Zimbra Cross-Site Scripting vulnerabilities
Monthly Archives: February 2016
Bugtraq: RE: CVE-2016-0729: Apache Xerces-C XML Parser Crashes on Malformed Input
RE: CVE-2016-0729: Apache Xerces-C XML Parser Crashes on Malformed Input
RHSA-2016:0297-1: Low: Red Hat CloudForms 3.0 – End Of Life Notice
This is the 12 Month notification for the End of Production Phase 2 of
Red Hat CloudForms 3.0.
RHBA-2016:0299-1: kernel bug fix update
Red Hat Enterprise Linux: Updated kernel packages that fix one bug are now available for Red Hat
Enterprise Linux 6.4 Advanced Update Support.
RHBA-2016:0298-1: findutils bug fix update
Red Hat Enterprise Linux: Updated findutils packages that fix one bug are now available for Red Hat
Enterprise Linux 7.
Why we should pay more attention to our Download folder

How many files have you got resting in your computer’s download folder? It’s normal that it gets filled with installation apps form all the different programs that we download from the Internet and then forget to delete. Although this seems harmless at first, what is certain is that it could lead to some serious problems for your computer.
A recently detected vulnerability in the Java installation program, a platform that many applications and websites need to function correctly, has put this seemingly innocuous area at risk.
The Java software needs to update itself periodically with new versions so as to be able to maintain the performance and security of the tools that it helps to run.
Its distributor, Oracle, has warned of a security issue that affects the installation programs of the platform’s 6, 7, and 8 versions. The company has therefore advised its users to delete these programs from the download folder and replace them with new ones if necessary.
The reason given is that the installation software is designed to automatically search and load a set of files that are included in the installation pack (including its own .exe file) and to the store them in the same folder.
This procedure, which all installation programs carries out, shouldn’t pose a risk to your computer, as the majority of folders where they are stored aren’t vulnerable to attack. However, the “Downloads” directory is able to be modified.
If a cybercriminal manages to add this type of file (named Dynamic Link Library, or DLL), charged with malware, to the folder, the installation program will run it when the user wants to install Java for the first time, or if they manually update the tool by downloading a new installation program.
An added risk is that many browsers are set up to automatically download certain files, even if they don’t run later. Via an infected website, the attacker could use this feature to hide malware in the download folder without the user knowing about it. The files with malicious software would then be read to be executed by the installation program.
Deleting your browsing history would only help to eliminate the websites that you’ve visited, but not the programs that are already stored. Therefore, it is recommended that you delete the documents and software from your download folder every so often.
“Though considered relatively complex to exploit, this vulnerability may result, if successfully exploited, in a complete compromise of the unsuspecting user’s system”, says Eric Maurice, Head of IT Security at Oracle.
The post Why we should pay more attention to our Download folder appeared first on MediaCenter Panda Security.
GIMP For Windows DLL Hijacking
GIMP for Windows suffers from a dll hijacking vulnerability.
What happens to your Facebook account when you pass away?
We leave a huge digital footprint on Facebook. Did you ever think about what will happen with your data when you pass away?
The social giant Facebook has existed long enough to realize that it is part of a human’s life events. We announce the most important milestones on our timelines by sharing with our Facebook friends the joy of getting married, having babies, or moving abroad. But what will happen with all that data when we pass away? Discussing your digital legacy isn’t pleasant, but it’s important is our reality. Don’t leave it up to your family member, friends, or even worse: Facebook itself. In this article I will guide you through all the options you have, so you can make a conscious decision about your data, using the tools that Facebook offers to its users.
Decide what to do with your data!
In short you have two options: To delete your account or agree to memorialize your person within the social network. In case you decide on the second option, it is recommended to set up a Legacy Contact: A person who will take care of your account, if something happens to you.
Delete your account
Deleting an account is the easier and more radical option. All your data – pictures, posts, comments, connections, messages, apps you have ever installed – simply everything, will be permanently removed.
