Monthly Archives: December 2015
Whisper This, But Java Deserialization Vulnerability Affects More Libraries
Variety Jones, Alleged Silk Road Mentor, Arrested In Thailand
France Looking At Banning Tor, Blocking Public Wi-Fi
Hacker Buba releases data belonging to customers of a UAE bank
Hacker Buba has released tens of thousands of records belonging to Invest Bank customers online.
The post Hacker Buba releases data belonging to customers of a UAE bank appeared first on We Live Security.
![]()
Avira Security Experts Visit University
A day’s work is never quiet done, when you are working on behalf of IT-Security.
The post Avira Security Experts Visit University appeared first on Avira Blog.
CESA-2015:2549 Moderate CentOS 6 libxml2 SecurityUpdate
CentOS Errata and Security Advisory 2015:2549 Moderate Upstream details at : https://rhn.redhat.com/errata/RHSA-2015-2549.html The following updated files have been uploaded and are currently syncing to the mirrors: ( sha256sum Filename ) i386: ef6fc5b110883e8b85e6e0aadb0dece190506569ba1c25247b612ffee5e10e7c libxml2-2.7.6-20.el6_7.1.i686.rpm 02e4ba1fea746762064a0fc7ba37d9fa1626cefd43257360db633fb23007c1d7 libxml2-devel-2.7.6-20.el6_7.1.i686.rpm d45068dcb62936bfd95e45182c807339dc060963d97adeae4d7717943a0107df libxml2-python-2.7.6-20.el6_7.1.i686.rpm 3c14ee97b4f56ede803f59fcdadb4786e3e4ab6792d68e7b509e7a346973b363 libxml2-static-2.7.6-20.el6_7.1.i686.rpm x86_64: ef6fc5b110883e8b85e6e0aadb0dece190506569ba1c25247b612ffee5e10e7c libxml2-2.7.6-20.el6_7.1.i686.rpm 6c42e07b5804dc8c346d5fa29755a515e8338618fc2b228959e4449e0d7b3227 libxml2-2.7.6-20.el6_7.1.x86_64.rpm 02e4ba1fea746762064a0fc7ba37d9fa1626cefd43257360db633fb23007c1d7 libxml2-devel-2.7.6-20.el6_7.1.i686.rpm 46fa4d9f942837bb4dc48907578ed4e12ca6a830b61719c649ff2b7ac5292bbf libxml2-devel-2.7.6-20.el6_7.1.x86_64.rpm 248032ec39a9aa0964763fa824604bc696dc54b59adaaac6b9e7c54f76137518 libxml2-python-2.7.6-20.el6_7.1.x86_64.rpm 67315973b872c5fdfc8656df43af9d21bd9a881e4c20d1bff3f53db1def4022b libxml2-static-2.7.6-20.el6_7.1.x86_64.rpm Source: 647b02b23b0fc8a0cb8d0821279cb4600f130b3776e345e91dee342f8dfbbbb4 libxml2-2.7.6-20.el6_7.1.src.rpm
SB15-341: Vulnerability Summary for the Week of November 30, 2015
Original release date: December 07, 2015
The US-CERT Cyber Security Bulletin provides a summary of new vulnerabilities that have been recorded by the National Institute of Standards and Technology (NIST) National Vulnerability Database (NVD) in the past week. The NVD is sponsored by the Department of Homeland Security (DHS) National Cybersecurity and Communications Integration Center (NCCIC) / United States Computer Emergency Readiness Team (US-CERT). For modified or updated entries, please visit the NVD, which contains historical vulnerability information.
The vulnerabilities are based on the CVE vulnerability naming standard and are organized according to severity, determined by the Common Vulnerability Scoring System (CVSS) standard. The division of high, medium, and low severities correspond to the following scores:
-
High – Vulnerabilities will be labeled High severity if they have a CVSS base score of 7.0 – 10.0
-
Medium – Vulnerabilities will be labeled Medium severity if they have a CVSS base score of 4.0 – 6.9
-
Low – Vulnerabilities will be labeled Low severity if they have a CVSS base score of 0.0 – 3.9
Entries may include additional information provided by organizations and efforts sponsored by US-CERT. This information may include identifying information, values, definitions, and related links. Patch information is provided when available. Please note that some of the information in the bulletins is compiled from external, open source reports and is not a direct result of US-CERT analysis.
