Debian Linux Security Advisory 3293-1 – Tim McLean discovered that pyjwt, a Python implementation of JSON Web Token, would try to verify an HMAC signature using an RSA or ECDSA public key as secret. This could allow remote attackers to trick applications expecting tokens signed with asymmetric keys, into accepting arbitrary tokens.
Monthly Archives: June 2015
GCHQ Broke Rules When Spying On NGOs
Reports Tie Together Anthem And OPM Data Breaches
HP Releases Details, Exploit Code For Unpatched IE Flaws
This Radio Bug Can Steal Laptop Crypto Keys, Fits Inside A Pita
Apple reinforces security with iOS 9 and OS X El Capitan
Moscone Center in San Francisco (California), the same convention center where Google or Intel hold their events, welcomed around 5,000 developers between June 8th and 12th. All attended Apple’s annual Worldwide Developers Conference (WWDC).
Cupertino’s company officials revealed some of the features of the brand’s new operating systems, which are already available in their beta version. IPhones and iPads will update to iOS 9 and Mac computers to OS X 10.11 El Capitan, named after a vertical rock formation in Yosemite National Park (California).
In addition to the changes aimed to improve the user experience, in both new versions many of the innovations have to do with security. An aspect in which Apple has insisted over the past years.
One of the most obvious changes affect passwords. To increase the level of protection, the devices running iOS 9 after the update will require six digits passwords, instead of the standard four-digit one. However, you will be able to choose from several options: you can use a custom alphanumeric code, a custom numeric code or, as it was so far, a four-digit numeric code.
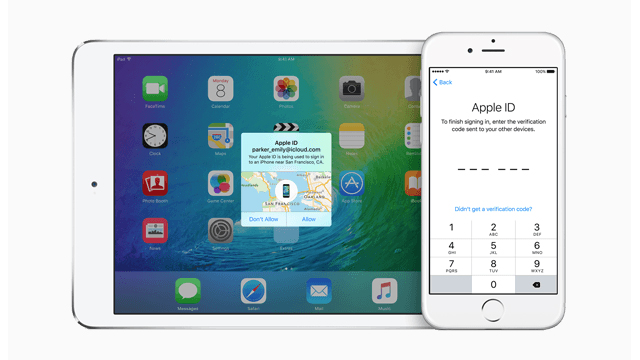
For those who decide to join the new format, this new passcode will make it more difficult for cybercriminals who want to take control over your phone or tablet. It allows over a million different combinations, significantly more than the 10,000 allowed by the current authentication method.
On the other hand, developers will have the best tools to guarantee the security of applications in their hands. With them, they will be able to connect their apps to the Internet via virtual private networks (VPN), a technology that allows a device to send and receive data in a public network with, in theory, as much security as if it was private.
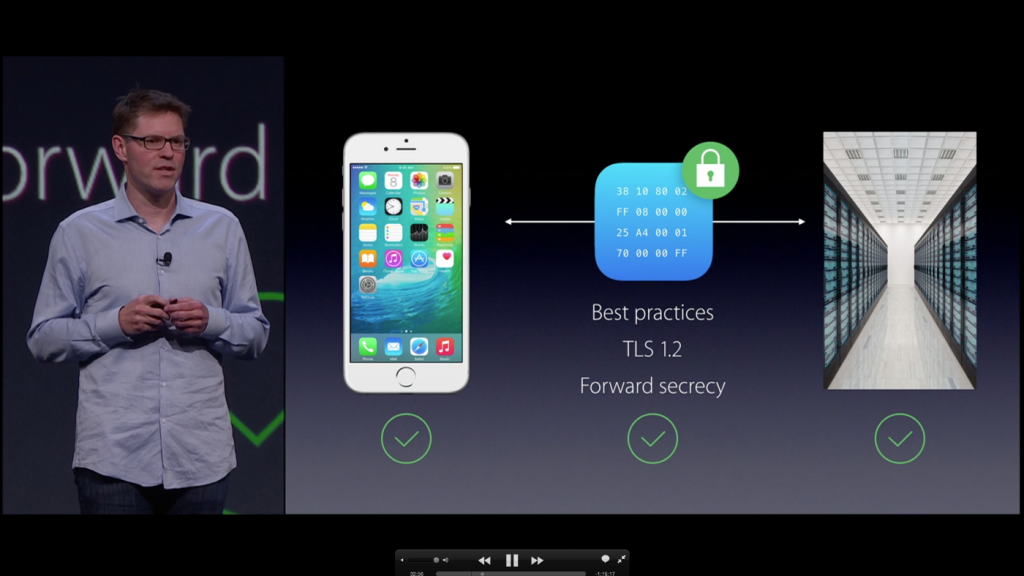
Another important innovation is related to the Secure Socket Layer (SSL), which includes the protocols that encrypt communications over the internet. iOS 9 allows users to configure their system so that all internet connections made by their applications use HTTPS, a secure data transfer protocol.
In addition, Cupertino’s team ensure that the protocols will be updated constantly to avoid security vulnerabilities.
Another iOS 9 security goodness. Apple’s SSL library (SecureTransport) has support for Certificate Transparency! pic.twitter.com/d59VtFNwoH
— Frederic Jacobs (@FredericJacobs) June 8, 2015
Safari has also improved its security measures. On the one hand, the extensions will have a certificate from Apple. Developers can distribute extensions with their own signature, but the apps will not be updated by themselves.
