KeePass Password Safe Classic version 1.29 suffers from a denial of service vulnerability.
Monthly Archives: January 2016
How Google hopes to revolutionize the way we access our accounts

Google is about to put another nail in the coffin for traditional passwords. The search engine giant is testing out a new system of passwords that will take the place of the usual combination of letters, numbers, and symbols that we use to access services on our mobile phone.
At the moment, the new authentication method is only available for a select group of users, although the company has confirmed it will extend it to other users within the near future. Notorious passwords such as pizza, password, and 123456 will soon be confined to the past, joked a Google spokesperson at the announcement.
How the new system works is rather easy. Whenever we want to access our Google account – which is becoming more and more central to our lives – we will only have to enter our user name or email address.
By doing this, a notification will appear on our mobile phone, which is linked to the account, asking if we are trying to access from a different computer. By confirming this, we can access without any issues.
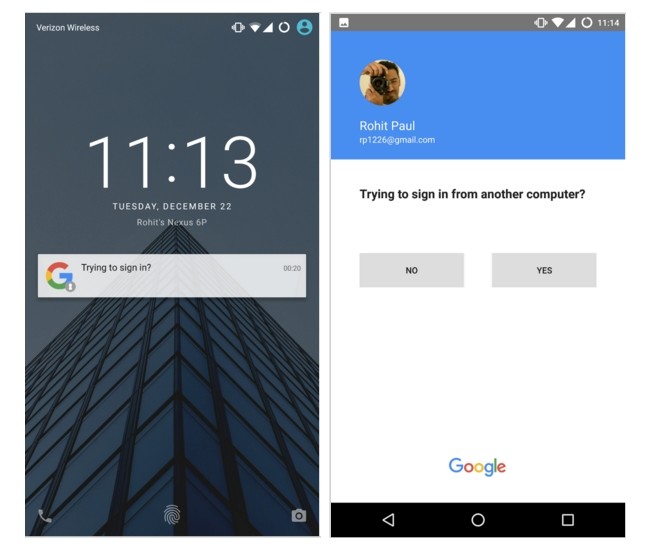
The main advantage of this method is that it is extremely simple. With just one click of the smartphone’s screen it is possible to by-pass the process of entering a password or, in some cases, going through a two-step verification process.
What’s more, this new method should allow us to feel more protected when it comes to other people gaining access to our private accounts, as some people continue to use basic and easy to guess passwords, which do little to ward off cybercriminals.
It’s not all doom and gloom for passwords, however, as they can still be used alongside the new method and will come in handy should you run out of battery on your mobile phone. The new identification procedure can still be used alongside the current two-step process, too.
In the event of losing the mobile phone, or having it stolen, your account won’t be at risk for long. You can long-in from another device (your laptop, for example) and from there remove the access permission for the mobile phone.
With this initiative, Google joins a list of multinational companies that are looking for alternatives to traditional passwords. Recently, Yahoo created its own system called Key Account, which has a lot in common with the system being trialed by Google. Whether we like it or not, traditional passwords may soon be confined to the annals of history.
The post How Google hopes to revolutionize the way we access our accounts appeared first on MediaCenter Panda Security.
CVE-2015-7115
libxml2 in Apple iOS before 9.2, OS X before 10.11.2, and tvOS before 9.1 allows remote attackers to obtain sensitive information or cause a denial of service (memory corruption) via a crafted XML document, a different vulnerability than CVE-2015-7116.
CVE-2015-7116
libxml2 in Apple iOS before 9.2, OS X before 10.11.2, and tvOS before 9.1 allows remote attackers to obtain sensitive information or cause a denial of service (memory corruption) via a crafted XML document, a different vulnerability than CVE-2015-7115.
CVE-2015-7397
Multiple open redirect vulnerabilities in the Aurora starter store in IBM WebSphere Commerce 7.0 through Feature Pack 8 allow remote attackers to redirect users to arbitrary web sites and conduct phishing attacks via a URL in the referrer parameter.
CVE-2015-7465
Cross-site request forgery (CSRF) vulnerability in Lifecycle Query Engine (LQE) in IBM Jazz Reporting Service (JRS) 6.0 before 6.0.0-Rational-CLM-ifix005 allows remote authenticated users to hijack the authentication of arbitrary users for requests that insert XSS sequences.
CVE-2015-7466
Lifecycle Query Engine (LQE) in IBM Jazz Reporting Service (JRS) 6.0 before 6.0.0-Rational-CLM-ifix005 allows remote authenticated users to conduct LDAP injection attacks, and consequently bypass intended query restrictions or modify the LDAP directory, via unspecified vectors.
DSA-3439 prosody – security update
Two vulnerabilities were discovered in Prosody, a lightweight
Jabber/XMPP server. The Common Vulnerabilities and Exposures project
identifies the following issues:
