CentOS Errata and Enhancement Advisory 2016:1394 Upstream details at : https://rhn.redhat.com/errata/RHEA-2016-1394.html The following updated files have been uploaded and are currently syncing to the mirrors: ( sha256sum Filename ) x86_64: 2a1c1b67665db54057507583ecdf00b98a14ffe148d8306e18522bf654d258cf kmod-i40evf-1.5.10_k-1.el7_2.x86_64.rpm Source: 69581fb96f87613531f5b8532435e908f99e286402c42f3b6335da009c3f5f0b i40evf-1.5.10_k-1.el7_2.src.rpm
Monthly Archives: July 2016
CEEA-2016:1394 CentOS 7 i40e Enhancement Update
CentOS Errata and Enhancement Advisory 2016:1394 Upstream details at : https://rhn.redhat.com/errata/RHEA-2016-1394.html The following updated files have been uploaded and are currently syncing to the mirrors: ( sha256sum Filename ) x86_64: 38665ae0af8a8192bebd09c5f624f7acf95a07b8ab6197ae20766c79c327ad9a kmod-i40e-1.5.10_k-1.el7_2.x86_64.rpm Source: 05c0b3ff6a502a50a80a5024fcb158604723884cd8e5dddfcc40001420a021cb i40e-1.5.10_k-1.el7_2.src.rpm
Tiki Wiki CMS 15.0 Arbitrary File Download
Tiki Wiki CMS version 15.0 suffers from an arbitrary file download vulnerability.
CESA-2016:1392 Important CentOS 6 thunderbirdSecurity Update
CentOS Errata and Security Advisory 2016:1392 Important Upstream details at : https://rhn.redhat.com/errata/RHSA-2016-1392.html The following updated files have been uploaded and are currently syncing to the mirrors: ( sha256sum Filename ) i386: 4bb99c7b348a1507e1aac8a03f31c3c030fba5ed556ed4841f9a34ddecbda953 thunderbird-45.2-1.el6.centos.i686.rpm x86_64: 60a356711d21bb97f9c2ea44226bbb08ff09156303329a74b4366c9e85294647 thunderbird-45.2-1.el6.centos.x86_64.rpm Source: 9872bdd23676d96e6ddb0761d1190d25277e35d53ab3f7388f2a266a58693d55 thunderbird-45.2-1.el6.centos.src.rpm
Persistent Cross-Site Scripting in WordPress Activity Log plugin
Posted by Summer of Pwnage on Jul 11
————————————————————————
Persistent Cross-Site Scripting in WordPress Activity Log plugin
————————————————————————
Han Sahin, July 2016
https://sumofpwn.nl/advisory/2016/activity-log-plugin.png
————————————————————————
Abstract
————————————————————————
A…
AVG offers free ransomware decryptor tools for businesses
AVG just released six new ransomware decryption tools for our channel partners and their clients. The free tools decrypt the recent ransomware strains Apocalypse, BadBlock, Crypt888, Legion, SZFlocker and TeslaCrypt.
While our AVG Business products help detect and block against all known ransomware strains – including this recent six – our AVG partners now have helpful tools if a new client, or even a prospect, has a situation where files are already infected by ransomware.
With our new decryption tools, you should be able to recover your clients’ files and data without paying the ransom.
Using the AVG ransomware decryption tools
To use our AVG decryptor tools for the six recent ransomware strains, follow our simple five step process to unlock the encrypted files:
- Run a full system scan on the infected PC and quarantine all the infected files.
- Identify which infection strain encrypted the files. See the descriptions of each strain below. If the ransomware infection matches the strain details, download the appropriate tool and launch it.
- The tool opens a wizard, which breaks the decryption process into several easy steps.
- Follow the steps and you should again be able to reclaim your files in most cases.
- After decryption, be sure to properly back up restored files.
The six ransomware strains and AVG decryptor tools include:
- Apocalypse
- Description: The Apocalypse ransomware appends “.encrypted,” “.locked,” or “.SecureCrypted” to names of encrypted files (e.g. example.docx.encrypted, docx.locked, example.docx.SecureCrypted). It also creates ransom messages in files with extensions “.How_To_Decrypt.txt”, “.README.Txt,” or “.Contact_Here_To_Recover_Your_Files.txt” (e.g. example.docx.How_To_Decrypt.txt, example.docx.README.Txt)
- In those messages, you can find contact addresses such as [email protected], [email protected], [email protected], or [email protected].