High Vulnerabilities
| Primary Vendor — Product |
Description | Published | CVSS Score | Source & Patch Info |
|---|---|---|---|---|
| cisco — ios_xe | Cisco IOS XE 15.4(3)S on ASR 1000 devices improperly loads software packages, which allows local users to bypass license restrictions and obtain certain root privileges by using the CLI to enter crafted filenames, aka Bug ID CSCuv93130. | 2015-12-02 | 7.2 | CVE-2015-6383 CISCO |
| cisco — ios | The publish-event event-manager feature in Cisco IOS 15.5(2)S and 15.5(3)S on Cloud Services Router 1000V devices allows local users to execute arbitrary commands with root privileges by leveraging administrative access to enter crafted environment variables, aka Bug ID CSCux14943. | 2015-12-01 | 7.2 | CVE-2015-6385 CISCO |
| cyrus — imap | The index_urlfetch function in index.c in Cyrus IMAP 2.3.x before 2.3.19, 2.4.x before 2.4.18, 2.5.x before 2.5.4 allows remote attackers to obtain sensitive information or possibly have unspecified other impact via vectors related to the urlfetch range, which triggers an out-of-bounds heap read. | 2015-12-03 | 7.5 | CVE-2015-8076 CONFIRM CONFIRM CONFIRM CONFIRM CONFIRM MLIST MLIST MLIST SUSE SUSE |
| cyrus — imap | Integer overflow in the index_urlfetch function in imap/index.c in Cyrus IMAP 2.3.19, 2.4.18, and 2.5.6 allows remote attackers to have unspecified impact via vectors related to urlfetch range checks and the start_octet variable. NOTE: this vulnerability exists because of an incomplete fix for CVE-2015-8076. | 2015-12-03 | 7.5 | CVE-2015-8077 MLIST CONFIRM CONFIRM MLIST MLIST SUSE |
| cyrus — imap | Integer overflow in the index_urlfetch function in imap/index.c in Cyrus IMAP 2.3.19, 2.4.18, and 2.5.6 allows remote attackers to have unspecified impact via vectors related to urlfetch range checks and the section_offset variable. NOTE: this vulnerability exists because of an incomplete fix for CVE-2015-8076. | 2015-12-03 | 7.5 | CVE-2015-8078 CONFIRM CONFIRM MLIST SUSE |
| debian — debian_linux | The Debian build procedure for the smokeping package in wheezy before 2.6.8-2+deb7u1 and jessie before 2.6.9-1+deb8u1 does not properly configure the way Apache httpd passes arguments to smokeping_cgi, which allows remote attackers to execute arbitrary code via crafted CGI arguments. | 2015-12-03 | 7.5 | CVE-2015-0859 DEBIAN |
| debian — dpkg | Off-by-one error in the extracthalf function in dpkg-deb/extract.c in the dpkg-deb component in Debian dpkg 1.16.x before 1.16.17 and 1.17.x before 1.17.26 allows remote attackers to execute arbitrary code via the archive magic version number in an “old-style” Debian binary package, which triggers a stack-based buffer overflow. | 2015-12-03 | 7.5 | CVE-2015-0860 CONFIRM MISC CONFIRM UBUNTU DEBIAN |
| mcafee — mcafee_enterprise_security_manager | McAfee Enterprise Security Manager (ESM), Enterprise Security Manager/Log Manager (ESMLM), and Enterprise Security Manager/Receiver (ESMREC) 9.3.x before 9.3.2MR19, 9.4.x before 9.4.2MR9, and 9.5.x before 9.5.0MR8, when configured to use Active Directory or LDAP authentication sources, allow remote attackers to bypass authentication by logging in with the username “NGCP|NGCP|NGCP;” and any password. | 2015-12-02 | 9.3 | CVE-2015-8024 CONFIRM MISC |
