CA Technologies Support is alerting customers to multiple potential risks with products that bundle CA Common Services on Unix/Linux platforms. A local attacker may exploit these vulnerabilities to gain additional privileges.
Monthly Archives: June 2015
TGIF: Wrap-up May 6 – June 5
We have had a busy month with multiple announcements important to Avast customers and company-watchers. Here’s the quick rundown in case you missed it.
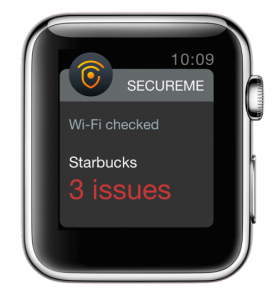
Avast SecureMe will launch in the next month or so to protect the new Apple Watch, as well as iPhones and iPads, when connected to unsecured Wi-Fi. That’s sure to make Apple gadget freaks happy. Read Avast SecureMe Protects Apple Watch Wi-Fi Users.
Image via TechRadar
Windows 10 is scheduled to launch in July, and Avast is ready. Avast version V2015 R2 and newer are already compatible with Windows 10. Read Latest versions of Avast compatible with Windows 10.
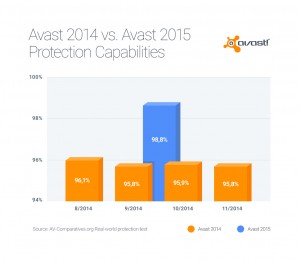 Avast customers who are using older versions of our Avast antivirus products cannot upgrade to Windows 10, but more importantly they will no longer receive product upgrades or enhancements. We recommend that everyone upgrade to the latest version to benefit from better detection rates and new features. Read Support for older Avast versions will end.
Avast customers who are using older versions of our Avast antivirus products cannot upgrade to Windows 10, but more importantly they will no longer receive product upgrades or enhancements. We recommend that everyone upgrade to the latest version to benefit from better detection rates and new features. Read Support for older Avast versions will end.
 The new Android powered tablets by ASUS come preloaded with Avast Mobile Security, so you are protected right out of the box. Read New ASUS ZenPad to come with Avast Mobile Security.
The new Android powered tablets by ASUS come preloaded with Avast Mobile Security, so you are protected right out of the box. Read New ASUS ZenPad to come with Avast Mobile Security.
 Want a career with Avast? A new Avast Software office has opened in Charlotte, North Carolina to bring the new free Avast for Business to the U.S. market and beyond. Read The Tar Heel State welcomes Avast Software.
Want a career with Avast? A new Avast Software office has opened in Charlotte, North Carolina to bring the new free Avast for Business to the U.S. market and beyond. Read The Tar Heel State welcomes Avast Software.
Check out the Avast blog for other news and how-to articles that provide useful information about security, privacy, and Avast products. Have a great weekend! ![]()
Fedora 20 Security Update: armacycles-ad-0.2.8.3.3-1.fc20
Changes since 0.2.8.3.2:
– security fix: do not read ahead of the beginning of network buffer.
– security fix: don’t attribute network errors from processing random
packets to the connection to the server
– security fix: while at it, don’t process random packets unless they
may be important
– fix for potential crash with friend list filtering
– intel driver compatibility
– fix for rare crash with sound lock
– fix for camera turning for bizarre axis configurations
Fedora 22 Security Update: armacycles-ad-0.2.8.3.3-1.fc22
Changes since 0.2.8.3.2:
– security fix: do not read ahead of the beginning of network buffer.
– security fix: don’t attribute network errors from processing random
packets to the connection to the server
– security fix: while at it, don’t process random packets unless they
may be important
– fix for potential crash with friend list filtering
– intel driver compatibility
– fix for rare crash with sound lock
– fix for camera turning for bizarre axis configurations
Fedora 21 Security Update: qpid-cpp-0.32-4.fc21
Resolved Bugs
1224260 – [abrt] python-qpid: qpid-python-test:563::ImportError: No module named tests
1181721 – CVE-2015-0203 qpid-cpp: 3 qpidd DoS issues in AMQP 0-10 protocol handling
1186308 – CVE-2015-0223 qpid-cpp: anonymous access to qpidd cannot be prevented
1184488 – build failure in qpid-cpp-0.30/src/tests/txshift.cpp<br
Removed qpid-send and qpid-receive from qpid-cpp-client-devel.
