
“We suck at dealing with abuse and trolls on the platform”, said Dick Costolo, former CEO of Twitter, as he stepped down July 1, at the beginning of the year. This statement showed what any user of the social network already new: that Twitter regrettably fails to control harassment.
A recent study carried out by Pew Research Center showed that 40% of the Internet users surveyed claimed to have been victims of cyber harassment. That’s why, one of the purposes of the social network is implementing the necessary tools so that the users do not suffer the abuses of those who are hiding behind anonymity to insult and attack others.
The most recent attempt from Twitter to minimize its impact was allowing users to share with their friends their lists of blocked tweeters. Thus, you can already block several trolls at the same time. Mass-blocking.
“You can now export and share your block lists with people in your community facing similar issues or import another user’s list into your own account and block multiple accounts all at once, instead of blocking them individually”, explained from the social network’s blog.
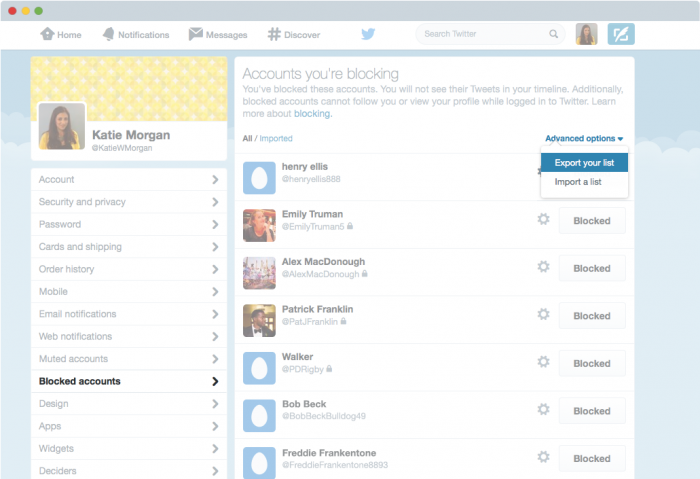
To use this new feature to import and export lists of blocked users, tweeters who want to avoid harassment on Twitter just need to follow a few simple steps, starting from the ‘Blocked accounts‘ section of the settings on Twitter:
How to export a block list on Twitter
- In the ‘blocked accounts settings’, click on ‘advanced options’ and select ‘export your list’.
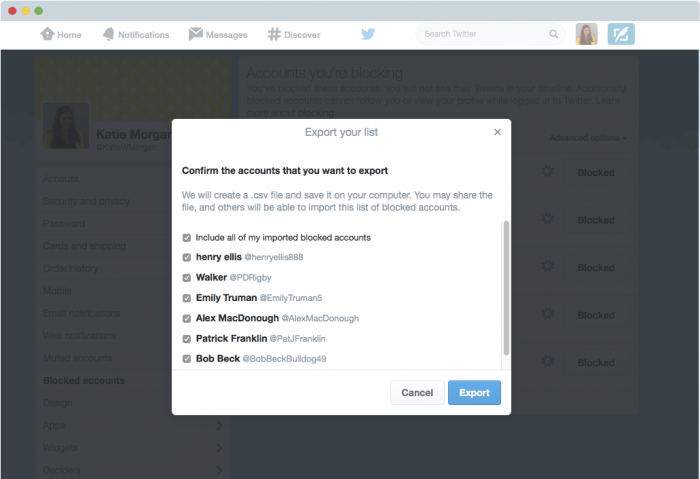
- Twitter will ask you to confirm which accounts you want to export. In this intermediate step, you have two options: select all the accounts that you have blocked with a single click or uncheck those that you don’t want to share.
- Once you have selected the accounts that you want to incorporate to the file, click ‘Export’. It will generate a .csv file that will be downloaded automatically on your computer and which you can share with who you want.
How to import a block list on Twitter
- Before starting, you must have received from a contact the .csv file corresponding to their list of blocked accounts on Twitter.
- With the file already downloaded on your computer, go to ‘advanced options’, in the ‘blocked accounts settings’, and there select ‘Import a List’.
- In the pop-up, click on the paperclip icon on the option ‘attach a file’ to upload it. From there, you must select the .csv file you had downloaded.
- It will display the list of accounts blocked by your twitter friend that shared the file with you. It will be then when you will have to select if you want to block the whole list (with just one click) or if you prefer to give some of them a chance. To do so, you will have to uncheck those accounts which you don’t want to block.
- Click on ‘Block’ to confirm your selection and automatically, the marked accounts on that list will no longer be among the potential stalkers who someday may decide to attack you on Twitter.
With these simple tools, the lists of blocked users will be shared very easily, so that Twitter users may clip with hardy any effort the wings of several trolls simultaneously (and by recommendation the contact who has shared with us his list).
The post Trolls on Twitter. How to avoid them appeared first on MediaCenter Panda Security.