| pcre — perl_compatible_regular_expression_library | PCRE before 8.36 mishandles the /(((a2)|(a*)g<-1>))*/ pattern and related patterns with certain internal recursive back references, which allows remote attackers to cause a denial of service (segmentation fault) or possibly have unspecified other impact via a crafted regular expression, as demonstrated by a JavaScript RegExp object encountered by Konqueror. | 2015-12-01 | 7.5 | CVE-2015-2327 CONFIRM CONFIRM MLIST MISC CONFIRM |
| pcre — perl_compatible_regular_expression_library | PCRE before 8.36 mishandles the /((?(R)a|(?1)))+/ pattern and related patterns with certain recursion, which allows remote attackers to cause a denial of service (segmentation fault) or possibly have unspecified other impact via a crafted regular expression, as demonstrated by a JavaScript RegExp object encountered by Konqueror. | 2015-12-01 | 7.5 | CVE-2015-2328 CONFIRM CONFIRM MLIST MISC CONFIRM |
| pcre — perl_compatible_regular_expression_library | The pcre_exec function in pcre_exec.c in PCRE before 8.38 mishandles a // pattern with a 1 string, which allows remote attackers to cause a denial of service (heap-based buffer overflow) or possibly have unspecified other impact via a crafted regular expression, as demonstrated by a JavaScript RegExp object encountered by Konqueror. | 2015-12-01 | 7.5 | CVE-2015-8380 CONFIRM MISC MLIST CONFIRM |
| pcre — perl_compatible_regular_expression_library | The compile_regex function in pcre_compile.c in PCRE before 8.38 and pcre2_compile.c in PCRE2 before 10.2x mishandles the /(?J:(?|(:(?|(?’R’)(k’R’)|((?’R’)))H’Rk’Rf)|s(?’R’))))/ and /(?J:(?|(:(?|(?’R’)(z(?|(?’R’)(k’R’)|((?’R’)))k’R’)|((?’R’)))H’Ak’Rf)|s(?’R’)))/ patterns, and related patterns with certain group references, which allows remote attackers to cause a denial of service (heap-based buffer overflow) or possibly have unspecified other impact via a crafted regular expression, as demonstrated by a JavaScript RegExp object encountered by Konqueror. | 2015-12-01 | 7.5 | CVE-2015-8381 CONFIRM CONFIRM MLIST CONFIRM |
| pcre — perl_compatible_regular_expression_library | PCRE before 8.38 mishandles certain repeated conditional groups, which allows remote attackers to cause a denial of service (buffer overflow) or possibly have unspecified other impact via a crafted regular expression, as demonstrated by a JavaScript RegExp object encountered by Konqueror. | 2015-12-01 | 7.5 | CVE-2015-8383 MLIST CONFIRM |
| pcre — perl_compatible_regular_expression_library | PCRE before 8.38 mishandles the /(?J)(?’d'(?’d’g{d}))/ pattern and related patterns with certain recursive back references, which allows remote attackers to cause a denial of service (buffer overflow) or possibly have unspecified other impact via a crafted regular expression, as demonstrated by a JavaScript RegExp object encountered by Konqueror, a related issue to CVE-2015-8392 and CVE-2015-8395. | 2015-12-01 | 7.5 | CVE-2015-8384 MLIST CONFIRM |
| pcre — perl_compatible_regular_expression_library | PCRE before 8.38 mishandles the /(?|(k’Pm’)|(?’Pm’))/ pattern and related patterns with certain forward references, which allows remote attackers to cause a denial of service (buffer overflow) or possibly have unspecified other impact via a crafted regular expression, as demonstrated by a JavaScript RegExp object encountered by Konqueror. | 2015-12-01 | 7.5 | CVE-2015-8385 MLIST CONFIRM |
