Monthly Archives: May 2016
Anonymous Begins Hacking Campaign Against Banks
Why it would have been a relief to know who’s behind bitcoin

News broke that Australian businessman Craig Steven Wright is Satoshi Nakamoto earlier this week.
(Image via the Wall Street Journal)
Finally, we know the inventor of bitcoin! Wait, maybe not so fast. Actually, we don’t know anything at all.
![]()
Jigsaw and how ransomware is becoming more aggressive with new capabilities
There is no doubt that criminals have found a mechanism in ransomware enabling them to obtain significant benefits with relatively little effort, reports ESET’s Josep Albors.
The post Jigsaw and how ransomware is becoming more aggressive with new capabilities appeared first on We Live Security.
![]()
Google introduces HTTPS for blogspot domain names
Google is adding further security to the world wide web by introducing HTTPS for every blogspot domain name.
The post Google introduces HTTPS for blogspot domain names appeared first on We Live Security.
![]()
CEBA-2016:0717 CentOS 6 kdebase-workspace BugFixUpdate
CentOS Errata and Bugfix Advisory 2016:0717 Upstream details at : https://rhn.redhat.com/errata/RHBA-2016-0717.html The following updated files have been uploaded and are currently syncing to the mirrors: ( sha256sum Filename ) i386: 587077044c62f85aa03244e66f2381b335de1f2316c811b8a26cc9af8a884454 kdebase-workspace-4.3.4-33.el6_7.i686.rpm 0b66c8ef112ca136ec640d419e785eb07bca0e9d64bf87011ea2999b173c19e6 kdebase-workspace-akonadi-4.3.4-33.el6_7.i686.rpm 2c9ad5ca10aa7f3cb6039674428b9997743e650746a3bb9b48aa67564460a35e kdebase-workspace-devel-4.3.4-33.el6_7.i686.rpm 1fcfc59285c6dd014bdc88ddcc492e03f271b27189b6d05ab2ca0d1aee56c91c kdebase-workspace-libs-4.3.4-33.el6_7.i686.rpm fd15af38ac3467dbe2e2a47fd4b57eacd089e8863e327e8a0b850a351d006bf7 kdebase-workspace-python-applet-4.3.4-33.el6_7.i686.rpm 982d638a6705180bb142a17fe4fae8558535be6e0e7f3ab8c553cbf8839a1b75 kdebase-workspace-wallpapers-4.3.4-33.el6_7.noarch.rpm da4e6515d5c7f14386676b27852e7cf1e303b4701ceca51dba2daaf93d30f2d0 kdm-4.3.4-33.el6_7.i686.rpm 3530578bc3a02f886db5d2c86c898bfd9cd3dafac197d8d313383926e1a3a8bb ksysguardd-4.3.4-33.el6_7.i686.rpm 9494adc6952ca48e18383b3ff9f5a4d868c0ad6a50fa1f6467e6de963285aaba oxygen-cursor-themes-4.3.4-33.el6_7.noarch.rpm x86_64: 52e363a8d81e69115846ac705090ff6dab166a6aabe0ebeafa6f9ac312d3f8e4 kdebase-workspace-4.3.4-33.el6_7.x86_64.rpm 2680a8a3021a8a7448ebe0651fbcd14767e5295bad2e3312ac6c70e7a69dd899 kdebase-workspace-akonadi-4.3.4-33.el6_7.x86_64.rpm 2c9ad5ca10aa7f3cb6039674428b9997743e650746a3bb9b48aa67564460a35e kdebase-workspace-devel-4.3.4-33.el6_7.i686.rpm 96793b85aa863d41dfc7c4dd8d411cd05e998b3f3dc6e1cfd297b8e1659259eb kdebase-workspace-devel-4.3.4-33.el6_7.x86_64.rpm 1fcfc59285c6dd014bdc88ddcc492e03f271b27189b6d05ab2ca0d1aee56c91c kdebase-workspace-libs-4.3.4-33.el6_7.i686.rpm f391dd8d36918e48a4b729d9eabfaa33c57823837cb33b62da7166c99bb8d788 kdebase-workspace-libs-4.3.4-33.el6_7.x86_64.rpm fad74d6d271c1ab5717376c268cde8e787df841d41225814cda9791d101bb205 kdebase-workspace-python-applet-4.3.4-33.el6_7.x86_64.rpm 982d638a6705180bb142a17fe4fae8558535be6e0e7f3ab8c553cbf8839a1b75 kdebase-workspace-wallpapers-4.3.4-33.el6_7.noarch.rpm d34729ccefc85a9a1c66613c1563f5e54f631340cccb8fe38141796464aa6fd3 kdm-4.3.4-33.el6_7.x86_64.rpm ec64aff8483dadeb241c1db5a4617060737d77c38760ad7f4831e04bde68dd00 ksysguardd-4.3.4-33.el6_7.x86_64.rpm 9494adc6952ca48e18383b3ff9f5a4d868c0ad6a50fa1f6467e6de963285aaba oxygen-cursor-themes-4.3.4-33.el6_7.noarch.rpm Source: 32e2aaa39dd509d7eea46b755b7a0a5f159381802dacbeec0b6a8e8f684459e8 kdebase-workspace-4.3.4-33.el6_7.src.rpm
Warning — Widely Popular ImageMagick Tool Vulnerable to Remote Code Execution
A serious zero-day vulnerability has been discovered in ImageMagick, a widely popular software tool used by a large number of websites to process user’s photos, which could allow hackers to execute malicious code remotely on servers.
