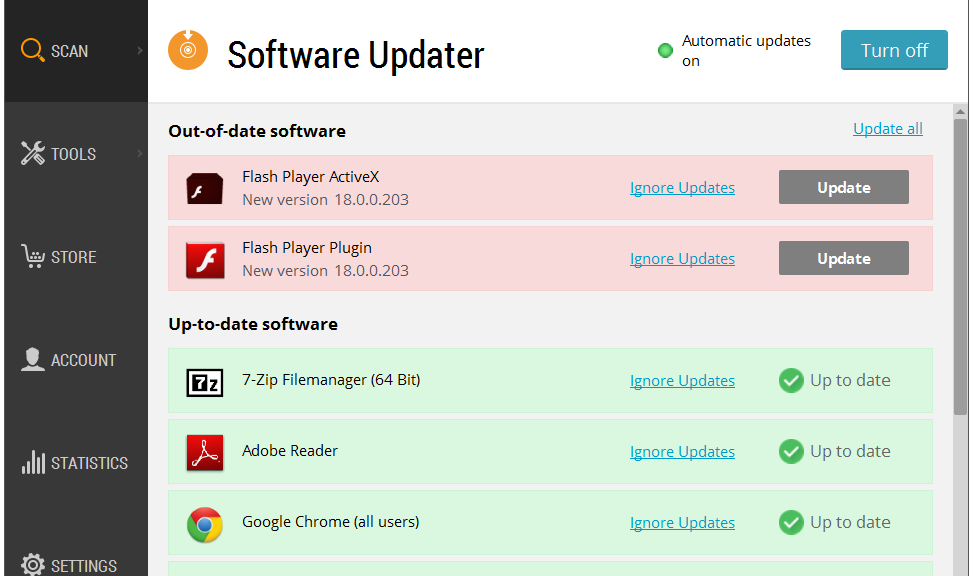
Avast Software Updater helps you apply software updates.
Earlier this week, we told our readers about the three Flash Player zero-day vulnerabilities that were found in stolen files that were leaked from the Hacking Team. We advised Avast users to disable Flash until the bugs are fixed.
It doesn’t look good for Flash. Because of the continuing security problems facing the 20-year old platform, Google and Mozilla each announced this week that their Web browsers will eventually be dropping default support for Adobe Flash, and Facebook’s new security chief wants to kill Flash. For now you can still use it, but the reports of it’s death are not greatly exaggerated…
Adobe has released security patches for Windows, Mac OS X, and Linux. Adobe Flash Player installed with Google Chrome will be automatically updated to the latest Google Chrome version. Users of Internet Explorer 10 and 11 for Windows 8.x will be automatically updated to the latest version.
Another Hacking Team zero-day vulnerability was discovered in Microsoft’s Internet Explorer. Microsoft released a total of 14 security bulletins, 4 ‘critical’ and the remainder ‘important’ in their July Security Bulletin.
And finally, Oracle released a security update to fix the Java zero-day exploit reportedly used to attack military and defense contractors from the U.S. and spy on NATO members. The Critical Patch Update Advisory also includes 193 new security updates; 99 of which could be exploited by remote attackers.
Avast Software Updater can help you with most software updates. To find it, open your Avast user interface. Click Scan on the left side, then choose Scan for outdated software. You an then decide how to proceed.
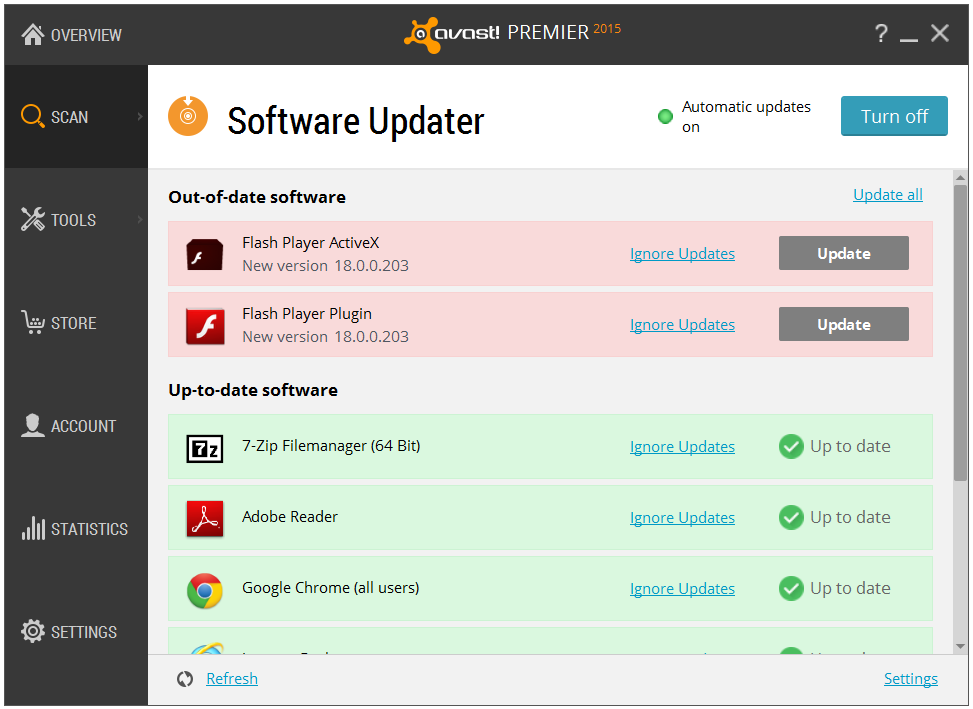
Avast Software Updater shows you an overview of all your outdated software applications
Follow Avast on Facebook, Twitter, YouTube, and Google+ where we keep you updated on cybersecurity news every day.
![]()