| pcre — perl_compatible_regular_expression_library | PCRE before 8.38 mishandles the interaction of lookbehind assertions and mutually recursive subpatterns, which allows remote attackers to cause a denial of service (buffer overflow) or possibly have unspecified other impact via a crafted regular expression, as demonstrated by a JavaScript RegExp object encountered by Konqueror. | 2015-12-01 | 7.5 | CVE-2015-8386 MLIST CONFIRM |
| pcre — perl_compatible_regular_expression_library | PCRE before 8.38 mishandles (?123) subroutine calls and related subroutine calls, which allows remote attackers to cause a denial of service (integer overflow) or possibly have unspecified other impact via a crafted regular expression, as demonstrated by a JavaScript RegExp object encountered by Konqueror. | 2015-12-01 | 7.5 | CVE-2015-8387 MLIST CONFIRM |
| pcre — perl_compatible_regular_expression_library | PCRE before 8.38 mishandles the /(?=di(?<=(?1))|(?=(.))))/ pattern and related patterns with an unmatched closing parenthesis, which allows remote attackers to cause a denial of service (buffer overflow) or possibly have unspecified other impact via a crafted regular expression, as demonstrated by a JavaScript RegExp object encountered by Konqueror. | 2015-12-01 | 7.5 | CVE-2015-8388 MLIST CONFIRM |
| pcre — perl_compatible_regular_expression_library | PCRE before 8.38 mishandles the /(?:|a|){100}x/ pattern and related patterns, which allows remote attackers to cause a denial of service (infinite recursion) or possibly have unspecified other impact via a crafted regular expression, as demonstrated by a JavaScript RegExp object encountered by Konqueror. | 2015-12-01 | 7.5 | CVE-2015-8389 MLIST CONFIRM |
| pcre — perl_compatible_regular_expression_library | PCRE before 8.38 mishandles the [: and \ substrings in character classes, which allows remote attackers to cause a denial of service (uninitialized memory read) or possibly have unspecified other impact via a crafted regular expression, as demonstrated by a JavaScript RegExp object encountered by Konqueror. | 2015-12-01 | 7.5 | CVE-2015-8390 MLIST CONFIRM |
| pcre — perl_compatible_regular_expression_library | The pcre_compile function in pcre_compile.c in PCRE before 8.38 mishandles certain [: nesting, which allows remote attackers to cause a denial of service (CPU consumption) or possibly have unspecified other impact via a crafted regular expression, as demonstrated by a JavaScript RegExp object encountered by Konqueror. | 2015-12-01 | 9.0 | CVE-2015-8391 MLIST CONFIRM |
| pcre — perl_compatible_regular_expression_library | PCRE before 8.38 mishandles certain instances of the (?| substring, which allows remote attackers to cause a denial of service (unintended recursion and buffer overflow) or possibly have unspecified other impact via a crafted regular expression, as demonstrated by a JavaScript RegExp object encountered by Konqueror, a related issue to CVE-2015-8384 and CVE-2015-8395. | 2015-12-01 | 7.5 | CVE-2015-8392 MLIST CONFIRM |
| pcre — perl_compatible_regular_expression_library | PCRE before 8.38 mishandles the (?(<digits>) and (?(R<digits>) conditions, which allows remote attackers to cause a denial of service (integer overflow) or possibly have unspecified other impact via a crafted regular expression, as demonstrated by a JavaScript RegExp object encountered by Konqueror. | 2015-12-01 | 7.5 | CVE-2015-8394 MLIST CONFIRM |
