Monthly Archives: December 2015
190GB Of Photos And Chat Logs Stolen In Vtech Breach
Adele Ticket Site Exposes Fan Data
FBI National Security Letter Details Revealed By Court
How many people connect to unknown Wi-Fi hotspots without even knowing?
An Avast team calling themselves the Security Warriors, comprised of intra-departmental specialists, are running experiments in the streets of San Francisco. They spent a few days setting up the first of them and have already gathered some interesting statistics. In Filip‘s words, here is what they have done so far and what they want to achieve.

Filip Chytrý , president of mobile Gagan Singh, Bára Štěpánová, Jaroslav Slaby, and Vladislav Iliushin. Not pictured: Ondrej David
One of our first experiment’s objectives is to analyze people’s behavior by seeing how they have their devices preset in terms of outside communication. We didn’t have to go far to find out – it’s pretty disturbing. Currently, we have a variety of devices prepared for different traffic experiments but now we are using them for one really easy target – to analyze how many people connect to a fake hotspot. We created fake Wi-Fi networks called Xfinity, Google Starbucks, and Starbucks. From what we’ve noticed, Starbucks is one of the most widespread networks here, so it’s pretty easy to get people’s devices to connect to ours.
Wi-Fi networks screen
What is the problem we’re trying to point out?
Once your device connects to a known SSID name at your favorite cafe, the next time you visit, it will automatically try to connect to a network with the same name. This common occurrence becomes a problem because it can be misused by a hacker. Armed with some basic information, a hacker can figure out what you are doing and even which device you have. It is just a matter of time to come up with the right technique to hack into your device. After a day of walking around with my tablet, we gathered some telling statistics.  From data we gathered in seven hours, we found that 264 people connected to our fake Wi-Fi networks and generated 512,000 data packets*.
From data we gathered in seven hours, we found that 264 people connected to our fake Wi-Fi networks and generated 512,000 data packets*.
- 52% connected from an Apple device
- 42% connected from an Android device
- 10% connected from a tablet or notebook
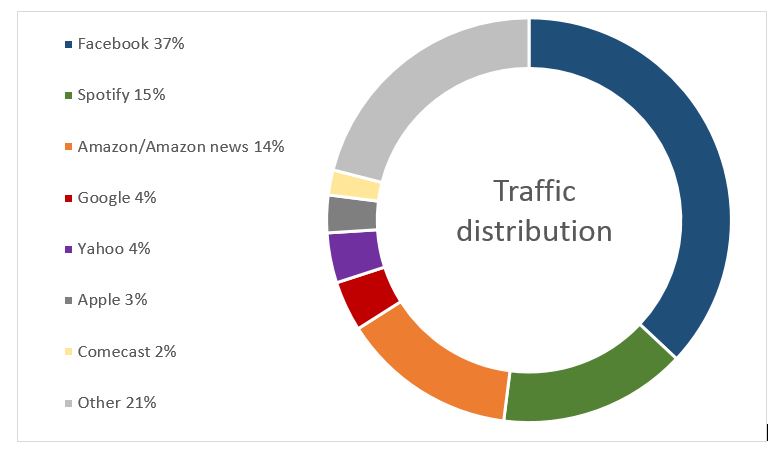
Percentage of traffic distribution generated from those devices
- 70% of them have the Facebook app installed
- 30% of them have the Twitter app installed
- 30% of them accessed a Google-related service
- 20% browsed a webpage
What is on our tablet?
The device used for this experiment is a pretty simple off-the-shelf Nexus 7 with a rooted LTE modem. We set up fake hotspots and used tools to catch TCP dumps. Later on, we analyzed who was doing what. Nothing hard at all. Our hotspots are movable, so I have one tablet with me at all times with a fake Wi-Fi network called Google Starbucks. If you see that hotspot somewhere in town, you might want to watch your device more carefully. ![]() Did I mention we did this using only a tablet? We do have a couple of other things up and running, but that‘s something for another blog.
Did I mention we did this using only a tablet? We do have a couple of other things up and running, but that‘s something for another blog.