Include the qpid.tests module in python-qpid
Bumped the release to force a build against Proton 0.9 in F22.
Added qpidtoollibs to the qpid-tools package.
Fixed path to qpid-ha in the systemd service descriptor.
Resolves: BZ#1186308
Apply patch 10.
Resolves: BZ#1184488
Resolves: BZ#1181721
Fedora 21 Security Update: armacycles-ad-0.2.8.3.3-1.fc21
Changes since 0.2.8.3.2:
– security fix: do not read ahead of the beginning of network buffer.
– security fix: don’t attribute network errors from processing random
packets to the connection to the server
– security fix: while at it, don’t process random packets unless they
may be important
– fix for potential crash with friend list filtering
– intel driver compatibility
– fix for rare crash with sound lock
– fix for camera turning for bizarre axis configurations
Fedora 22 Security Update: redis-2.8.21-1.fc22
Fedora 20 Security Update: xen-4.3.4-5.fc20
Resolved Bugs
1223846 – CVE-2015-4103 xen: potential unintended writes to host MSI message data field via qemu (xsa-128)
1227627 – CVE-2015-4103 xen: potential unintended writes to host MSI message data field via qemu (xsa-128) [fedora-all]
1223851 – CVE-2015-4104 xen: PCI MSI mask bits inadvertently exposed to guests (xsa-129)
1227628 – CVE-2015-4104 xen: PCI MSI mask bits inadvertently exposed to guests (xsa-129) [fedora-all]
1223853 – xen: guest triggerable qemu MSI-X pass-through error messages (xsa-130)
1227629 – CVE-2015-4105 xen: guest triggerable qemu MSI-X pass-through error messages (xsa-130) [fedora-all]
1223859 – xen: unmediated PCI register access in qemu (xsa-131)
1227631 – CVE-2015-4106 xen: unmediated PCI register access in qemu (xsa-131) [fedora-all]<br
Potential unintended writes to host MSI message data field via qemu
[XSA-128, CVE-2015-4103],
PCI MSI mask bits inadvertently exposed to guests [XSA-129,
CVE-2015-4104],
Guest triggerable qemu MSI-X pass-through error messages [XSA-130,
CVE-2015-4105],
Unmediated PCI register access in qemu [XSA-131, CVE-2015-4106]
Fedora 21 Security Update: redis-2.8.21-1.fc21
Fedora 21 Security Update: xen-4.4.2-5.fc21
Resolved Bugs
1227627 – CVE-2015-4103 xen: potential unintended writes to host MSI message data field via qemu (xsa-128) [fedora-all]
1227628 – CVE-2015-4104 xen: PCI MSI mask bits inadvertently exposed to guests (xsa-129) [fedora-all]
1227629 – CVE-2015-4105 xen: guest triggerable qemu MSI-X pass-through error messages (xsa-130) [fedora-all]
1227631 – CVE-2015-4106 xen: unmediated PCI register access in qemu (xsa-131) [fedora-all]
1223846 – CVE-2015-4103 xen: potential unintended writes to host MSI message data field via qemu (xsa-128)
1223851 – CVE-2015-4104 xen: PCI MSI mask bits inadvertently exposed to guests (xsa-129)
1223853 – xen: guest triggerable qemu MSI-X pass-through error messages (xsa-130)
1223859 – xen: unmediated PCI register access in qemu (xsa-131)<br
Potential unintended writes to host MSI message data field via qemu
[XSA-128, CVE-2015-4103],
PCI MSI mask bits inadvertently exposed to guests [XSA-129,
CVE-2015-4104],
Guest triggerable qemu MSI-X pass-through error messages [XSA-130,
CVE-2015-4105],
Unmediated PCI register access in qemu [XSA-131, CVE-2015-4106]