| pcre — perl_compatible_regular_expression_library | PCRE before 8.38 mishandles certain references, which allows remote attackers to cause a denial of service or possibly have unspecified other impact via a crafted regular expression, as demonstrated by a JavaScript RegExp object encountered by Konqueror, a related issue to CVE-2015-8384 and CVE-2015-8392. | 2015-12-01 | 7.5 | CVE-2015-8395 MLIST CONFIRM |
| siemens — simatic_cp_343-1_firmware | Siemens SIMATIC CP 343-1 Advanced devices before 3.0.44, CP 343-1 Lean devices, CP 343-1 devices, TIM 3V-IE devices, TIM 3V-IE Advanced devices, TIM 3V-IE DNP3 devices, TIM 4R-IE devices, TIM 4R-IE DNP3 devices, CP 443-1 devices, and CP 443-1 Advanced devices might allow remote attackers to obtain administrative access via a session on TCP port 102. | 2015-11-27 | 9.7 | CVE-2015-8214 CONFIRM |
Medium Vulnerabilities
| Primary Vendor — Product |
Description | Published | CVSS Score | Source & Patch Info |
|---|---|---|---|---|
| cisco — web_security_appliance | The passthrough FTP feature on Cisco Web Security Appliance (WSA) devices with software 8.0.7-142 and 8.5.1-021 allows remote attackers to cause a denial of service (CPU consumption) via FTP sessions in which the control connection is ended after data transfer, aka Bug ID CSCut94150. | 2015-12-01 | 5.0 | CVE-2015-6386 CISCO |
| cisco — unity_connection | Cross-site scripting (XSS) vulnerability in the management interface in Cisco Unity Connection 9.1(1.10) allows remote attackers to inject arbitrary web script or HTML via a crafted value in a URL, aka Bug ID CSCup92741. | 2015-12-02 | 4.3 | CVE-2015-6390 CISCO |
| pcre — perl_compatible_regular_expression_library | The match function in pcre_exec.c in PCRE before 8.37 mishandles the /(?:((abcd))|(((?:(?:(?:(?:abc|(?:abcdef))))b)abcdefghi)abc)|((*ACCEPT)))/ pattern and related patterns involving (*ACCEPT), which allows remote attackers to obtain sensitive information from process memory or cause a denial of service (partially initialized memory and application crash) via a crafted regular expression, as demonstrated by a JavaScript RegExp object encountered by Konqueror, aka ZDI-CAN-2547. | 2015-12-01 | 6.4 | CVE-2015-8382 CONFIRM CONFIRM MLIST MLIST CONFIRM CONFIRM CONFIRM |
| pcre — perl_compatible_regular_expression_library | pcregrep in PCRE before 8.38 mishandles the -q option for binary files, which might allow remote attackers to obtain sensitive information via a crafted file, as demonstrated by a CGI script that sends stdout data to a client. | 2015-12-01 | 5.0 | CVE-2015-8393 MLIST CONFIRM |
| redhat — ceph | CRLF injection vulnerability in the Ceph Object Gateway (aka radosgw or RGW) in Ceph before 0.94.4 allows remote attackers to inject arbitrary HTTP headers and conduct HTTP response splitting attacks via a crafted bucket name. | 2015-12-03 | 4.3 | CVE-2015-5245 REDHAT CONFIRM MLIST |
This product is provided subject to this Notification and this Privacy & Use policy.
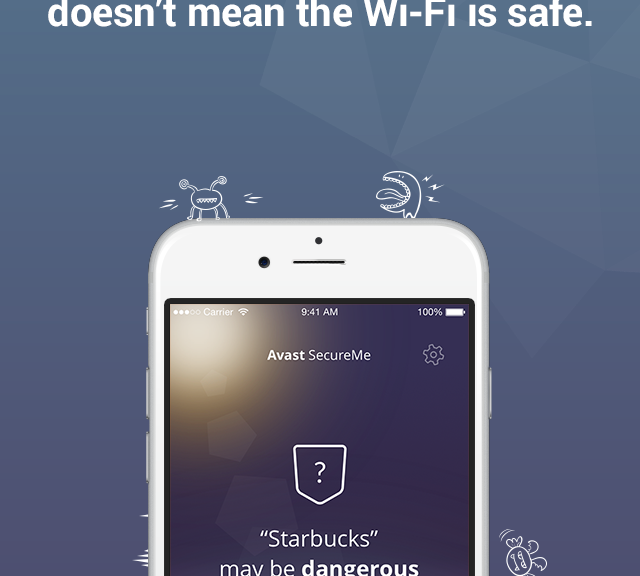
Avast SecureMe app protects iOS users from Wi-Fi hacking
Avast SecureMe is the world’s first application that gives iPhone users a tool to protect their devices and personal data when they connect to Wi-Fi networks. The free app scans Wi-Fi networks and tells users which of them are safe. Since many users use Wi-Fi networks without knowing whether or not they are safe, Avast SecureMe will create a secure connection in order to keep them safe.
