ManageEngine Firewall Analyzer version 8.5 suffers from a remote SQL injection vulnerability.
Monthly Archives: February 2016
Oxwall Forum v1.8.1 – Persistent Cross Site Scripting Vulnerability
Posted by Vulnerability Lab on Feb 22
Document Title:
===============
Oxwall Forum v1.8.1 – Persistent Cross Site Scripting Vulnerability
References (Source):
====================
http://www.vulnerability-lab.com/get_content.php?id=1740
Release Date:
=============
2016-02-22
Vulnerability Laboratory ID (VL-ID):
====================================
1740
Common Vulnerability Scoring System:
====================================
3.6
Product & Service Introduction:…
Kaspersky Lab’s Leslie Bois Recognized as CRN 2016 Channel Chief
Cryptolocker ‘Locky’. How it works
We don’t know if you’ve heard of the new Cryptolocker which is called ‘Locky’…
It works as follows:
- It arrives by mail and the attachment is a Word document with macros.
- Upon opening the document the macros infects the computer.
- It deletes any security copies that Windows has made and starts to encrypt the files.
- Once finished, it opens a file called “_Locky_recover_instructions.txt” in the notepad.
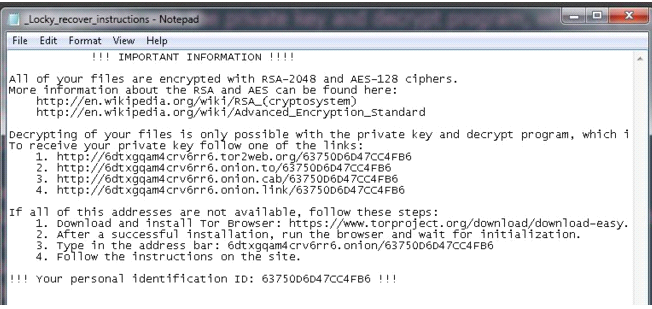
In fact, if we suspect that we have been attacked by Locky we can look for one of these files in our computer – if they’re there, then we know Locky has paid us a visit:
- “_Locky_recover_instructions.txt”
- “_Locky_recover_instructions.bmp”
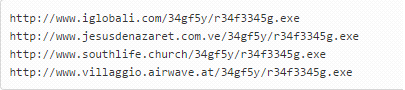
When the Word document that started the infection is opened, it downloads Locky, and what we have seen is that in all cases the malware comes from a legal website which has been compromised. It is there that the malware is stored. These are some of the URLs hosting malware:
The email that it comes attached in is the following:
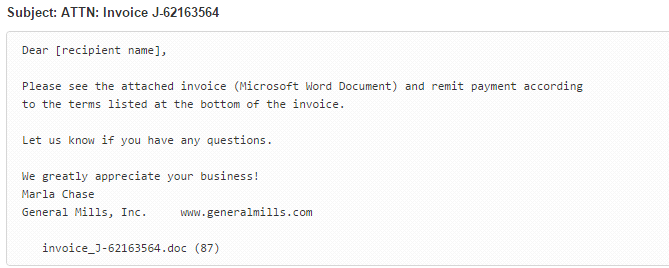
In this case, the attached Word is called invoice_J-67870889.doc
Some of the variants that we have seen used PowerShell to carry out the downloading and running of Locky from the macro, with the rest of it being the same.
The post Cryptolocker ‘Locky’. How it works appeared first on MediaCenter Panda Security.
Re: Cisco ASA VPN – Zero Day Exploit
Posted by Daniel Hadfield on Feb 22
Is there a CVE ID for this?
Also what firmware does this effect? I tested this and the input gets
HTML encoded so is nulled.
Re: Cisco ASA VPN – Zero Day Exploit
Posted by Joey Maresca on Feb 22
For folks who want code that runs, I did you all a favor, fixed the ident
issues, removed unused libraries, fixed SSL certificate validation checks
causing failures, fixed typos that prevent running, killed dead code, made
sure it actually used the Port input. All while stripping out the
unnecessary fluff. It may not be perfect but it will at least now run.
import string, sys
import ssl, socket, httplib
if __name__ == ‘__main__’:…
Avast Virtualization Driver – Elevation Of Privileges
Posted by Kyriakos Economou on Feb 22
* CVE: CVE-2015-8620
* Vendor: Avast
* Reported by: Kyriakos Economou
* Date of Release: 17/02/2016
* Affected Products: Multiple
* Affected Version: <= v11.1.2245
* Fixed Version: v11.1.2253
Description:
A heap overflow bug in the Avast Virtualization kernel mode driver (aswSnx.sys) allows a local attacker to elevate his
privileges from any account type and execute code as SYSTEM.
Affected Products:
Avast Internet Security v11.1.2245…
BlackBerry Enterprise Service 12 Self-Service – SQLi and Reflected XSS
Posted by Adrian Hayes on Feb 22
( , ) (,
. ‘.’ ) (‘. ‘,
). , (‘. ( ) (
(_,) .’), ) _ _,
/ _____/ / _ ____ ____ _____
____ ==/ /_ _/ ___/ _ /
/ / | \ __( <_> ) Y Y
/______ /___|__ / ___ >____/|__|_| /
/ /.-. / /:wq
(x.0)
‘=.|w|.=’
_=”””=….
PLANET IP Surveillance camera Multiple Vulnerabilities
Posted by 0rwell Labs on Feb 22
Overview
=======
Technical Risk: high
Likelihood of Exploitation: medium
Tested version: ICA-5350V/ICA-*
Credits: Discovered and researched by GT.Omaz from OrwellLabs
Issues
=====
I. Local File Inclusion
II. Arbitrary file read/Authentication bypass
III. Sensitive information disclosure
IV. Cross-site request forgery
V. Reflected Cross-site scripting
VI. hardcoded credentials
I. Local File Inclusion
================
The Web Management…
ferretCMS– Multiple Cross-Site Scripting Vulnerabilities
Posted by Sachin Wagh on Feb 22
Information
*——————————**——————————*
*——————————**——————————*
Vulnerability Type : Multiple Cross Site Scripting Vulnerabilities
Vulnerable Version : 2.0.2-alpha
Vendor Homepage:https://github.com/JRogaishio/ferretCMS
CVE-ID :
Severity : Medium
Author – Sachin Wagh (@tiger_tigerboy)
Description…