On the other hand, this new version includes extensions to block content (‘Content Blocking Safari extensions’), a way of preventing the execution of cookies, pop-ups, automated videos and other web content.
Despite the rumors for iOS 9 that suggested it would be ‘rootless’, which means it would not be possible to gain access to root directories, this feature does not exist in the beta versions. It is true that Apple has changed the administrators’ privileges in OS X El Capitan, so they cannot modify any of the options of the critical system files. The measure prevents the installation of some types of malware, and its persistence. There are also those who think that it will serve, rather than to protect the security, to avoid that users apply the dreaded ‘jailbreak’ to Apple’s devices.
The post Apple reinforces security with iOS 9 and OS X El Capitan appeared first on MediaCenter Panda Security.
How safe are the apps on your Android?
Privacy Advisor
As the name suggests it, the newest feature offered by Avira Antivirus Security for Android allows registered users to increase the level of privacy on their smartphones and tablets by avoiding and potentially uninstalling high risk apps.
The ap ps that are most likely to be included in this category ask for very sensitive and personal data related permissions during the installation process.
ps that are most likely to be included in this category ask for very sensitive and personal data related permissions during the installation process.
In worst cases, malicious apps can take advantage of SMS permissions to send premium messages and register users for unwanted services, sometimes leading to financial losses.
Even if there are applications that may have an important impact on the users’ privacy, some of them have a high number of permissions related to personal data because their purpose of being demands them. These applications may either be trusted by Avira itself (e.g. Community Trusted applications) due to the developer’s reputation and/or high number of downloads or can be trusted by the user himself if he knows for a fact that the app is not a security risk.
Coming soon… on Android Optimizer
Three months after releasing its Android Optimizer app, we already helped almost 500.000 users optimize the overall speed and performance of their mobile devices. Following users’ feedback, the app has already been localized to three more languages (French, Italian and Portuguese), making it easier to use.
In order to make the app even better, our mobile development team will soon release a version that supports an always-on widget, enabling users to instantly optimize their devices, at the tap of the screen.
12 million downloads and numerous awards
Avira’s efforts of enhancing mobile security are paying off, as Avira Antivirus Security for Android excels in all Independent Labs Test results. Only last month, AV-Test nominated Avira as “The best antivirus software for Android”, with 100% detection rates and a total score of 6/6 on Protection and Usability. PCSL also awarded 5 Stars for Avira in the April edition of its Android Malware Detection Test.
More than that, 12 million users have already downloaded Avira Antivirus Security for Android, making this the best reward for the Product team.
“Avira users should feel safe and protected on every device they use to connect to the Internet. My team has the important mission of securing their mobile devices and preventing all types of attacks from happening. As private data becomes an easier target on smartphones and tablets, protecting the users’ privacy is a top priority for us. We strongly believe that a feature like “Privacy Advisor” will make it easier for people to know which app is interested in their personal information and gives them the power to decide if they agree to share it or not” said Corneliu Balaban, Mobile Development Manager at Avira.
The newest version of Avira Antivirus Security for Android (version 4.1.3643) was uploaded on the Google Play Store and can be downloaded for free.
The post How safe are the apps on your Android? appeared first on Avira Blog.
RubyGems Patches Serious Redirection Vulnerability
RubyGems maintainers patched a vulnerability, reported by Trustwave and OpenDNS, that allows RubyGem clients to be redirected to an attacker-controlled gem server.
NSA and GCHQ Have Been Spying on Antivirus Companies
While not the main target of the operation, Avira was nonetheless mentioned together with several other antivirus and security firms as being at least a target of interest (It’s noteworthy that none of the targets were US or UK companies). Since the revelation we have received various requests vis-à-vis our position and capabilities regarding this affair. We are of course more than happy to share our thoughts with you.
“Avira has frequently seen efforts by governments to write malicious software that attempts to prevent, circumvent, or disable our software from protecting our users. The goal is always the same: installing their programs on the computer users’ systems without detection. These tactics are used by malware authors of all kinds, not just governments.
We at Avira are constantly improving our defense and detection mechanisms to avoid such manipulation. We also use various other systems and utilities to detect such efforts, outside of our own products. Whether a government-funded malware writer, mafia, friend or enemy, the exploitation of applications is something that we are determined to prevent from happening,” says Travis Witteveen, Chief Executive Officer of Avira.
Let’s also not forget that Avira is a founding member of IT Security made in Germany and we pride ourselves in committing, among other things, to:
- Exclusively provide IT security solutions no other third party can access (no backdoors!).
- Offer products that do not cause the transmission of crypto keys, parts of keys or access recognition.
- Eliminate vulnerabilities or avoidance methods for access control systems as fast as possible once detected.
Avira will always strive to keep those commitments, be it against your run-of-the-mill malware or attempts by governments to obtain information.
The post NSA and GCHQ Have Been Spying on Antivirus Companies appeared first on Avira Blog.
CVE-2015-4200 (ios)
Memory leak in the IPv6-to-IPv4 functionality in Cisco IOS 15.3S in the Performance Routing Engine (PRE) module on uBR10000 devices allows remote attackers to cause a denial of service (memory consumption) by triggering an error during CPE negotiation, aka Bug ID CSCug00885.