The app notifies you upon the discovery of security issues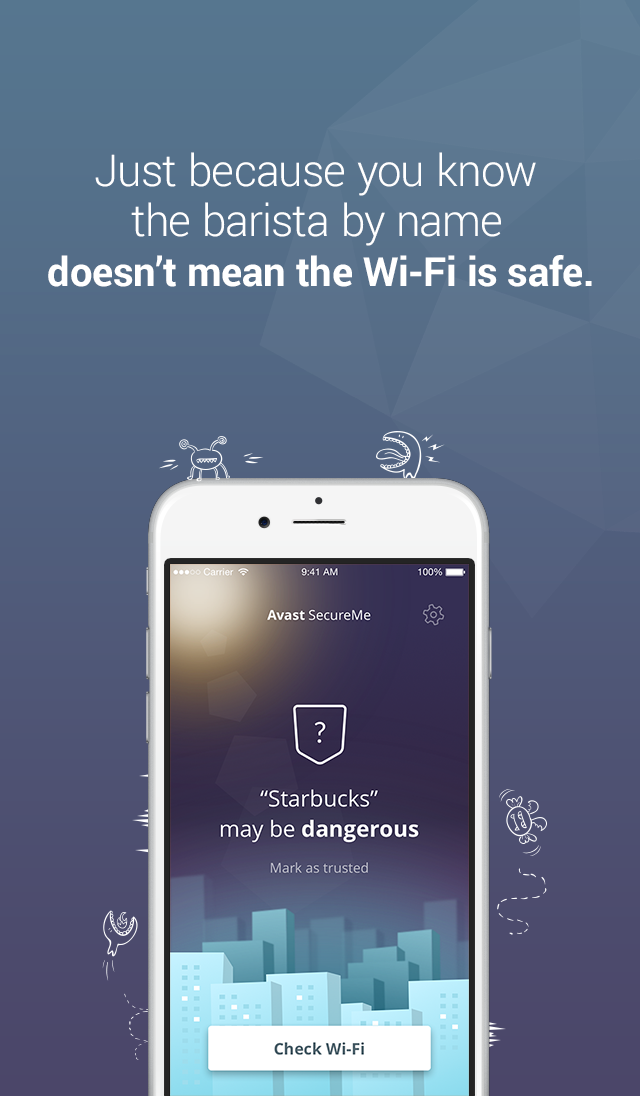
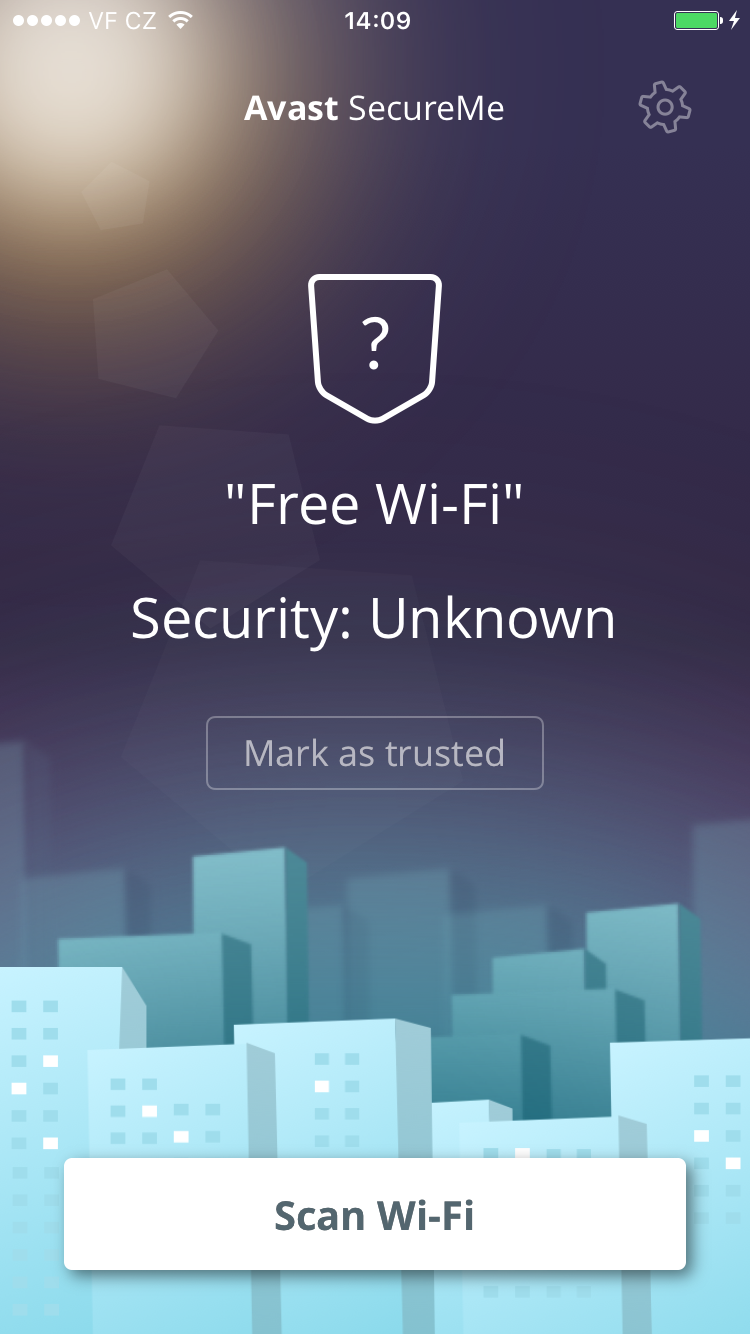
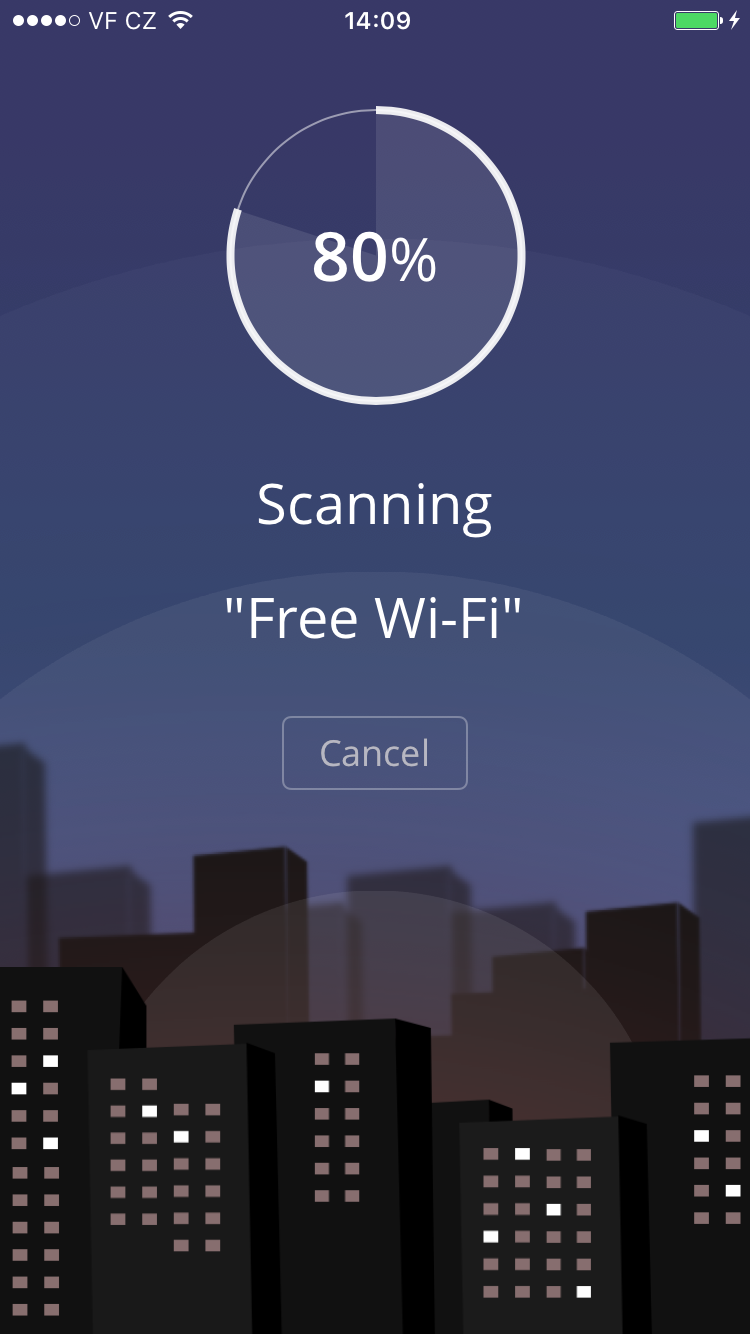
Avast SecureMe includes a feature called Wi-Fi Security. People who use open Wi-Fi in public areas such as airports, hotels, or cafes will find this helpful. This feature’s job is to scan Wi-Fi connections and notify you if any security issues are found, such as routers with weak passwords, unsecured wireless networks, and routers with vulnerabilities that could be exploited by hackers. Users have the option to label Wi-Fi networks that they frequently use as trusted — this way, the app won’t need to check the networks every time.
What’s the risk that my personal data will be stolen?
If you use unsecured Wi-Fi when you log in to a banking site, for example, cybercrooks can capture your login credentials which can lead to identity theft. On unprotected Wi-Fi networks, crooks can also easily view your emails, browsing history, and personal data if you don’t use a secure or encrypted connection like a virtual private network (VPN). For more details on this point, see our recent Wi-Fi hotspot experiment to see how widespread the threat really is.
