Red Hat Enterprise Linux: An updated rhevm-dwh package that fixes one bug is now available.
Monthly Archives: May 2016
RHBA-2016:1113-1: rhev-hypervisor bug fix and enhancement update for RHEV 3.6.6
Red Hat Enterprise Linux: An updated rhev-hypervisor package that fixes several security issues, bugs, and
enhancements is now available.
RHBA-2016:1110-1: rhevm-setup-plugins bug fix update for 3.6.6
Red Hat Enterprise Linux: Updated rhevm-setup-plugins packages that add fix one bug are now available.
RHBA-2016:1108-1: ovirt-engine-extension-aaa-ldap bug fix and enhancement update for 3.6.6
Red Hat Enterprise Linux: Updated ovirt-engine-extension-aaa-ldap 1.1.4 packages that fix several bugs and
add various enhancements are now available.
RHBA-2016:1107-1: ovirt-engine-extension-aaa-jdbc bug fix and enhancement update for 3.6.6
Red Hat Enterprise Linux: Updated ovirt-engine-extension-aaa-jdbc 1.0.7 package that fix several bugs and
add various enhancements is now available.
USN-2950-5: Samba regression
Ubuntu Security Notice USN-2950-5
25th May, 2016
samba regression
A security issue affects these releases of Ubuntu and its
derivatives:
- Ubuntu 16.04 LTS
- Ubuntu 15.10
- Ubuntu 14.04 LTS
Summary
USN-2950-1 introduced a regression in Samba.
Software description
- samba
– SMB/CIFS file, print, and login server for Unix
Details
USN-2950-1 fixed vulnerabilities in Samba. USN-2950-3 updated Samba to
version 4.3.9, which introduced a regression when using the ntlm_auth tool.
This update fixes the problem.
Original advisory details:
Jouni Knuutinen discovered that Samba contained multiple flaws in the
DCE/RPC implementation. A remote attacker could use this issue to perform
a denial of service, downgrade secure connections by performing a man in
the middle attack, or possibly execute arbitrary code. (CVE-2015-5370)
Stefan Metzmacher discovered that Samba contained multiple flaws in the
NTLMSSP authentication implementation. A remote attacker could use this
issue to downgrade connections to plain text by performing a man in the
middle attack. (CVE-2016-2110)
Alberto Solino discovered that a Samba domain controller would establish a
secure connection to a server with a spoofed computer name. A remote
attacker could use this issue to obtain sensitive information.
(CVE-2016-2111)
Stefan Metzmacher discovered that the Samba LDAP implementation did not
enforce integrity protection. A remote attacker could use this issue to
hijack LDAP connections by performing a man in the middle attack.
(CVE-2016-2112)
Stefan Metzmacher discovered that Samba did not validate TLS certificates.
A remote attacker could use this issue to spoof a Samba server.
(CVE-2016-2113)
Stefan Metzmacher discovered that Samba did not enforce SMB signing even if
configured to. A remote attacker could use this issue to perform a man in
the middle attack. (CVE-2016-2114)
Stefan Metzmacher discovered that Samba did not enable integrity protection
for IPC traffic. A remote attacker could use this issue to perform a man in
the middle attack. (CVE-2016-2115)
Stefan Metzmacher discovered that Samba incorrectly handled the MS-SAMR and
MS-LSAD protocols. A remote attacker could use this flaw with a man in the
middle attack to impersonate users and obtain sensitive information from
the Security Account Manager database. This flaw is known as Badlock.
(CVE-2016-2118)
Samba has been updated to 4.3.8 in Ubuntu 14.04 LTS and Ubuntu 15.10.
Ubuntu 12.04 LTS has been updated to 3.6.25 with backported security fixes.
In addition to security fixes, the updated packages contain bug fixes,
new features, and possibly incompatible changes. Configuration changes may
be required in certain environments.
Update instructions
The problem can be corrected by updating your system to the following
package version:
- Ubuntu 16.04 LTS:
-
samba
2:4.3.9+dfsg-0ubuntu0.16.04.2
- Ubuntu 15.10:
-
samba
2:4.3.9+dfsg-0ubuntu0.15.10.2
- Ubuntu 14.04 LTS:
-
samba
2:4.3.9+dfsg-0ubuntu0.14.04.3
To update your system, please follow these instructions:
https://wiki.ubuntu.com/Security/Upgrades.
In general, a standard system update will make all the necessary changes.
References
USN-2985-1: GNU C Library vulnerabilities
Ubuntu Security Notice USN-2985-1
25th May, 2016
eglibc, glibc vulnerabilities
A security issue affects these releases of Ubuntu and its
derivatives:
- Ubuntu 15.10
- Ubuntu 14.04 LTS
- Ubuntu 12.04 LTS
Summary
Several security issues were fixed in the GNU C Library.
Software description
- eglibc
– GNU C Library - glibc
– GNU C Library
Details
Martin Carpenter discovered that pt_chown in the GNU C Library did not
properly check permissions for tty files. A local attacker could use this
to gain administrative privileges or expose sensitive information.