Traffic flowing over the Golden Gate Bridge
If you want to be involved and aware of how these things work, you can catch up with us in San Francisco. Up until now, we have let the traffic flow as it should and gathered data, but next, we‘ll play a bit with redirection. ![]() *A packet is the unit of data that is routed between an origin and a destination on the Internet or any other packet-switched network.
*A packet is the unit of data that is routed between an origin and a destination on the Internet or any other packet-switched network.
Follow Avast on Facebook, Twitter, YouTube, and Google+ where we keep you updated on cybersecurity news every day.
![]()
VTech data breach: Your kid’s personel information is out there
If you are a parent you’re probably doing everything to protect your child. That’s the reason the latest trick Mattel pulled with their “Hello Barbie” dolls has not received the warmest of welcomes (at least here in Germany – but I’m sure elsewhere, too).
The post VTech data breach: Your kid’s personel information is out there appeared first on Avira Blog.
Consumers Admit to Using One Password for All Their Online Accounts, Kaspersky Lab Cyber Savvy Quiz Shows
Virtual machine security – offloading the endpoint
If many endpoints’ traffic pass through the VM host, why not move security there, sort of catch “bad things” before they even enter the endpoint, asks ESET’s Cameron Camp.
The post Virtual machine security – offloading the endpoint appeared first on We Live Security.
![]()
Demand grows across the world for cybersecurity experts

During the second quarter of 2015 there were 230,000 new malware samples created daily. This is one of the alarming details to emerge from the latest PandaLabs report, the security laboratory of Panda Security, which analyzes cyberattacks carried out during this period. The document also reveals that the threats aren’t just directed at individuals, but also at private businesses.
Some example include Ryanair, which suffered a loss of $5 million, or the online dating site AdultFriendFinder, which saw its users’ sensitive information published online.
Businesses are continually becoming more and more conscious of the danger posed by these attacks, both in economic terms and what it means for their customers. According to a survey carried out by PwC, budgeting for IT security, on a global level, has grown by 24% during the last year.

Businesses nowadays can count on a team of experienced and specialized security experts who can help to protect their networks and systems. However, the sheer scale, complexity, and amount of malware that is created by cybercriminals means that, in many cases, IT departments aren’t able to cope with the onslaught.
In the State of Cybersecurity 2015 report, experts from U-Tad analyze the threats that affect businesses, institutions, and individuals. They reflect that, although 37% of companies plan on employing more cybersecurity professionals, 92% of them claim to have problems finding candidates that meet the requirements.
These experts claim that there is a lack of specialized workers in this sector and estimate a shortfall of more than one million people on a global level.

From a business point of view, this information is an opportunity in the cybersecurity market, which will grow from $106 million in 2015 to over $170 million in 2020, according to MarketsandMarkets.
As the U-Tad experts indicate, the sectors most interested in safeguarding their systems against threats are banking, aerospace, and the manufacturing industry. SMEs also need professionals, especially those involved in cloud based storage solutions.
The survey done by U-Tad also reveals another significant statistic – 75% of the organizations surveyed are believed to be exposed to the risked related to the actions of their own employees. Practices such as BYOD (Bring Your Own Device), whose risks we’ve already explained to you, are responsible for this.
In Spain, for example, the National Cybersecurity Institute estimates that there are more than 42,000 professionals working in the IT security sector, and that the demand for workers continues to grow. The organization even offers grants to students, because the only way to cover the demand for professionals is to create specialists that can tackle the goals of the present and future.
The post Demand grows across the world for cybersecurity experts appeared first on MediaCenter Panda Security.
CVE-2015-6385 (ios)
The publish-event event-manager feature in Cisco IOS 15.5(2)S and 15.5(3)S on Cloud Services Router 1000V devices allows local users to execute arbitrary commands with root privileges by leveraging administrative access to enter crafted environment variables, aka Bug ID CSCux14943.