Here are the steps you have to take first, to set this option in your profile:
- From the top right of Facebook, click and select Settings
- From the left menu, click Security
- Click Legacy Contact
- Click have your account permanently deleted and follow the on-screen instructions.
This is however only an initial step to remove your account. If something happens to you, Facebook still needs to be notified. Your immediate family member needs to contact Facebook to inform about the lose. There is a Special Request for Deceased Person’s Account where all the information, including a death certificate needs to be sent. Only after that will Facebook permanently remove the profile.
Setting up a Legacy Contact
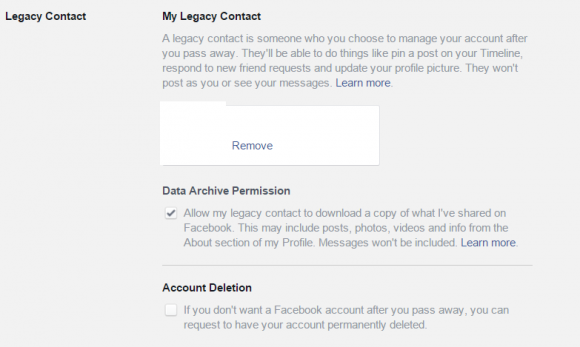
A Legacy Contact is a trusted person, a friend or a family member, that will make sure your profile is memorialized and that will take care of it afterwards. According to Facebook, the Legacy Contact will be able to:
- Write a post to display at the top of the memorialized Timeline (for example, to announce a memorial service or share a special message)
- Respond to new friend requests from family members and friends who were not yet connected on Facebook
- Update the profile picture and cover photo
- Archive your data (Only if you check this option in the settings): Photos and videos you uploaded, wall posts, profile and contact info, events, and friends list. The following data can’t be downloaded: Messages, ads you clicked, pokes, security and settings info, photos you automatically synced but didn’t post.
How to set up a Legacy Contact?
Select the person first and talk about it in advance. You can always change your selection and chose another person, but it is always better to discuss this responsibility in person ahead. It is also important to educate your Legacy Contact what to do.
Here is how to add a legacy contact:
- Click in the top right of Facebook and select Settings
- In the left menu, click Security
- Click Legacy Contact
- Type in a friend’s name and click Add
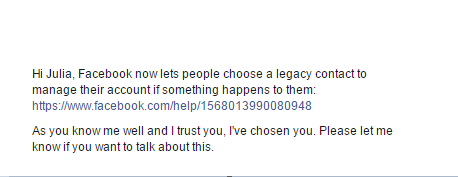
- To let your friend know they’re now your legacy contact, click Send
- Your friend will be notified with the following message
What to do, if you are appointed to be a Legacy Contact?
Respecting your deceased friend or family member is a responsibility. The first thing you will have to do is request memorialization of the profile. Once it is set up as a memorial, the profile will receive the “Remembering” label just above the name, next to the deceased person’s profile picture. Memorialized profiles don’t appear in public spaces such as in suggestions for People You May Know, ads, or birthday reminders. As a Legacy Contact you can manage a profile in a limited way. To do it you have to go to the profile, in the bottom right of the cover photo click Manage and than you can:
- Add a pinned post to announce to the circle of the friends what has happened
- Respond to new friend requests
- Change the profile picture and cover photo
Please visit our blog often for more updates on security and privacy on Social Media.
Follow Avast on Facebook, Twitter, YouTube, and Google+ where we keep you updated on cybersecurity news every day.
![]()
CVE-2016-1297
The Device Manager GUI in Cisco Application Control Engine (ACE) 4710 A5 before A5(3.1) allows remote authenticated users to bypass intended RBAC restrictions and execute arbitrary CLI commands with admin privileges via an unspecified parameter in a POST request, aka Bug ID CSCul84801.
CVE-2016-1342
The device login page in Cisco FirePOWER Management Center 5.3 through 6.0.0.1 allows remote attackers to obtain potentially sensitive software-version information by reading help files, aka Bug ID CSCuy36654.