- For example:
- Download the AVG decryptor tool: AVG offers one decryptor tool for the early versions of Apocalypse and one for the current version:
- http://files-download.avg.com/util/avgrem/avg_decryptor_Apocalypse.exe
- http://files-download.avg.com/util/avgrem/avg_decryptor_ApocalypseVM.exe
- BadBlock
- Description: BadBlock does not rename encrypted files. You can identify BadBlock by the ransom message named “Help Decrypt.html” and by a red window with ransom messages that begin with “This machine was infected with ransomware BadBlock . . .”
- Download the AVG decryptor tool (for 32-bit and 64-bit systems):
- http://files-download.avg.com/util/avgrem/avg_decryptor_BadBlock32.exe
- http://files-download.avg.com/util/avgrem/avg_decryptor_BadBlock64.exe
- Crypt888
- Description: Crypt888 (aka Mircop) creates encrypted files with the prepended name “Lock.” It also changes your desktop’s wallpaper to a message on a black background that begins with, “You’ve stolen 48.48BTC from the wrong people, please be so kind to return them and we will return your files.”
- Unfortunately, Crypt888 is a badly written piece of code, which means some of the encrypted files or folders will stay that way, even if you pay the fine, as the cybercriminals’ “official decryptor” may not work.
- Download the AVG decryptor tool:
- http://files-download.avg.com/util/avgrem/avg_decryptor_Crypt888.exe
- Legion
- Description: Legion encrypts and renames files with names like “example.docx[email protected]$.legion.” It also changes the desktop wallpaper and displays a “Your data is encrypted!!” warning.
- Download the AVG decryptor tool:
- http://files-download.avg.com/util/avgrem/avg_decryptor_Legion.exe
- SZFLocker
- Description: The name of the SZFlocker ransomware originates from a string that is appended to the names of encrypted files (e.g. example.docx.szf). The original files are rewritten with a Polish message.
- Download the AVG decryptor tool:
- http://files-download.avg.com/util/avgrem/avg_decryptor_SzfLocker.exe
- TeslaCrypt
- Description: This tool supports decryption of files encrypted by TeslaCrypt v3 and v4. The encrypted files come with different extensions, such as .vvv, .micro, .mp3, or with the original name only.
- Download the AVG decryptor tool:
- http://files-download.avg.com/util/avgrem/avg_decryptor_TeslaCrypt3.exe
At AVG, we take ransomware threats very seriously. We encourage our partners to continue being proactive by using multilayered protection, such as AVG Business solutions, which detect and block ransomware. You can find additional examples of the six ransomware strains and detailed descriptions here.
![]()
![]()
IoT Medical Devices: A Prescription for Disaster
Hospitals are on the IoT device vanguard revolutionizing patient care, but they are also huge targets for hackers targeting unsecure IoT medical devices.
Tools deliver false promises to YouTubers and Gamers
If you have a YouTube account and are an aspiring YouTube star, you may have wondered if there’s an easy way to speed up the slow process of raising your channel to the top. If you’re a slow-moving gamer looking for a simple way to advance your skills, you may have wished for coins to make more in game purchases and progress. If you search the Internet, you will definitely find websites with good advice on how to promote your content and even tips on how to create good videos and how to improve your gaming abilities.
“Want more subscribers? No problem!”
There’s much more available on the Internet than just advice and tips. You can also find websites, tools, and bots that promise to quickly boost a user’s YouTube or other social channels. Looking for more subscribers or followers? You’re in luck — we found a website where you just fill out a short form and click on a button or download their tool. Of course, there are comments left by satisfied customers who are promoting the tools. Since you’re not the first to use the tool and it has good reviews by others, it has to work, right?
