MediaWiki before 1.23.11, 1.24.x before 1.24.4, and 1.25.x before 1.25.3 does not throttle file uploads, which allows remote authenticated users to have unspecified impact via multiple file uploads.
Monthly Archives: November 2015
CVE-2015-8004
MediaWiki before 1.23.11, 1.24.x before 1.24.4, and 1.25.x before 1.25.3 does not properly restrict access to revisions, which allows remote authenticated users with the viewsuppressed user right to remove revision suppressions via a crafted revisiondelete action, which returns a valid a change form.
CVE-2015-8005
MediaWiki before 1.23.11, 1.24.x before 1.24.4, and 1.25.x before 1.25.3 uses the thumbnail ImageMagick command line argument, which allows remote attackers to obtain the installation path by reading the metadata of a PNG thumbnail file.
CVE-2015-8007
The Echo extension for MediWiki does not properly implement the hideuser functionality, which allows remote authenticated users to see hidden usernames in “non-revision based” notifications, as demonstrated by viewing a hidden username in a Thanks notification.
CVE-2015-8006
Cross-site scripting (XSS) vulnerability in the PageTriage toolbar in the PageTriage extension for MediWiki allows remote attackers to inject arbitrary web script or HTML via the page title.
‘Secret Sister’ gift exchange is a scam
Tis’ the season for scams to circulate on Facebook and other social sites.
It sounds like great fun! Join your friends for a “Secret Santa” type gift exchange, and invite lots of others to the party. Only problem is that it’s a hoax.

Don’t wait by your mailbox for gifts from this exchange
Watch out if you get a message on your Facebook Newsfeed (also spotted on Reddit) inviting you to join a ‘Secret Sister’ gift exchange. And don’t pass it on, either. It’s a scam, it’s against Facebook’s Terms of Service for sharing personal information, and it could very well be illegal.
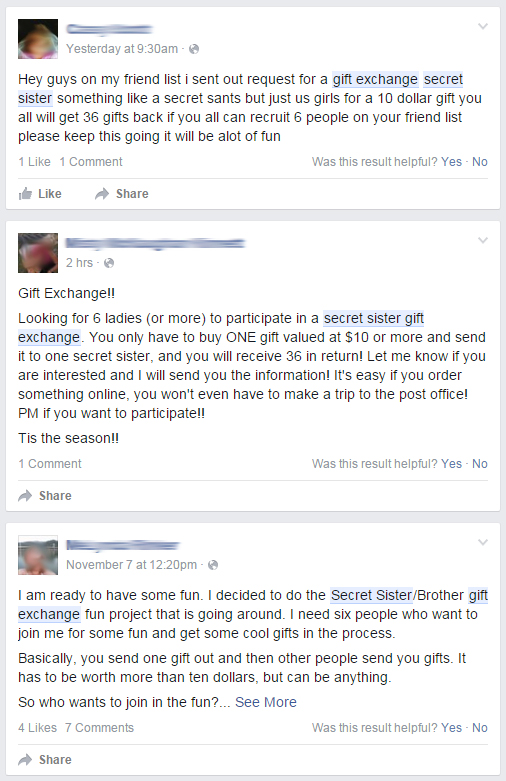
Recent messages shared on Facebook
The invitation describes the way it works; you send one present valued at $10 or more to one person and list six other women’s names to continue the process. You are promised to receive up to 36 gifts in return. Sounds fun and lots of women are falling for it. The messages above were sent this weekend, and one of them only 2 hours ago!
What this gift exchange really looks like is a social media version of the old Chain Letter people used to get in their mail boxes. It’s also known as a Pyramid or Ponzi scheme. The recipient of a chain letter was instructed to copy the letter and send it to a bunch of their friends in order not to “break the chain”.
The United States Postal Inspection Service (USPIS) describes a chain letter as “a get-rich-quick scheme that promises that your mailbox will soon be stuffed full of cash if you decide to participate.”
A typical chain letter includes names and addresses of several individuals whom you may or may not know. You are instructed to send a certain amount of money–usually $5–to the person at the top of the list, and then eliminate that name and add yours to the bottom. You are then instructed to mail copies of the letter to a few more individuals who will hopefully repeat the entire process. The letter promises that if they follow the same procedure, your name will gradually move to the top of the list and you’ll receive money — lots of it.
If you don’t think about it too carefully, it sounds like it could work. The problem is that it doesn’t work, and it’s illegal. USPIS says,
They’re illegal if they request money or other items of value and promise a substantial return to the participants. Chain letters are a form of gambling, and sending them through the mail (or delivering them in person or by computer, but mailing money to participate) violates Title 18, United States Code, Section 1302, the Postal Lottery Statute.
Why do people fall for these scams?
When you receive a message over and over again by friends that you have learned to trust, you automatically think that the information they share is trustworthy. Because these scams exist (read about The Tiffany & Co scam), it’s better to stop and think about it, even do a quick search for the topic, so you don’t become a victim,too.
If you receive a message like this, do not participate in it. You may also want to inform the sender of the scam by sharing this blog with them.
Follow Avast on Facebook, Twitter, YouTube, and Google+ where we keep you updated on cybersecurity news every day.
![]()
ProtonMail Back Online Following Six-Day DDoS Attack
Encrypted email service ProtonMail is back online Monday following a crippling six-day DDoS attack.
SAP HANA SQL Login Remote Code Execution
Sending a crafted packet to the SAP HANA SQL interface, a remote unauthenticated attacker could fully compromise the platform executing arbitrary code or performing a denial of service rendering the platform unavailable until the next process restart. SAP HANA DB version 1.00.73.00.389160 is affected.
SAP HANA HTTP Login Remote Code Execution
By sending a crafted HTTP packet to the SAP HANA XS Server, a remote unauthenticated attacker could fully compromise the platform executing arbitrary code or performing a denial of service, thus rendering the platform unavailable until the next process restart. SAP HANA DB version 1.00.73.00.389160 is affected.
WordPress Ajax Load More PHP Upload
This Metasploit module exploits an arbitrary file upload in the WordPress Ajax Load More version 2.8.1.1. It allows you to upload arbitrary php files and get remote code execution. This Metasploit module has been tested successfully on WordPress Ajax Load More 2.8.0 with WordPress 4.1.3 on Ubuntu 12.04/14.04 Server.