Our blogpost from a few days ago, NSA and GCHQ Have Been Spying on Antivirus Companies, contained our response to recent revelations that the NSA and GCHQ had been targeting antivirus vendors located outside the US and UK. The original story was published by The Intercept, and contained an image from a PowerPoint presentation listing all the potential targets which included Avira, AVAST, and AVG, among others.
We then issued our blog post indicating that our role as a security company is to keep intruders out – even if they might be governments. So far, so good.
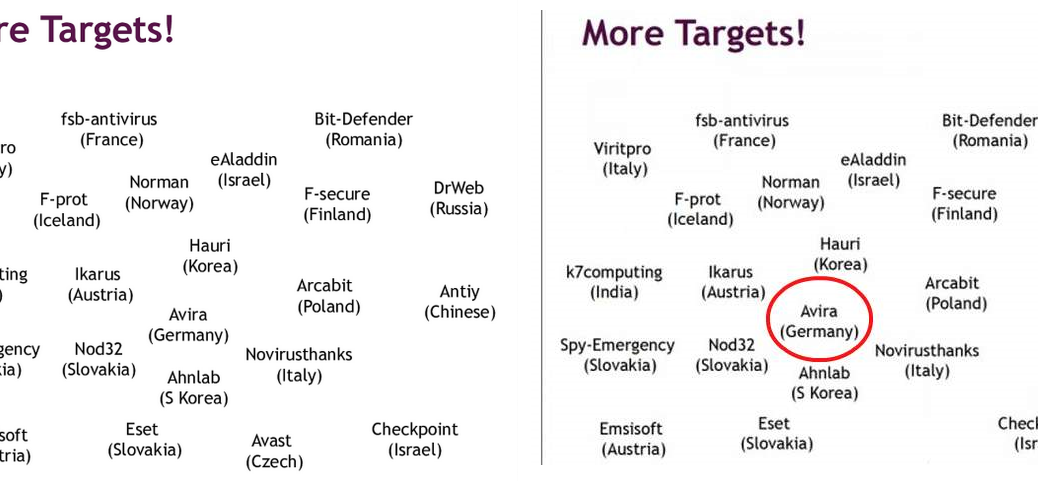
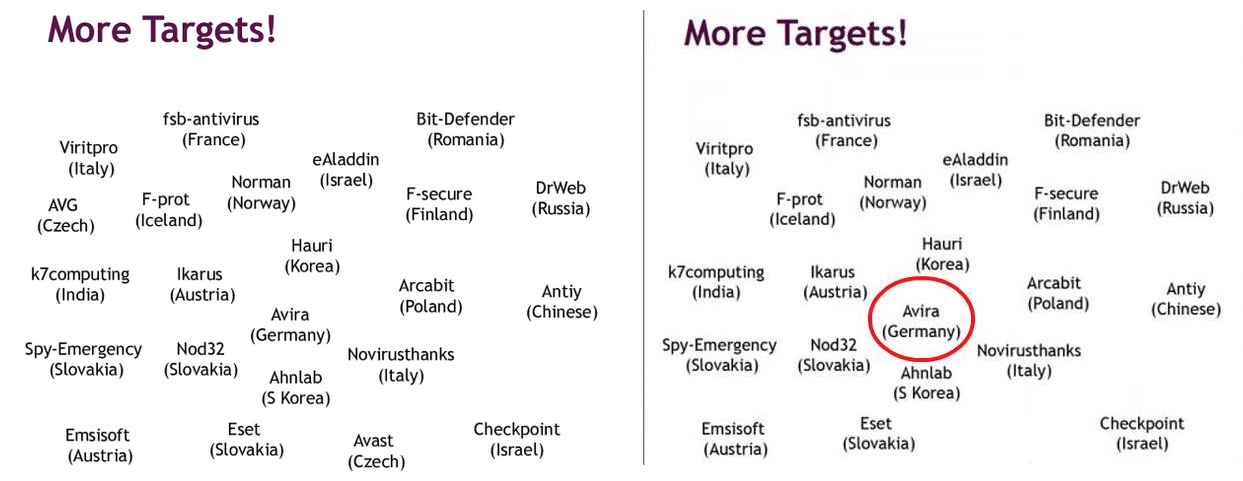
Yesterday though, it was brought to our attention that a German website had published an article telling readers that Avira has been attacked by the NSA and that they should instead download AVAST, AVG, or G-Data, because they are more secure. This in itself is not an uncommon tactic and definitely no reason to go ahead and write a blog post – if it would have ended here. Which it didn’t: both AVAST and AVG have been removed from the list of targets (we’re not sure why, but perhaps to give the article more gravitas …)
Can you spot the difference?
Original from The Intercept (left) / Falsified image from freeware.de (right)
As you can see in the version reported by freeware.de, only Avira has been carefully encircled, while both AVG and AVAST have been removed.
Who is behind this? We are not sure, but we want our customers to be aware that this information presented is false.
The post We Focus on Customers, Others Play Dirty Tricks appeared first on Avira Blog.