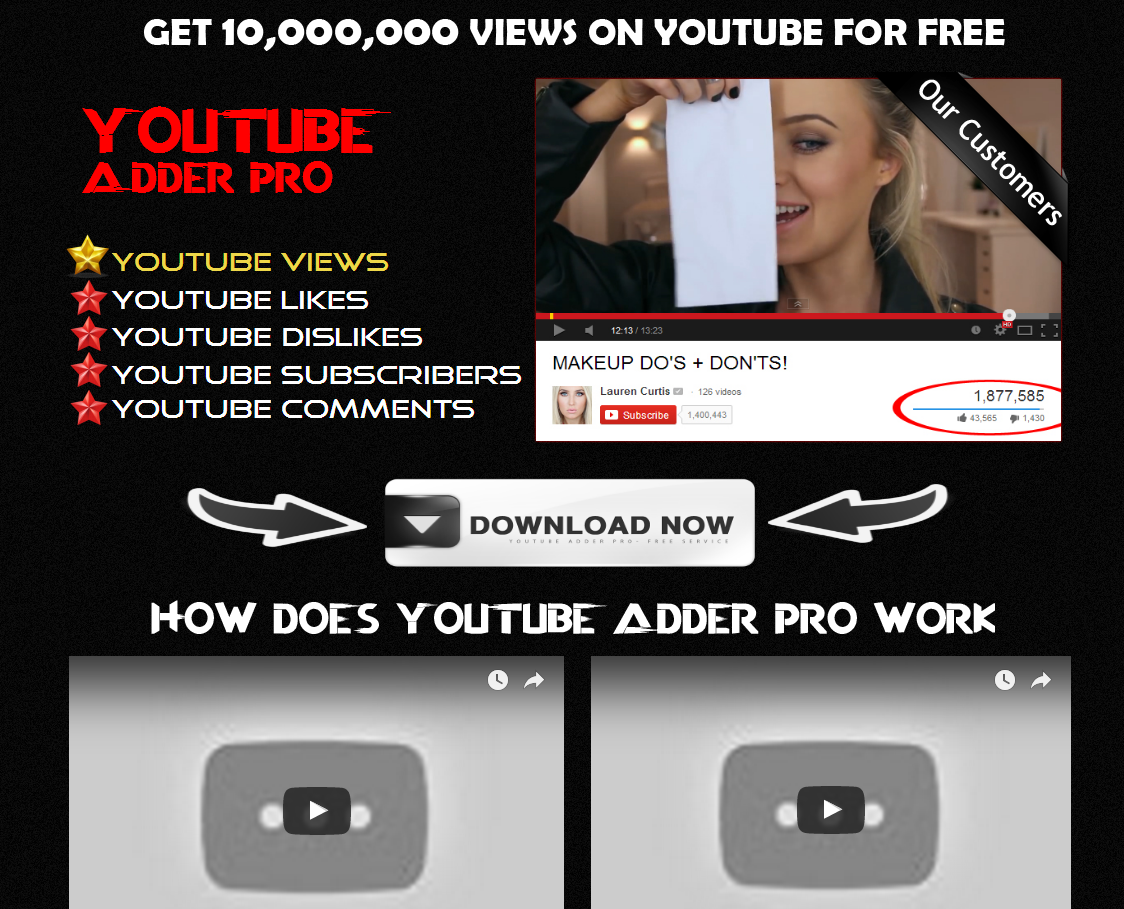
Webpage of the tool we took a closer look at
![]()
Tools deliver false promises to YouTubers and Gamers
If you have a YouTube account and are an aspiring YouTube star, you may have wondered if there’s an easy way to speed up the slow process of raising your channel to the top. If you’re a slow-moving gamer looking for a simple way to advance your skills, you may have wished for coins to make more in game purchases and progress. If you search the Internet, you will definitely find websites with good advice on how to promote your content and even tips on how to create good videos and how to improve your gaming abilities.
“Want more subscribers? No problem!”
There’s much more available on the Internet than just advice and tips. You can also find websites, tools, and bots that promise to quickly boost a user’s YouTube or other social channels. Looking for more subscribers or followers? You’re in luck — we found a website where you just fill out a short form and click on a button or download their tool. Of course, there are comments left by satisfied customers who are promoting the tools. Since you’re not the first to use the tool and it has good reviews by others, it has to work, right?

Webpage of the tool we took a closer look at
![]()
Persistent Cross-Site Scripting in WP Live Chat Support plugin
Posted by Securify B.V. on Jul 11
————————————————————————
Persistent Cross-Site Scripting in WP Live Chat Support plugin
————————————————————————
Han Sahin, July 2016
————————————————————————
Abstract
————————————————————————
A persistent Cross-Site Scripting (XSS) vulnerability has been…
