Also Read: Microsoft Drops a Cloud Data Center Under the Ocean.
Why a Linux Subsystem?
Isn’t this exciting?
![]()
Also Read: Microsoft Drops a Cloud Data Center Under the Ocean.
Isn’t this exciting?
![]()
WordPress’ latest version, 4.4.2, fixes a handful of bugs and vulnerabilities in the content management system.
Ormandy notes that “all shortcuts are replaced with Chromodo links and all settings, cookies, etc are imported from Chrome. They also hijack DNS settings, among other shady practices.”
To understand this, assume you are logged into Facebook and somehow visits a malicious website in another tab.
![]()

When one works in a power plant, a water treatment facility, a gas plant, a recycling center, or any other critical infrastructure for a country, it’s essential to be extra careful about what you post on social media.
It might seem to be common sense, but IT security experts have raised worries over the amount of selfies taken by employees in these centers, which have started to appear across different sites such as Facebook, Twitter, and Instagram.
With the recent blackout which affected more than 80,000 people in Ukraine still fresh in the memory, the proliferation of selfies that could reveal security secrets in these installations could become a problem that needs to be stamped out immediately.
IT systems that could be compromised as a result of worker indiscretion are named SCADA – the initials are taken from Supervision, Control and Acquisition of Data – and they are continually used to manage all types of industrial processes, which means that their security is extremely important.
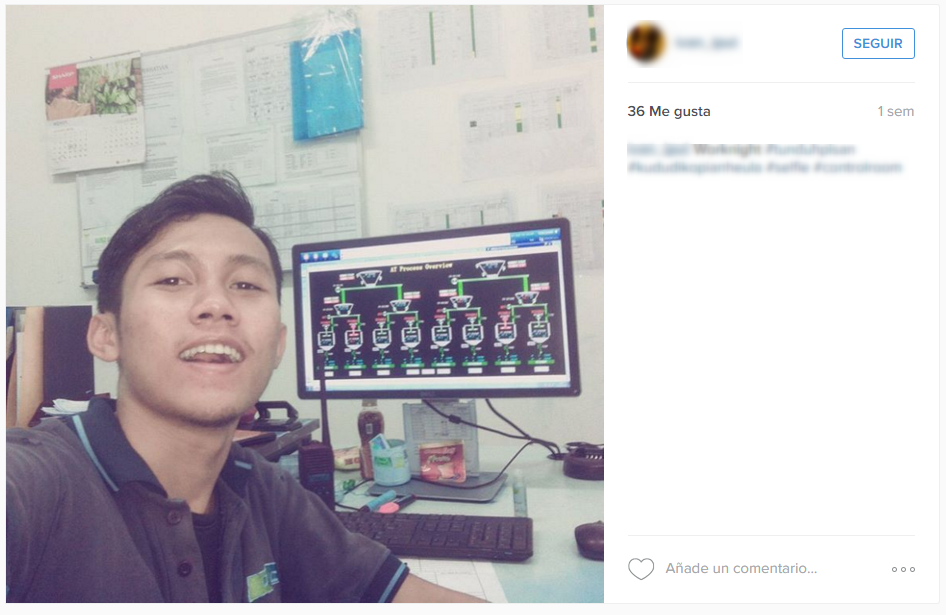
They allow you to obtain information from anywhere, in real-time, about the automated operations in a factory (or a gas station, for example), in such a way that the decision making and remote management of these installations is easy and economically sensible.
On the other hand, however, if a cybercriminal manages to enter the systems, especially if he manages to take control or alter the function of the machines, it could result in unrepairable damage.
Businesses, governments, and professionals from the sector are growing more and more aware of the risk that these infrastructures are exposed to. This is usually because they fear that the weakest link in the chain, which is always a person, could commit a silly mistake with their smartphone.
Just as has been discussed dedicated forums, IT security experts in the industrial sector have been able to locate these selfies, and other things, on Facebook and Instagram in which it is possible to see valuable information on the SCADA systems.
Furthermore, they have also discovered panoramic photos and virtual tours of the control rooms and the critical infrastructures, which are available for anyone to view, on the companies’ websites. This could allow someone with malicious intentions to extract information relating to employees, shift patterns, etc.
In fact, the German security expert Ralph Langner discovered that an image of the Natanz nuclear plant in Iran, distributed by president Ahmadinejad’s own press office, had been used by the creators of Stuxnet malware to attack the country’s nuclear program.
The image, which was happily shared by the Islamic regime, showed a control monitor for the SCADA system that was controlling its new uranium centrifuges. A real treat for their western enemies!
The post Employees’ selfies and the dangers of cybercrime for critical infrastructures appeared first on MediaCenter Panda Security.
The jpeg2000_decode_tile function in libavcodec/jpeg2000dec.c in FFmpeg before 2.8.6 allows remote attackers to cause a denial of service (out-of-bounds array read access) via crafted JPEG 2000 data.
Equibase.com suffers from an html injection vulnerability that may allow for cross site scripting.