ImageMagick is an open-source image processing library that lets users resize, scale, crop, watermarking and tweak images.
The ImageMagick tool is supported by
![]()
“I’m with Stupid†Locky network gets hacked and dissed
A few months ago, we reported on a white hack against Dridex where the malicious payload was removed and an Avira antivirus downloader added.
The post “I’m with Stupid” Locky network gets hacked and dissed appeared first on Avira Blog.
FreeBSD-SA-16:17.openssl
PandaLabs identifies 227,000 malware samples per day in the first quarter of 2016
 PandaLabs, Panda Security’s laboratory, outlined in this report the main cyber-security developments over the first months in 2016, showing statistics of malware and cyber-attacks in the first quarter of 2016. The amount of malware created continues to break records, with more than 20 million new samples identified, an average of 227,000 per day.
PandaLabs, Panda Security’s laboratory, outlined in this report the main cyber-security developments over the first months in 2016, showing statistics of malware and cyber-attacks in the first quarter of 2016. The amount of malware created continues to break records, with more than 20 million new samples identified, an average of 227,000 per day.
Cyber-crime does not stop
Cyber-criminals continue attacking without giving sensitive infrastructures the chance to take a break, as seen in the attack suffered by 21st Century Holdings, a clinic specialized in cancer treatments with headquarters in Florida. The clinic had to alert their 2.2 million patients and workers that their personal data might have been compromised.
The Rosen Hotels & Resort chain has been the victim of an attack that occurred between September 2014 and February 2016. The company alerted their clients who may have used a credit or debit card in their establishments over this time period that their data could have been stolen by the attackers.
Even the world’s most powerful governments haven’t been spared, such as the United States, where the Department of Defense has presented a rewards program called “Hack the Pentagon” in which rewards are offered to hackers who find security holes in the Pentagon’s web pages, applications and networks.
Smartphones are another easy target for cyber-criminals. SNAP is the name of a vulnerability that affects the LG G3 phones. The problem is due to an error in the implementation of LG notifications called Smart Notice, which allows JavaScript to be executed.
The growing sector, the Internet of Things, is also affected by this year’s criminal activity. In this area, we can see how something as innocent as a doorbell can be attacked. Manufacturers are becoming more aware of their product’s safety, in fact, General Motors just launched a new rewards program for hackers who are able to find vulnerabilities in their vehicles.
Q1 in numbers
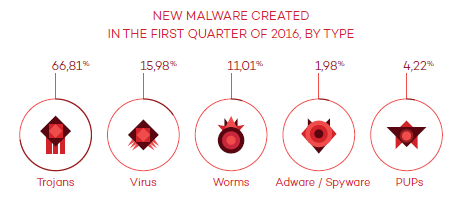
The PandaLabs study shows that Trojans continue to be in the lead of all malware samples. Out all malware samples created in 2016, Trojans are number one with 66.81% of the total (an increase compared to last year), followed by viruses (15.98%), worms (11.01%), PUPs (4.22%) and aware/Spyware (1.98%):
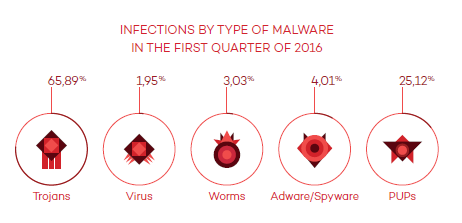
When we analyze the infections caused by malware worldwide, we find Trojans in the lead again. This is normal if we take into account the rise in ransomware infections, including the rise of Trojans, which is also one of the most popular attacks cyber-criminals use because it allows them to obtain money easily and securely. There are more and more companies whose networks are falling victim to these cyber-criminals and who are paying millions of euros to rescue their stolen information:
According to PandaLabs, Asia and Latin America are the most affected regions
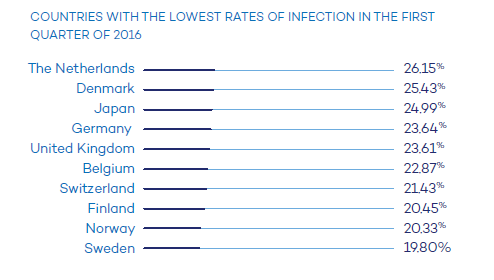
In this study we can find a table showing the countries with the highest and lowest infection rates in Q1 of 2016: Asia and Latin America (China leads the ranking with 51.35% of infections) are the most affected countries; while the Scandinavian countries have the lowest infection rates with (Sweden at the lowest at 19.80%).

 If you want to know more about the specific attacks, be up to date with the latest research carried out by the FBI, and the latest news of the cyberwar, you can download the entire document here. We hope this is of interest to you!
If you want to know more about the specific attacks, be up to date with the latest research carried out by the FBI, and the latest news of the cyberwar, you can download the entire document here. We hope this is of interest to you!
The post PandaLabs identifies 227,000 malware samples per day in the first quarter of 2016 appeared first on Panda Security Mediacenter.