Monthly Archives: February 2016
Bill Gates Saddened No One Is Asking For Windows Phone Backdoor
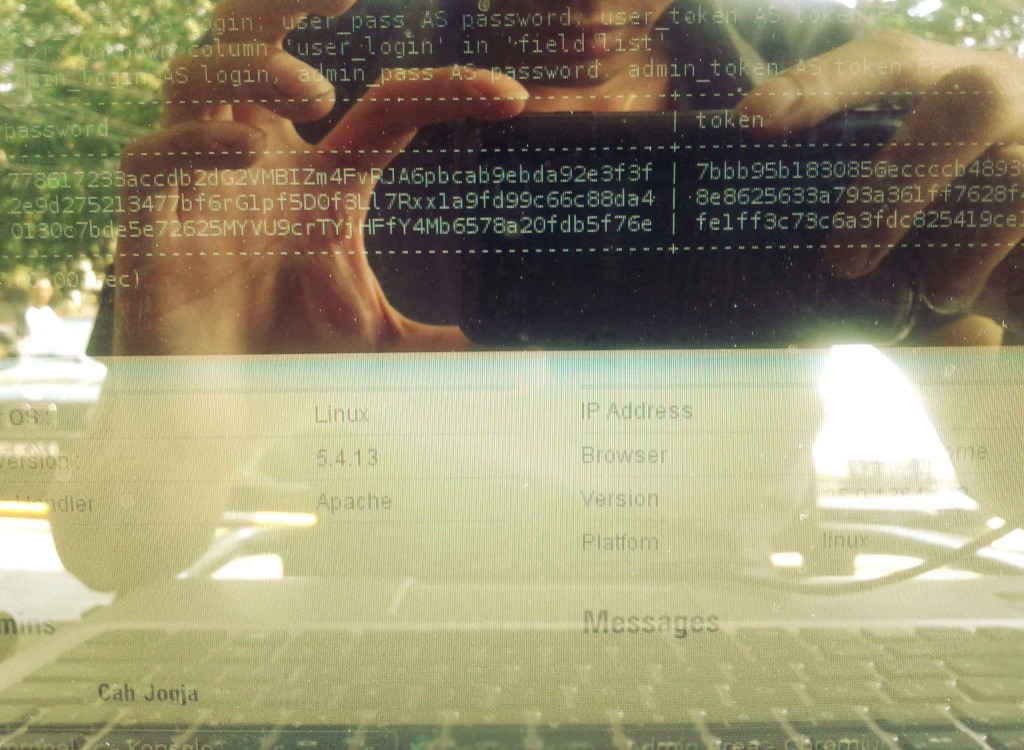
uKnowKids Flaw Literally Let Everyone Know Kids
Is DNSSEC Causing More Problems Than It Solves?
10 memory tricks for creating safe and easy-to-remember passwords

You’re probably sick of hearing how important it is to follow certain steps when creating passwords, but we assure you that it really is vital to keep them in mind. We also recommend that you change them every so often, that you don’t use the same one for various accounts, and that they aren’t related to anything personal about you (birthday, favorite football team, pet, etc.).
This is all common sense and we won’t stop reminding you, but we are also aware that remembering so many different, complex passwords is difficult. Because of this, we have some little tricks to share with you that will help you remember all of those tough-to-guess passwords!
1. Think of a sentence
Think of a saying or sentence that means something to you and, if possible, only you. It shouldn’t be too short, as it shouldn’t be easily guessable, nor so long that you forget it. If it contains upper and lower case letters, great. Symbols? Even better. “In the local pub the beers are €4”, for example. Now, take the first letter from each word and you get “Itlptba€3”, which is a good password. If you can’t think of anything maybe use the title of your favorite song, for example.
2. Combine two words
Choose two words (again, best if they only mean something to you) and make a different word by mixing up the letters. If you have chosen “Beards” and “Lighters”, the base for your new password will be “BLeiagrhdtsrs”. It doesn’t contain any numbers or symbols, but you can easily strengthen it by following some more examples that we’ll tell you about below.