Avast SecureMe is a simple way to find and choose safe networks.
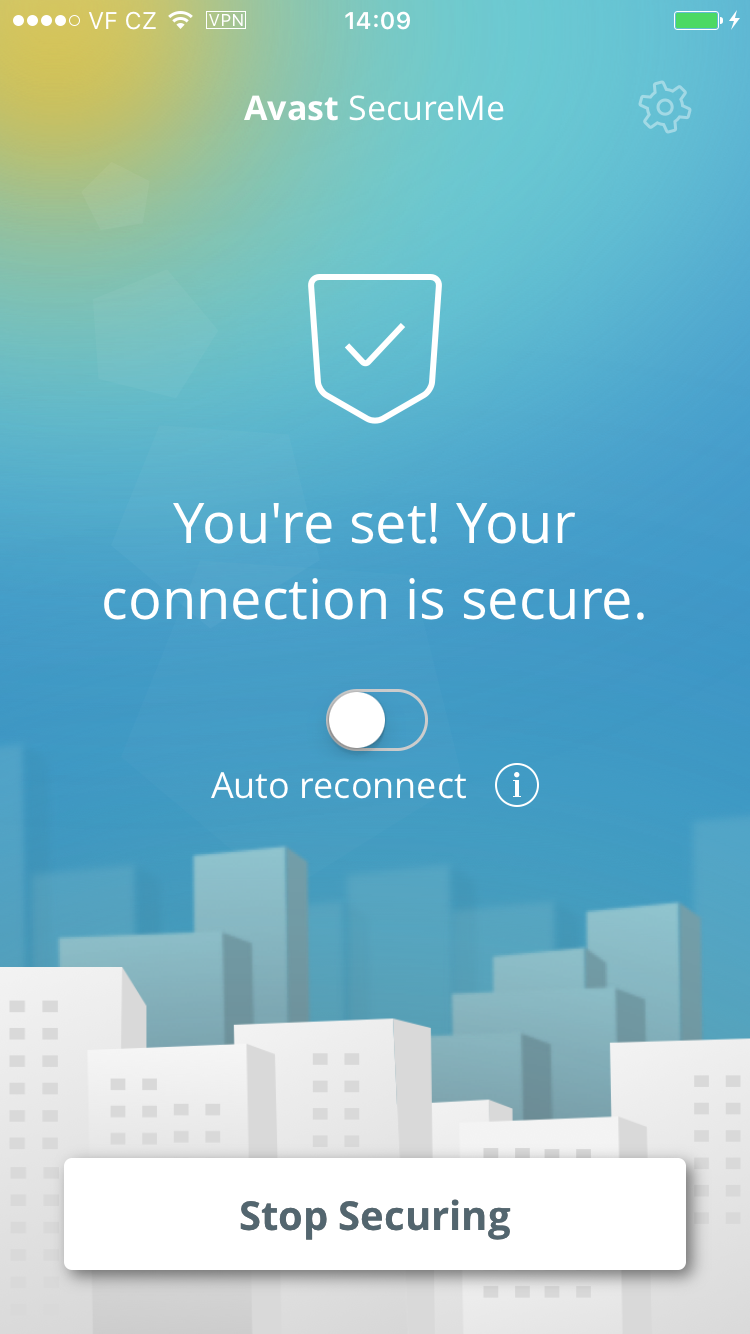
The Avast SecureMe app includes a VPN to protect your privacy
Avast SecureMe features a VPN to secure your connections while you conduct online tasks that you’d like to remain private. This could include checking emails, doing your online banking, and even visiting your favorite social network sites. Avast SecureMe connects to the secure VPN when it detects that you have connected to a public Wi-Fi network, making all transferred data invisible to prying eyes. For convenience, you can disable the protection for Wi-Fi connections you trust, such as your home network.
Try it for yourself! You can download Avast SecureMe free of charge on iTunes.
Follow Avast on Facebook, Twitter, YouTube, and Google+ where we keep you updated on cybersecurity news every day.
![]()
The security review: VM machines and security, online banking and VTech data breach
The last seven days in information security have been notable to say the least, with VTech experiencing a major data breach and Google being the subject of a complaint over data gathering practices. Read on for more on both these stories, as well as other highlights of the past week.
The post The security review: VM machines and security, online banking and VTech data breach appeared first on We Live Security.
![]()