
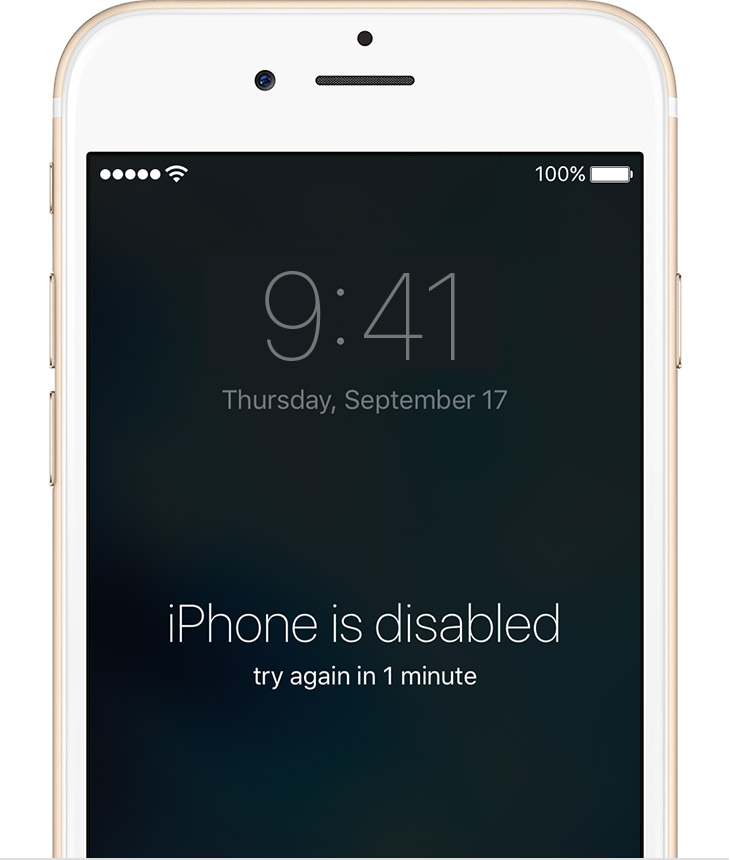
Despite being essential to protect your personal data, the security measures implemented by smartphone manufacturers to protect it from cyber-criminals can work against you. That’s the case wìth Apple and the Auto-Lock feature that automatically locks your device after six failed passcode attempts.
There are multiple reasons why that could occur. For example, your little one starts playing with your phone, you suffer a temporary memory lapse, or pay the consequences of a party that went a bit out of hand… Whatever the reason, a situation like that can have some serious consequences if you don’t take the appropriate precautionary measures.
A feature designed to prevent strangers from accessing your device in the event of loss or theft can cause you, the phone’s owner, to lose all of your photos, videos, music, and contacts. The solution? A backup which, if you haven’t already, you should definitely make now.
iPhones usually provide two options to make backups: iTunes (which saves backups to your computer) and iCloud (which saves them to Apple’s cloud). If you choose the first option, you can do two things: connect your smartphone to your computer via a USB port, or via Wi-Fi if both devices belong to the same network. You can check Apple’s website for detailed instructions.
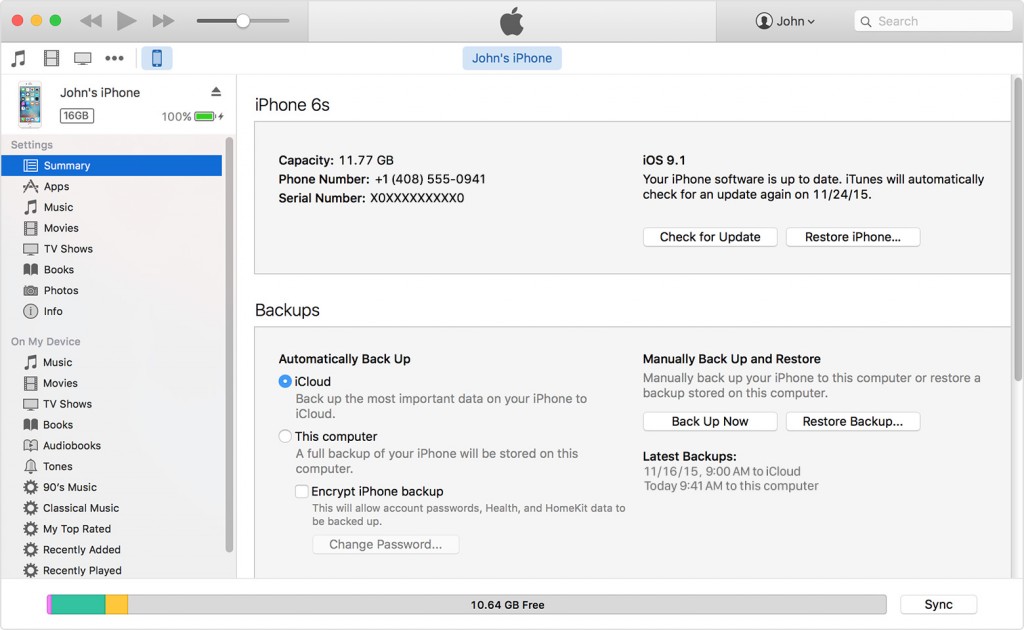
If you choose iCloud, there is no need for both devices to be on the same network or connected via a cable: you can make the backup from any place, any time. Additionally, you can configure your account to make daily backups automatically. Another advantage is that cloud backups are encrypted by default, an option you can also enable in iTunes.
Whatever mechanism you choose to back up your iPhone, a recent backup can save your life if your device gets locked after six wrong codes are entered.
If that ever happens to you, the only solution is to wipe the content of the locked device and retrieve it from a backup. There is no way to reset the passcode. No shortcuts. You will have to wipe the entire iPhone and start it from the backup copy (if you have one), or, in the worst case scenario, from scratch. The entire process is explained on the website of the company with the half eaten apple logo.
However, there is yet another, more extreme scenario. If you have complete faith in your memory, there are no kids around and you think that the only reason to have a wrong code entered on your smartphone is that it gets stolen, you can choose to erase your device automatically (without locking it) after ten failed passcode attempts. In that case, keeping an up-to-date backup copy is even more necessary.
A good example of all this is what has happened with the iPhone of one of the perpetrators of the recent San Bernardino (California) shooting after being arrested by the police. As you may already know, the FBI has asked Apple to make a special version of iOS that doesn’t lock the device after six failed passcode attempts or wipes it after ten attempts. That would allow the FBI to brute-force attack the criminal’s phone to break into it without fear of turning it into a paperweight.
That is precisely what happened with the iPhone of another criminal that ended up in the hands of a not-so-skilled member of the Massachusetts Police Department. When trying to access the phone in search of evidence, the agent entered ten wrong passcodes, setting the device back to its factory defaults. Goodbye to any possible evidence…
So be careful. If you ignore our advice and don’t make backup copies regularly, the same could happen to you. Are you really willing to run that risk?
The post How to prevent your iPhone content from being lost if you forget your password appeared first on MediaCenter Panda Security.