3. Turn vowels into numbers
This is a trick that cybercriminals already know about, but it could work well as an extra to a different password method. Taking the previous example, our password “BLeiagrhdtsrs” becomes “BL314grhdtsrs”. Adding a few symbols would make it perfect to use.
4. Remove the vowels
Instead of replacing them with number such as in the previous example, we can remove the vowels completely. If we use our invented word “BLeiagrhdtsrs”, the password would turn out to be “BLgrhdtsrs”. Just be sure to add some extra numbers and symbols to make it even more secure.
5. The keyboard trick
Once again, this one consists of removing something. First of all, choose a sequence of numbers that is easy to remember (a postal code, for example), so imagine that we end up with 28921. Now, look for the numbers on the keypad and instead of using numbers, use the letters just beneath them: “2wsx8ik9ol2wsx1qaz”. To make it a little more complicated, you can change one of the characters for a symbol and put some into upper case.
6. Mix a number and a word together
This one is easy, so let’s imagine we use the word “Beards” and the number “28921”. So if we join them together, one letter and number at a time, and in reverse, we end up with “B1e2a9r8d2s”. All that’s missing is a symbol and you’re good to go.
7. Use the account as a base
Using the same password for various accounts and websites is a terrible idea, but a simple trick could turn your go-to password into one that could work for different accounts. For example, if you want to sign up to Facebook you could add “FB” to the start or end of the password. You could also try a variation of the website’s name by mixing upper and lower cases, symbols, and numbers until you have a password that you like. If we stick with the examples from above, we would end up with these two versions:
ElbdJptga3€_FB
F4c3b00k_ElbdJptga3€
8. Roll a dice
This system is a little more elaborate, but if an 11-year-old girl can do it, there’s no reason why you can’t. The method used, known as Diceware, generates completely random passwords – which are very strong and secure – by rolling a dice and a list of words. You can check it all out here and see what you think.
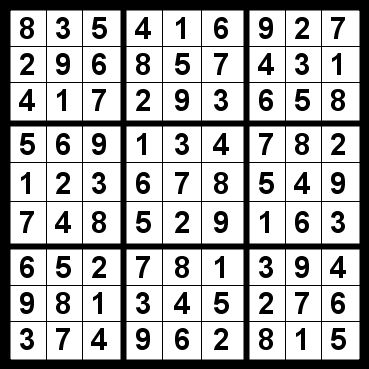
9. Sudoku style
This will involve you getting creative, so grab a pen and paper and draw a 6×6 square, with random numbers in each of the blocks. Now think of how you move your finger on your phone’s screen when unlocking it, and move your fingers over the Sudoku that you’ve just drawn. The numbers that you’ve just traced over will form the basis for your password, which you can add some letters and symbols to.
This might just be the best method on the list. If you change the numbers that you have placed in the blocks, the same movement with your finger will give you a new code. So by just remembering the movement and keeping the innocent looking piece of paper, you’ll have an infinite source of passwords.
10. Final tip: don’t follow the crowd
Some attackers aren’t just clever, but they also dedicate a lot of time to thinking about how to guess passwords. They know all of these methods, so your ability to out-smart them depends on how you combine the different letters or numbers that form the base of your password. So, try to think a little outside the box, as the more unconventional your password, the harder it is for them to guess it.
The post 10 memory tricks for creating safe and easy-to-remember passwords appeared first on MediaCenter Panda Security.
Core FTP Server 1.2 Buffer Overflow
Core FTP Server version 1.2 buffer overflow proof of concept exploit.
Android Calling Getpidcon Gets Wrong Security Context
The servicemanager, keystore and drmserver all use getpidcon function to get the security context of the caller from a binder. When combined with a one way binder transaction this results in getting the security context of the current process which might allow a selinux mac bypass.
Wireshark Dissect_oml_attrs Out-Of-Bounds Read
A crash was observed in an ASAN build of Wireshark (current git master), by feeding a malformed file to tshark.
Wireshark Add_ff_vht_compressed_beamforming_report Out-Of-Bounds Read
A crash was observed in an ASAN build of Wireshark (current git master), by feeding a malformed file to tshark.
Wireshark Dissect_ber_set Out-Of-Bounds Read
A crash was observed in an ASAN build of Wireshark (current git master), by feeding a malformed file to tshark.
