Ubuntu Security Notice 2685-1 – A flaw was discovered in the kvm (kernel virtual machine) subsystem’s kvm_apic_has_events function. A unprivileged local user could exploit this flaw to cause a denial of service (system crash). A flaw was discovered in how the Linux kernel handles invalid UDP checksums. A remote attacker could exploit this flaw to cause a denial of service using a flood of UDP packets with invalid checksums. Various other issues were also addressed.
Monthly Archives: July 2015
Malware that Just Won’t Give Up on Google Play
A team of malware authors is playing a cat and mouse game with Google. The game goes like this: they upload their malware, Google Play quickly takes it down, they upload a new mutation and Google takes it down. Current status of the game: the malware is back on Google Play. So far, the malicious apps have infected hundreds of thousands of innocent victims.
In April, we discovered porn clicker malware on Google Play posing as the popular Dubsmash app.
Mutant malware
Two days ago, we reported that a mutation of the porn clicker malware, created by a Turkish group of malware authors, made its way back onto Google Play, but have since been removed from the Play Store.
Once the apps were downloaded they did not do anything significant when opened by the user, they just showed a static image. However, once the unsuspecting victim opened his/her browser or other apps, the app began to run in the background and redirect the user to porn sites. Users may not have necessarily understood where these porn redirects were coming from, since it was only possible to stop them from happening once the app waskilled. Fellow security researchers at Eset reported that more apps with this mutation were on Google Play earlier this week. Eset also reported that the original form of the malware was uploaded to Google Play multiple times in May. Our findings combined with that from Eset, prove that these malware authors are extremely persistent and determined to make Google Play a permanent residency for their malware.
I’ll be back…
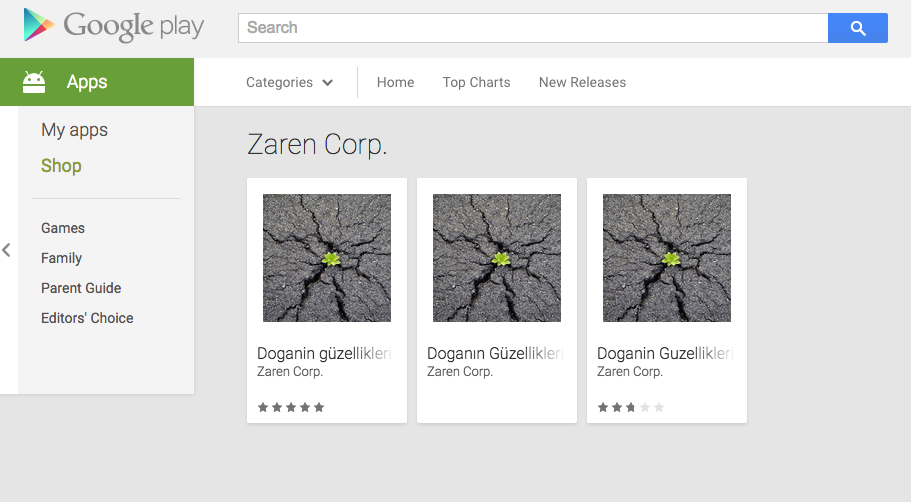
… is what the authors of this malware must have said when Google removed their apps from the Play Store earlier this week. And sure enough, their malware is back on Google Play. The malware, which Avast detects as Clicker-AR, is in the following three apps: Doganin Güzellikleri, Doganin Güzellikleri 2, Doganin Güzellikleri 3. The name translates to “Nature’s Beauties”. Avast has reported the apps to Google.
What can you do?
Google has a lot on its plate. It has to maintain the most popular mobile operating system in the world, along with an app store with around 1.5 million apps.
That is where security providers, like Avast, jump in. You don’t expect Windows to completely protect you from malware, so just as you would install antivirus on your PC as an extra layer of protection, it is vital you install antivirus on your mobile device. More and more people are using mobile devices and storing a plethora of valuable information on them. This large target pool, combined with the valuable data, naturally makes mobile devices an attractive target for cybercriminals and they are determined to come for you.
