Security Note 2113995.
CVE-2015-2993
SysAid Help Desk before 15.2 does not properly restrict access to certain functionality, which allows remote attackers to (1) create administrator accounts via a crafted request to /createnewaccount or (2) write to arbitrary files via the fileName parameter to /userentry.
CVE-2015-2994
Unrestricted file upload vulnerability in ChangePhoto.jsp in SysAid Help Desk before 15.2 allows remote administrators to execute arbitrary code by uploading a file with a .jsp extension, then accessing it via a direct request to the file in icons/user_photo/.
CVE-2015-2995
SysAid Help Desk before 15.2 does not properly check file extensions, which allows remote attackers to upload and execute arbitrary files via a NULL byte after the extension, as demonstrated by a .war%00 file.
