Monthly Archives: May 2016
North Korea makes a Facebook clone, site gets hacked hours later
When it comes to countries notorious for censoring online content and gleaning information from citizens, North Korea is one of the first names to come to mind. If a country like North Korea was to create its own social network, wouldn’t you think that securing the site would be one of its top priorities? Recent news begs to differ.
North Korea recently launched a social networking site that bears an uncanny resemblance to the Facebook we know and love. The site, which was hosted in North Korea itself, could originally be found at www.starcon.net.kp/.
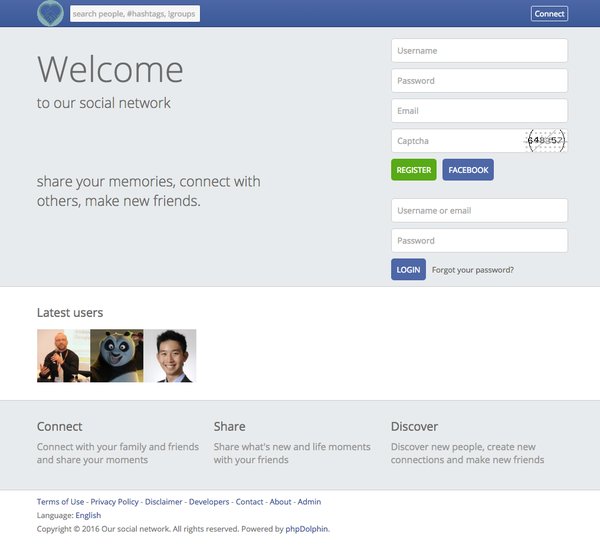 A screenshot of North Korea’s own social network. (Image via Dyn Research)
A screenshot of North Korea’s own social network. (Image via Dyn Research)
![]()
CESA-2016:1137 Important CentOS 5 opensslSecurity Update
CentOS Errata and Security Advisory 2016:1137 Important Upstream details at : https://rhn.redhat.com/errata/RHSA-2016-1137.html The following updated files have been uploaded and are currently syncing to the mirrors: ( sha256sum Filename ) i386: 631e91525505003d8b42dfc52fd9b1423aa4f62b52fe0a99b179fc7ca5d402df openssl-0.9.8e-40.el5_11.i386.rpm 91707deacf653a4c5e1ee71bfe78c312ddaf1ced22598aa0ed9364b801a95f75 openssl-0.9.8e-40.el5_11.i686.rpm b14fb301e7bb528ac9f12862471875a8a937e557437bf5dfeeb5bf45ba62a7a0 openssl-devel-0.9.8e-40.el5_11.i386.rpm 7f74ee4c3eb94f41034d716729f5a922301984327d3c7e1398d625e3d9828071 openssl-perl-0.9.8e-40.el5_11.i386.rpm x86_64: 91707deacf653a4c5e1ee71bfe78c312ddaf1ced22598aa0ed9364b801a95f75 openssl-0.9.8e-40.el5_11.i686.rpm 4b01840b72a7ee82f9a3eb20df16106e3c0fdfcd0fb83457487a740fb4774413 openssl-0.9.8e-40.el5_11.x86_64.rpm b14fb301e7bb528ac9f12862471875a8a937e557437bf5dfeeb5bf45ba62a7a0 openssl-devel-0.9.8e-40.el5_11.i386.rpm e2fd36a8953c239a4526ee747fcef4faf0e52ba5c8c3a870bf3d05895ee19e72 openssl-devel-0.9.8e-40.el5_11.x86_64.rpm 3bad2a15cbbb096392eb97d9a414aae6b05edacc290ae266b2bbc47a875cf0b2 openssl-perl-0.9.8e-40.el5_11.x86_64.rpm Source: 603c7be208dc0cb4de26b9db6a29d6aa9bf796d0227ee58d81a0c07038ef1bfe openssl-0.9.8e-40.el5_11.src.rpm
CESA-2016:1139 Moderate CentOS 7 squid SecurityUpdate
CentOS Errata and Security Advisory 2016:1139 Moderate Upstream details at : https://rhn.redhat.com/errata/RHSA-2016-1139.html The following updated files have been uploaded and are currently syncing to the mirrors: ( sha256sum Filename ) x86_64: 431c4c5b1d7c4795b0597f7a655c44e03db6cd573082375d28bb9eac9e527f4e squid-3.3.8-26.el7_2.3.x86_64.rpm 1c04bd54d4b10395d2c3e78a6e00ef49a7123a4347edf5aa70f57e71a87528c1 squid-sysvinit-3.3.8-26.el7_2.3.x86_64.rpm Source: fa239d6add7aeb21c9bceb300207e173ce7dbca3a6bd73c52266571d58e7ec91 squid-3.3.8-26.el7_2.3.src.rpm
CESA-2016:1141 Moderate CentOS 7 ntp SecurityUpdate
CentOS Errata and Security Advisory 2016:1141 Moderate Upstream details at : https://rhn.redhat.com/errata/RHSA-2016-1141.html The following updated files have been uploaded and are currently syncing to the mirrors: ( sha256sum Filename ) x86_64: afb3dfae974c95e885c4f6335cd06f21263224ae21bff8bd2a5c54d5dde44d00 ntp-4.2.6p5-22.el7.centos.2.x86_64.rpm 46cc107c74c97c07bbbf1275133cc0e1b6a5598fa53bb34650e7f7559a49a36e ntpdate-4.2.6p5-22.el7.centos.2.x86_64.rpm f916317311a69c1fc27d297a15df69002e0a92ae91f290bed52ac99bf3ff3dab ntp-doc-4.2.6p5-22.el7.centos.2.noarch.rpm aad649a9c029e0fc173d24eaa3e548524f3cbe7271128ebd571d9535b2a9d38a ntp-perl-4.2.6p5-22.el7.centos.2.noarch.rpm d2c4d2d7472eb1a732e68cec9f7e60bc17d356bc879e3b23a69faf607793a995 sntp-4.2.6p5-22.el7.centos.2.x86_64.rpm Source: ccbc05d3874452e7c1e9b72fac58c4fc5f69d9a37cf77c5b7ffe34d6416acfe2 ntp-4.2.6p5-22.el7.centos.2.src.rpm
[RT-SA-2016-005] Unauthenticated File Upload in Relay Ajax Directory Manager may Lead to Remote Command Execution
Posted by RedTeam Pentesting GmbH on May 31
Advisory: Unauthenticated File Upload in Relay Ajax Directory Manager
may Lead to Remote Command Execution
A vulnerability within the Relay Ajax Directory Manager web application
allows unauthenticated attackers to upload arbitrary files to the web
server running the web application.