Be vigilant
In addition to having antivirus installed on your phone, make sure you do the following:
- Pay attention to app permissions. If an app requests permissions that you think it does not need to function properly, then something is probably not right with the app
- Check out the app’s reviews. If other users write bad reviews about the app, that is a sign that the app may not be something you want to download.
You can download Avast Mobile Security for free from the Google Play Store.
Hashes:
d8adb784d08a951ebacf2491442cf90d21c20192085e44d1cd22e2b6bdd4ef5f
2a14b4d190303610879a01fb6be85d577a2404dfb22ab42ca80027f3b11f1a6f
d05dcddecc2f93a17b13aa6cca587a15c4d82fe34fdb5e3acf97ddaaefb61941
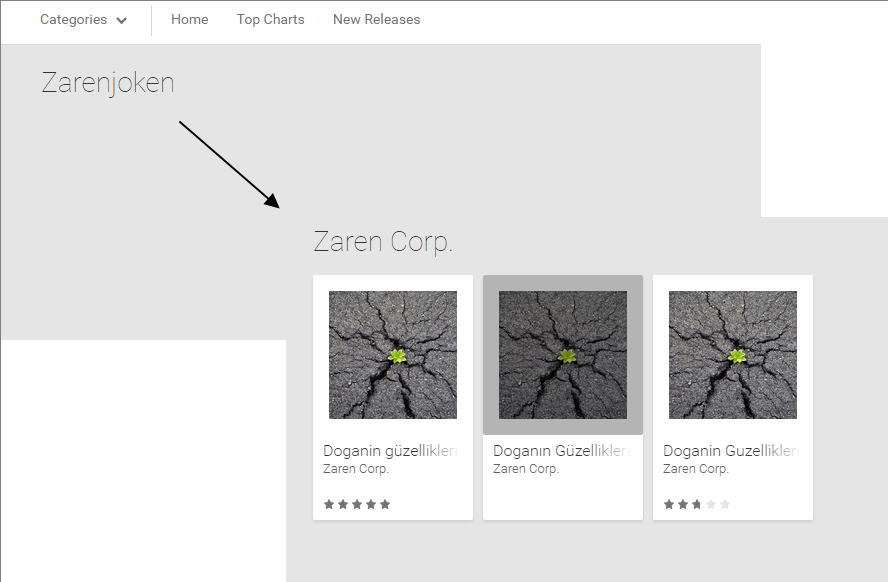
*It seems as though “Zaren” may be sensing we are all onto him and has therefore changed his developer account name…
![]()
Researchers unveil super-fast anonymity network
A group of six academics have published a paper describing a new high speed anonymity network that could increase the privacy of internet users everywhere.
The post Researchers unveil super-fast anonymity network appeared first on We Live Security.
![]()
CVE-2015-4235 (application_policy_infrastructure_controller_(apic), nx-os)
Cisco Application Policy Infrastructure Controller (APIC) devices with software before 1.0(3o) and 1.1 before 1.1(1j) and Nexus 9000 ACI devices with software before 11.0(4o) and 11.x before 11.1(1j) do not properly restrict access to the APIC filesystem, which allows remote authenticated users to obtain root privileges via unspecified use of the APIC cluster-management configuration feature, aka Bug IDs CSCuu72094 and CSCuv11991.
CVE-2015-4262 (unified_meetingplace_web_conferencing)
The password-change feature in Cisco Unified MeetingPlace Web Conferencing 8.5 before 8.5(5) MR3 and 8.6 before 8.6(2) does not check the session ID or require entry of the current password, which allows remote attackers to reset arbitrary passwords via a crafted HTTP request, aka Bug ID CSCuu51839.
Drones And Spyware: The Bizarre Tale Of A Brutal Kidnapping
McAfee Claims Ashley Madison Hack Could Destabilize Society
Chris Valasek On Car Hacking
Three Estonians Jailed For Malware Spree That Infected 4 Million
Bugtraq: [SECURITY] [DSA 3314-1] typo3-src end of life
[SECURITY] [DSA 3314-1] typo3-src end of life