(CVE-2013-2207, CVE-2016-2856)
Robin Hack discovered that the Name Service Switch (NSS) implementation in
the GNU C Library did not properly manage its file descriptors. An attacker
could use this to cause a denial of service (infinite loop).
(CVE-2014-8121)
Joseph Myers discovered that the GNU C Library did not properly handle long
arguments to functions returning a representation of Not a Number (NaN). An
attacker could use this to cause a denial of service (stack exhaustion
leading to an application crash) or possibly execute arbitrary code.
(CVE-2014-9761)
Arjun Shankar discovered that in certain situations the nss_dns code in the
GNU C Library did not properly account buffer sizes when passed an
unaligned buffer. An attacker could use this to cause a denial of service
or possibly execute arbitrary code. (CVE-2015-1781)
Sumit Bose and Lukas Slebodnik discovered that the Name Service
Switch (NSS) implementation in the GNU C Library did not handle long
lines in the files databases correctly. A local attacker could use
this to cause a denial of service (application crash) or possibly
execute arbitrary code. (CVE-2015-5277)
Adam Nielsen discovered that the strftime function in the GNU C Library did
not properly handle out-of-range argument data. An attacker could use this
to cause a denial of service (application crash) or possibly expose
sensitive information. (CVE-2015-8776)
Hector Marco and Ismael Ripoll discovered that the GNU C Library allowed
the pointer-guarding protection mechanism to be disabled by honoring the
LD_POINTER_GUARD environment variable across privilege boundaries. A local
attacker could use this to exploit an existing vulnerability more easily.
(CVE-2015-8777)
Szabolcs Nagy discovered that the hcreate functions in the GNU C Library
did not properly check its size argument, leading to an integer overflow.
An attacker could use to cause a denial of service (application crash) or
possibly execute arbitrary code. (CVE-2015-8778)
Maksymilian Arciemowicz discovered a stack-based buffer overflow in the
catopen function in the GNU C Library when handling long catalog names. An
attacker could use this to cause a denial of service (application crash) or
possibly execute arbitrary code. (CVE-2015-8779)
Florian Weimer discovered that the getnetbyname implementation in the GNU C
Library did not properly handle long names passed as arguments. An attacker
could use to cause a denial of service (stack exhaustion leading to an
application crash). (CVE-2016-3075)
Update instructions
The problem can be corrected by updating your system to the following
package version:
- Ubuntu 15.10:
-
libc6-dev
2.21-0ubuntu4.2
-
libc6
2.21-0ubuntu4.2
- Ubuntu 14.04 LTS:
-
libc6-dev
2.19-0ubuntu6.8
-
libc6
2.19-0ubuntu6.8
- Ubuntu 12.04 LTS:
-
libc6-dev
2.15-0ubuntu10.14
-
libc6
2.15-0ubuntu10.14
To update your system, please follow these instructions:
https://wiki.ubuntu.com/Security/Upgrades.
After a standard system update you need to reboot your computer to
make all the necessary changes.
References
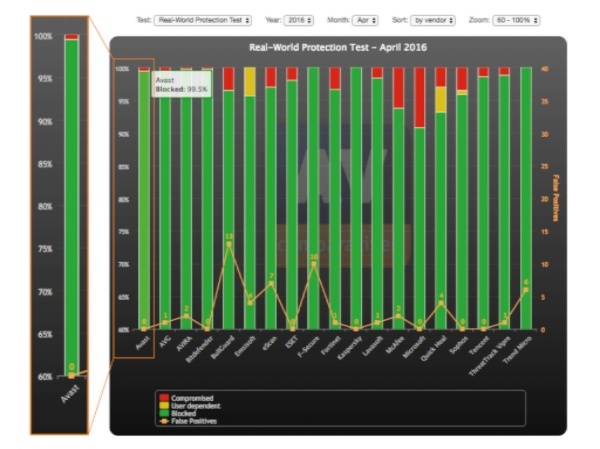
Avast Free Antivirus is top-rated free security software
Avast Free Antivirus has nearly 100% detection rate and no false positives.
Wondering if Avast Free Antivirus is worth the price? We understand that when it comes to “free” things, you mostly get what you pay for. But in the case of Avast Free Antivirus, our free security product is better than pricey premium antivirus products!
![]()
HP Security Bulletin HPSBMU03600 1
HP Security Bulletin HPSBMU03600 1 – HPE Insight Control server provisioning has addressed security vulnerabilities in OpenSSL that could be exploited remotely resulting in Denial of Service (DoS). Revision 1 of this advisory.
HP Security Bulletin HPSBUX03606 1
HP Security Bulletin HPSBUX03606 1 – Potential security vulnerabilities have been identified in HP-UX running the Apache Tomcat 7 Servlet Engine. These vulnerabilities could be exploited remotely resulting in URL redirection, access restriction bypass, Cross-Site Request Forgery (CSRF), directory traversal, unauthorized read access to data, execution of arbitrary code with privilege elevation, or Denial of Service (DoS). Revision 1 of this advisory.