Details
=======
Product: Relay Ajax Directory Manager
Affected Versions: relayb01-071706, 1.5.1, 1.5.3 were tested, other
versions…
[RT-SA-2016-004] Websockify: Remote Code Execution via Buffer Overflow
Posted by RedTeam Pentesting GmbH on May 31
Advisory: Websockify: Remote Code Execution via Buffer Overflow
RedTeam Pentesting discovered a buffer overflow vulnerability in the C
implementation of Websockify, which allows attackers to execute
arbitrary code.
Details
=======
Product: Websockify C implementation
Affected Versions: all versions <= 0.8.0
Fixed Versions: versions since commit 192ec6f (2016-04-22) [0]
Vulnerability Type: Buffer Overflow
Security Risk: high
Vendor URL:…
[RT-SA-2015-012] XML External Entity Expansion in Paessler PRTG Network Monitor
Posted by RedTeam Pentesting GmbH on May 31
Advisory: XML External Entity Expansion in Paessler PRTG Network Monitor
Authenticated users who can create new HTTP XML/REST Value sensors in
PRTG Network Monitor can read local files on the PRTG host system via
XML external entity expansion.
Details
=======
Product: Paessler PRTG Network Monitor
Affected Versions: 14.4.12.3282
Fixed Versions: 16.2.23.3077/3078
Vulnerability Type: XML External Entity Expansion
Security Risk: medium
Vendor…
CESA-2016:1140 Moderate CentOS 6 squid34 SecurityUpdate
CentOS Errata and Security Advisory 2016:1140 Moderate Upstream details at : https://rhn.redhat.com/errata/RHSA-2016-1140.html The following updated files have been uploaded and are currently syncing to the mirrors: ( sha256sum Filename ) i386: 8b20601c95dc356ab1bb2b087331ee432f10cc567eb7503bef2e37891e18f03d squid34-3.4.14-9.el6_8.3.i686.rpm x86_64: 50ccde2efa8f46ef1c4dabba442427aa812ce24ecdf202e1390346dc190659b7 squid34-3.4.14-9.el6_8.3.x86_64.rpm Source: 304814481410fe9686f28f996c09882e794901d99aa3b509e92753ee683abf4c squid34-3.4.14-9.el6_8.3.src.rpm
CESA-2016:1141 Moderate CentOS 6 ntp SecurityUpdate
CentOS Errata and Security Advisory 2016:1141 Moderate Upstream details at : https://rhn.redhat.com/errata/RHSA-2016-1141.html The following updated files have been uploaded and are currently syncing to the mirrors: ( sha256sum Filename ) i386: 8cb6eac95c0d760035a5b251c4f6f72920d0c23766e98c845885ea91d4a69f08 ntp-4.2.6p5-10.el6.centos.1.i686.rpm 45f7a3ef55eff1448bdc1e6dd7e7d8db030461562643b6df33d82f59b3eb20da ntpdate-4.2.6p5-10.el6.centos.1.i686.rpm 27f007b3249dcb28a17938d3d09ef2534c30c9106b21515849a44dada7aebdbd ntp-doc-4.2.6p5-10.el6.centos.1.noarch.rpm f9cb8483b4f76c243ab2b3dd60b37d43444425fd9df60f46c01c720cd04774fc ntp-perl-4.2.6p5-10.el6.centos.1.i686.rpm x86_64: e4177b6e3734069c1ee814bd358b92c9fb81d66b80ce02b687df4579174d8abe ntp-4.2.6p5-10.el6.centos.1.x86_64.rpm 7179b002333ae35af41f07b70c1d6c87407d446645038ec70f401fc178fc69f2 ntpdate-4.2.6p5-10.el6.centos.1.x86_64.rpm 27f007b3249dcb28a17938d3d09ef2534c30c9106b21515849a44dada7aebdbd ntp-doc-4.2.6p5-10.el6.centos.1.noarch.rpm 281370467116872d146d319ee7687896e59db493724b51ed3b9fac10b6d1787d ntp-perl-4.2.6p5-10.el6.centos.1.x86_64.rpm Source: f8d4b4a86e65c984352cd0c1b79bbbb518f986112f8ee91a2e2d953c270fc307 ntp-4.2.6p5-10.el6.centos.1.src.rpm
